Which of the following security principles most likely requires validation before allowing traffic between systems?
An unexpected and out-of-character email message from a Chief Executive Officer’s corporate account asked an employee to provide financial information and to change the recipient's contact number. Which of the following attack vectors is most likely being used?
Which of the following actors attacking an organization is the most likely to be motivated by personal beliefs?
A company makes a change during the appropriate change window, but the unsuccessful change extends beyond the scheduled time and impacts customers. Which of the following would prevent this from reoccurring?
An important patch for a critical application has just been released, and a systems administrator is identifying all of the systems requiring the patch. Which of the following must be maintained in order to ensure that all systems requiring the patch are updated?
A security analyst and the management team are reviewing the organizational performance of a recent phishing campaign. The user click-through rate exceeded the acceptable risk threshold, and the management team wants to reduce the impact when a user clicks on a link in a phishing message. Which of the following should the analyst do?
A company needs to determine whether authentication weaknesses in a customer-facing web application exist. Which of the following is the best technique to use?
The marketing department set up its own project management software without telling the appropriate departments. Which of the following describes this scenario?
Which of the following should be used to ensure that a device is inaccessible to a network-connected resource?
Which of the following consequences would a retail chain most likely face from customers in the event the retailer is non-compliant with PCI DSS?
Which of the following best explains how open service ports increase an organization's attack surface?
A university uses two different cloud solutions for storing student data. Which of the following does this scenario represent?
Which of the following security measures is required when using a cloud-based platform for loT management?
A company expects its provider to ensure servers and networks maintain 97% uptime. Which of the following would most likely list this expectation?
During a SQL update of a database, a temporary field used as part of the update sequence was modified by an attacker before the update completed in order to allow access to the system. Which of the following best describes this type of vulnerability?
A security analyst investigates abnormal outbound traffic from a corporate endpoint. The traffic is encrypted and uses non-standard ports. Which of the following data sources should the analyst use first to confirm whether this traffic is malicious?
A systems administrator is working on a solution with the following requirements:
Provide a secure zone.
Enforce a company-wide access control policy.
Reduce the scope of threats.
Which of the following is the systems administrator setting up?
Which of the following methods to secure credit card data is best to use when a requirement is to see only the last four numbers on a credit card?
An organization is evaluating the cost of licensing a new solution to prevent ransomware. Which of the following is the most helpful in making this decision?
Which of the following would most likely be deployed to obtain and analyze attacker activity and techniques?
A company receives an alert that a network device vendor, which is widely used in the enterprise, has been banned by the government.
Which of the following will the company's general counsel most likely be concerned with during a hardware refresh of these devices?
In which of the following scenarios is tokenization the best privacy technique 10 use?
An organization is leveraging a VPN between its headquarters and a branch location. Which of the following is the VPN protecting?
Two companies are in the process of merging. The companies need to decide how to standardize their information security programs. Which of the following would best align the security programs?
A penetration tester is testing the security of a building’s alarm system. Which type of penetration test is being conducted?
Which of the following is the best way to securely store an encryption key for a data set in a manner that allows multiple entities to access the key when needed?
During a recent log review, an analyst discovers evidence of successful injection attacks. Which of the following will best address this issue?
A company is concerned about the theft of client data from decommissioned laptops. Which of the following is the most cost-effective method to decrease this risk?
Which of the following security concepts is the best reason for permissions on a human resources fileshare to follow the principle of least privilege?
A security analyst is reviewing logs and discovers the following:

Which of the following should be used lo best mitigate this type of attack?
A company’s legal department drafted sensitive documents in a SaaS application and wants to ensure the documents cannot be accessed by individuals in high-risk countries. Which of the following is the most effective way to limit this access?
Which of the following explains how regular patching helps mitigate risks when securing an enterprise environment?
Which of the following best practices gives administrators a set period to perform changes to an operational system to ensure availability and minimize business impacts?
Which of the following explains how a supply chain service provider could introduce a security vulnerability into an organization?
A university employee logged on to the academic server and attempted to guess the system administrators' log-in credentials. Which of the following security measures should the university have implemented to detect the employee's attempts to gain access to the administrators' accounts?
A penetration test has demonstrated that domain administrator accounts were vulnerable to pass-the-hash attacks. Which of the following would have been the best strategy to prevent the threat actor from using domain administrator accounts?
Which of the following would best prepare a security team for a specific incident response scenario?
Which of the following risk management strategies is being used when a Chief Information Security Officer ignores known vulnerabilities identified during a risk assessment?
A company wants to ensure secure remote access to its internal network. The company has only one public IP and would like to avoid making any changes to the current network setup. Which of the following solutions would best accomplish this goal?
