In FusionCompute, the user can set the priority for each member port in a port group.
Which of the following statements are true about the differences between OpenStack and FusionCompute?
Desktop users on the same FusionAccess can be authenticated using different domains.
Which of the following statements are true about high-fidelity audio and video based on Huawei Desktop Protocol (HDP)?
Match the emerging technologies with their respective features or application scenarios

With centralized storage, all physical disks are centrally deployed in disk enclosures and provide storage services externally through the controller.
There are two types of virtual switches. FusionCompute uses ___, which can be distributed on different physical hosts and configured in a unified manner using the virtualization management tool. (Enter the abbreviation.)
Virtualization is the fundamental technology powering cloud computing. It is the act of creating a virtual version of something and a logical representation of physical resources. It allows resource simulation, isolation, and sharing.
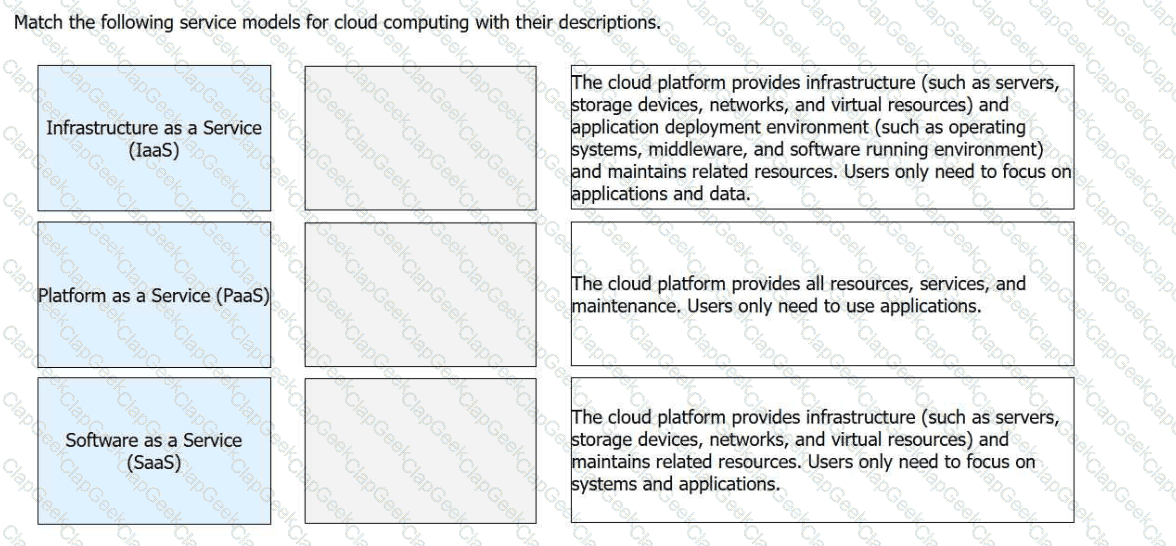
Match the following service models for cloud computing with their descriptions.
When FusionAccess is running properly, you are advised to restart infrastructure VMs once every quarter during off-peak hours. You can run the reboot command to restart Linux infrastructure VMs at the same time.
Which of the following statements is false about a Virtual Image Management System (VIMS) file system?
Generally, a subnet mask is used together with an IP address. The 0s in the binary value represent the network portion of an IP address, and the 1s represent the host portion.
When a user VM uses a USB device, FusionAccess defaults to "USB Port Redirection". If the device is still unavailable, the"Device Redirection"policy can be configured.
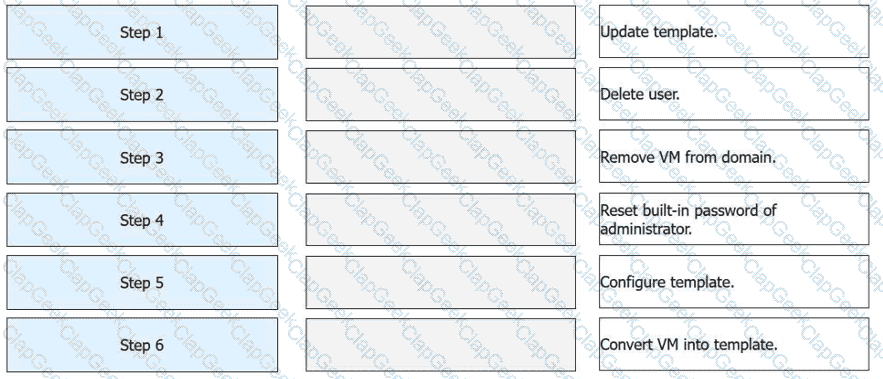
FusionAccess can use a provisioned full copy VM as a full copy VM template. Place the following operations in the correct order.
During the deployment of the FusionAccess gateway and load balancer, the HA status is abnormal after vAG/vLB configuration. Which of the following is not a possible cause of this fault?
The following table lists the FusionAccess environment plan. Which of the following network segments is the most suitable for deploying FusionAccess Linux infrastructure VMs?

On FusionAccess software deployment, if multiple FusionAccess systems share a License, the License component should be deployed independently.
When an administrator uses alinked clone templateto quickly provision virtual machines (VMs) on FusionAccess, which of the following are thesteps of the quick provision process?
The application scenarios of FusionAccess include secure offices, public terminals, general offices, and GPU graphics. Which of the following desktop types ismost suitable for new media operations?
Which of the following statements isfalseabout High Availability (HA) in Huawei FusionCompute?
On FusionAccess, modifying or deleting a full copy template will affect the virtual machines created using the template.
The kernel is an essential part of the operating system (OS). It is used to manage computer hardware resources and provide a system call interface to run upper-layer application programs.
Two virtual machines run on the same host and are in the same network segment, but they cannot communicate with each other. Which of the following isnota possible cause?
Hypervisor is the key to virtualize compute resources.7Which of the following is also called a hypervisor?


