Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
You are configuring IPS (Intrusion Prevention System) on a Cisco IOS router. The IPS Policy Wizard window opens when you confirm the SDEE messages. Which of the following tasks can you perform using the IPS Policy Wizard window?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following components are usually found in an Intrusion detection system (IDS)?
Each correct answer represents a complete solution. Choose two.
You work as the Network Administrator for a company that does a large amount of defense contract business. A high level of security, particularly regarding sensitive documents, is required. Which of the following are the steps you should take to secure network printers?
Each correct answer represents a complete solution. Choose two.
PassGuide Research and Training Center is developing its new network model. Which of the following protocols should be implemented in the new network? (Click the Exhibit button on the toolbar to see the case study.) Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. Rick, your assistant, is configuring some laptops for wireless access. For security, WEP needs to be configured for wireless communication. By mistake, Rick configures different WEP keys in a laptop than that is configured on the Wireless Access Point (WAP). Which of the following statements is true in such situation?
Which of the following types of cryptography algorithms uses the MD series of encryption algorithms?
Which of the following types of authentication is generally used for public Internet Web sites?
Which of the following RAID standards distributes data across multiple disks in a way that gives improved speed at any given instant?
Which of the following documents is described in the statement below?
"It is developed along with all processes of the risk management. It contains the results of the qualitative risk analysis, quantitative risk analysis, and risk response planning."
John works as a Network Administrator for We-are-secure Inc. The We-are-secure server is based on Windows Server 2003. One day, while analyzing the network security, he receives an error message that Kernel32.exe is encountering a problem. Which of the following steps should John take as a countermeasure to this situation?
Each correct answer represents a complete solution. Choose all that apply.
You are the program manager for your project. You are working with the project managers regarding the procurement processes for their projects. You have ruled out one particular contract type because it is considered too risky for the program. Which one of the following contract types is usually considered to be the most dangerous for the buyer?
Which of the following can be used as a countermeasure against the SQL injection attack?
Each correct answer represents a complete solution. Choose two.
You have forgotten your password of an online shop. The web application of that online shop asks you to enter your email so that they can send you a new password. You enter your email you@gmail.com' and press the submit button. The Web application displays the server error. What can be the reason of the error?
You are the Network Administrator for a bank. In addition to the usual security issues, you are concerned that your customers could be the victim of phishing attacks that use fake bank Web sites.
Which of the following would protect against this?
Victor works as a professional Ethical Hacker for SecureNet Inc. He wants to use the Steganographic file system method to encrypt and hide some secret information. Which of the following disk spaces will he use to store this secret information?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following cryptographic system services ensures that information will not be disclosed to any unauthorized person on a local network?
Which of the following options is an approach to restricting system access to authorized users?
Which of the following terms describes the statement given below?
"It refers to a range of skills, tools, and techniques used to manage time when accomplishing specific tasks, projects, and goals. This set encompasses a wide scope of activities, and these include planning, allocating, setting goals, delegation, analysis of time spent, monitoring, organizing, scheduling, and prioritizing."
Which of the following federal laws are related to hacking activities?
Each correct answer represents a complete solution. Choose three.
Which of the following are the examples of administrative controls?
Each correct answer represents a complete solution. Choose all that apply.
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
What are the steps related to the vulnerability management program?
Each correct answer represents a complete solution. Choose all that apply.
Which type of virus is able to alter its own code to avoid being detected by anti-virus software?
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest network. You have recently added three new SCSI hard disk drives to a domain controller that already has two physical disk drives. The new SCSI disk drives are configured in a RAID-5 array. You are required to enhance the performance of the Active Directory database on the domain controller. Which of the following steps will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose two.
You have configured a virtualized Internet browser on your Windows XP professional computer. Using the virtualized Internet browser, you can protect your operating system from which of the following?
Which of the following is a fake target that deters hackers from locating your real network?
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
You work as a Network Administrator for Net Perfect Inc. The company's intranet Web site netperfect.com uses a digital certificate issued by the company's Enterprise Certificate Authority. The Enterprise Certificate Authority is located on a server named certificates.netperfect.com. Kate, a user, complains that she is unable to access the secure Web site on her computer using Internet Explorer. An error message appears stating that the digital certificate is not from a trusted source. What is the most likely cause?
