When adding a new search head to a search head cluster (SHC), which of the following scenarios occurs?
A customer has written the following search:
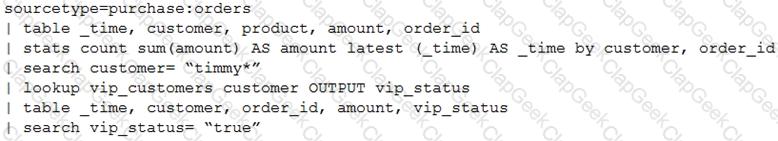
How can the search be rewritten to maximize efficiency?
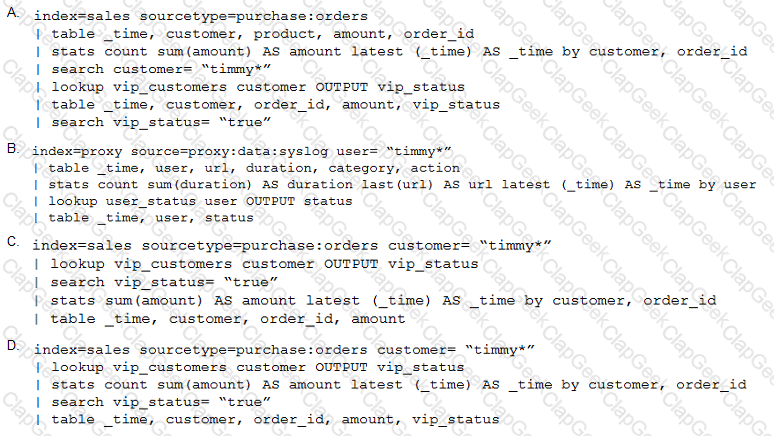
A customer is using both internal Splunk authentication and LDAP for user management.
If a username exists in both $SPLUNK_HOME/etc/passwd and LDAP, which of the following statements is accurate?
How does Monitoring Console (MC) initially identify the server role(s) of a new Splunk Instance?
A customer wants to implement LDAP because managing local Splunk users is becoming too much of an overhead. What configuration details are needed from the customer to implement LDAP authentication?
A customer has been using Splunk for one year, utilizing a single/all-in-one instance. This single Splunk server is now struggling to cope with the daily ingest rate. Also, Splunk has become a vital system in day-to-day operations making high availability a consideration for the Splunk service. The customer is unsure how to design the new environment topology in order to provide this.
Which resource would help the customer gather the requirements for their new architecture?


