You update a props. conf file while Splunk is running. You do not restart Splunk and you run this command: splunk btoo1 props list —debug. What will the output be?
Consider the following stanza ininputs.conf:
What will the value of the source filed be for events generated by this scripts input?
Which setting allows the configuration of Splunk to allow events to span over more than one line?
Which of the following monitor inputs stanza headers would match all of the following files?
/var/log/www1/secure.log
/var/log/www/secure.l
/var/log/www/logs/secure.logs
/var/log/www2/secure.log
The following stanza is active in indexes.conf:
[cat_facts]
maxHotSpanSecs = 3600
frozenTimePeriodInSecs = 2630000
maxTota1DataSizeMB = 650000
All other related indexes.conf settings are default values.
If the event timestamp was 3739283 seconds ago, will it be searchable?
Which feature of Splunk’s role configuration can be used to aggregate multiple roles intended for groups of
users?
Which data pipeline phase is the last opportunity for defining event boundaries?
When using a directory monitor input, specific source types can be selectively overridden using which configuration file?
An admin updates the Role to Group mapping for external authentication. How does the change affect users that are currently logged into Splunk?
Who provides the Application Secret, Integration, and Secret keys, as well as the API Hostname when setting
up Duo for Multi-Factor Authentication in Splunk Enterprise?
Which Splunk component would one use to perform line breaking prior to indexing?
Seven different network switches are sending traffic to a server hosting a Universal Forwarder. Three of the devices are sending TCP data and four of the devices are sending UDP data.
What is the minimum number of input stanzas that must be created on the Universal Forwarder to successfully capture data from all seven sources?
Which of the following CLI commands removes a search peer from Distributed Search?
Which of the following are required when defining an index in indexes. conf? (select all that apply)
In which scenario would a Splunk Administrator want to enable data integrity check when creating an index?
When deploying apps, which attribute in the forwarder management interface determines the apps that clients install?
A Universal Forwarder is collecting two separate sources of data (A,B). Source A is being routed through a Heavy Forwarder and then to an indexer. Source B is being routed directly to the indexer. Both sets of data require the masking of raw text strings before being written to disk. What does the administrator need to do to
ensure that the masking takes place successfully?
What is the importance of modifying Transparent Huge Pages (THP) and ulimit settings when installing Splunk Enterprise?
Where can scripts for scripted inputs reside on the host file system? (select all that apply)
All search-time field extractions should be specified on which Splunk component?
Which configuration file would be used to forward the Splunk internal logs from a search head to the indexer?
During search time, which directory of configuration files has the highest precedence?
Which of the following is the use case for the deployment server feature of Splunk?
Within props. conf, which stanzas are valid for data modification? (select all that apply)
In case of a conflict between a whitelist and a blacklist input setting, which one is used?
User role inheritance allows what to be inherited from the parent role? (select all that apply)
A Splunk administrator has been tasked with developing a retention strategy to have frequently accessed data sets on SSD storage and to have older, less frequently accessed data on slower NAS storage. They have set a mount point for the NAS. Which parameter do they need to modify to set the path for the older, less frequently accessed data in indexes.conf?
Which of the following enables compression for universal forwarders in outputs. conf ?
A)
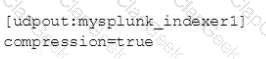
B)

C)
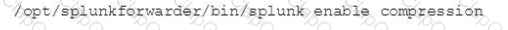
D)

Which file will be matched for the following monitor stanza in inputs. conf?
[monitor: ///var/log/*/bar/*. txt]
Which of the following accurately describes HTTP Event Collector indexer acknowledgement?
Which Splunk component(s) would break a stream of syslog inputs into individual events? (select all that apply)
UsingSEDCMDinprops.confallows raw data to be modified. With the given event below, which option will mask the first three digits of theAcctIDfield resulting output:[22/Oct/2018:15:50:21] VendorID=1234 Code=B AcctID=xxx5309
Event:
[22/Oct/2018:15:50:21] VendorID=1234 Code=B AcctID=xxx5309
What event-processing pipelines are used to process data for indexing? (select all that apply)
Which scenario is applicable given the stanzas in authentication.conf below?
[authentication]
externalTwoFactorAuthVendor = Duo
externalTwoFactorAuthSettings = duoMFA
[duoMFA]
integrationKey = aGFwcHliaXJ0aGRheU1pZGR5
secretKey = YXVzdHJhaWxpYW5Gb3JHcmVw
applicationKey = c3BsaW5raW5ndGhlcGx1bWJ1c3NpbmN1OTU
apiHostname = 466993018.duosecurity.com
failOpen = True
timeout = 60
When deploying apps on Universal Forwarders using the deployment server, what is the correct component and location of the app before it is deployed?
An index stores its data in buckets. Which default directories does Splunk use to store buckets? (Choose all that apply.)
There is a file with a vast amount of old data. Which of the following inputs.conf attributes would allow an admin to monitor the file for updates without indexing the pre-existing data?


