A customer wants to upgrade their legacy on-premises proxy to a cloud-based proxy for a hybrid network.
Which two FortiSASE features would help the customer achieve this outcome? (Choose two.)
An administrator must restrict endpoints from certain countries from connecting to FortiSASE.
Which configuration can achieve this?
Refer to the exhibit.
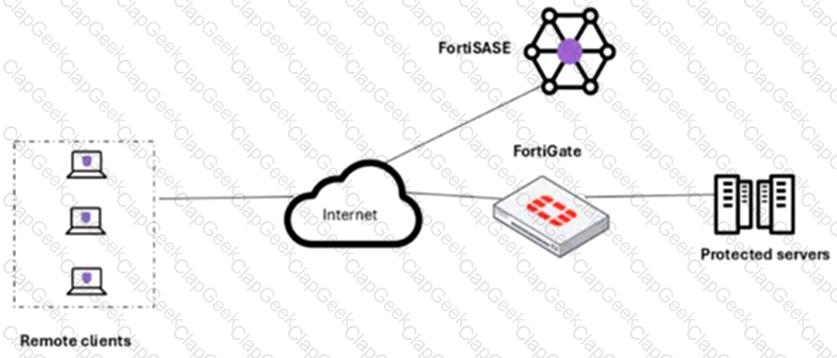
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which two setups will achieve these requirements? (Choose two.)
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
In a FortiSASE SD-WAN deployment with dual hubs, what are two benefits of assigning hubs with different priorities? (Choose two.)
Which two are required to enable central management on FortiSASE? (Choose two.)
What are two benefits of deploying FortiSASE with FortiGate ZTNA access proxy? (Choose two.)
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two.)
Which information can an administrator monitor using reports generated on FortiSASE?
In which two ways does FortiSASE help organizations ensure secure access for remote workers? (Choose two.)
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?


