Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
Click the Exhibit button.
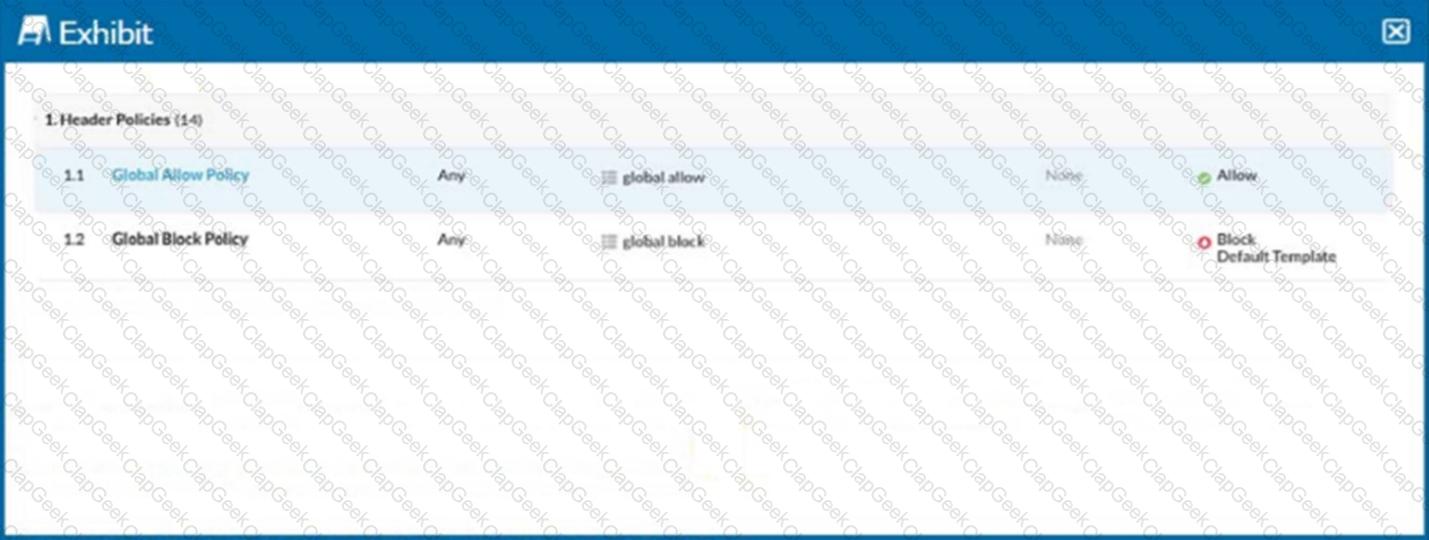
Referring to the exhibit, you have a user reporting that a blocked website is needed for legitimate business reasons. Upon review, you determine that the user has been blocked by the Global Block policy. You need to create an exception forthat domain. You create a custom URL list that includes the domain.
In this scenario, which two actions would allow this access? (Choose two.)
Which three technologies describe the primary cloud service models as defined by the National Institute of Standards and Technology (NIST)? (Choose three.)
A company user cannot open a sports news site. You want to review the category of the website and see how the rules are applied even though this category is allowed. In this scenario, which action will accomplish this task?
Click the Exhibit button.
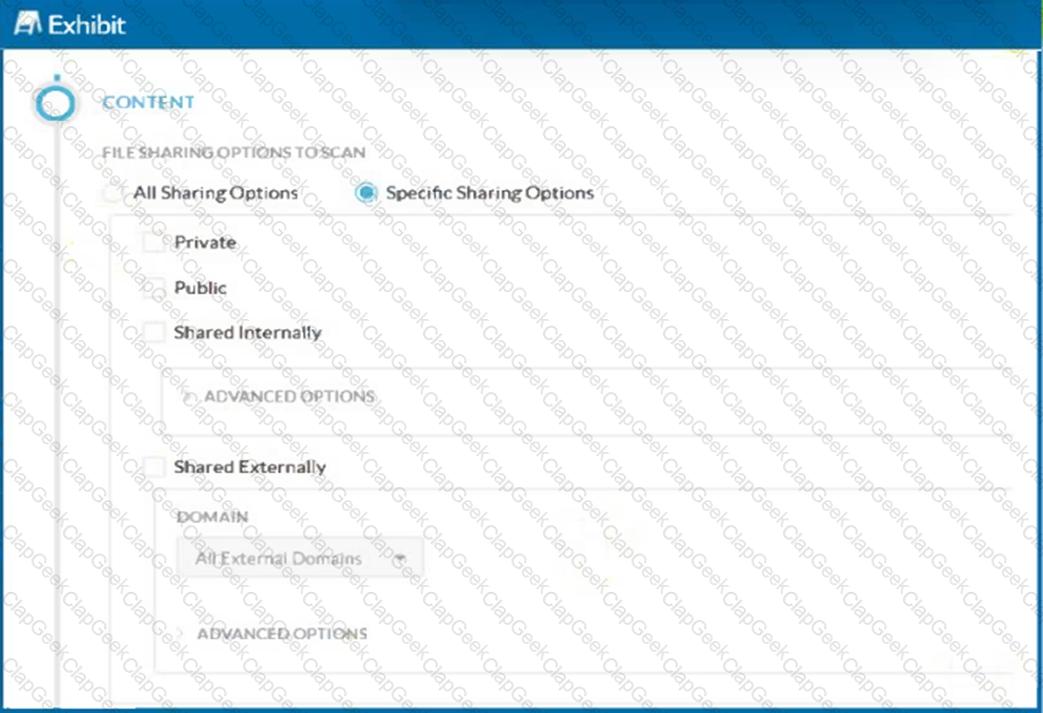
A customer has created a CASB API-enabled Protection policy to detect files containing sensitive data that are shared outside of their organization.
