A company recently added an addition to their office building. A technician runs new plenum network cables from the switch on one side of the company's gymnasium 80 meters (262 ft.) to the new offices on the other side, draping the wires across the light fixtures. Users working out of the new offices in the addition complain of intermittent network connectivity. Which of the following is MOST likely the cause of the connectivity issue?
A firewall that detects and prevents attacks from outside the network based on learned data patterns can BEST be described as which of the following?
A user is unable to connect to a remote computer using RDP. The technician checks the firewall rules and notes that there is no rule that blocks RDP. Which of the following features of the firewall is responsible for blocking RDP?
A technician is terminating a new run of network cables to a 110 block. Which of the following tools would the technician use?
Which of the following network monitoring resources would be used to analyze possible connectivity issues such as duplex mismatches and uptime statistics?
A new technician has been tasked with implementing a QoS policy for the Network. The technician decides it would be best to monitor the information traversing the network to gain statistical information on ports and protocols utilized. Which of the following tools should the technician use to complete this objective QUICKEST?
A technician is looking to create a new network cable. Which of the following tools would assist in creating and testing a cable properly? (Select TWO).
An IP camera has a failed PoE NIC. This is the third time in months that a PoE NIC has failed on this device. The technician suspects a possible power issue. Which of the following should be used to test the theory?
An administrator is using a packet sniffer to try to determine what is causing the traffic on the network. The administrator sees a lot of packets on port 25. Which of the following traffic types is MOST likely using port 25?
Which of the following protocols is MOST commonly used for the transfer of router configuration files?
A company pays a third-party vendor a monthly fee to connect to offsite servers and desktops. Users connect to the desktops via RDP, and administrators connect to the servers via VPN. Servers and desktops are hardware-based. Which of the following is the third-party providing?
A technician, Joe, visits a site that has reported a network down emergency. He immediately reboots the switches and the router since the network is down. Which of the following network troubleshooting methodology steps should Joe have performed FIRST?
A network technician is troubleshooting signal problems with certain WAPs in an office and finds consistently high ping times across the units. Such an issue is called which of the following?
Which of the following OSI model layers is used to frame packets that are sent over a medium?
An administrator is able to list the interfaces on a switch after providing the community string "public". Which of the protocols is the administrator MOST likely using?
Which of the following dynamic routing protocols selects routing paths based upon hop count?
Which of the following OSI model layers are present in the application layer of the TCP/IP model? (Select TWO).
Using source port numbers as a way to keep track of connections is a characteristic of which of the following protocols?
A network administrator notices that load balancing is not working properly on the web cluster as previously configured. In speaking with management, a change to the IP addressing scheme was made yesterday which possibly affected one member of the cluster. Due to the timing of the events, the administrator theorizes that this change caused the problem. Which of the following should the administrator do NEXT?
The address 6FFE:FFFF:0000:2F3B:04AC:00FF:FEBE:5C4A is an example of which of the following?
Which of the following network protocols is used to transport email across the Internet?
An administrator needs to provide remote connectivity to server1, web traffic to server2, and FTP access to server3 using a single outside IP address. Which of the following would the administrator implement on the firewall to accomplish this?
Which of the following allows for groups of ports on the same switch to operate as a part of different segmented networks?
A network manager is interested in a device that watches for threats on a network but does not act on its own, and also does not put a strain on client systems. Which of the following would BEST meet these requirements?
A company wants to have a security zone to isolate traffic within the firewall. Which of the following could be used?
Which of the following would be the BEST solution for an IDS to monitor known attacks?
Which of the following should be mitigated by employing proper coding techniques when developing software?
An unusual amount of activity is coming into one of the switches in an IDF. A malware attack is suspected. Which of the following tools would appropriately diagnose the problem?
Users at a remote site are unable to establish a VPN to the main office. At which of the following layers of the OSI model does the problem MOST likely reside?
Which of the following attacks would allow an intruder to do port mapping on a company’s internal server from a separate company server on the Internet?
Which of the following would be used in a firewall to block incoming TCP packets that are not from established connections?
An administrator would like to search for network vulnerabilities on servers, routers, and embedded appliances. Which of the following tools would MOST likely accomplish this?
Which of the following is the default authentication method for a Windows client using PPP over a dialup connection?
