You need to add a new PSM server to an existing CyberArk environment.
What is the best way to determine the sizing of this server?
As a member of a PAM Level-2 support team, you are troubleshooting an issue related to load balancing four PVWA servers at two data centers. You received a note from your Level-1 support team stating “When testing PVWA website from a workstation, we noticed that the “Source IP of last sign-in” was shown as the VIP (Virtual IP address) assigned to the four PVWA servers instead of the workstation IP where the PVWA site was launched from.”
Which step should you take?
In large-scale environments, it is important to enable the CPM to focus its search operations on specific Safes instead of scanning all Safes it sees in the Vault.
How is this accomplished?
For redundancy, you want to add a secondary RADIUS server.
What must you do to accomplish this?
The account used to install a PVWA must have ownership of which safes? (Choose two.)
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA_Hardening.ps1 perform when run? (Choose two.)
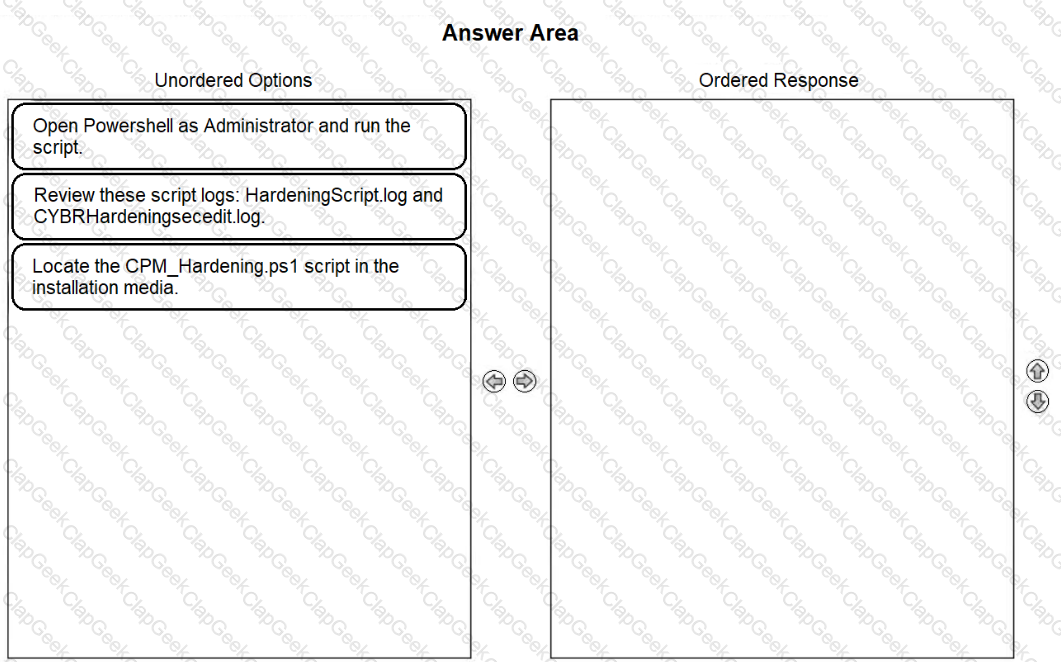
Arrange the steps to complete CPM Hardening for Out-of-Domain Deployment in the correct sequence.
A customer asked you to help scope the company's PSM deployment.
What should be included in the scoping conversation?
The PrivateArk clients allows a user to view the contents of the vault like a filesystem.
Which components can connect to a satellite Vault in a distributed Vault architecture?
Which file would you modify to configure the vault to send SNMP traps to your monitoring solution?
After installing the first PSM server and before installing additional PSM servers, you must ensure the user performing the installation is not a direct owner of which safe?
You are configuring the Vault to send syslog audit data to your organization’s SIEM solution.
What is a valid value for the SyslogServerProtocol parameter in DBPARM.INI file?
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? Choose all that apply
What is a valid combination of primary and secondary layers of authentication to a company's two-factor authentication policy?
If a customer has one data center and requires fault tolerance, how many PVWAs should be deployed?
When a DR vault server becomes an active vault, it will automatically fail back to the original state once the primary vault comes back online.
The RemoteApp feature of PSM allows seamless Application windows (i e the Desktop of the PSM server will not be visible)
You are configuring SNMP remote monitoring for your organization’s Vault servers.
In the PARAgent.ini, which parameter specifies the destination of the Vault SNMP traps?
What is the purpose of the CPM_Preinstallation.ps1 script included with the CPM installation package?
In which file must the attribute ‘SignAuthnRequest=”true”’ be added to the PartnerIdentityProvider element to support signed SAML requests?
CyberArk User Neil is trying to connect to the Target Linux server 192.168.1.164 using a domain account ACME/linuxuser01 on domain acme.corp using PSM for SSH server 192.168.65.145.
What is the correct syntax?
Which keys are required to be present in order to start the PrivateArk Server Service? Select all that apply.