What are two system-level logs that can be purged using application configuration? (Choose two.)
What are two different services that you can configure for monitoring system and cluster health statuses on FortiSOAR?
(Choose two.)
Which edition of license, when deployed, will serve as a primary node in a distributed deployment?
Refer to the exhibit.
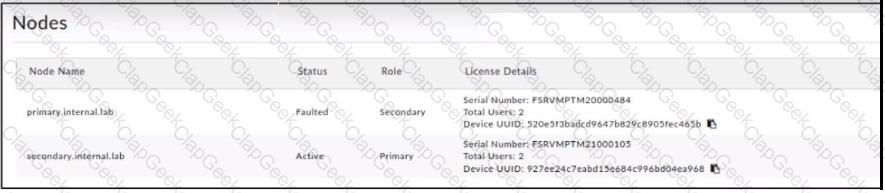
The former primary node was relegated to the secondary rote but is stuck in the Faulted state.
Which two steps must you take to restore operation in the high availability (HA) cluster? (Choose two.)
Refer to the exhibit.
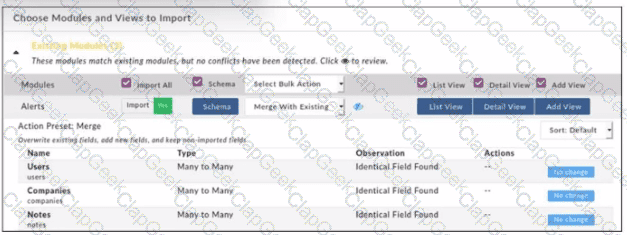
When importing modules to FortiSOAR using the configuration wizard, what actions are applied to fields it you select Merge with Existing as the Bulk action?
A security analyst has reported unauthorized access to System Configuration. You must review the user's current level of access, and then restrict their access according to your organization's requirements. As part of your auditing process, which two actions should you perform? (Choose two.)


