Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
A FortiSASE customer has been enforcing always-on VPN for their remote users running FortiClient. What option can be enabled under the customer’s Endpoint Profile to allow them access different resources located in the same L2 network? (Choose one answer)
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
Which two statements about the Hub Selection Method in FortiSASE Secure Private Access (SPA) are correct? (Choose two answers)
Which three traffic flows are supported by FortiSASE Secure Private Access (SPA)? (Choose three answers)
Which FortiSASE feature ensures least-privileged user access to all applications?
What is the maximum number of Secure Private Access (SPA) service connections (SPA hubs) supported in the SPA use case? (Choose one answer)
Refer to the exhibits.
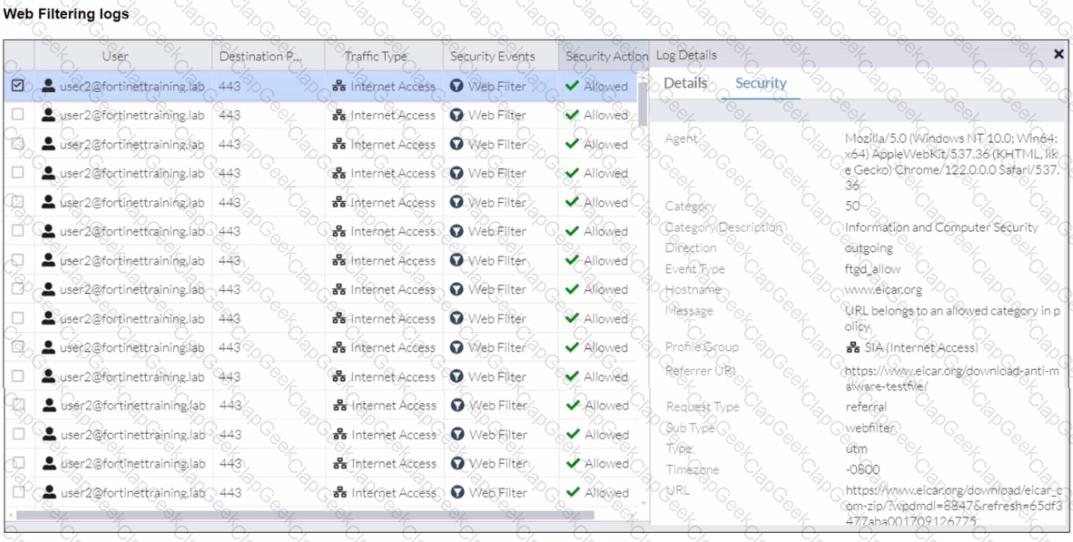
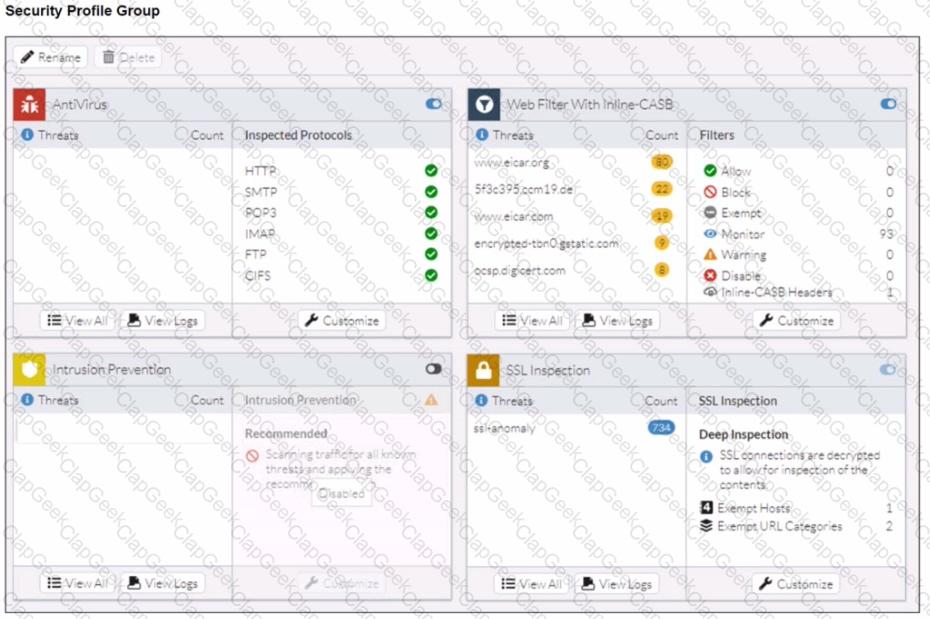
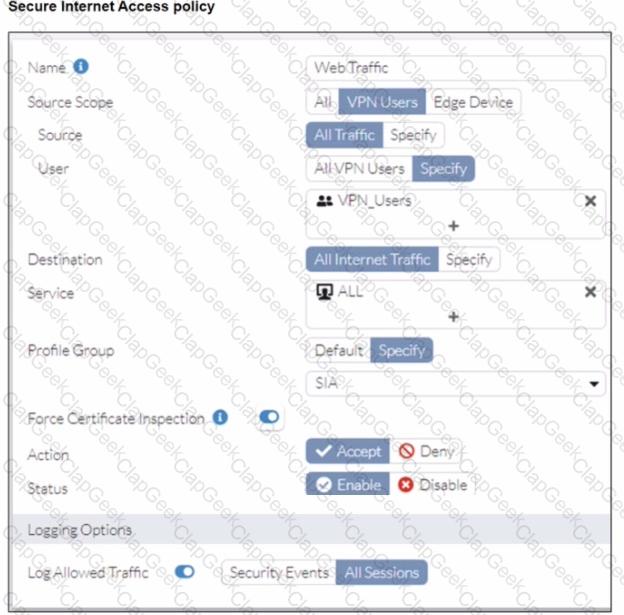
