Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
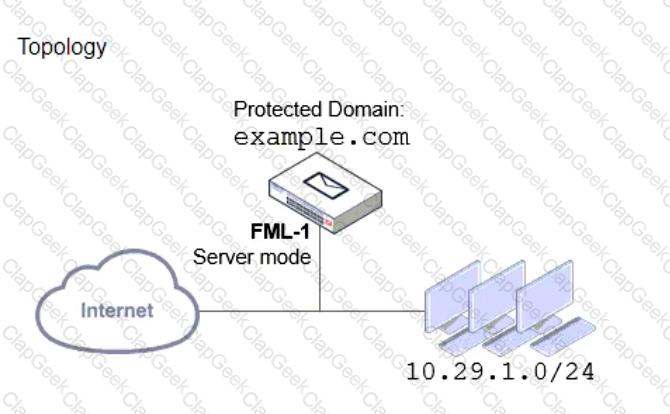
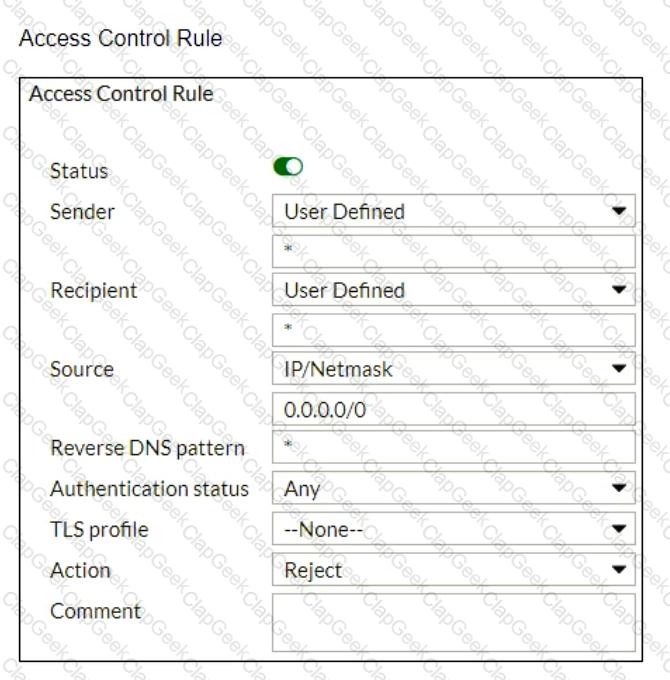
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
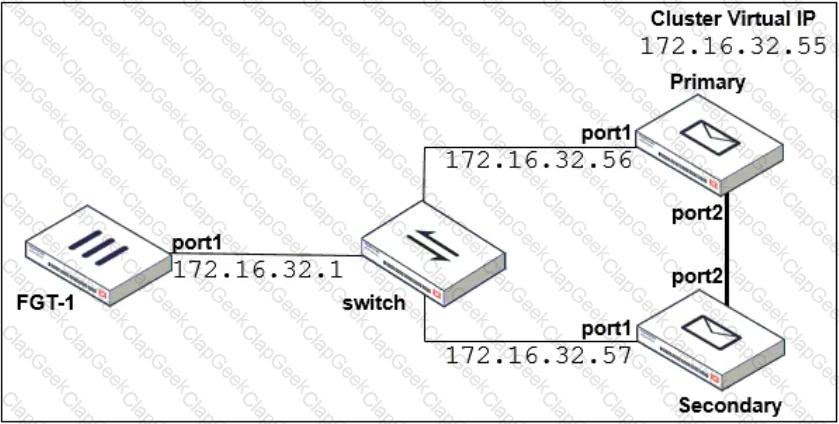
Which IP address must the DNS MX record for this organization resolve to?
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
Refer to the exhibits which shows a DLP scan profile configuration (DLP Scan Rule 1 and DLP Scan Rule 2) from a FortiMail device.
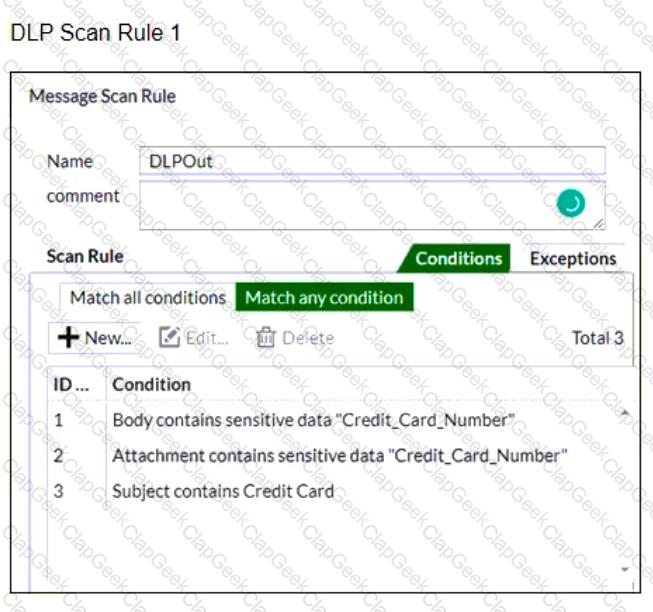
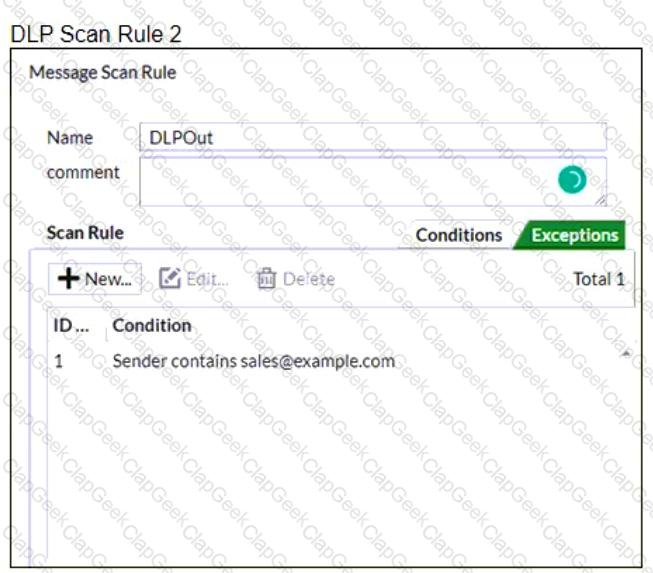
Which two message types will trigger this DLP scan rule? (Choose two.)
Refer to the exhibit which shows an nslookup output of MX records of the example.com domain.
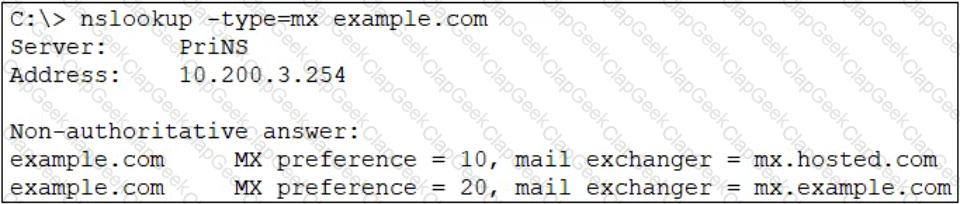
Which two MTA selection behaviors for the example.com domain are correct? (Choose two.)