A few weeks after deploying additional email servers, a company begins to receive complaints that messages are going into recipients’ spam folders. Which of the following needs to be updated?
Which of the following cryptographic methods is preferred for securing communications with limited computing resources?
Which of the following environments utilizes a subset of customer data and is most likely to be used to assess the impacts of major system upgrades and demonstrate system features?
Which of the following architectures is most suitable to provide redundancy for critical business processes?
A new employee accessed an unauthorized website. An investigation found that the employee violated the company's rules. Which of the following did the employee violate?
A systems administrator wants to use a technical solution to explicitly define file permissions for the entire team. Which of the following should the administrator implement?
During a recent log review, an analyst found evidence of successful injection attacks. Which of the following will best address this issue?
Which of the following would be the greatest concern for a company that is aware of the consequences of non-compliance with government regulations?
During a penetration test in a hypervisor, the security engineer is able to inject a malicious payload and access the host filesystem. Which of the following best describes this vulnerability?
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
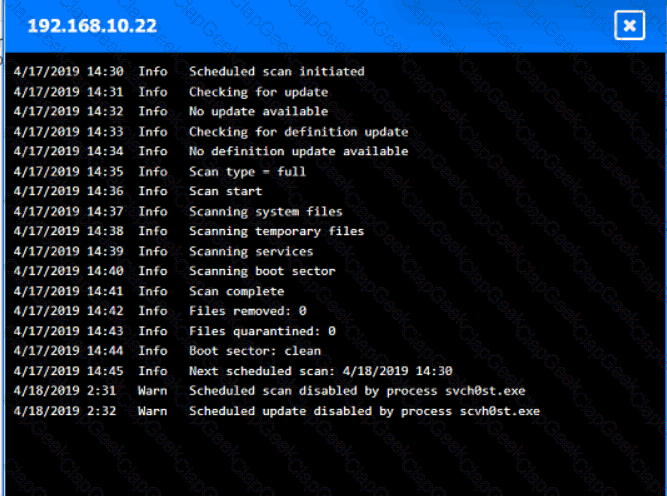
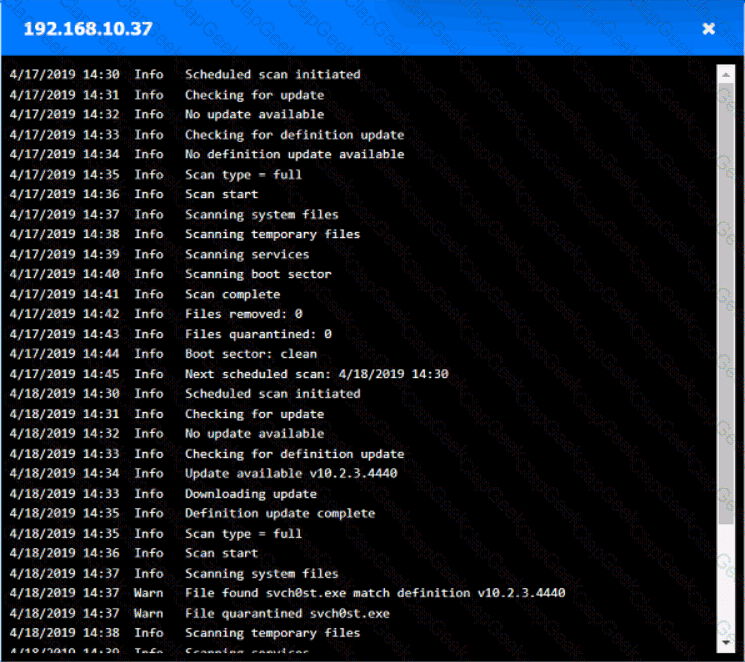
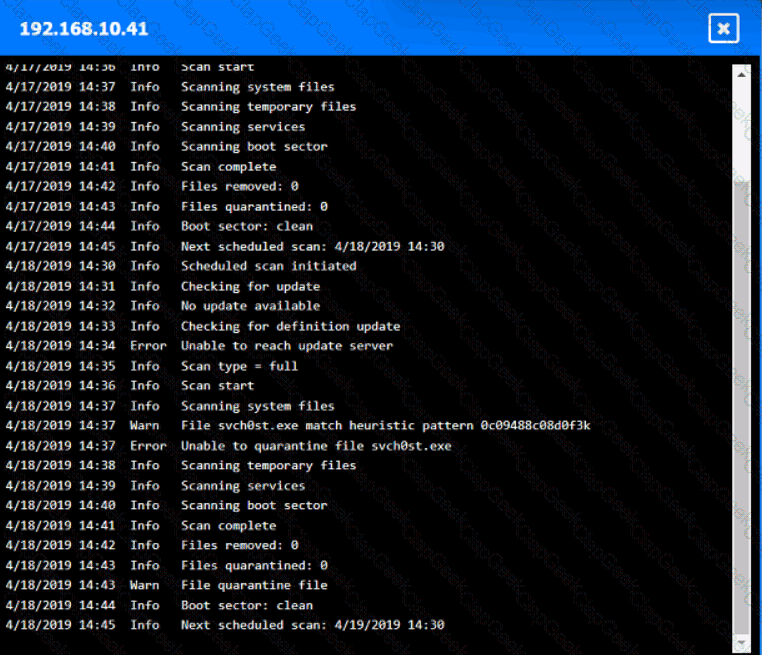
