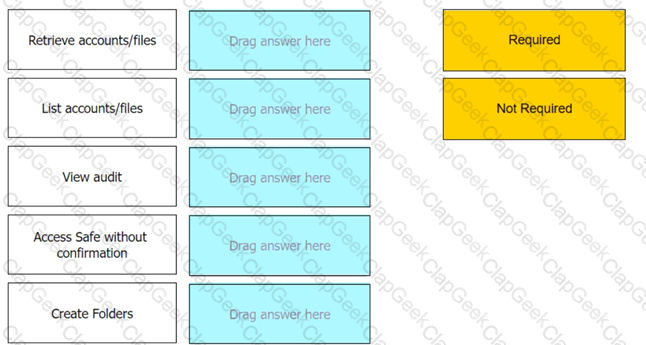
What are the minimum permissions to add multiple accounts from a file when using PVWA bulk-upload? (Choose three.)
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?
Which Master Policy Setting must be active in order to have an account checked-out by one user for a pre-determined amount of time?
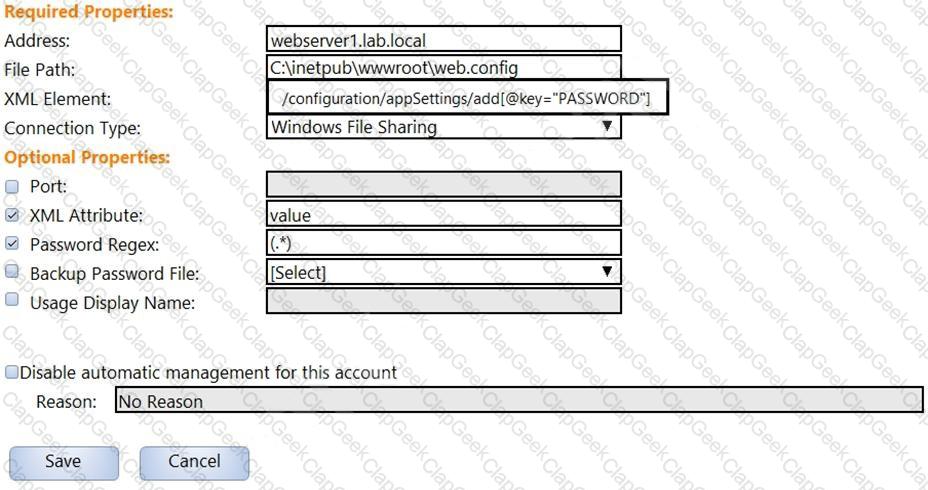
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server, which user will be utilized?
What must you specify when configuring a discovery scan for UNIX? (Choose two.)
When onboarding multiple accounts from the Pending Accounts list, which associated setting must be the same across the selected accounts?
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
The primary purpose of exclusive accounts is to ensure non-repudiation (Individual accountability).
Due to network activity, ACME Corp’s PrivateArk Server became active on the OR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault.
Which steps should you perform to restore DR replication to normal?
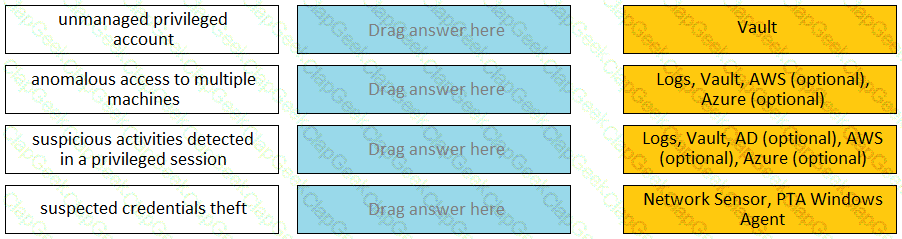
Match each PTA alert category with the PTA sensors that collect the data for it.
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
Which methods can you use to add a user directly to the Vault Admin Group? (Choose three.)
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will help the CyberArk Support Team debug the issue? (Choose three.)
Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
Where can a user with the appropriate permissions generate a report? (Choose two.)
You are logging into CyberArk as the Master user to recover an orphaned safe.
Which items are required to log in as Master?
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
The Vault administrator can change the Vault license by uploading the new license to the system Safe.
Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to be changed.
When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
It is possible to control the hours of the day during which a user may log into the vault.
You want to give a newly-created group rights to review security events under the Security pane. You also want to be able to update the status of these events.
Where must you update the group to allow this?
PSM for Windows (previously known as “RDP Proxy”) supports connections to the following target systems
Can the 'Connect' button be used to initiate an SSH connection, as root, to a Unix system when SSH access for root is denied?
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
A user is receiving the error message “ITATS006E Station is suspended for User jsmith” when attempting to sign into the Password Vault Web Access (PVWA). Which utility would a Vault administrator use to correct this problem?
When an account is unable to change its own password, how can you ensure that password reset with the reconcile account is performed each time instead of a change?
You created a new safe and need to ensure the user group cannot see the password, but can connect through the PSM.
Which safe permissions must you grant to the group? (Choose two.)
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
When running a “Privileged Accounts Inventory” Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
Which change could CyberArk make to the REST API that could cause existing scripts to fail?
Which authorizations are required in a recording safe to allow a group to view recordings?
You are creating a shared safe for the help desk.
What must be considered regarding the naming convention?
If a password is changed manually on a server, bypassing the CPM, how would you configure the account so that the CPM could resume management automatically?
Before failing back to the production infrastructure after a DR exercise, what must you do to maintain audit history during the DR event?
Which permissions are needed for the Active Directory user required by the Windows Discovery process?
To change the safe where recordings are kept for a specific platform, which setting must you update in the platform configuration?
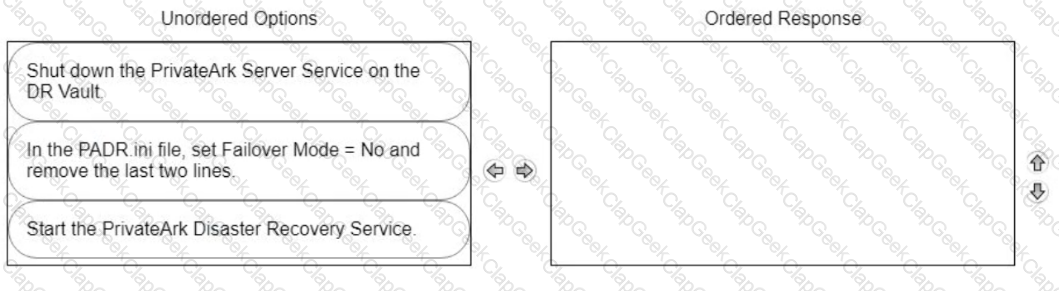
ADR Vault became active due to a failure of the primary Vault. Service on the primary Vault has now been restored. Arrange the steps to return the DR vault to its normal standby mode in the correct sequence.
A new colleague created a directory mapping between the Active Directory groups and the Vault.
Where can the newly Configured directory mapping be tested?
You have been asked to turn off the time access restrictions for a safe.
Where is this setting found?
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
For Digital Vault Cluster in a high availability configuration, how does the cluster determine if a node is down?
Which of the following files must be created or configured m order to run Password Upload Utility? Select all that apply.
You receive this error:
“Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.”
Which root cause should you investigate?