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?
Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
A customer configured the On/off-net detection rule to disable FortiSASE VPN auto-connect when users are inside the corporate network. The rule is set to Connects with a known public IP using the company’s public IP address. However, when the users are on the corporate network, the FortiSASE VPN still auto-connects. The customer has confirmed that traffic is going to the internet with the correct IP address.
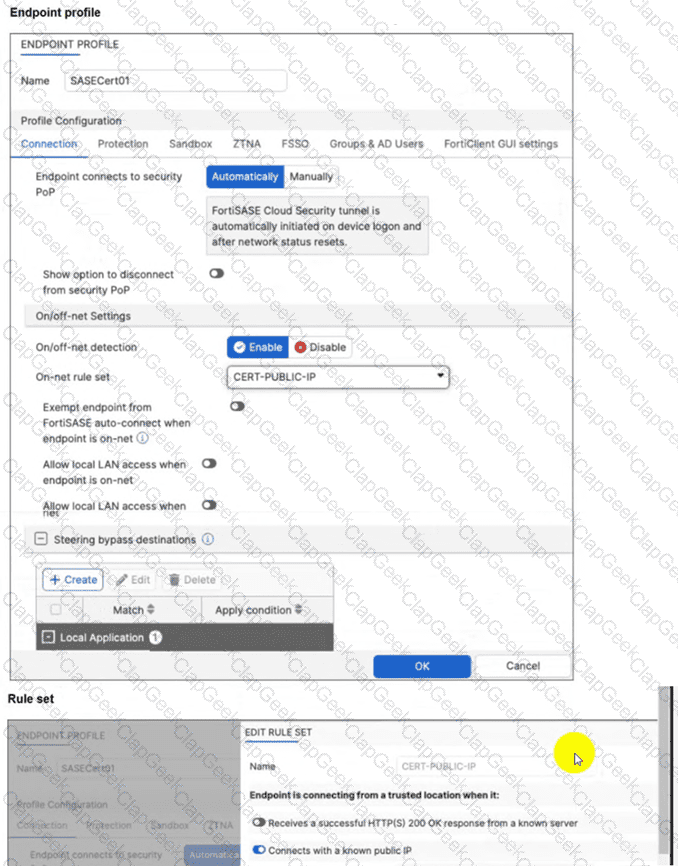
Which configuration is causing the issue? (Choose one answer)
Your FortiSASE customer has a small branch office in which ten users will be using their personal laptops and mobile devices to access the internet. Which deployment should they use to secure their internet access with minimal configuration? (Choose one answer)
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
Refer to the exhibit.
