Following a Digital Forensics investigation, which of the following should be included in the final forensics report?
Which tasks would a First Responder perform during the Identification phase of Incident Response?
Requiring criminal and financial background checks for new employees is an example of what type of security control?
A company wants to allow only company-issued devices to attach to the wired and wireless networks. Additionally, devices that are not up-to-date with OS patches need to be isolated from the rest of the network until they are updated. Which technology standards or protocols would meet these requirements?
Which of the following is an SNMPv3 security feature that was not provided by earlier versions of the protocol?
Of the following pieces of digital evidence, which would be collected FIRST from a live system involved in an incident?
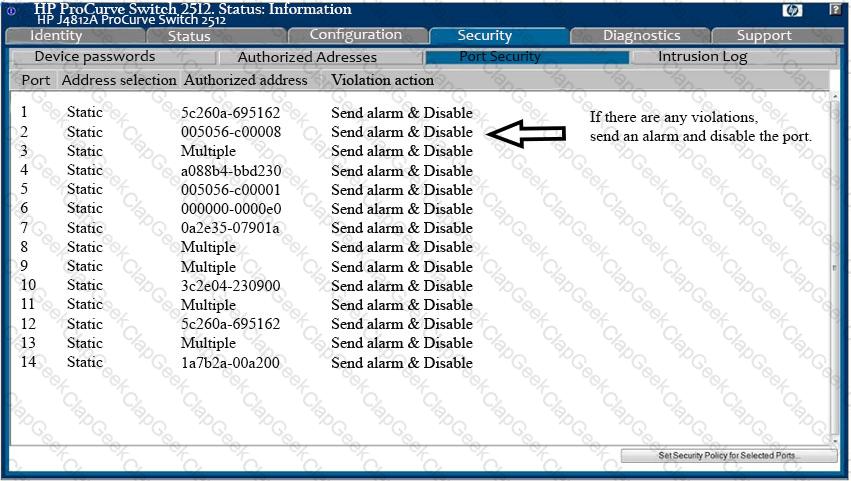
Analyze the screenshot below. Which of the following attacks can be mitigated by these configuration settings?
An analyst wants to see a grouping of images that may be contained in a pcap file. Which tool natively meets this need?
Requiring background checks for employees who access protected data is an example of which type of data loss control?
From a security perspective, how should the Root Bridge be determined in a Spanning Tree Protocol (STP) environment?


