Which security fabric component sends a notification io quarantine an endpoint after IOC detection "n the automation process?
Exhibit.
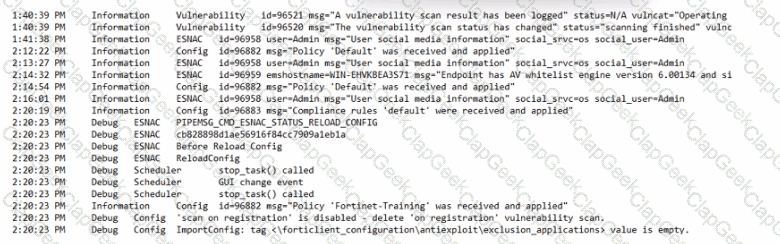
Based on the FortiClient logs shown in the exhibit, which endpoint profile policy is currently applied lo the ForliClient endpoint from the EMS server?
An administrator has a requirement to add user authentication to the ZTNA access for remote or off-fabric users Which FortiGate feature is required m addition to ZTNA?
A FortiClient EMS administrator has enabled the compliance rule for the sales department Which Fortinet device will enforce compliance with dynamic access control?
An administrator has lost web access to the FortiClient EMS console, and the web page to access to the console is timing out.
How can the administrator gather information to investigate the issue? (Choose one answer)
Refer to the exhibit.
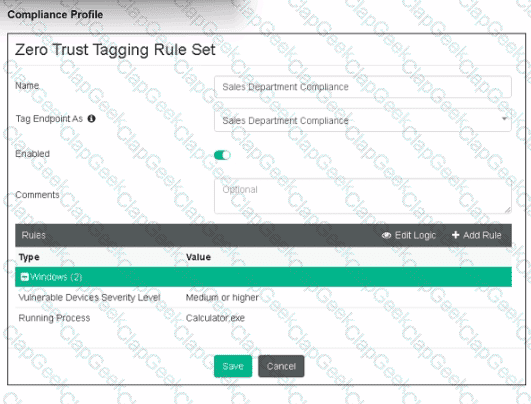
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two.)
Refer to the exhibit.
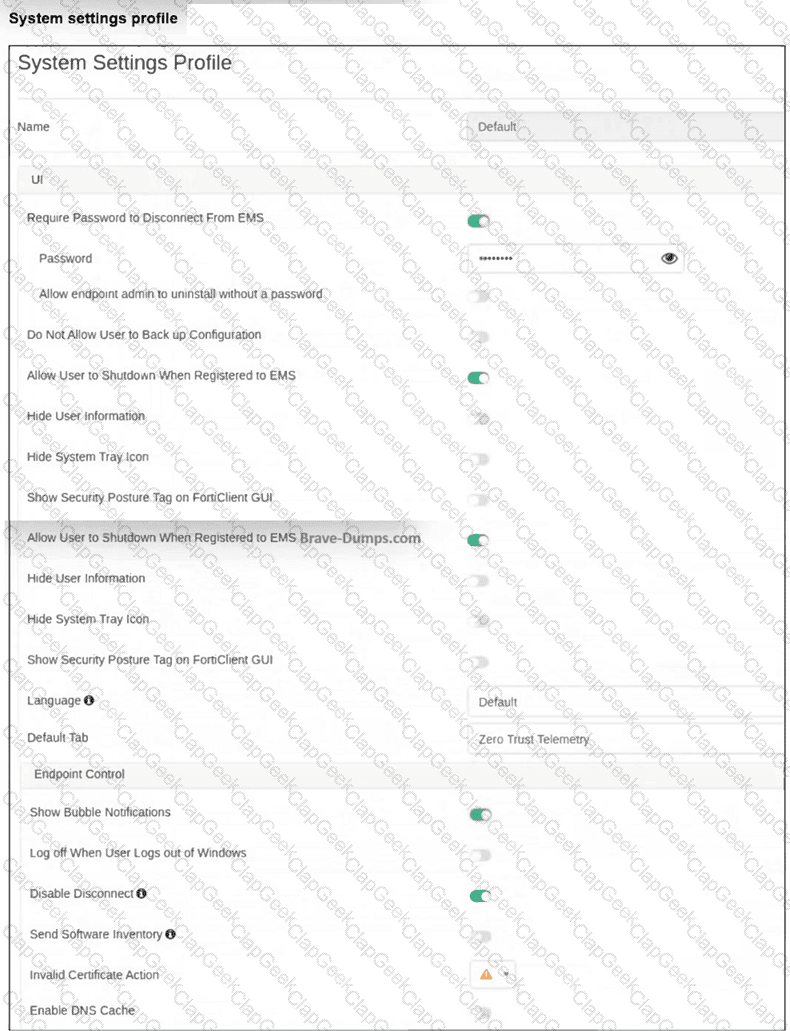
Which behavior should you expect when FortiClient with an invalid certificate is connecting to FortiClient EMS? (Choose one answer)
Refer to the exhibit, which shows the output of the ZTNA traffic log on FortiGate.
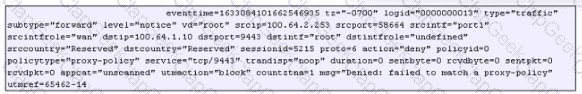
What can you conclude from the log message?
Refer to the exhibit.
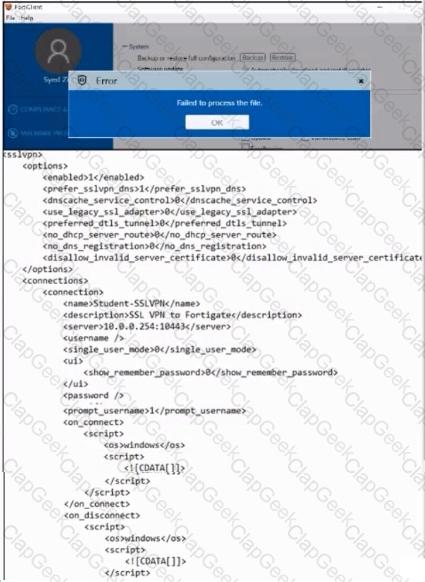
An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit.
Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
Refer to the exhibit.
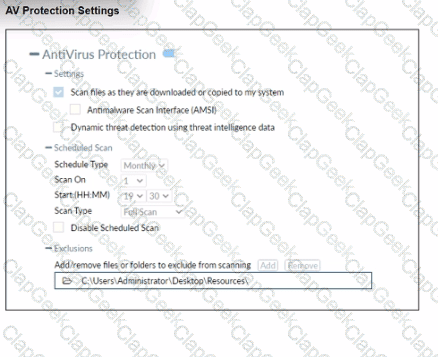
Based on The settings shown in The exhibit, which statement about FortiClient behaviour is Hue?
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
Refer to the exhibit.
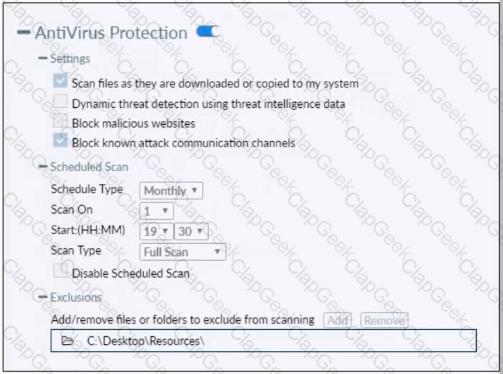
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
Which two are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)


