Refer to the exhibits, which display a topology diagram (Topology) and two FortiMail device configurations (FML1 ConfigurationandFML2 Configuration).
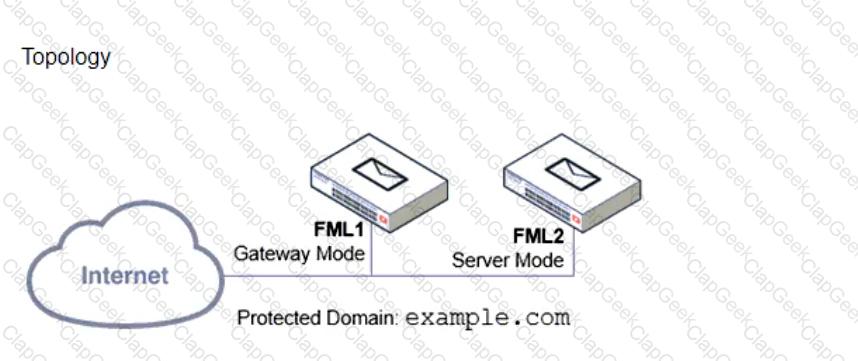
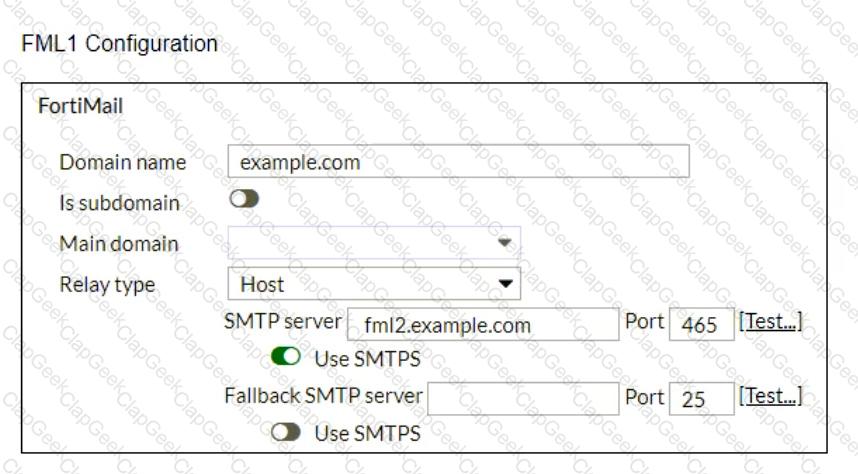
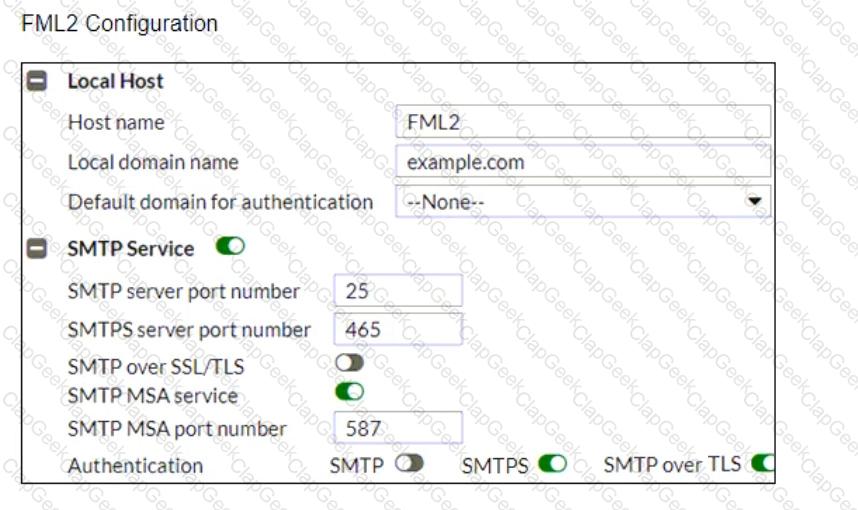
What is the expected outcome of SMTP sessions sourced from FML1 and destined for FML2?
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
Refer to the exhibit which displays a topology diagram.
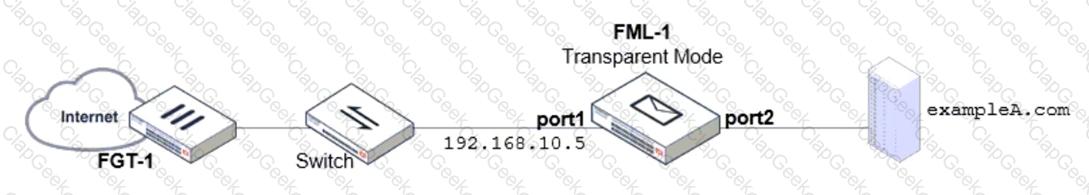
Which two statements describe the built-in bridge functionality on a transparent mode FortiMail? (Choose two.)
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)
Refer to the exhibit, which shows a topology diagram of two MTAs.

MTA-1 is delivering an email intended for User 1 to MTA-2. User 1 uses Outlook as an email client. Which two statements about protocol usage between these devices are correct? (Choose two.)
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
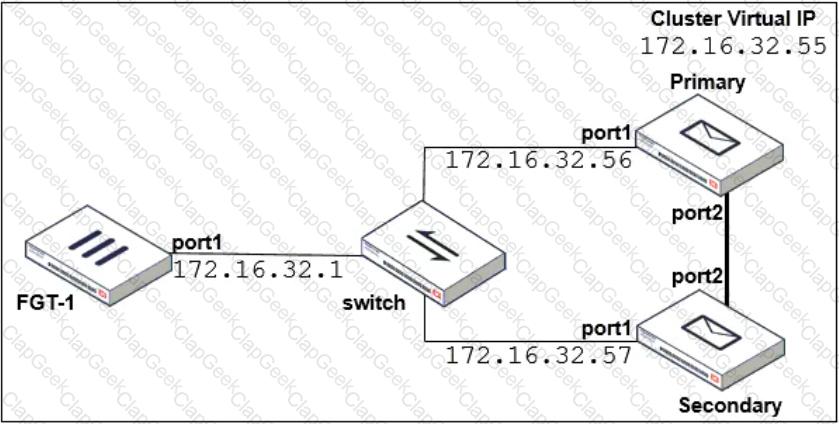
Which IP address must the DNS MX record for this organization resolve to?
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identities that the DSNs were not generated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator enable to prevent this scenario?
When configuring a FortiMail HA group consisting of different models, which two statements are true? (Choose two.)
What are Two reasons for having reliable DNS servers configured on FortiMail? (Choose two.)
Which three configuration steps must you set to enable DKIM signing for outbound messages on FortiMail? (Choose three.}
Which two FortiMail antispam techniques can you use to combat zero-day spam? (Choose two.)


