Which of the following statements is true regarding Deep Security Manager-todatabase com-munication?
Which of the following statements is true regarding Maintenance Mode in the Application Control protection Module?
Which of the following correctly describes the Firewall rule Action of Force Allow?
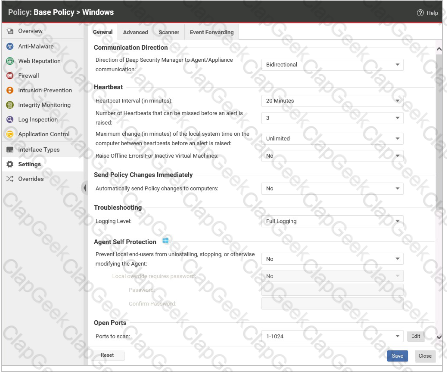
Based on the policy configuration displayed in the exhibit, which of the following statements is true?
Which of the following statements is FALSE regarding Firewall rules using the Bypass action?
Which of the following is not an operation that is performed when network traffic is intercepted by the network driver on the Deep Security Agent?
Recommendation scans can detect applications and/or vulnerabilities on servers on the network. Which of the following Protection Modules make use of Recommendation scans?