Which of the following exists between the client and the server system to provide security and allows customized NAT traversal filters to be plugged into the gateway to support address and port translation for certain application layer protocols?
Part of your change management plan details what should happen in the change control system for your project. Theresa, a junior project manager, asks what the configuration management activities are for scope changes. You tell her that all of the following are valid configuration management activities except for which one?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
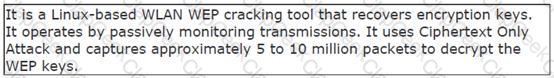
Which of the following tools is John using to crack the wireless encryption keys?
You configure a wireless router at your home. To secure your home Wireless LAN (WLAN), you implement WEP. Now you want to connect your client computer to the WLAN. Which of the following is the required information that you will need to configure the client computer?
Each correct answer represents a part of the solution. Choose two.
Which of the following statements are true about TCP/IP model?
Each correct answer represents a complete solution. Choose all that apply.
Mark works as a Network Administrator for Technet Inc. The company has a Windows 2003 domainbased network. The network has a file server that uses a RAID-5 volume. The RAID-5 volume is configured with five hard disk drives. Over the weekend, a drive in the RAID-5 volume fails. What will Mark do to restore the RAID-5 volume?
You work as an Exchange Administrator for McRobert Inc. You are configuring a new Exchange 2000 Server computer and two storage groups, group A and group B, on your network. You have to configure the physical disks on the Exchange 2000 Server computer to provide better performance and availability. Which configuration will you use to achieve this?
Which of the following techniques is based on a set of criteria that has been acquired in a specific knowledge area or product area?
Which of the following are the countermeasures against a man-in-the-middle attack?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements are true about locating rogue access points using WLAN discovery software such as NetStumbler, Kismet, or MacStumbler if you are using a Laptop integrated with Wi-Fi compliant MiniPCI card?
Each correct answer represents a complete solution. Choose two.
You work as a project manager for an IT project. You are analyzing activity sequences, durations, resource requirements, and schedule constraints to create the project schedule. In which of the following Knowledge Areas are you working on?
John works as an IT Technician for PassGuide Inc. One morning, John receives an e-mail from the company's Manager asking him to provide his logon ID and password, but the company policy restricts users from disclosing their logon IDs and passwords. Which type of possible attack is this?
Mark works as a Network Administrator for NetTech Inc. Several employees of the company work from the remote locations. The company provides a dial-up connection to employees to connect to the company's network using remote access service. Mark wants to implement call back feature for the employees who are dialing for long distance. Which of the following protocols will he use for remote access services to accomplish the task?
You work as a Consumer Support Technician for ABC Inc. The company provides troubleshooting support to users. You are troubleshooting a computer of a user who is working on Windows Vista.
He reports that his sensitive data is being accessed by someone because of security vulnerability in the component of Windows Vista. Which of the following features of Windows Security Center will you configure to save the user's data?
Which of the following technologies is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet?
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the following are the most likely threats to his computer?
Each correct answer represents a complete solution. Choose two.
Which of the following is the best encryption algorithm to encrypt and decrypt messages?
Rick works as the Network Administrator of a Windows 2000 network. The network consists of 30 domain controllers, 65 member servers, and 5000 workstations. All the computers on the network use Windows 2000 Advanced Server, Windows 2000 Server, and Windows 2000 Professional operating systems. The Windows 2000 Advanced Server computers are running the Cluster Service. The network uses TCP/IP as its only protocol. Once a week Rick works from home. But rest of the weekdays, he has to travel. Rick wants to be able to remotely administer each Windows 2000 server on his network with the following considerations:
• He must be able to establish a VPN connection to the Windows 2000 Server computers on the network from his home, so that the data remain encrypted and encapsulated during data transfer.
• While traveling , he must be able to connect to the network from a laptop computer via remote access connection, so that he can perform any task on the main Windows 2000 domain controller.
• While traveling, he must be able to edit the registry of the Windows 2000 Server computer.
