You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
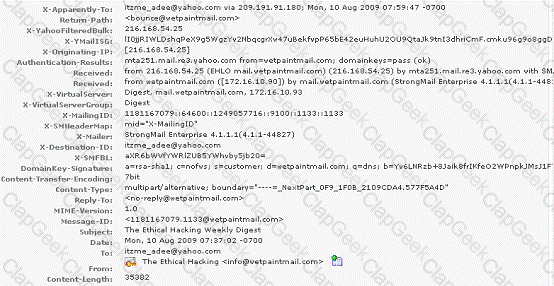
What is the IP address of the sender of this email?
Jason, a game lover, owns an Apple's iPod nano. He wants to play games on his iPod. He also wants to improve the quality of the audio recording of his iPod. Which of the following steps can Jason take to accomplish the task?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
What are the purposes of audit records on an information system?
Each correct answer represents a complete solution. Choose two.
You are responsible for all computer security at your company. This includes initial investigation into alleged unauthorized activity. Which of the following are possible results of improperly gathering forensic evidence in an alleged computer crime by an employee?
Each correct answer represents a complete solution. Choose three.
Joseph works as a Software Developer for WebTech Inc. He wants to protect the algorithms and the techniques of programming that he uses in developing an application. Which of the following laws are used to protect a part of software?
You work as a Network Administrator for Blue Well Inc. Your company's network has a Windows 2000 server with the FAT file system. This server stores sensitive data. You want to encrypt this data to protect it from unauthorized access. You also have to accomplish the following goals:
Data should be encrypted and secure.
Administrative effort should be minimum.
You should have the ability to recover encrypted files in case the file owner leaves the company.
Other permissions on encrypted files should be unaffected.
File-level security is required on the disk where data is stored.
Encryption or decryption of files should not be the responsibility of the file owner.
You take the following steps to accomplish these goals:
Convert the FAT file system to NTFS file system.
Use third-party data encryption software.
What will happen after taking these steps?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.weare-secure.com. He enters a single quote in the input field of the login page of the We-are-secure Web site and receives the following error message:
Microsoft OLE DB Provider for ODBC Drivers error '0x80040E14'
This error message shows that the We-are-secure Website is vulnerable to __________.
In Linux, which of the following files describes the processes that are started up during boot up?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a multimedia enabled mobile phone, which is suspected to be used in a cyber crime. Adam uses a tool, with the help of which he can recover deleted text messages, photos, and call logs of the mobile phone. Which of the following tools is Adam using?
Which of the following steps should be performed in order to optimize a system performance?
Each correct answer represents a complete solution. Choose three.
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
Which of the following statutes is enacted in the U.S., which prohibits creditors from collecting data from applicants, such as national origin, caste, religion etc?
What is the name of the Secondary IDE slave, fourth partition in Linux operating system according to the Linux naming convention?
You work as a professional Computer Hacking Forensic Investigator. A project has been assigned to you to investigate the DoS attack on a computer network of SecureEnet Inc. Which of the following methods will you perform to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following commands can you use to create an ext3 file system?
Each correct answer represents a complete solution. Choose two.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate an iphone, which is being seized from a criminal. The local police suspect that this iphone contains some sensitive information. Adam knows that the storage partition of the iphone is divided into two partitions. The first partition is used for the operating system. Other data of iphone is stored in the second partition. Which of the following is the name with which the second partition is mounted on the iphone?
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to fix partitions on a hard drive. Which of the following Unix commands can you use to accomplish the task?
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to allow direct access to the filesystems data structure. Which of the following Unix commands can you use to accomplish the task?
Adam works as a professional Computer Hacking Forensic Investigator. He has been called by the FBI to examine data of the hard disk, which is seized from the house of a suspected terrorist. Adam decided to acquire an image of the suspected hard drive. He uses a forensic hardware tool, which is capable of capturing data from IDE, Serial ATA, SCSI devices, and flash cards. This tool can also produce MD5 and CRC32 hash while capturing the data. Which of the following tools is Adam using?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He receives the following e-mail:

The e-mail that John has received is an example of __________.
Adam, a malicious hacker has successfully gained unauthorized access to the Linux system of
Umbrella Inc. Web server of the company runs on Apache. He has downloaded sensitive documents and database files from the computer. After performing these malicious tasks, Adam finally runs the following command on the Linux command box before disconnecting. for (( i = 0;i<11;i++ )); do
dd if=/dev/random of=/dev/hda && dd if=/dev/zero of=/dev/hda done
Which of the following actions does Adam want to perform by the above command?
You company suspects an employee of sending unauthorized emails to competitors. These emails are alleged to contain confidential company data. Which of the following is the most important step for you to take in preserving the chain of custody?
Which of the following tools can be used by a user to hide his identity?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a Computer Hacking Forensic Investigator for a garment company in the United States. A project has been assigned to him to investigate a case of a disloyal employee who is suspected of stealing design of the garments, which belongs to the company and selling those garments of the same design under different brand name. Adam investigated that the company does not have any policy related to the copy of design of the garments. He also investigated that the trademark under which the employee is selling the garments is almost identical to the original trademark of the company. On the grounds of which of the following laws can the employee be prosecuted?
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Which of the following directories in Linux operating system contains device files, which refers to physical devices?
Normally, RAM is used for temporary storage of data. But sometimes RAM data is stored in the hard disk, what is this method called?
John works for an Internet Service Provider (ISP) in the United States. He discovered child
pornography material on a Web site hosted by the ISP. John immediately informed law enforcement authorities about this issue. Under which of the following Acts is John bound to take such an action?
Which of the following are the benefits of information classification for an organization?
Each correct answer represents a complete solution. Choose two.
What is the name of the group of blocks which contains information used by the operating system in Linux system?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a compromised system of a cyber criminal, who hides some information in his computer. This computer runs on Linux operating system. Adam wants to extract the data units of a file, which is specified by its meta-data address. He is using the Sleuth Kit for this purpose. Which of the following commands in the Sleuth kit will he use to accomplish the task?
Adam works as a Computer Hacking Forensic Investigator in a law firm. He has been assigned with his first project. Adam collected all required evidences and clues. He is now required to write an investigative report to present before court for further prosecution of the case. He needs guidelines to write an investigative report for expressing an opinion. Which of the following are the guidelines to write an investigative report in an efficient way?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following laws or acts, formed in Australia, enforces prohibition against cyber stalking?
Which of the following is the Windows feature on which the file management can be performed by a PC user?
Which of the following Windows XP system files handles memory management, I/O operations, and interrupts?
Joseph works as a Web Designer for WebTech Inc. He creates a Web site and wants to protect it from lawsuits. Which of the following steps will he take to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate and examine drive image of a compromised system, which is suspected to be used in cyber crime. Adam uses Forensic Sorter to sort the contents of hard drive in different categories. Which of the following type of image formats is NOT supported by Forensic Sorter?
Which of the following is a documentation of guidelines that computer forensics experts use to handle evidences?
Which of the following diagnostic codes sent by POST to the internal port h80 refers to the system board error?
In which of the following files does the Linux operating system store passwords?
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following directories contains administrative commands and daemon processes in the Linux operating system?