Which of the following are correct statements regarding the use of access keys? (Choose two.)
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
Given this information:
The Console is located at https://prisma-console.mydomain.local The username is: cluster
The password is: password123
The image to scan is: myimage:latest
Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
The development team wants to block Cross Site Scripting attacks from pods in its environment. How should the team construct the CNAF policy to protect against this attack?
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[? (@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
Which two integrated development environment (IDE) plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
Prisma Cloud supports sending audit event records to which three targets? (Choose three.)
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)

The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
An administrator needs to write a script that automatically deactivates access keys that have not been used for 30 days.
In which order should the API calls be used to accomplish this task? (Drag the steps into the correct order from the first step to the last.) Select and Place:

Which Prisma Cloud policy type detects port scanning activities in a customer environment?
The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User: $ADMIN_USER
Which command generates the YAML file for Defender install?
Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
An administrator of Prisma Cloud wants to enable role-based access control for Docker engine.
Which configuration step is needed first to accomplish this task?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
An administrator wants to retrieve the compliance policies for images scanned in a continuous integration (CI) pipeline.
Which endpoint will successfully execute to enable access to the images via API?
What is the behavior of Defenders when the Console is unreachable during upgrades?
Which two required request headers interface with Prisma Cloud API? (Choose two.)
Which two proper agentless scanning modes are supported with Prisma Cloud? (Choose two).
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
Which two frequency options are available to create a compliance report within the console? (Choose two.)
An administrator has access to a Prisma Cloud Enterprise.
What are the steps to deploy a single container Defender on an ec2 node?
A customer finds that an open alert from the previous day has been resolved. No auto-remediation was configured.
Which two reasons explain this change in alert status? (Choose two.)
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
Put the steps of integrating Okta with Prisma Cloud in the right order in relation to CIEM or SSO okra integration.

A customer is interested in PCI requirements and needs to ensure that no privilege containers can start in the environment.
Which action needs to be set for “do not use privileged containers”?
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
What is the correct method for ensuring key-sensitive data related to SSNs and credit card numbers cannot be viewed in Dashboard > Data view during investigations?
Which two offerings will scan container images in Jenkins pipelines? (Choose two.)
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
Anomaly policy uses which two logs to identify unusual network and user activity? (Choose two.)
Given the following JSON query:
$.resource[*].aws_s3_bucket exists
Which tab is the correct place to add the JSON query when creating a Config policy?
Which three incident types will be reflected in the Incident Explorer section of Runtime Defense? (Choose three.)
Which two CI/CD plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?
Given a default deployment of Console, a customer needs to identify the alerted compliance checks that are set by default.
Where should the customer navigate in Console?
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
Which file extension type is supported for Malware scanning in Prisma Cloud Data Security (PCDS)?
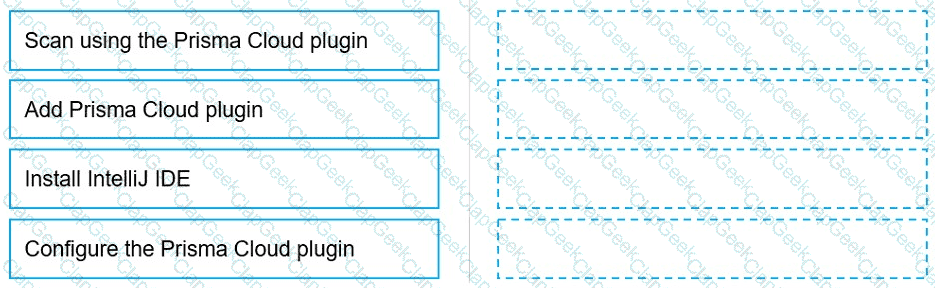
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
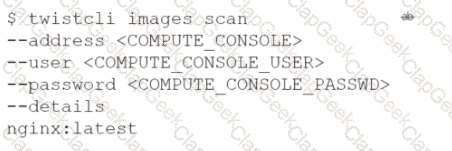
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)

C)
D)
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
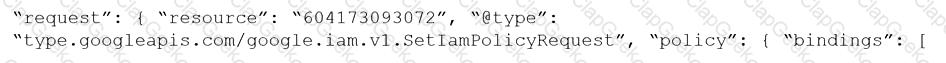
B)
C)
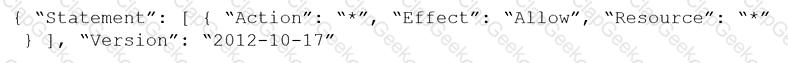
D)

A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
Based on the following information, which RQL query will satisfy the requirement to identify VM hosts deployed to organization public cloud environments exposed to network traffic from the internet and affected by Text4Shell RCE (CVE-2022-42889) vulnerability?
• Network flow logs from all virtual private cloud (VPC) subnets are ingested to the Prisma Cloud Enterprise Edition tenant.
• All virtual machines (VMs) have Prisma Cloud Defender deployed.
A)
B)
C)
D)
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
A Prisma Cloud administrator is tasked with pulling a report via API. The Prisma Cloud tenant is located on app2.prismacloud.io.
What is the correct API endpoint?
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
A customer's Security Operations Center (SOC) team wants to receive alerts from Prisma Cloud via email once a day about all policies that have a violation, rather than receiving an alert every time a new violation occurs.
Which alert rule configuration meets this requirement?
An administrator wants to enforce a rate limit for users not being able to post five (5) .tar.gz files within five (5) seconds.
What does the administrator need to configure?
An administrator needs to detect and alert on any activities performed by a root account.
Which policy type should be used?
A customer has Prisma Cloud Enterprise and host Defenders deployed.
What are two options that allow an administrator to upgrade Defenders? (Choose two.)
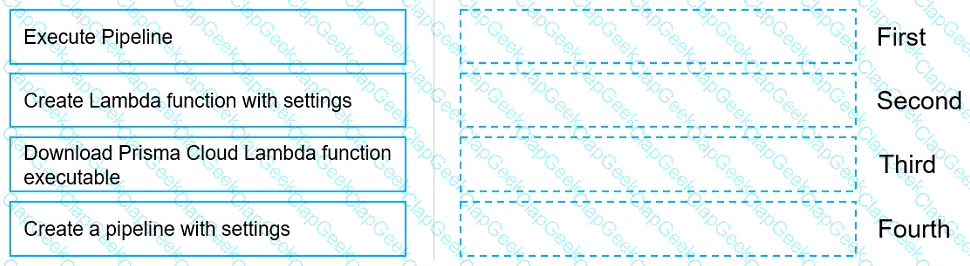
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
Given the following RQL:
Which audit event snippet is identified by the RQL?
A)
B)
C)
D)
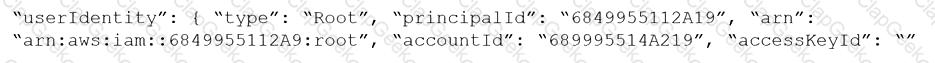
Which of the following is not a supported external integration for receiving Prisma Cloud Code Security notifications?
One of the resources on the network has triggered an alert for a Default Config policy.
Given the following resource JSON snippet:
Which RQL detected the vulnerability?
A)

B)
C)
D)
Which two processes ensure that builds can function after a Console upgrade? (Choose two.)


