The application behavior control configuration file takes effect immediately after being referenced, without configuration submission.
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
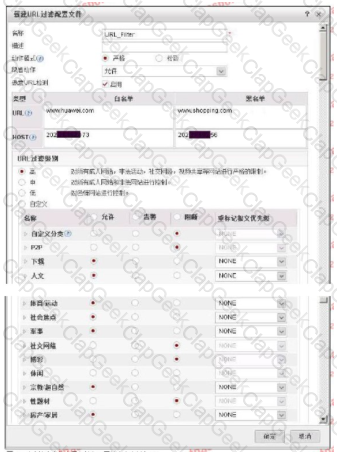
Regarding the network intrusion detection system (NIDS), which of the following statements is wrong?
Regarding the sequence of file filtering technology processing flow, which of the following is correct?
(1) The security policy is applied as permit
(2) Protocol decoding
(3) File type recognition
(4) Application recognition
(5) File filtering
When you suspect that the company's network has been attacked by hackers, you have carried out a technical investigation. Which of the following options does not belong to the behavior that occurred in the early stage of the attack?
If the Huawei USG600 product uses its own protocol stack cache for all files passing through the device and then performs a virus scan, then the device uses
It is the stream scanning method.
Under the CLI command, which of the following commands can be used to view the AV engine and virus database version?
The core technology of content security lies in anomaly detection, and the concept of defense lies in continuous monitoring and analysis.
Which of the following options are common reasons for IPS detection failure? (multiple choices)
Analysis is the core function of intrusion detection. The analysis and processing process of intrusion detection can be divided into three phases; build an analyzer to perform analysis on actual field data.
Which of the analysis, feedback and refinement is the function included in the first two stages?
Anti DDoS seven-layer defense can work from the dimensions of interface-based defense, global defense and defense object-based defense.
Regarding the anti-spam local black and white list, which of the following statements is wrong?
In the deployment of Huawei NIP6000 products, only port mirroring can be used for streaming replication.
With the continuous development of the network and the rapid development of applications, companies are making users more and more frequently start to transfer files on the network.
Virus threats are becoming more and more serious. Only by rejecting the virus outside the network can data security and system stability be guaranteed. So, which of the following are
What harm might be caused by illness? (multiple choices)
USG6000V software logic architecture is divided into three planes: management plane, control plane and
Cloud sandbox refers to deploying the sandbox in the cloud and providing remote detection services for tenants. The process includes:
1. Report suspicious files
2. Retrospective attack
3. Firewall linkage defense
4. Prosecution in the cloud sandbox
For the ordering of the process, which of the following options is correct?
Which of the following options belong to the upgrade method of the anti-virus signature database of Huawei USG6000 products? (multiple choice)
Among the following options, which attack is a malformed packet attack based on the TCR protocol?
When using the misuse check technology, if the normal user behavior is successfully matched with the intrusion feature knowledge base, it will be falsely reported.
Which of the following options is wrong for the description of the cleaning center?
Which of the following options belong to the keyword matching mode? (multiple choice)
Regarding traditional firewalls, which of the following statements are correct? (multiple choice)
The following commands are configured on the Huawei firewall:
[USG] firewall defend ip-fragment enable
Which of the following situations will be recorded as an offensive behavior? (multiple choice)
Which three aspects should be considered in the design of cloud platform security solutions? (multiple choice)