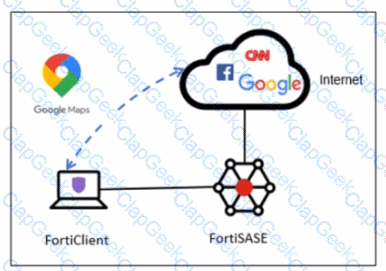
A company has a requirement to inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical Interface.
Which configuration must you apply to achieve this requirement?
Refer to the exhibits.
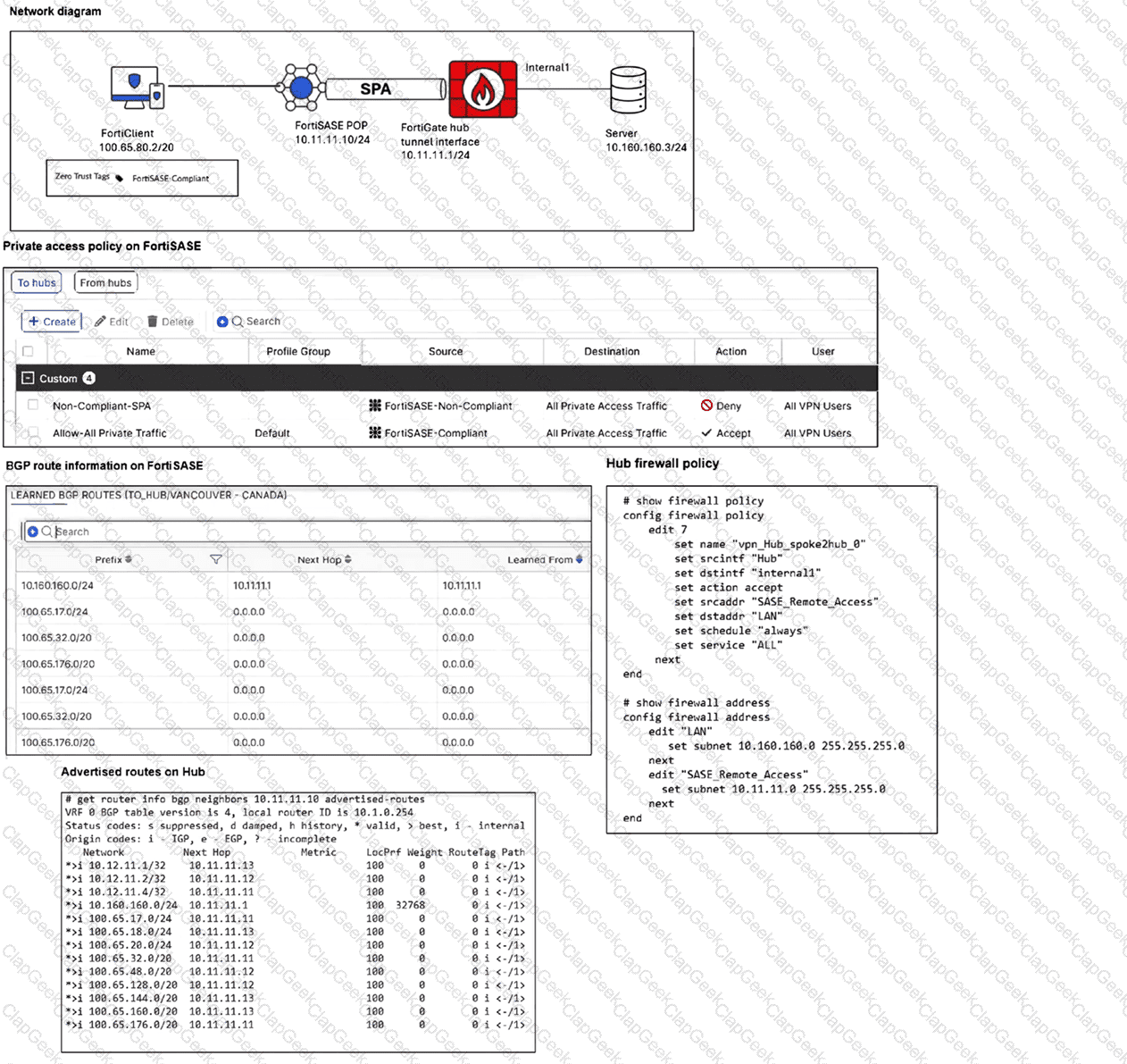
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub. What is the reason for the access failure? (Choose one answer)
Refer to the exhibits.
