Which of the following is correct about the configuration of the firewall interface bound to the VPN instance?
IPSec NAT traversal does not support IKE main mode, aggressive mode IP address + pre-shared key mode authentication, because pre-shared key mode authentication needs to extract the source IP address in the IP address to find the pre-shared key corresponding to this address. . The address change caused by the presence of NAT prevents the device from finding the pre-shared key.
The main function of URPF is to prevent network attack behavior based on destination address spoofing.
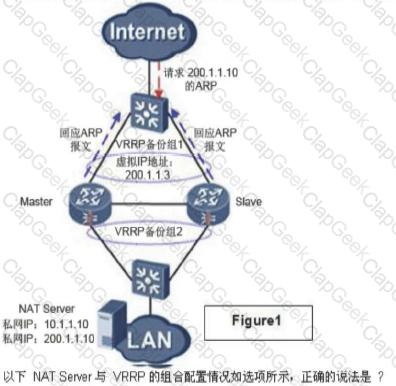
In a dual-system hot standby network, the NAT configurations of the two USGs are consistent. When the address in the NAT address pool is on the same network segment as the virtual IP address of the VRRP backup group, the next two graphs show the ARP response of the NAT server and VRRP combination application (lack of a picture).
In dual-system hot backup, the backup channel must be the primary interface on the interface board. Which type is not supported?
The Haiwei Secoway VPN client initiates an L2TP connection. The source port of the L2TP packet is 1710 and the port 1710 of the destination port.
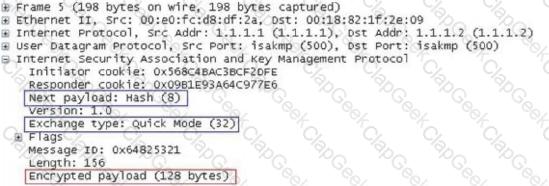
In the IKE V1 pre-shared key mode, what is the main role of the data captured in the following figure?
Two USG firewalls establish an IPSec VPN through the Site to Site mode. When viewing the status of a USG A, the following is displayed: display ipsec statistics the security packet statistics: input/output security paskets: 40 input/output security bytes: 400/0 input /output dropped security packets: 0/0 By status information, what information can be obtained correctly?
In the L2TP over IPSec application scenario, the USG device encrypts the original data packet with IPSec and then encapsulates the packet with L2TP.
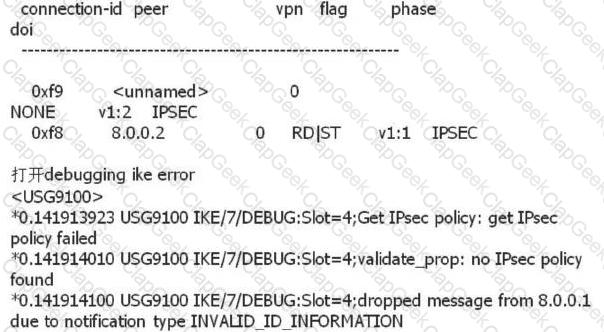
An administrator can view the IPSec status information and Debug information as follows. What is the most likely fault?
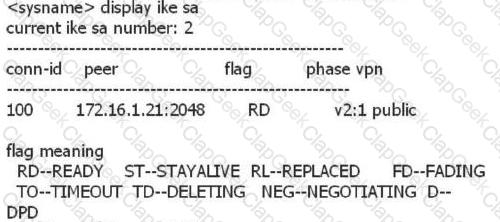
Run the display ike sa command to check the IKE SA information. The following statement is correct?
What are the correct statements about the following VRRP and VGMP protocol messages?
A certain network is as follows: LAN----G0/0/0 USG G0/0/1 ----Server. After the administrator analyzes the Attarcker on the LAN network connected to G0/0/0, if you want to prevent ARP flood attacks, limit the ARP traffic to 100 packets/minute. Which is the correct configuration?
The principle of HTTPS Flood source authentication defense is that the Anti-DDoS device replaces the SSL server with the client to complete the TCP three-way handshake. If the TCP three-way handshake is complete, the HTTPS flood source authentication check is successful.
112. The ESP only verifies the IP payload and can perform NAT traversal, but the ESP encrypts the Layer 4 port information and causes the PAT function to be unusable. This problem can be solved by using the IPSec transparent NAT function, which encapsulates the ESP packet in the UDP header and comes with the necessary port information to make the PAT work normally.
A user dials to the LNS of the company through L2TP over IPSec using the VPN client, and the final dialup fails. However, the debug ike all and debug l2tp all did not see any information on the LNS. The two stages of establishing ike failed. What are the reasons for the failure?
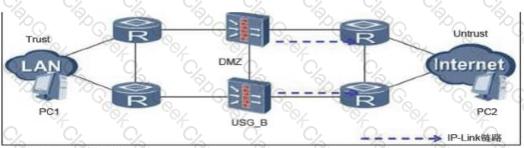
In the networking environment of dual-system hot backup and ip-link, which of the following configurations is the key configuration for ip-link and dual-system hot backup?
In the dual-system hot backup, when the slave does not receive the hello packet of the HRP sent in the HRP hello packet period, the slave device is considered to be faulty.
Accessing the headquarters server through the IPSec VPN from the branch computer. The IPSec tunnel can be established normally, but the service is unreachable. What are the possible reasons?
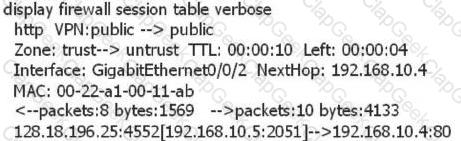
Based on the following information analysis on the firewall, which of the following options are correct?
The Tracert packet attack is an ICMP timeout packet returned by the attacker when the TTL is ____, and the ICMP port unreachable packet returned when the destination address is reached to find the path through which the packet arrives at the destination. Spying on the structure of the network
Site to Site IPSec VPN negotiation failed. Which of the following should be checked? 1. Network connectivity issues; 2. View the establishment of IKE phase 1 security associations and related configurations; 3. View the establishment of IKE phase 2 security associations and related configurations; 4. See if the security ACLs at both ends mirror each other.
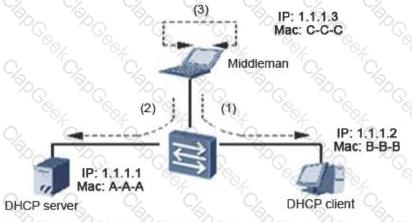
Man-in-the-middle attacks are: the middleman completes the data exchange between the server and the client. In the server's view, all messages are sent or sent to the client. From the client's point of view, all messages are also sent or sent.
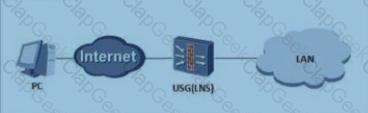
A network is as follows: The l2tp vpn is established through the VPN Client and the USG (LNS). What are the reasons for the dialup failure?