A network architect needs to build a new data center for a large company that has business units that process retail financial transactions. Which of the following information should the architect request from the company?
An organization with an on-premises data center is adopting additional cloud-based solutions. The organization wants to keep communication secure between remote employees' devices and workloads. Which of the following ZTA features best achieves this goal?
A network architect is designing a new network for a rural hospital system. Given the following requirements:
Highly available
Consistent data transmission
Resilient to simultaneous failures
Which of the following topologies should the architect use?
A cloud engineer is planning to build VMs in a public cloud environment for a cloud migration. A cloud security policy restricts access to the console for new VM builds. The engineer wants to replicate the settings for each of the VMs to ensure the network settings are preconfigured. Which of the following is the best deployment method?
Which of the following helps the security of the network design to align with industry best practices?
A network engineer is setting up guest access on a Wi-Fi network. After a recent network analysis, the engineer discovered that a user could access the guest network and attack the corporate network, since the networks share the same VLAN. Which of the following should the engineer do to prevent an attack like this one from happening?
A large commercial enterprise that runs a global video streaming platform recently acquired a small business that serves customers in a geographic area with limited connectivity to the global telecommunications infrastructure. The executive leadership team issued a mandate to deliver the highest possible video streaming quality to all customers around the world. Which of the following solutions should the enterprise architect suggest to meet the requirements?
A network engineer is working on securing the environment in the screened subnet. Before penetration testing, the engineer would like to run a scan on the servers to identify the OS, application versions, and open ports. Which of the following commands should the engineer use to obtain the information?
A network engineer is establishing a wireless network for handheld inventory scanners in a manufacturing company's warehouse. The engineer needs an authentication mechanism for these scanners that uses the Wi-Fi network and works with the company's Active Directory. The business requires that the solution authenticate the users and authorize the scanners. Which of the following provides the best solution for authentication and authorization?
A network administrator is troubleshooting an outage at a remote site. The administrator examines the logs and determines that one of the internet links at the site appears to be down. After the service provider confirms this information, the administrator fails over traffic to the backup link. Which of the following should the administrator do next?
A company is experiencing multiple switch failures. The network analyst discovers the following:
Network recovery time is unacceptable and occurs after the shutdown of some switches.
Some loops were detected in the network.
No broadcast storm was detected.
Which of the following is the most cost-effective solution?
End users are getting certificate errors and are unable to connect to an application deployed in a cloud. The application requires HTTPS connection. A network solution architect finds that a firewall is deployed between end users and the application in the cloud. Which of the following is the root cause of the issue?
A company hosts a cloud-based e-commerce application and only wants the application accessed from certain locations. The network team configures a cloud firewall with WAF enabled, but users can access the application globally. Which of the following should the network team do?
A user reports an issue connecting to a database server. The front-end application for this database is hosted on the company's web server. The network engineer has changed the network subnet that the company servers are located on along with the IP addresses of the servers. These are the new configurations:
New subnet for the servers is 10.10.10.64/27
Web server IP address is 10.10.10.101
Database server IP is 10.10.10.93
Which of the following is most likely causing the user's issue?
A cloud network engineer needs to enable network flow analysis in the VPC so headers and payload of captured data can be inspected. Which of the following should the engineer use for this task?
A network architect is designing a solution to place network core equipment in a rack inside a data center. This equipment is crucial to the enterprise and must be as secure as possible to minimize the chance that anyone could connect directly to the network core. The current security setup is:
In a locked building that requires sign in with a guard and identification check.
In a locked data center accessible by a proximity badge and fingerprint scanner.
In a locked cabinet that requires the security guard to call the Chief Information Security Officer (CISO) to get permission to provide the key.
Which of the following additional measures should the architect recommend to make this equipment more secure?
A company is experiencing numerous network issues and decides to expand its support team. The new junior employees will need to be onboarded in the shortest time possible and be able to troubleshoot issues with minimal assistance. Which of the following should the company create to achieve this goal?
After a company migrated all services to the cloud, the security auditor discovers many users have administrator roles on different services. The company needs a solution that:
Protects the services on the cloud
Limits access to administrative roles
Creates a policy to approve requests for administrative roles on critical services within a limited time
Forces password rotation for administrative roles
Audits usage of administrative roles
Which of the following is the best way to meet the company's requirements?
A network architect needs to design a solution to ensure every cloud environment network is built to the same baseline. The solution must meet the following requirements:
Use automated deployment.
Easily update multiple environments.
Share code with a community of practice.
Which of the following are the best solutions? (Choose two.)
A network security administrator needs to set up a solution to:
Gather all data from log files in a single location.
Correlate the data to generate alerts.
Which of the following should the administrator implement?
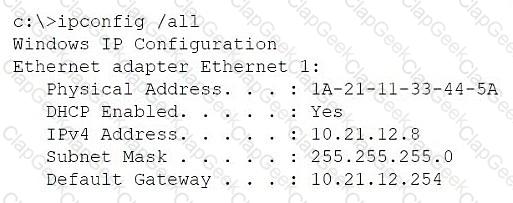
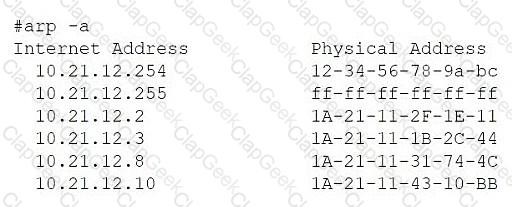
A network administrator is troubleshooting a user's workstation that is unable to connect to the company network. The results of ipconfig and arp -a are shown. The user’s workstation:
A router on the same network shows the following output:
Has an IP address of 10.21.12.8
Has subnet mask 255.255.255.0
Default gateway is 10.21.12.254
ARP table shows 10.21.12.8 mapped to 1A-21-11-31-74-4C (a different MAC address than the local adapter)
A network architect must ensure only certain departments can access specific resources while on premises. Those same users cannot be allowed to access those resources once they have left campus. Which of the following would ensure access is provided according to these requirements?