Which action will prevent the automatic extraction of indicators such as IP addresses and URLs from a script's output?
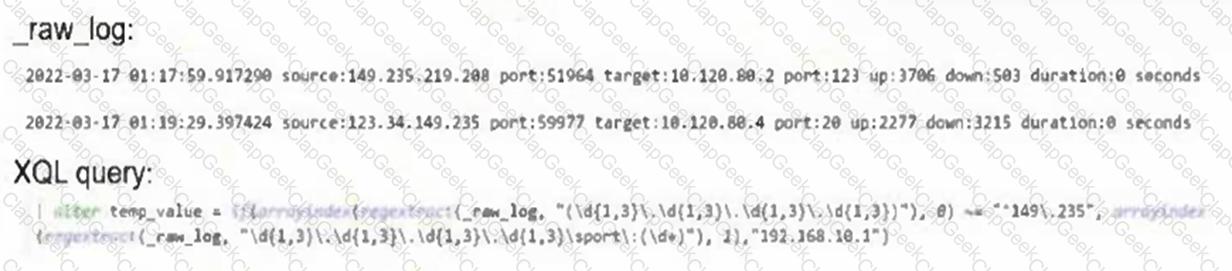
Based on the _raw_log and XQL query information below, what will be the result(s) of the temp_value?
Which two alert notification options can be configured without creating a playbook? (Choose two.)
Which two alert notification options can be configured without creating a playbook? (Choose two.)
Using the integrationContext object, how is data stored and retrieved between integration command runs in Cortex XSIAM?
Administrators from Building 3 have been added to Cortex XSIAM to perform limited functions on a subset of endpoints. Custom roles have been created and applied to the administrators to limit their permissions, but their access should also be constrained through the principle of least privilege according to the endpoints they are allowed to manage. All endpoints are part of an endpoint group named "Building3," and some endpoints may also be members of other endpoint groups.
Which technical control will restrict the ability of the administrators to manage endpoints outside of their area of responsibility, while maintaining visibility to Building 3's endpoints?
A Cortex XSIAM engineer at a SOC downgrades a critical threat intelligence content pack from the Cortex Marketplace while performing routine maintenance. As a result, the SOC team loses access to the latest threat intelligence data.
Which action will restore the functionality of the content pack to its previously installed version?
While using the playbook debugger, an engineer attaches the context of an alert as test data.
What happens with respect to the interactions with the list objects via tasks in this scenario?
An engineer is conducting a threat actor emulated test to determine which Cortex XDR module would provide protection or alert on a real-world attack. The first test was prevented.
Which action must the engineer take to enable continued testing?
A Remove the hash from the restrictions profile
B. Add an indicator exclusion.
C. Add a prevention rule.
D. Change the profile from "alert" to "prevent" for the BTP module.


