
Ethical Hacking and Countermeasures V8
Last Update Feb 21, 2026
Total Questions : 878
Why Choose ClapGeek



Try a free demo of our ECCouncil EC0-350 PDF and practice exam software before the purchase to get a closer look at practice questions and answers.

We provide up to 3 months of free after-purchase updates so that you get ECCouncil EC0-350 practice questions of today and not yesterday.

We have a long list of satisfied customers from multiple countries. Our ECCouncil EC0-350 practice questions will certainly assist you to get passing marks on the first attempt.

ClapGeek offers ECCouncil EC0-350 PDF questions, web-based and desktop practice tests that are consistently updated.

ClapGeek has a support team to answer your queries 24/7. Contact us if you face login issues, payment and download issues. We will entertain you as soon as possible.

Thousands of customers passed the ECCouncil Designing ECCouncil Azure Infrastructure Solutions exam by using our product. We ensure that upon using our exam products, you are satisfied.
Customers Passed
ECCouncil EC0-350
Average Score In Real
Exam At Testing Centre
Questions came word by
word from this dump
An Attacker creates a zuckerjournals.com website by copying and mirroring HACKERJOURNALS.COM site to spread the news that Hollywood actor Jason Jenkins died in a car accident. The attacker then submits his fake site for indexing in major search engines. When users search for "Jason Jenkins", attacker's fake site shows up and dupes victims by the fake news.
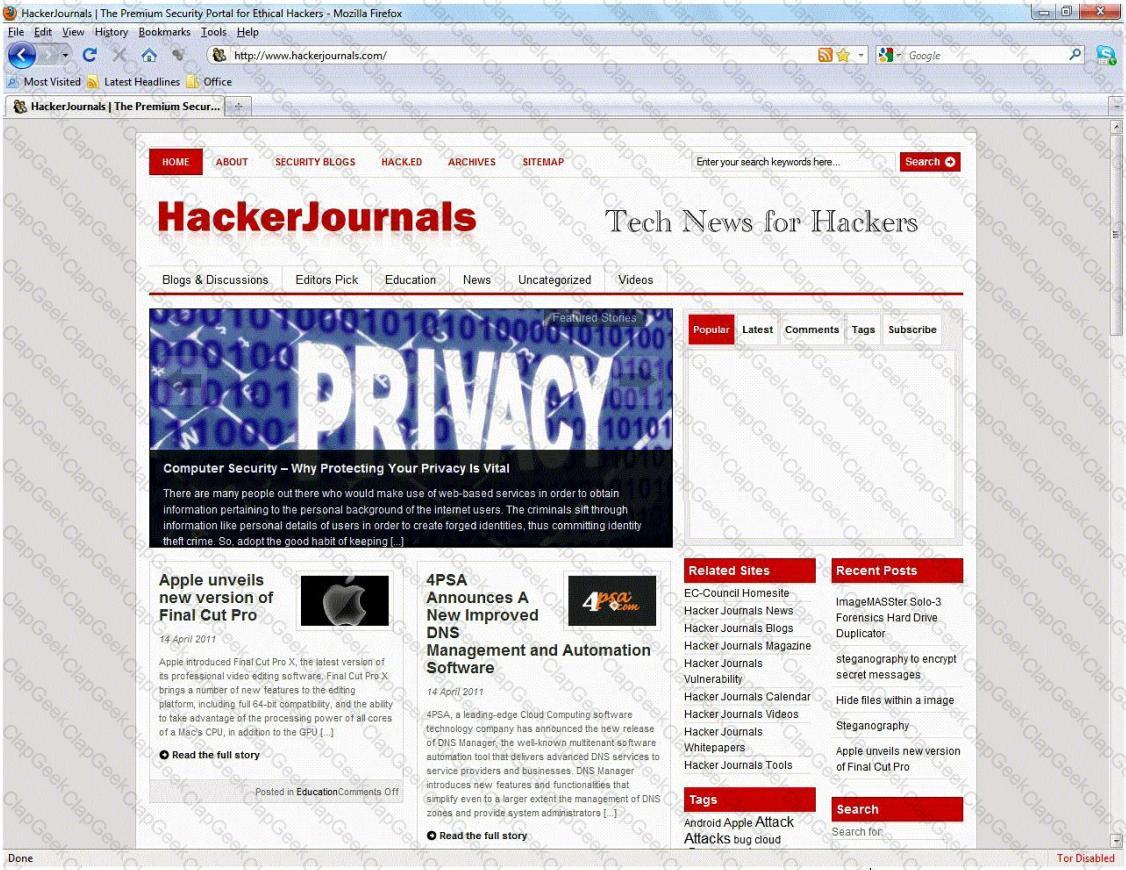
This is another great example that some people do not know what URL's are. Real website:
Fake website: http://www.zuckerjournals.com
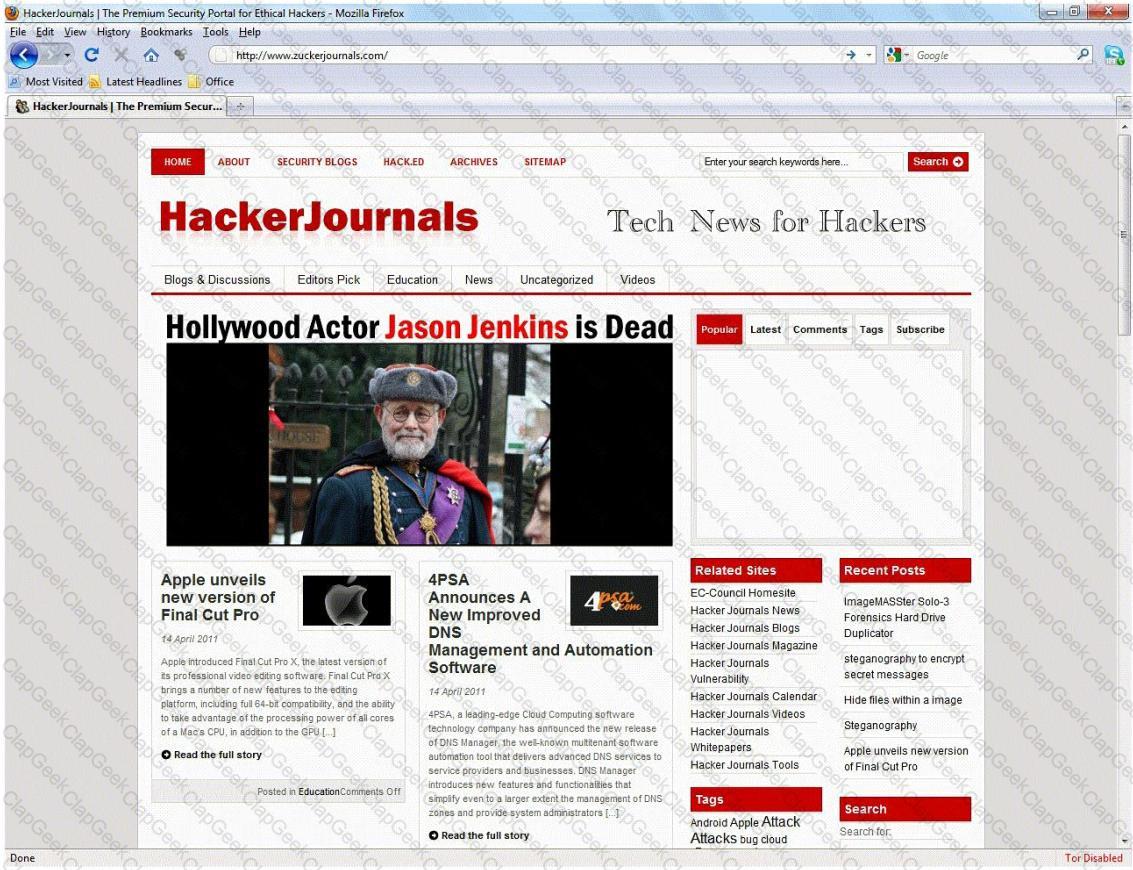
The website is clearly not WWW.HACKERJOURNALS.COM. It is obvious for many, but unfortunately some people still do not know what an URL is. It's the address that you enter into the address bar at the top your browser and this is clearly not legit site, its www.zuckerjournals.com
How would you verify if a website is authentic or not?
What sequence of packets is sent during the initial TCP three-way handshake?
What is the correct order of steps in CEH System Hacking Cycle?
