A Linux administrator wants to make the enable_auth variable set to 1 and available to the environment of subsequently executed commands. Which of the following should the administrator use for this task?
A Linux administrator updates the DNS record for the company using:
cat /etc/bind/db.abc.com
The revised partial zone file is as follows:
ns1 IN A 192.168.40.251
ns2 IN A 192.168.40.252
www IN A 192.168.30.30
When the administrator attempts to resolve www.abc.com to its IP address, the domain name still points to its old IP mapping:
nslookup www.abc.com
Server: 192.168.40.251
Address: 192.168.40.251#53
Non-authoritative answer:
Name: www.abc.com
Address: 199.168.20.81
Which of the following should the administrator execute to retrieve the updated IP mapping?
A Linux administrator just finished setting up passwordless SSH authentication between two nodes. However, upon test validation, the remote host prompts for a password. Given the following logs:

Which of the following is the most likely cause of the issue?
User1 reports "access denied" errors while trying to execute app. Given the following outputs:
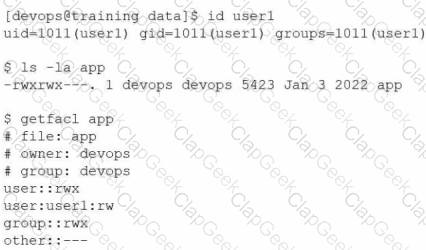
Which of the following options will remediate this issue?
A systems administrator needs to integrate a new storage array into the company's existing storage pool. The administrator wants to ensure that the server is able to detect the new storage array. Which of the following commands should the administrator use to ensure that the new storage array is presented to the systems?
Which of the following utilities supports the automation of security compliance and vulnerability management?
A Linux administrator tries to install Ansible in a Linux environment. One of the steps is to change the owner and the group of the directory /opt/Ansible and its contents. Which of the following commands will accomplish this task?
A systems administrator is creating a backup copy of the /home/ directory. Which of the following commands allows the administrator to archive and compress the directory at the same time?
A DevOps engineer made some changes to files in a local repository. The engineer realizes that the changes broke the application and the changes need to be reverted back. Which of the following commands is the best way to accomplish this task?
A Linux administrator is making changes to local files that are part of a Git repository. The administrator needs to retrieve changes from the remote Git repository. Which of the following commands should the administrator use to save the local modifications for later review?
Which of the following cryptographic functions ensures a hard drive is encrypted when not in use?
A Linux administrator wants to add a user to the Docker group without changing the user’s primary group. Which of the following commands should the administrator use to complete this task?
A Linux user runs the following command:
nohup ping comptia.com &
Which of the following commands should the user execute to attach the process to the current terminal?
An administrator receives the following output while attempting to unmount a filesystem:
umount /data1: target is busy.
Which of the following commands should the administrator run next to determine why the filesystem is busy?
A Linux user needs to download the latest Debian image from a Docker repository. Which of the following commands makes this task possible?
An administrator logs in to a Linux server and notices the clock is 37 minutes fast. Which of the following commands will fix the issue?
An administrator is investigating the reason a Linux workstation is not resolving the website http://www.comptia.org. The administrator executes some commands and receives the following output:
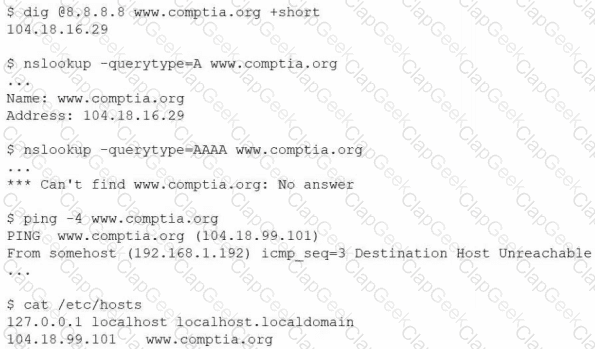
Which of the following is the most likely cause?
Users cannot access a server after it has been restarted. At the server console, the administrator runs the following commands;
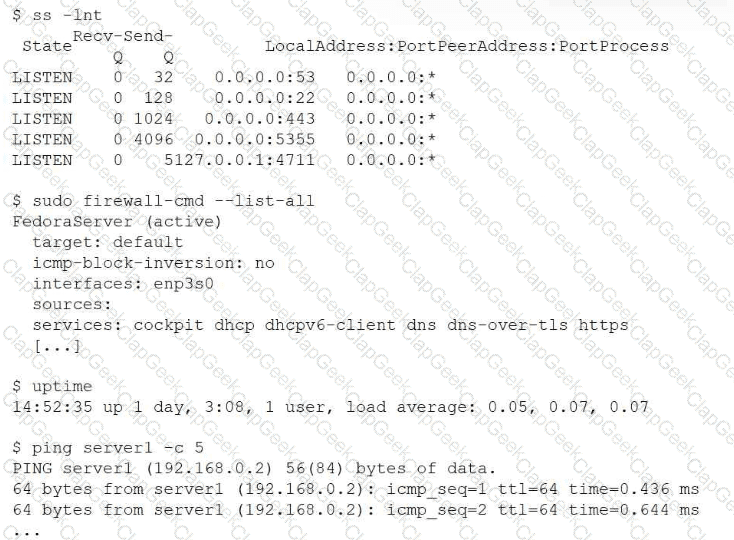
Which of the following is the cause of the issue?
A Linux administrator needs to create and then connect to the app-01-image container. Which of the following commands accomplishes this task?
A Linux user frequently tests shell scripts located in the /home/user/scripts directory. Which of the following commands allows the user to run the program by invoking only the script name?
A Linux administrator needs to analyze a compromised disk for traces of malware. To complete the analysis, the administrator wants to make an exact, block-level copy of the disk. Which of the following commands accomplishes this task?