• During the migration process to Windows 2000, he depleted all the financial resources for licensing. Therefore, he must not be required to add additional licenses to the network.
Rick takes the following actions:
• He implements the VPN connection on the proper server, the laptop computer, and the home computer.
• He configures the VPN connection to use the IPSec protocol in Encapsulating Security Payload (ESP) Tunnel Mode.
• He implements Windows 2000 Terminal Services using the Remote Administration mode on the Windows 2000 servers.
• He installs and configures Routing and Remote Access properly.
Which of the following goals will be accomplished by these actions?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He finds that the We-are-secure server is vulnerable to attacks. As a countermeasure, he suggests that the Network Administrator should remove the IPP printing capability from the server. He is suggesting this as a countermeasure against __________.
Which of the following can be performed to verify the effectiveness of a quality management system?
Which firewall architecture uses two NICs with a screening router inserted between the host and the untrusted network?
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of www.we-are-secure.com. He installs a sniffer on the We-are-secure server thinking that the following protocols of the We-are-secure server are being used in the network:
• HTTP
• SSL
• SSH
• IPSec
Considering the above factors, which of the following types of packets can he expect to see captured in encrypted form when he checks the sniffer's log file?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements about Digest authentication are true?
Each correct answer represents a complete solution. Choose two.
You are concerned about rogue wireless access points being connected to your network. What is the best way to detect and prevent these?
Which of the following honeypots captures limited amounts of information, mainly transactional data and some limited interaction?
You are concerned about attackers simply passing by your office, discovering your wireless network, and getting into your network via the wireless connection. Which of the following are NOT steps in securing your wireless connection?
Each correct answer represents a complete solution. Choose two.
Which of the following protocols are used to provide secure communication between a client and a server over the Internet?
Each correct answer represents a part of the solution. Choose two.
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
Each correct answer represents a complete solution. Choose all that apply.
In which of the following attacking methods does an attacker distribute incorrect IP address?
John works as a network security officer in Gentech Inc. The company uses a TCP/IP network. While working on the network, a problem occurs related to the DNS resolution. Which of the following utilities can he use to diagnose the problem?
Which of the following options is an approach to restricting system access to authorized users?
Which of the following tools hides information about IIS Webservers so that they can be prevented from various attacks performed by an attacker?
All of the following steps should be taken to prevent a Web server from IIS buffer overflow attacks except for which one?
Which of the following processes is NOT a part of the Project Procurement Management Knowledge Area?
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of www.we-are-secure.com. He installs a sniffer on the We-are-secure server thinking that the following protocols of the We-are-secure server are being used in the network:
HTTP
SSL
SSH
IPSec
Considering the above factors, which of the following types of packets can he expect to see captured in encrypted form when he checks the sniffer's log file?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is an automated tool that is used to implement SQL injections and to retrieve data from Web server databases?
Which of the following viruses is designed to prevent antivirus researchers from examining its code by using various methods that make tracing and disassembling difficult?
Which of the following is the practice of a domain name registrant using the five-day "grace period" (the Add Grace Period or AGP) at the beginning of the registration of an ICANN-regulated second-level domain to test the marketability of the domain?
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
Which of the following password authentication schemes enables a user with a domain account to log on to a network once, using a password or smart card, and to gain access to multiple computers in the domain without being prompted to log in again?
You are taking over the security of an existing network. You discover a machine that is not being used as such, but has software on it that emulates the activity of a sensitive database server. What is this?
You work as Network and Security Manager for PassGuide Inc. The management of the company is quite concerned about the security of the network. The management has assigned this task to you to improve the security. Which of the following access methods will you use if the method is to be primarily based on pre-established access, and users cannot change it?
Which methodology is a method to analyze the involved tasks in completing a given project, especially the time needed to complete each task, and identifying the minimum time needed to complete the total project?
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the following are the most likely threats to his computer?
Each correct answer represents a complete solution. Choose two.
Which of the following domains of the DNS hierarchy consists of categories found at the end of domain names, such as .com or .uk and divides the domains into organizations (.org), businesses (.com), countries (.uk), and other categories?
Which of the following are symptoms of a virus attack on your computer?
Each correct answer represents a complete solution. Choose two.