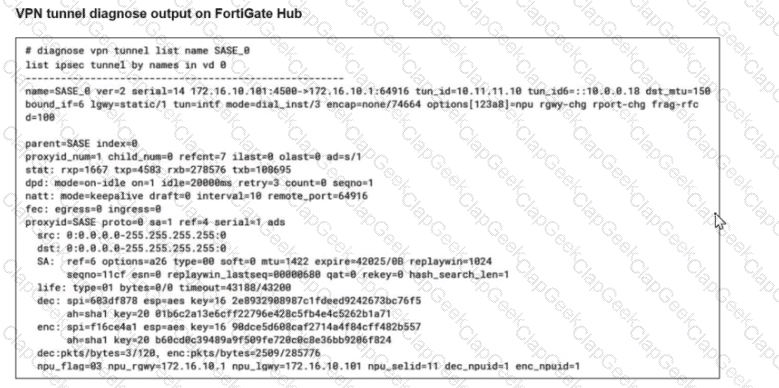
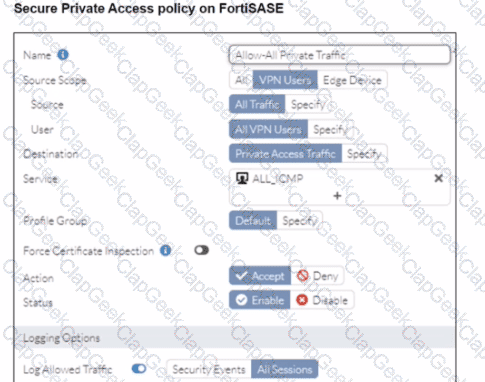
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGale hub. However, the administrator is not able to ping the webserver hosted behind the FortiGate hub.
Based on the output, what is the reason for the ping failures?
You are designing a new network, and the cybersecurity policy mandates that all remote users working from home must always be connected and protected. Which FortiSASE component facilitates this always-on security measure? (Choose one answer)
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system. How can you provide secure internet access to the contractor using FortiSASE? (Choose one answer)
Refer to the exhibits.
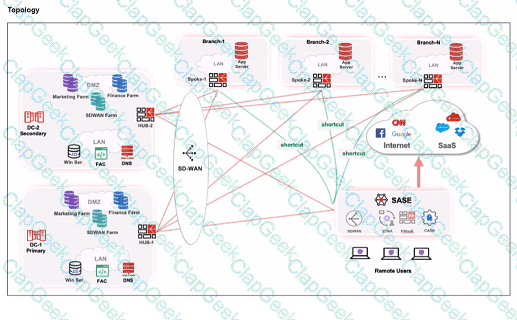
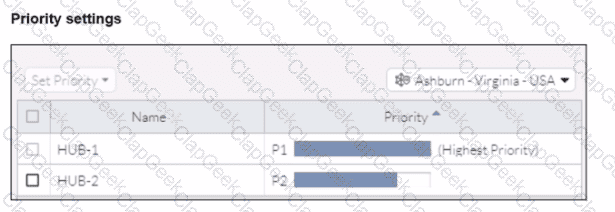
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
A FortiSASE administrator is receiving reports that some users have travelled overseas and cannot establish their agent-based VPN tunnels, although they can authenticate with their SSO credentials to access O365 and SFDC directly. The administrator reviewed the firewall policies and ZTNA tags of some users and could not find anything unusual. Which action can the administrator take to resolve this problem? (Choose one answer)
Which two benefits come from integrating SoCaaS with FortiSASE? (Choose two answers)


