Which of the following is not part of the changing trend in cyberattacks? (Single selection)
Verify user-provided data in the form of whitelists or blacklists, and construct SQL sentences So that user-supplied data cannot affect the logic of the statement This protects against SQL injection attacks.
When a user terminates the use of HUAWEI CLOUD services, as a service provider, we should ensure the security of user data operations.
The IPS function of Huawei's intrusion prevention device is not controlled by License (radio selection).
As TRUE
B. FALSE
Digital signature technology can guarantee the credibility of the data source and verify whether the data has been tampered with during transmission. (Single selection)
Formatting your computer means that the files have been completely erased Unable to fix.
Which options below are the main changes in Equal Protection 2.0 compared to Equal Protection 1.0' (multiple choices).
Which of the following options allows complete destruction of data, (multiple selection)
The following describes the hot standby of the dual machine What are the wrong items? (multiple selection).
Which of the following services are security management services in HUAWEI CLOUD solutions?
If the attributes of the file all match the match conditions of the rule Then this file successfully matches the rules for the file to be overmixed with the poppy file. If one of the conditions does not match • The next rule continues to be matched, and so on If all the rules do not match FW will discard the file o (single selection).
When using server authentication Before visiting the business, the visitor first logs in through the client or potal authentication page The firewall then proactively obtains the user's login information (including the username and IP address used by the visitor) from the server (single selection).
Let's take the L2TP over IPSec in the dual-machine scenario What is wrong with the description is the egg? (single selection).
Which of the following options fall under the Security Manager requirements in Graded Protection 2.0? A Grading and filing
B. System administration
C. Audit management
D. Centralized control
In the following description of the principles of network trapping defense, which are correct? (multiple selection).
The signature filter will batch out signatures, and usually set to a uniform action for ease of management. If an app wants to treat it differently You can also use exception signatures to match O's from signature filters
The following describes how to create a trap account Which one is correct? (single selection).
Create a local account named Administrator and set its permissions to the most, plus a strong password of more than 10 digits
Create a local account named Administrator and set its permissions to the minimum, plus a weak password less than 6 digits
Create a local account named Administrator and set its permissions to the minimum, plus a strong password of more than 10 digits
D. Create a local account named Administrator and set its permissions to maximum Plus a weak password less than 6 digits
If you want to intelligently select traffic for the source IP address, you can use which of the following intelligent routing methods^ (single selection).
The following describes FW's application behavior control features Which one is correct? (single selection).
The following is a description of traceability audits Which one is correct? (single selection).
Categorize vulnerabilities by common ways Which of the following types of vulnerabilities should XSS fall into? (single selection).
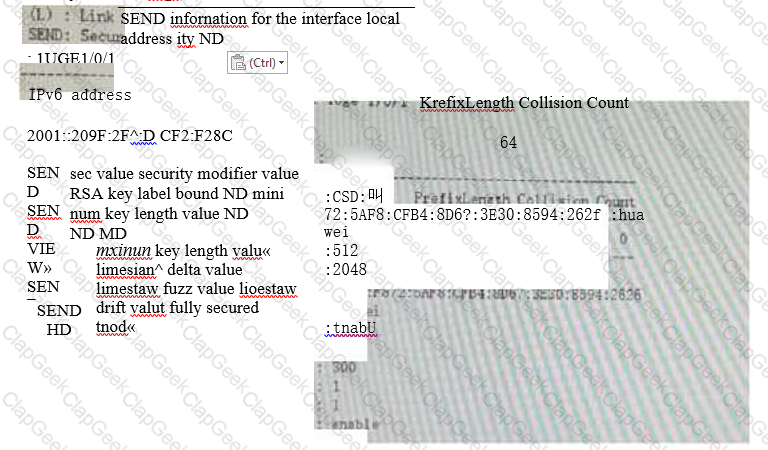
A description of the following IPv6 Secure Neighbor Discovery feature information for one of the interfaces Which one is wrong?
The following describes the network layer protection plan for HUAWEI CLOUD security architecture Which one is incorrect? (single selection).
If the database O&M workload is much greater than the host O&M workload, you can choose to have an independent department outside the original O&M bastion host
The database bastion host.
In the capacity building of the security team, it is generally divided into management positions and technical posts, which of the following are not the key responsibilities of technical positions? (single selection).
Which of the following behaviors does not pose an information security risk. (Single selection)
The following is a humble description of transparent and reverse proxies Which items are correct? (multiple selection).
How does the following not belong to the firewall to detect viruses? (single selection).
in the architecture of software-defined security Which of the following feature descriptions is correct?
In the first half of 2021 alone, there were 944 data breaches that resulted in 3.3 billion data records being compromised. Organizations must follow the principle of which of the following options to keep data safe at all times.
The following describes the role of logs Which one is wrong? (single selection).
The main role of the audit system is to audit security events after the fact To provide sufficient evidence, a security audit product must have which of the following features7
In • User Login Web Page with User Name and Password Medium The following is about Username" Which one is described correctly? (single selection).