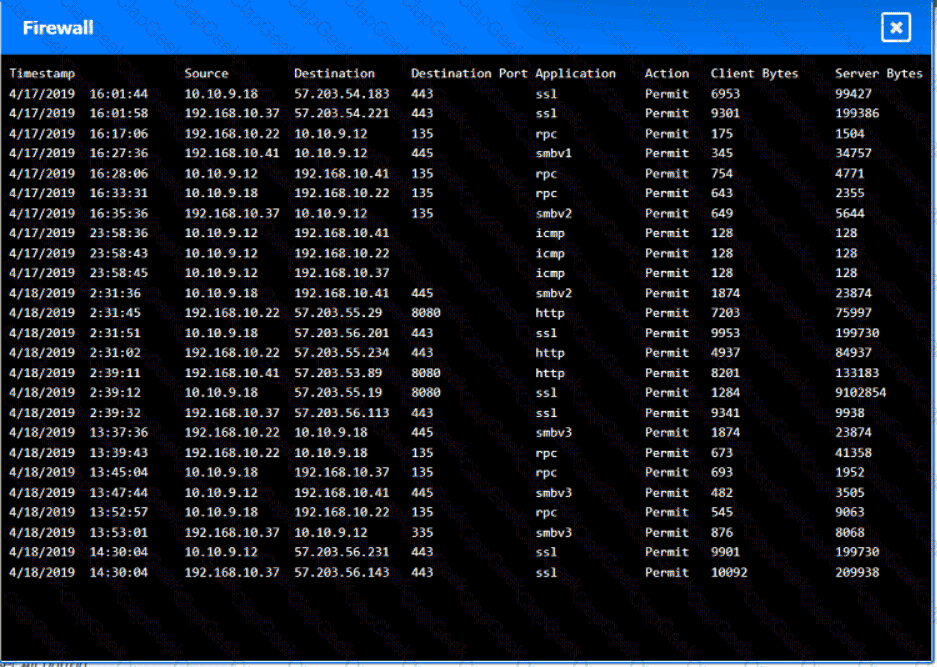
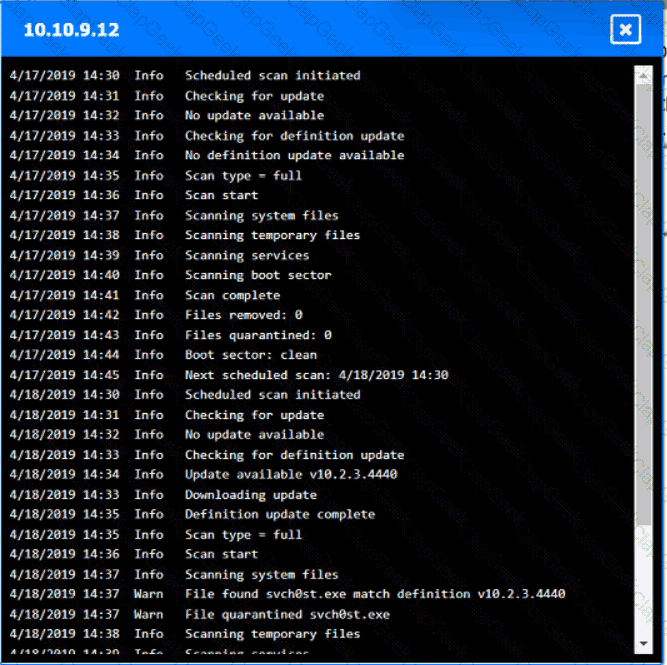
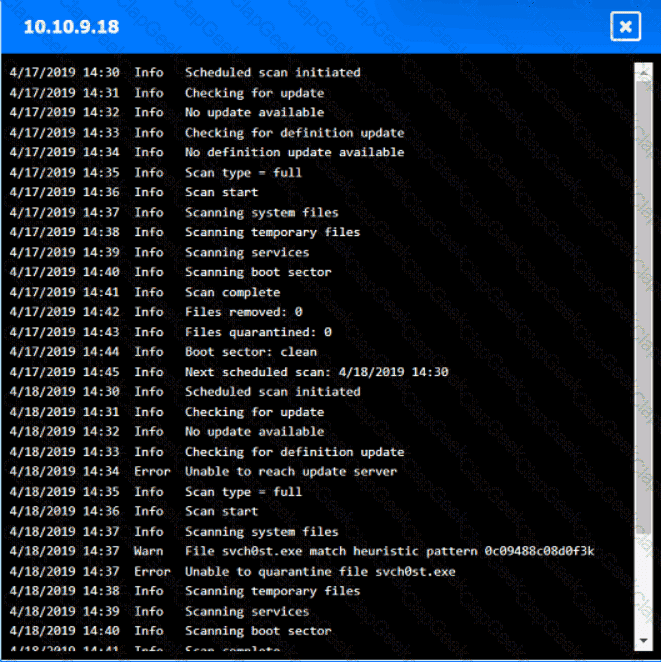
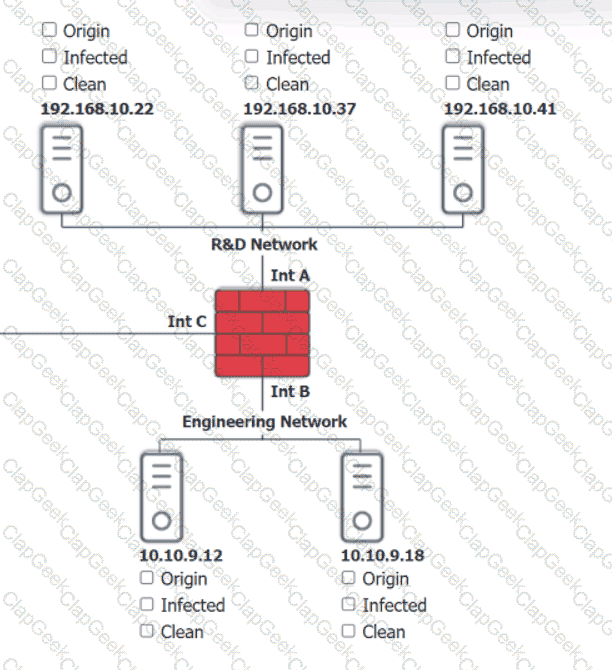
An employee who was working remotely lost a mobile device containing company data. Which of the following provides the best solution to prevent future data loss?
The management team notices that new accounts that are set up manually do not always have correct access or permissions.
Which of the following automation techniques should a systems administrator use to streamline account creation?
A cybersecurity incident response team at a large company receives notification that malware is present on several corporate desktops No known Indicators of compromise have been found on the network. Which of the following should the team do first to secure the environment?
Employees are missing features on company-provided tablets, affecting productivity. Management demands resolution in 48 hours. Which is the best solution?
Which of the following exercises should an organization use to improve its incident response process?
Malware spread across a company's network after an employee visited a compromised industry blog. Which of the following best describes this type of attack?
Which of the following control types involves restricting IP connectivity to a router's web management interface to protect it from being exploited by a vulnerability?
Which of the following threat actors would most likely deface the website of a high-profile music group?
A financial institution would like to store its customer data m the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
Which of the following could potentially be introduced at the time of side loading?
A security officer is implementing a security awareness program and is placing security-themed posters around the building and is assigning online user training. Which of the following would the security officer most likely implement?
The Chief Information Security Officer of an organization needs to ensure recovery from ransomware would likely occur within the organization's agreed-upon RPOs end RTOs. Which of the following backup scenarios would best ensure recovery?
A service provider wants a cost-effective way to rapidly expand from providing internet links to managing them. Which of the following methods will allow the service provider to best scale its services while maintaining performance consistency?
Cadets speaking a foreign language are using company phone numbers to make unsolicited phone calls lo a partner organization. A security analyst validates through phone system logs that the calls are occurring and the numbers are not being spoofed. Which of the following is the most likely explanation?
A company asks a vendor to help its internal red team with a penetration test without providing too much detail about the infrastructure. Which of the following penetration testing methods does this scenario describe?
A few weeks after deploying additional email servers, employees complain that messages are being marked as spam. Which needs to be updated?
Which of the following types of vulnerabilities is primarily caused by improper use and management of cryptographic certificates?
