Which access control model is best suited for a large organization with many departments and varied access needs?
During an ISC2 CC exam, you observe another candidate cheating. What should you do?
To avoid bodily injury claims, a company decides not to offer high-risk services. This is an example of:
The prevention of authorized access to resources or delaying time-critical operations is known as:
Which access control model can grant access to a given object based on complex rules?
Shaun is planning to protect data in all states (at rest, in motion, and in use), defending against data leakage. What is the BEST solution to implement?
The process of how an organization is managed and how decisions are made is called:
An organization’s security system that prevents, detects, analyzes, and responds to cybersecurity incidents is called:
David's team recently implemented a new system that gathers information from a variety of different log sources, analyzes that information, and then triggers automated playbooks in response to security events. What term BEST describes this technology?
A company wants to prevent employees from bringing unauthorized electronic devices into the workspace. Which physical control is best?
A centralized organizational function that monitors, detects, and analyzes security events to prevent disruptions is called:
An attack in which a user authenticated to a server unknowingly invokes unwanted actions after visiting a malicious website is known as:
System capabilities designed to detect and prevent unauthorized use and transmission of information are known as:
Which type of control is used to restore systems or processes to their normal state after an attack?
Exhibit.
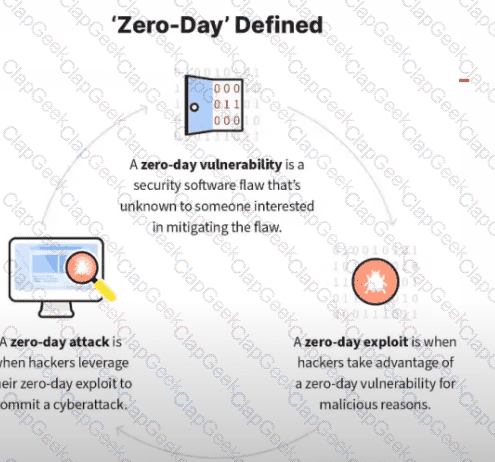
What kind of vulnerability is typically not identifiable through a standard vulnerability assessment?
The mitigation of violations of security policies and recommended practices is known as:
The evaluation of security controls to determine whether they are implemented correctly and operating as intended is known as:
A method for risk analysis that is based on the assignment of a descriptor such as low, medium, or high.
What is the primary goal of Identity and Access Management (IAM) in cybersecurity?
A prolonged, targeted cyberattack where an intruder remains undetected for an extended period is called:
The practice of sending fraudulent communications that appear to come from a reputable source is known as:
A company’s governing board decides that only legal services may review third-party contracts. They create a document stating that no other department has permission to do so. This document is a:
Which attack attempts to gain information by observing a device’s power consumption?
Which document serves as specifications for implementing policy and dictates mandatory requirements?
A one-way spinning door or barrier that allows only one person at a time to enter a building or area.
A company analyzes system requirements, functions, and interdependencies to prioritize contingency needs. What is this process called?
A practitioner needing step-by-step instructions to complete a provisioning task should consult a:
Which aspect of cybersecurity is MOST impacted by Distributed Denial of Service (DDoS) attacks?
An agreement between a cloud service provider and a customer based on cloud-specific terms is called:
Dylan is creating a cloud architecture that requires connections between systems in two different private VPCs. What is the BEST way to enable this access?
What is the first component the new security engineer should learn about in the incident response plan?
The prevention of authorized access to resources or the delaying of time-critical operations is known as:
A weighted factor based on the probability that a threat will exploit a vulnerability is called:
David is worried about distributed denial-of-service (DDoS) attacks against his company’s primary web application. Which option will provide the MOST resilience against large-scale DDoS attacks?
Which approach involves a continuous cycle of identifying, assessing, prioritizing, and mitigating cybersecurity risks?
An attack in which an attacker listens passively to the authentication protocol to capture information that can be used in a subsequent active attack to masquerade as the claimant is known as:
After an earthquake disrupts business operations, which document contains the reactive procedures required to return business to normal operations?
Which access control method uses attributes and rules evaluated by a central Policy Decision Point (PDP)?
What kind of control is it when we add a backup firewall that takes over if the main one stops working?
What is the difference between Business Continuity Planning (BCP) and Disaster Recovery Planning (DRP)?
Configuration settings or parameters stored as data and managed through a GUI are examples of:
In which cloud model does the customer have theleast responsibilityover infrastructure?
In which access control model can the creator of an object delegate permissions?
Which cloud service model provides the most suitable environment for customers to build and operate their own software?