A user at a hotel sees two SSIDs; both are called "HotelWireless". After the PC connects to one of the APs, the user notices their browser homepage has been changed. Which of the following BEST describes this AP?
Which of the following can use a third party back-end LDAP user database for authentication?
Which of the following would a network administrator MOST likely use to actively discover unsecure services running on a company’s network?
Many of the corporate users work from a coffee shop during their lunch breaks. The coffee shop only has an open wireless network. Which of the following should the administrator recommend to users to secure their wireless communications at the coffee shop?
A user reports that they are unable to access a new server but are able to access all other network resources. Based on the following firewall rules and network information, which of the following ACL entries is the cause?
User’s IP: 192.168.5.14
Server IP: 192.168.5.17
Firewall rules:
Permit 192.168.5.16/28192.168.5.0/28
Permit 192.168.5.0/24192.168.4.0/24
Permit 192.168.4.0/24192.168.5.0/24
Deny 192.168.5.0/28192.168.5.16/28
Deny 192.168.14.0/24192.168.5.16/28
Deny 192.168.0.0/24192.168.5.0/24
Ann, a user, connects to her company’s secured wireless network in the conference room when attending meetings. While using the conference room this morning, Ann notices an unsecured wireless network with the same name is available. Ann connects her laptop to this network instead of to the secured one. Ann has fallen victim to which of the following threats?
A network administrator is considering implementation of network access restrictions based upon layer two addressing information. Which of the following describes this method of network restrictions?
Which of the following wireless router security measures provides access to a network by allowing only devices on an approved physical address list?
Which of the following will BEST block a host from accessing the LAN on a network using static IP addresses?
A network administrator is implementing an IPS on VLAN 1 and wants the IPS to learn what to prevent on its own. Which of the following would MOST likely be installed?
A company wants to secure its WAPs from unauthorized access. Which of the following is the MOST secure wireless encryption method?
Which of the following TCP/IP model layers does the OSI model Presentation layer map to?
A SOHO client has tasked Joe, a technician, with setting up a basic SOHO network to support four laptops and one desktop PC. The client would also like to have a basic wireless network to use for internal devices only that is secure. Given the list of requirements, which of the following devices would Joe need to purchase for his client? (Select TWO).
Which of the following is MOST commonly implemented for remote access to UNIX systems?
Which of the following tools would a technician use to determine if a CAT6 cable is properly terminated?
The day network administrator is having problems on the network and realizes that the night administrator implemented a new device that is causing broadcast traffic. Which of the following should be implemented to avoid miscommunication between the administrators?
A technician is having trouble identifying a computer on a network. The technician has the IP address of the computer, but needs to find the hostname of the computer. Which of the following commands should the technician use?
Which of the following can be used to prioritize network streams to optimize performance for certain traffic types?
An administrator is trying to retrieve management information from the network devices on their LAN. Which of the following monitoring resources provides the ability to collect this information encrypted over the network?
An organization finds that most of the outgoing traffic on the network is directed at several Internet sites viewed by multiple computers simultaneously. Which of the following performance optimization methods would BEST alleviate network traffic?
A technician has traced a POTS line to a 110 block. Which of the following devices would the technician MOST likely use to see if the line carries a dial tone?
Which of the following tools would a technician use to terminate CAT6 wires to the inside of the wall jack?
A computer has lost network connectivity. The network technician determines the network cable and the cable drop are both good. Which of the following would the technician use to test the computer’s NIC?
A network administrator wants to see what ports are open on a server. Which of the following commands will show open ports?
Joe, a remote user, has called the helpdesk with an issue on his machine. The technician would like to remote into the machine for troubleshooting but does not know the IP address or host name. Which of the following commands can the technician ask Joe to execute to gain this information?
Users inform an administrator that the network is slow. The administrator notices the bulk of the traffic is SIP and RTP traffic. Which of the following could the administrator do to help BEST alleviate the traffic congestion for the users?