An organization wants to improve the company's security authentication method for remote employees. Given the following requirements:
• Must work across SaaS and internal network applications
• Must be device manufacturer agnostic
• Must have offline capabilities
Which of the following would be the most appropriate authentication method?
An organization is required to provide assurance that its controls are properly designed and operating effectively. Which of the following reports will best achieve the objective?
A security analyst is reviewing the security of a SaaS application that the company intends to purchase. Which of the following documentations should the security analyst request from the SaaS application vendor?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
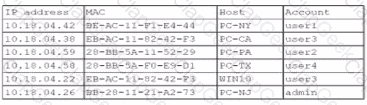
Which of the following is the most likely way a rogue device was allowed to connect?
A company is considering an expansion of access controls for an application that contractors and internal employees use to reduce costs. Which of the following risk elements should the implementation team understand before granting access to the application?
A company has yearly engagements with a service provider. The general terms and conditions are the same for all engagements. The company wants to simplify the process and revisit the general terms every three years. Which of the following documents would provide the best way to set the general terms?
Which of the following types of vulnerabilities involves attacking a system to access adjacent hosts?
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
A company is in the process of migrating to cloud-based services. The company's IT department has limited resources for migration and ongoing support. Which of the following best meets the company's needs?
A security administrator recently reset local passwords and the following values were recorded in the system:
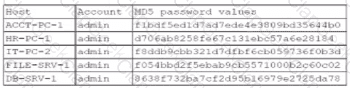
Which of the following in the security administrator most likely protecting against?
An administrator learns that users are receiving large quantities of unsolicited messages. The administrator checks the content filter and sees hundreds of messages sent to multiple users. Which of the following best describes this kind of attack?
Which of the following is a common data removal option for companies that want to wipe sensitive data from hard drives in a repeatable manner but allow the hard drives to be reused?
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
An administrator needs to perform server hardening before deployment. Which of the following steps should the administrator take? (Select two).
A group of developers has a shared backup account to access the source code repository. Which of the following is the best way to secure the backup account if there is an SSO failure?
Which of the following should a security administrator adhere to when setting up a new set of firewall rules?
A software developer would like to ensure. The source code cannot be reverse engineered or debugged. Which of the following should the developer consider?
Which of the following would be the best ways to ensure only authorized personnel can access a secure facility? (Select two).
A store is setting up wireless access for employees. Management wants to limit the number of access points while ensuring full coverage. Which tool will help determine how many access points are needed?
An analyst discovers a suspicious item in the SQL server logs. Which of the following could be evidence of an attempted SQL injection?
A security team installs an IPS on an organization's network and needs to configure the system to detect and prevent specific network attacks. Which of the following settings should the team configure first within the IPS?
Which of the following security concepts is being followed when implementing a product that offers protection against DDoS attacks?
Which of the following describes the difference between encryption and hashing?
An engineer needs to find a solution that creates an added layer of security by preventing unauthorized access to internal company resources. Which of the following would be the best solution?
Which of the following best represents an application that does not have an on-premises requirement and is accessible from anywhere?
A company's marketing department collects, modifies, and stores sensitive customer data. The infrastructure team is responsible for securing the data while in transit and at rest. Which of the following data roles describes the customer?
A company prevented direct access from the database administrators’ workstations to the network segment that contains database servers. Which of the following should a database administrator use to access the database servers?
A new employee logs in to the email system for the first time and notices a message from human resources about onboarding. The employee hovers over a few of the links within the email and discovers that the links do not correspond to links associated with the company. Which of the following attack vectors is most likely being used?
Which of the following security controls are a company implementing by deploying HIPS? (Select two).
A company's online shopping website became unusable shortly after midnight on January 30, 2023. When a security analyst reviewed the database server, the analyst noticed the following code used for backing up data:
Which of the following should the analyst do next?
A systems administrator wants to prevent users from being able to access data based on their responsibilities. The administrator also wants to apply the required access structure via a simplified format. Which of the following should the administrator apply to the site recovery resource group?
An administrator at a small business notices an increase in support calls from employees who receive a blocked page message after trying to navigate to a spoofed website. Which of the following should the administrator do?
A systems administrator receives an alert that a company's internal file server is very slow and is only working intermittently. The systems administrator reviews the server management software and finds the following information about the server:
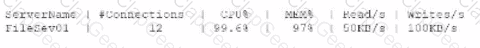
Which of the following indicators most likely triggered this alert?
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device's drive if the device is lost?
An organization has been experiencing issues with deleted network share data and improperly assigned permissions. Which of the following would best help track and remediate these issues?
