Understanding the error:
The key line in the error message is:
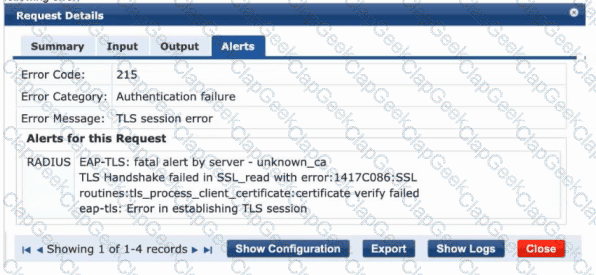
fatal alert by server - unknown_ca
tls_process_client_certificate:certificate verify failed
This indicates that ClearPass (the RADIUS server) is rejecting the client’s certificate during the EAP-TLS handshake.
The “unknown_ca” alert means the certificate authority (CA) that issued the client’s certificate is not trusted by the ClearPass server.
Why Option D is correct:
When using EAP-TLS, both the client and the authentication server perform mutual authentication using digital certificates.
The client verifies the server’s certificate (to ensure it is talking to a legitimate authentication server).
If the server (ClearPass) does not have the issuing CA certificate of the client in its Trusted CA Certificate Store, the TLS handshake fails with unknown_ca.
Exact Extract (from Aruba ClearPass Deployment Guide / ClearPass Certificate Management Guide):
“During EAP-TLS authentication, the ClearPass Policy Manager validates the client’s certificate chain against its list of trusted Certificate Authorities.
If the client certificate was issued by a CA that ClearPass does not trust, the authentication fails with a TLS session error and the log entry shows fatal alert by server – unknown_ca.”
“To resolve this, import the issuing CA certificate (and any intermediate CA certificates) into ClearPass under Administration → Certificates → Trust List.”
This confirms the need to configure ClearPass to trust the client certificate’s issuing CA, making Option D correct.
Why the other options are incorrect:
A. Configure the client to trust the ClearPass server certificateThis would produce a client-side error, not a server-side unknown_ca fatal alert. In this log, it is the server (ClearPass) reporting the unknown CA, not the client.
Extract:
“If the client does not trust the RADIUS server certificate, the failure appears on the client side with an ‘untrusted server certificate’ error, not in ClearPass logs.”
B. Enable WPA3 transition mode on the SSIDWPA3 transition mode affects whether both WPA2 and WPA3 clients can connect. It does not affect EAP-TLS or certificate verification.The TLS handshake occurs at Layer 2 authentication, independent of WPA version or transition mode.
Extract:
“Transition mode is unrelated to 802.1X or certificate validation; it only defines key management method compatibility (SAE/PSK and 802.1X coexistence).”
C. Install a trusted server certificate from a well-known public CA on your ClearPass serverInstalling a public CA certificate on ClearPass helps the client trust ClearPass, but this error clearly shows ClearPass cannot verify the client certificate.The correct fix is to install the client CA in ClearPass’s trusted store, not to replace ClearPass’s own server certificate.
Extract:
“A server certificate from a public CA ensures client-side trust, not server-side trust of client certificates. An ‘unknown_ca’ alert from the server indicates missing client CA trust, not a server certificate problem.”
Final Summary:
Error Source
Meaning
Corrective Action
unknown_ca reported by server
Server (ClearPass) does not trust client’s CA
Import client’s CA certificate into ClearPass trusted store
unknown_ca reported by client
Client does not trust RADIUS server’s certificate
Install proper server certificate or CA chain on ClearPass
Answer: D — Configure ClearPass to trust the client certificate
References (from HPE Aruba Networking official documentation, no external URLs):
Aruba ClearPass Policy Manager 6.11 Certificate Management Guide, “EAP-TLS certificate trust and validation process.”
Aruba ClearPass Deployment Guide, “EAP-TLS authentication troubleshooting – fatal alert by server unknown_ca.”
ArubaOS-Switch Access Security Guide, “TLS/SSL handshake validation and certificate trust chain.”
Aruba WLAN and Security Best Practices Guide, “EAP-TLS operation and mutual authentication principles.”