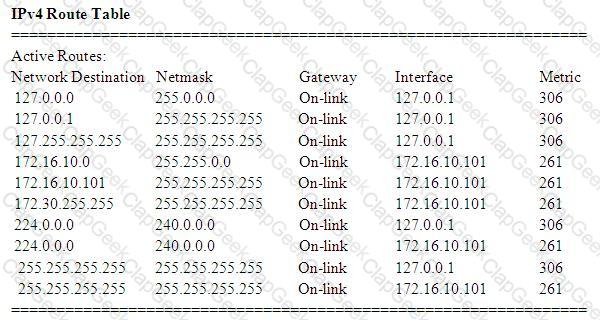
A technician is troubleshooting Internet connectivity for a PC. Which of the following is MOST likely the reason for Internet connectivity issues upon inspecting the routing table?
A technician has been tasked with planning and implementing a new wired-only network for a small office. A hardware list has been compiled, but the technician is unsure about the final necessary item. Which of the following will BEST complete the small wired network setup?
(1) 1000 foot CAT6 spool
(1) crimper
(1) 16 port gigabit switch
(20) RJ-45 connectors
(12) RJ-45 wall jacks
(1) ____________
A network technician is trying to run a protocol analyzer and is instructed to record the chimney offload state of TCP. Which of the following utilities did the technician use to check this parameter with the output listed below?
Querying active state...
TCP Global Parameters
----------------------------------------------
Receive-Side Scaling State : enabled
Chimney Offload State : disabled
Receive Window Auto-Tuning Level : normal
Add-On Congestion Control Provider : ctcp
ECN Capability : disabled
RFC 1323 Timestamps : disabled
A network technician is assigned to view websites that a user has visited. Which of the following should the technician review to find this information?
A company has been just opened a new site in another country. Both sites share information across the WAN continuously throughout the business day. Which of the following should be implemented to ensure both sites are accessible?
A Chief Executive Officer (CEO) decided that only a limited number of authorized company workstations will be able to connect to the Internet. Which of the following would BEST accomplish this goal?
Which of the following 802.11 standards transmits the signals the GREATEST distance?
A technician has been called about intermittent connectivity near IDF 2. Multiple cables were recently pulled through a common conduit. Which of the following is MOST likely the cause of the problem?
Which of the following cables would BEST be used to extend a network through an 80 feet (262 meters) machine shop that has many high voltage machines and generators running?
An administrator has added four switches to a campus network. The switch in wiring closet A is only connected to the switch in wiring closet C. The switch in wiring closet B is connected to the switch in wiring closet C as well as wiring closet D. The switch in wiring closet D is only connected to the switch in wiring closet B. Which of the following topologies is represented in this design?
Which of the following technologies allows multiple staff members to connect back to a centralized office?
A technician is tasked with replacing some older RS-232 serial printers. Which of the following ports would the technician most likely find on these printers?
A technician is assigned the task of connecting two buildings 125 meters apart (410 ft.). Which of the following cable types should the technician consider?
While preparing to replace an old CAT3 cable with a CAT6 cable to implement VoIP, a facilities employee mistakenly disconnects the entire patch panel, including valid wiring to live workstations. Which of the following should an administrator use in order to connect those ports FIRST?
A technician is troubleshooting a problem where data packets are being corrupted. Which of the following connectivity problems should the technician check?
A network administrator needs to ensure there is no same channel interference for an 802.11n deployment with four WAPs. Which of the following channel setting configurations meets this criteria when using 40 MHz channels?
Which of the following defines the pinout of an 8P8C eight pin modular jack for a CAT6a cable?
Which of the following connector types is MOST commonly used for serial connections?
A user would like to connect two laptops together and transfer files via the Ethernet ports. Which of the following should MOST likely be provided to the user to accomplish this?
The network technician is troubleshooting a connectivity issue on a CAT5 cable with a wire map and notices that only pins 1, 3, and 6 are mapping correctly. Which of the following pins are open and keeping traffic from flowing correctly?
Which of the following characteristics allows an 802.11g WAP to have transfer speeds up to 108Mbps?
A technician needs to restrict access to a SOHO wireless network to specific devices. Which of the following would MOST likely be used with minimal client configuration?
A company has recently allowed its employees to telecommute two days a week. The employees MUST have a minimum of 1Mbps non-shared connection to the Internet. Which of the following MUST the employees have at their home in order to connect to the Internet?
Joe, a vendor, walks into a customer’s site with a laptop. While waiting for his contact to arrive, he wants to check his email. He discovers the SSID for the site’s wireless network and receives a valid guest password from the receptionist. He is, however, unable to connect. Which of the following is MOST likely the problem?