Which of the following best describe why a process would require a two-person integrity security control?
A penetration tester visits a client’s website and downloads the site's content. Which of the following actions is the penetration tester performing?
Prior to implementing a design change, the change must go through multiple steps to ensure that it does not cause any security issues. Which of the following is most likely to be one of those steps?
A new security regulation was announced that will take effect in the coming year. A company must comply with it to remain in business. Which of the following activities should the company perform next?
An unknown source has attacked an organization’s network multiple times. The organization has a firewall but no other source of protection against these attacks. Which of the following is the best security item to add?
A security analyst is evaluating a SaaS application that the human resources department would like to implement. The analyst requests a SOC 2 report from the SaaS vendor. Which of the following processes is the analyst most likely conducting?
An engineer needs to ensure that a script has not been modified before it is launched. Which of the following best provides this functionality?
A company has begun labeling all laptops with asset inventory stickers and associating them with employee IDs. Which of the following security benefits do these actions provide? (Choose two.)
A company is in the process of cutting jobs to manage costs. The Chief Information Security Officer is concerned about the increased risk of an insider threat. Which of the following will most likely help the security awareness team address this potential threat?
Which of the following actions must an organization take to comply with a person's request for the right to be forgotten?
A business needs a recovery site but does not require immediate failover. The business also wants to reduce the workload required to recover from an outage. Which of the following recovery sites is the best option?
Which of the following receives logs from various devices and services, and then presents alerts?
A technician is opening ports on a firewall for a new system being deployed and supported by a SaaS provider. Which of the following is a risk in the new system?
Which of the following is an example of a data protection strategy that uses tokenization?
An organization is building a new backup data center with cost-benefit as the primary requirement and RTO and RPO values around two days. Which of the following types of sites is the best for this scenario?
The help desk receives multiple calls that machines with an outdated OS version are running slowly. Several users are seeing virus detection alerts. Which of the following mitigation techniques should be reviewed first?
After creating a contract for IT contractors, the human resources department changed several clauses. The contract has gone through three revisions. Which of the following processes should the human resources department follow to track revisions?
A penetration test identifies that an SMBvl Is enabled on multiple servers across an organization. The organization wants to remediate this vulnerability in the most efficient way possible. Which of the following should the organization use for this purpose?
Which of the following is the best reason to complete an audit in a banking environment?
A company is implementing a policy to allow employees to use their personal equipment for work. However, the company wants to ensure that only company-approved applications can be installed. Which of the following addresses this concern?
Which of the following solutions would most likely be used in the financial industry to mask sensitive data?
Which of the following tools is best for logging and monitoring in a cloud environment?
Which of the following should be used to ensure a device is inaccessible to a network-connected resource?
As part of new compliance audit requirements, multiple servers need to be segmented on different networks and should be reachable only from authorized internal systems. Which of the following would meet the requirements?
Which of the following activities should be performed first to compile a list of vulnerabilities in an environment?
Following a security review, an organization must ensure users verify their identities against the company's identity services with individual credentials leveraging WPA2-Enterprise for wireless access. Which of the following configuration steps correctly applies RADIUS in this environment?
A security analyst wants to better understand the behavior of users and devices in order to gain visibility into potential malicious activities. The analyst needs a control to detect when actions deviate from a common baseline Which of the following should the analyst use?
A security analyst has determined that a security breach would have a financial impact of $15,000 and is expected to occur twice within a three-year period. Which of the following is the ALE for this risk?
Which of the following describes the category of data that is most impacted when it is lost?
Which of the following is the most likely to be included as an element of communication in a security awareness program?
An organization has a new regulatory requirement to implement corrective controls on a financial system. Which of the following is the most likely reason for the new requirement?
A database administrator is updating the company's SQL database, which stores credit card information for pending purchases. Which of the following is the best method to secure the data against a potential breach?
A company wants to track modifications to the code used to build new virtual servers. Which of the following will the company most likely deploy?
An incident response specialist must stop a malicious attack from expanding to other parts of an organization. Which of the following should the incident response specialist perform first?
The Chief Information Security Officer (CISO) has determined the company is non-compliant with local data privacy regulations. The CISO needs to justify the budget request for more resources. Which of the following should the CISO present to the board as the direct consequence of non-compliance?
A company wants to track modifications to the code that is used to build new virtual servers. Which of the following will the company most likely deploy?
Which of the following strategies most effectively protects sensitive data at rest in a database?
An organization has recently decided to implement SSO. The requirements are to leverage access tokens and focus on application authorization rather than user authentication. Which of the following solutions would the engineering team most likely configure?
