Which phase of the cloud service lifecycle involves ongoing management activities to maintain cloud infrastructure and deployed services?
An organization wants to deliver applications quickly and effectively. They believe that it is the only way to stay competitive in this ever-changing digital world. The organization wants to adopt practices that promote collaboration across teams during various phases of the software development lifecycle.
Which practice will meet the organization’s requirements?
A development group is using an iterative and incremental software development method.
Which standard is being utilized?
What term refers to businesses that cautiously and gradually embrace digital transformation?
An administrator must design a fault-tolerant IT environment for applications.
Which techniques meet this requirement?
Which cloud security design principle prevents an individual from improper access or system misuse?
What is a possible cause for incurring high capital expenditures for IT, even though resources may remain underutilized for a majority of the time in a traditional data center?
What activity is performed during the service planning phase of the cloud service lifecycle?
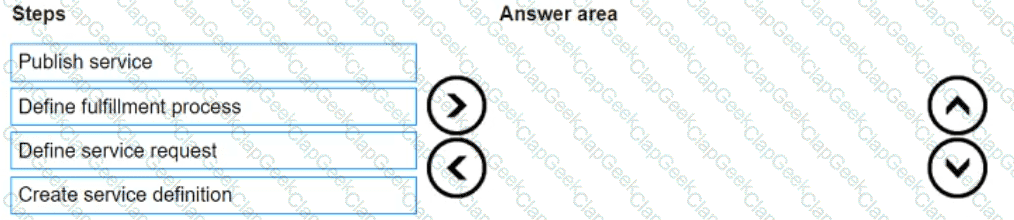
What is the correct sequence of steps in the service catalog design and implementation process?
A consumer is interested in a service that provides multiple operating systems and programming frameworks for application development and deployment.
Which cloud service model meets these requirements?
Which defines the maximum amount of data loss that can be tolerated by a business following a disaster?
An organization requires double the processing capacity for a specific duration to handle increased workload. For the remaining period, the organization might want to release the idle resources to save costs. The workload variations may be seasonal or transient.
Which cloud characteristic enables the consumer to handle such variations in workloads and IT resource requirements?
Two departments of an organization have their own volumes created on the same storage system. What can the organization implement to prevent unauthorized access to the volumes owned by the otherdepartment?
Which Dell Technologies product can automate and centralize the collection and analysis of data across physical and virtual environments?