Referring to the exhibit, which statement is correct?
Which three statements about Netskope Private Access Publishers are correct? (Choose three.)
Which Netskope platform component uses NewEdge Traffic Management for traffic steering?
Which two cloud security and infrastructure enablement technologies does Secure Access Service Edge (SASE) combine into its unified platform? (Choose two.)
Which two functions are available for both inline and API protection? (Choose two.)
You are working with a large retail chain and have concerns about their customer data. You want to protect customer credit card data so that it is never exposed in transit or at rest. In this scenario, which regulatory compliance standard should be used to govern this data?
You need to block all users from uploading data files into risky collaboration applications. Which element must you configure within Netskope's CASB to accomplish this task?
Which three statements are correct about Netskope's NewEdge Security Cloud Network Infrastructure? (Choose three.)
You want to determine which NewEdge data planes that your remote users have been recently using.
Which area of the Netskope Tenant UI would provide this information?
An administrator wants to determine to which data plane a user is traversing. In this scenario, what are two ways to accomplish this task? (Choose two.)
A user has performed a bulk delete activity. In this scenario, which Netskope feature monitors potential risky users for a malicious activity that would cause data loss?
You determine that a business application uses non-standard HTTPS ports. You want to steer all HTTPS traffic for this application and have visibility and control over user activities.
Which action will allow you to accomplish this task?
How does a cloud security solution achieve visibility into TLS/SSL-protected Web traffic?
Which two statements describe a website categorized as a domain generated algorithm (DGA)? (Choose two.)
What are two fundamental differences between the inline and API implementation of the Netskope platform? (Choose two.)
Your organization has implemented Netskope Private Access (NPA) for all users. Users from the European region are reporting that they are unable to access many of their applications. You suspect that the publishers for the European data center may be disconnected and you want to verify the Publishers' status.
Which two methods describe how you would accomplish this task? (Choose two.)
Click the Exhibit button.
What are two use cases where the parameter shown in the exhibit is required? (Choose two.)
Which two technologies form a part of Netskope's Threat Protection module? (Choose two.)
Which two statements are correct about DLP Incidents in the Netskope platform? (Choose two.)
Exhibit
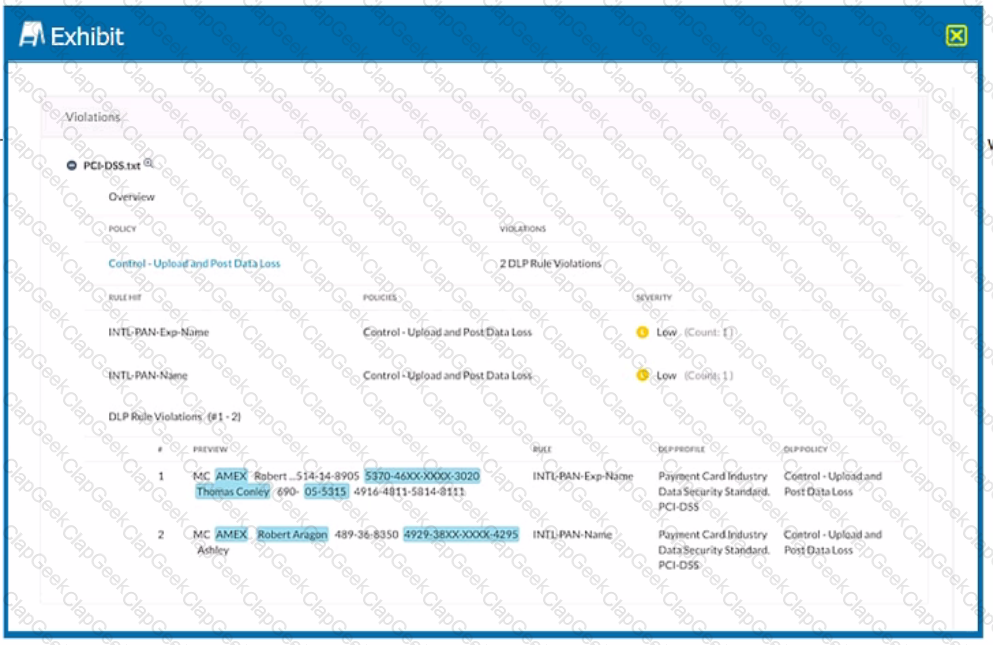
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
You are required to present a view of all upload activities completed by users tunneled from the Los Angeles office to cloud storage applications.