An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a “page not found” error message. Which of the following types of social engineering attacks occurred?
A systems administrator is changing the password policy within an enterprise environment and wants this update implemented on all systems as quickly as possible. Which of the following operating system security measures will the administrator most likely use?
Several employees received a fraudulent text message from someone claiming to be the Chief Executive Officer (CEO). The message stated:
“I’m in an airport right now with no access to email. I need you to buy gift cards for employee recognition awards. Please send the gift cards to following email address.”
Which of the following are the best responses to this situation? (Choose two).
A small business initially plans to open common communications ports (21, 22, 25, 80, 443) on its firewall to allow broad access to its screened subnet. However, their security consultant advises against this action. Which of the following security principles is the consultant addressing?
A security analyst receives alerts about an internal system sending a large amount of unusual DNS queries to systems on the internet over short periods of time during non-business hours. Which of the following is most likely occurring?
An organization would like to store customer data on a separate part of the network that is not accessible to users on the main corporate network. Which of the following should the administrator use to accomplish this goal?
Which of the following techniques would attract the attention of a malicious attacker in an insider threat scenario?
A security manager wants to reduce the number of steps required to identify and contain basic threats. Which of the following will help achieve this goal?
Which of the following would best allow a company to prevent access to systems from the Internet?
An organization recently started hosting a new service that customers access through a web portal. A security engineer needs to add to the existing security devices a new solution to protect this new service. Which of the following is the engineer most likely to deploy?
A systems administrator is concerned about vulnerabilities within cloud computing instances Which of the following is most important for the administrator to consider when architecting a cloud computing environment?
A company is experiencing issues with employees leaving the company for a competitor and taking customer contact information with them. Which of the following tools will help prevent this from reoccurring?
A security analyst identifies an incident in the network. Which of the following incident response activities would the security analyst perform next?
A company must ensure sensitive data at rest is rendered unreadable. Which of the following will the company most likely use?
A security team is setting up a new environment for hosting the organization's on-premises software application as a cloud-based service. Which of the following should the team ensure is in place in order for the organization to follow security best practices?
A security officer observes that a software development team is not complying with its corporate security policy on encrypting confidential data. Which of the following categories refers to this type of non-compliance?
An employee from the accounting department logs in to the website used for processing the company's payments. After logging in, a new desktop application automatically downloads on the employee's computer and causes the computer to restart. Which of the following attacks has occurred?
Which of the following is the best way to prevent data from being leaked from a secure network that does not need to communicate externally?
Which of the following can be used to mitigate attacks from high-risk regions?
After a security awareness training session, a user called the IT help desk and reported a suspicious call. The suspicious caller stated that the Chief Financial Officer wanted credit card information in order to close an invoice. Which of the following topics did the user recognize from the training?
A new vulnerability enables a type of malware that allows the unauthorized movement of data from a system. Which of the following would detect this behavior?
In which of the following will unencrypted PLC management traffic most likely be found?
A network engineer is increasing the overall security of network devices and needs to harden the devices. Which of the following will best accomplish this task?
Which of the following agreements defines response time, escalation, and performance metrics?
An administrator implements web-filtering products but still sees that users are visiting malicious links. Which of the following configuration items does the security administrator need to review?
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
Which of the following practices would be best to prevent an insider from introducing malicious code into a company's development process?
An administrator discovers a cross-site scripting vulnerability on a company website. Which of the following will most likely remediate the issue?
An IT manager informs the entire help desk staff that only the IT manager and the help desk lead will have access to the administrator console of the help desk software. Which of the following security techniques is the IT manager setting up?
A systems administrator is redesigning now devices will perform network authentication. The following requirements need to be met:
• An existing Internal certificate must be used.
• Wired and wireless networks must be supported
• Any unapproved device should be Isolated in a quarantine subnet
• Approved devices should be updated before accessing resources
Which of the following would best meet the requirements?
Which of the following is used to protect a computer from viruses, malware, and Trojans being installed and moving laterally across the network?
The Chief Information Officer (CIO) asked a vendor to provide documentation detailing the specific objectives within the compliance framework that the vendor's services meet. The vendor provided a report and a signed letter stating that the services meet 17 of the 21 objectives. Which of the following did the vendor provide to the CIO?
Which of the following is the best way to secure an on-site data center against intrusion from an insider?
A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
Which of the following is the most likely reason a security analyst would review SIEM logs?
Which of the following would best explain why a security analyst is running daily vulnerability scans on all corporate endpoints?
Which of the following enables the use of an input field to run commands that can view or manipulate data?
