You have onboarded the organization’s Microsoft Azure account on FortiCNAPP using the automated configuration approach. However, FortiCNAPP does not appear to be receiving any workload scanning data. How can you remedy this? (Choose one answer)
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)
Refer to the exhibit.
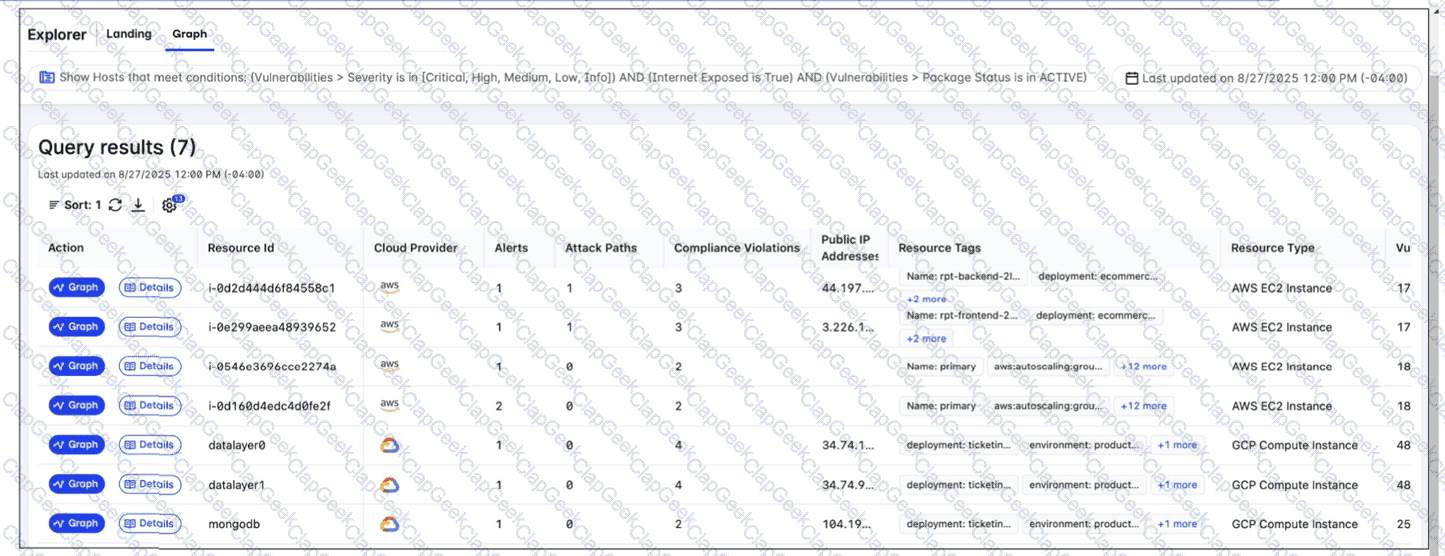
A FortiCNAPP administrator used the FortiCNAPP Explorer to reveal all hosts exposed to the internet that are running active packages with vulnerabilities of all severity levels. Why do only the first two results have an attack path? (Choose one answer)
Refer to the exhibit.

You are managing an active-passive FortiGate HA cluster in AWS that was deployed using CloudFormation. You have created a change set to examine the effects of some proposed changes to the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
Refer to the exhibit.

You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit.
What next step must the administrator take to access this instance from the internet?
An administrator is configuring a software-defined network (SDN) connector in FortiWeb to dynamically obtain information about existing objects in an Amazon Elastic Kubernetes Service (EKS) cluster.
Which AWS policy should the administrator attach to a user to achieve this goal?
Refer to the exhibit.
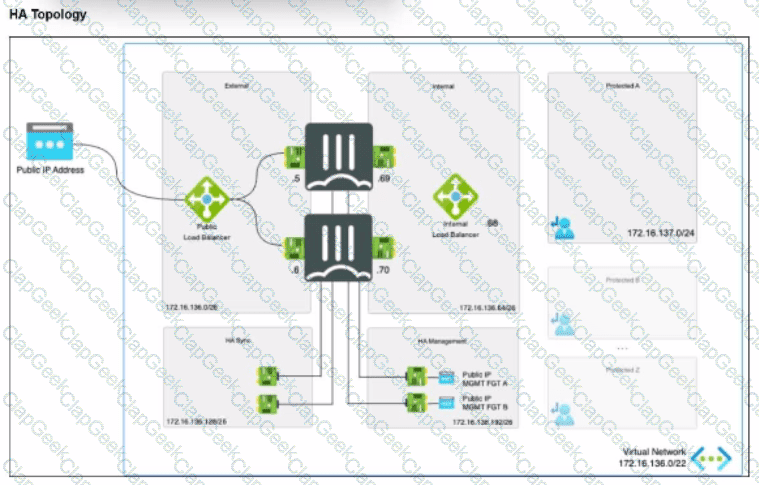
The exhibit shows an active-passive high availability FortiGate pair with external and internal Azure load balancers There is no SDN connector used in this solution.
Which configuration must the administrator implement on each FortiGate?
An administrator is trying to implement FortiCNP with Microsoft Azure Security integration. However, FortiCNP is not able to extract any cloud integration data from Azure; therefore, real-time cloud security monitoring is not possible.
What is causing this issue?
A Network security administrator is searching for a solution to secure traffic going in and out of the container infrastructure.
In which two ways can Fortinet container security help secure container infrastructures? (Choose two.)
An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.
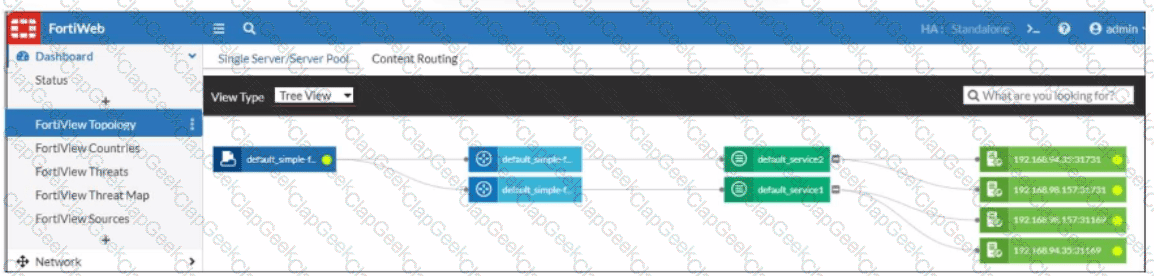
What can you conclude about the topology shown in FortiView?
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
Refer to the exhibit.

A senior administrator in a multinational organization needs to include a comment in the template shown in the exhibit to ensure that administrators from other regions change the Amazon Machine Image (AMI) ID to one that is valid in their location.
How can the administrator add the required comment in that section of the file?
Your DevOps team is evaluating different Infrastructure as Code (IaC) solutions for deploying complex Azure environments.
What is an advantage of choosing Azure Bicep over other IaC tools available?