Which two basic filters would you use on the SkopeIT Applications page to satisfy this requirement? (Choose two.)
All users are going through Netskope's Next Gen SWG. Your CISO requests a monthly report of all users who are accessing cloud applications with a "Low" or a "Poor" CCL, where the activity is either "Edit" or "Upload".
Using the Advanced Analytics interface, which two statements describe which actions must be performed in this scenario? (Choose two.)
Your company asks you to obtain a detailed list of all events from the last 24 hours for a specific user. In this scenario, what are two methods to accomplish this task? (Choose two.)
Click the Exhibit button.
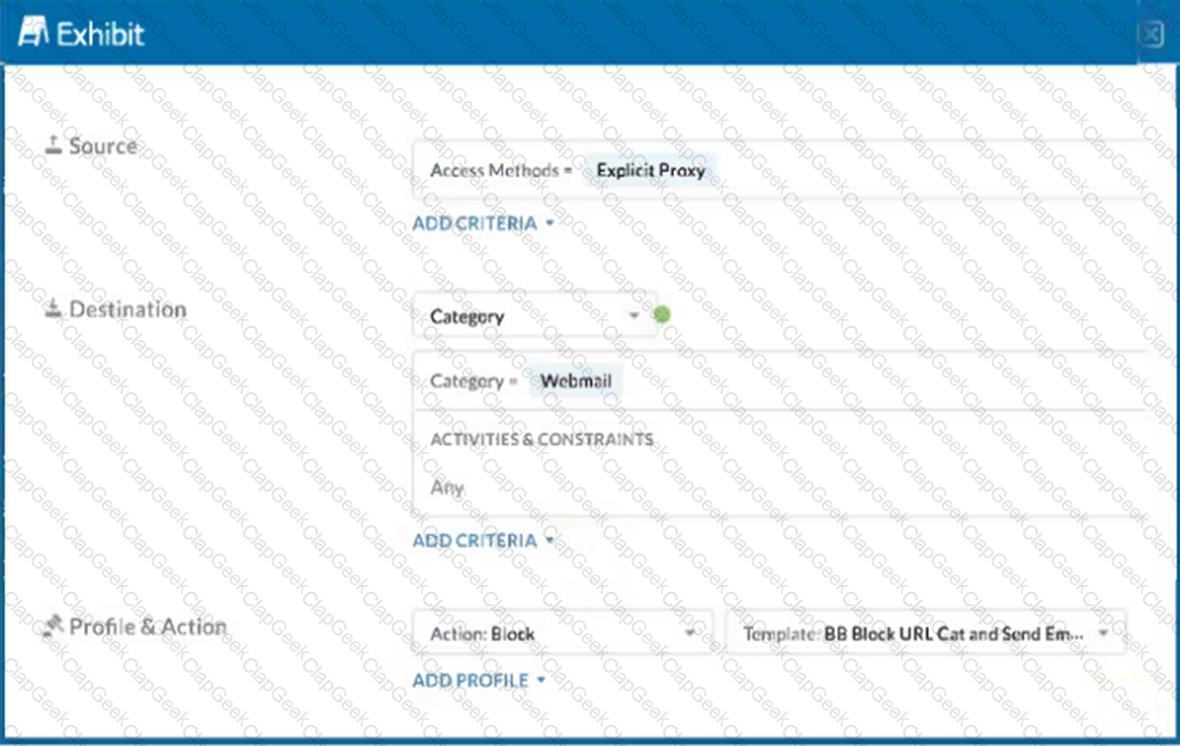
A user has the Netskope Client enabled with the correct steering configuration applied. The exhibit shows an inline policy that has a predefined webmail category blocked. However the user is still able to access Yahoo mail.
Which statement is correct in this scenario?