A company is expanding its threat surface program and allowing individuals to security test the company’s internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
A government official receives a blank envelope containing photos and a note instructing the official to wire a large sum of money by midnight to prevent the photos from being leaked on the Internet. Which of the following best describes the threat actor's intent?
While investigating a possible incident, a security analyst discovers the following log entries:
67.118.34.157 ----- [28/Jul/2022:10:26:59 -0300] "GET /query.php?q-wireless%20headphones / HTTP/1.0" 200 12737
132.18.222.103 ----[28/Jul/2022:10:27:10 -0300] "GET /query.php?q=123 INSERT INTO users VALUES('temp', 'pass123')# / HTTP/1.0" 200 935
12.45.101.121 ----- [28/Jul/2022:10:27:22 -0300] "GET /query.php?q=mp3%20players I HTTP/1.0" 200 14650
Which of the following should the analyst do first?
A systems administrator needs to ensure the secure communication of sensitive data within the organization's private cloud. Which of the following is the best choice for the administrator to implement?
A customer reports that software the customer downloaded from a public website has malware in it. However, the company that created the software denies any malware in its software at delivery time. Which of the following techniques will address this concern?
Which of the following is a social engineering attack in which a bad actor impersonates a web URL?
An employee decides to collect PII data from the company's system for personal use. The employee compresses the data into a single encrypted file before sending the file to their personal email. The security department becomes aware of the attempted misuse and blocks the attachment from leaving the corporate environment. Which of the following types of employee training would most likely reduce the occurrence of this type of issue?
(Select two).
Which of the following documents details how to accomplish a technical security task?
Which of the following would be the best way to test resiliency in the event of a primary power failure?
A recent penetration test identified that an attacker could flood the MAC address table of network switches. Which of the following would best mitigate this type of attack?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
A security administrator observed the following in a web server log while investigating an incident:

Which of the following attacks did the security administrator most likely see?
An employee clicked a malicious link in an email and downloaded malware onto the company's computer network. The malicious program exfiltrated thousands of customer records. Which of the following should the company implement to prevent this in the future?
A company's end users are reporting that they are unable to reach external websites. After reviewing the performance data for the DNS severs, the analyst discovers that the CPU, disk, and memory usage are minimal, but the network interface is flooded with inbound traffic. Network logs show only a small number of DNS queries sent to this server. Which of the following best describes what the security analyst is seeing?
A network administrator deploys an FDE solution on all end user workstations. Which of the following data protection strategies does this describe?
Which of the following describes the procedures a penetration tester must follow while conducting a test?
An analyst is evaluating the implementation of Zero Trust principles within the data plane. Which of the following would be most relevant for the analyst to evaluate?
Which of the following is a type of vulnerability that involves inserting scripts into web-based applications in order to take control of the client's web browser?
During a penetration test, a vendor attempts to enter an unauthorized area using an access badge Which of the following types of tests does this represent?
An organization needs to monitor its users' activities to prevent insider threats. Which of the following solutions would help the organization achieve this goal?
A security analyst is creating the first draft of a network diagram for the company's new customer-facing payment application that will be hosted by a third-party cloud service
provider.
A Chief Information Security Officer would like to conduct frequent, detailed reviews of systems and procedures to track compliance objectives. Which of the following is the best method to achieve this objective?
Which of the following topics would most likely be included within an organization's SDLC?
A company wants to reduce the time and expense associated with code deployment. Which of the following technologies should the company utilize?
Which of the following is the best way to remove personal data from a social media account that is no longer being used?
A security manager created new documentation to use in response to various types of security incidents. Which of the following is the next step the manager should take?
Which of the following is the primary purpose of a service that tracks log-ins and time spent using the service?
An organization wants a third-party vendor to do a penetration test that targets a specific device. The organization has provided basic information about the device. Which of the following best describes this kind of penetration test?
A company relies on open-source software libraries to build the software used by its customers. Which of the following vulnerability types would be the most difficult to remediate due to the company's reliance on open-source libraries?
Which of the following actions best addresses a vulnerability found on a company's web server?
Which of the following types of identification methods can be performed on a deployed application during runtime?
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
The private key for a website was stolen, and a new certificate has been issued. Which of the following needs to be updated next?
An administrator must replace an expired SSL certificate. Which of the following does the administrator need to create the new SSL certificate?
After multiple phishing simul-ations, the Chief Security Officer announces a new program that incentivizes employees to not click phishing links in the upcoming quarter. Which of the following security awareness execution techniques does this represent?
A company discovers suspicious transactions that were entered into the company's database and attached to a user account that was created as a trap for malicious activity. Which of the following is the user account an example of?