Which of the following is the BEST way to prevent new users from connecting to a wireless access point, but still allow already connected users to continue to connect?
A customer's email server is not sending emails. Arrange the troubleshooting steps in the order the technician should perform them:

A network administrator is tasked with deploying a company-wide wireless system which allows for accurate tracking of employees’ wireless device locations via WAP triangulation. Which of the following is the MOST important aspect of the deployment?
A user calls the helpdesk to report not being able to access network resources over the company’s Wi-Fi connection. During information gathering, the user mentions that the wireless network their computer is signed into is not the same name as it had been previously. Which of the following is the underlying cause?
A network technician is setting up a wireless access point that would only allow a certain laptop to be able to access the WAP. By using ACL, which of the following would be filtered to ensure only the authorized laptop can access the WAP?
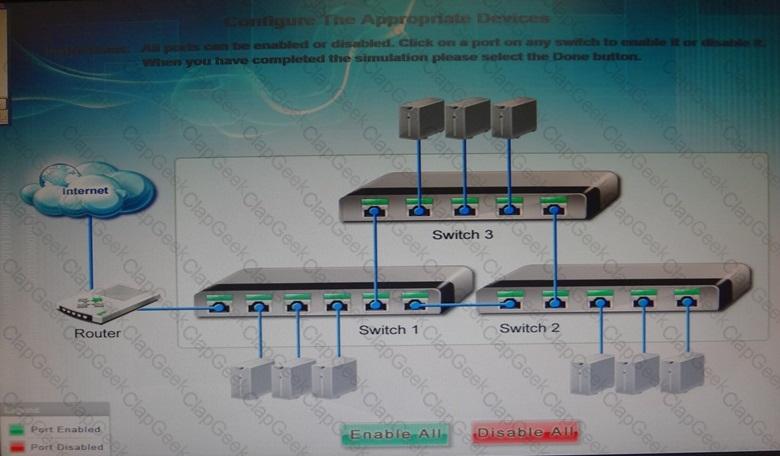
Workstations are unable to access the internet after a recent power outage. Configure the appropriate devices to ensure All workstations have internet connectivity.
Ann, a technician, is installing network cables for an office building. Some of the cables are not showing active on the switch even when moved to different ports. Which of the following is MOST likely the cause?
An IP address assigned from a DHCP server is said to be which of the following?
An administrator has created several virtual machines on the same host server and requires them to each be on separate VLANs. Which of the following should the administrator configure to meet this goal?
Linking two or more switches together so that they can share VLAN information is known as which of the following?
A new technician has moved the wireless access point from the middle of the office to an area near a corner office. Wireless users are MOST likely to experience issues with which of the following?
A stateful point to point wireless connection going down for a few hours at a time is MOST likely due to which of the following?
A client has just leased a new office space in a busy commercial building and would like to install a wireless network. Several other tenants are on the same floor. Multiple wireless networks are present in the building. Which of the following can be changed on the client’s wireless network to help ensure that interference from other wireless networks is at a minimum?
Which of the following wireless parameters may need to be modified when a new cordless telephone is installed?
A network has a large number of users who connect for short periods of time and the network needs to maximize the number of devices that can be configured using DHCP. Which of the following should be configured to solve this issue?
Several users are reporting that they are unable to connect to the network. After further investigation, the network administrator notices that a newly configured Layer 2 device lost its configuration. Which of the following MOST likely caused the issue?
Which of the following is the reason why a company’s network may contain a DHCP server?
A network technician needs to configure a port on a switch to provide connectivity and electrical support to a WAP being installed in a warehouse. Which of the following features needs to be configured on the switch?
After deploying a network switch, the network administrator is unable to remotely administer the device. The network administrator notices that the switch has the following configuration. Which of the following is the MOST likely cause of this issue?
Management LAN: 192.168.10.0/24
Management interfacE. 192.168.10.2 255.255.255.0
Default gateway: 192.168.11.1
STP is enabled
During business hours, users at a small office are reporting that all of a sudden they are unable to reach any host on the Internet, but they can still use the network shares to transfer files within the office. Which of the following is the MOST likely cause of the outage?