An application requires the storage of PII. A systems engineer needs to implement a solution that uses an external device for key management. Which of the following is the best solution?
A global organization wants to manage all endpoint and user telemetry. The organization also needs to differentiate this data based on which office it is correlated to. Which of the following strategies best aligns with this goal?
A company is preparing to move a new version of a web application to production. No issues were reported during security scanning or quality assurance in the CI/CD pipeline. Which of the following actions should thecompany take next?
A local government that is investigating a data exfiltration claim was asked to review the fingerprint of the malicious user's actions. An investigator took a forensic image of the VM and downloaded the image to a secured USB drive to share with the government. Which of the following should be taken into consideration during the process of releasing the drive to the government?
An external SaaS solution user reports a bug associated with the role-based access control module. This bug allows users to bypass system logic associated with client segmentation in the multitenant deployment model. When assessing the bug report, the developer finds that the same bug was previously identified and addressed in an earlier release. The developer then determines the bug was reintroduced when an existing software component was integrated from a prior version of the platform. Which of the following is the best way to prevent this scenario?
An organization determines existing business continuity practices are inadequate to support critical internal process dependencies during a contingency event. A compliance analyst wants the Chief Information Officer (CIO) to identify the level of residual risk that is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
A security engineer wants to enhance the security posture of end-user systems in a Zero Trust environment. Given the following requirements:
. Reduce the ability for potentially compromised endpoints to contact command-and-control infrastructure.
. Track the requests that the malware makes to the IPs.
. Avoid the download of additional payloads.
Which of the following should the engineer deploy to meet these requirements?
An external threat actor attacks public infrastructure providers. In response to the attack and during follow-up activities, various providers share information obtained during response efforts. After the attack, energy sector companies share their status and response data:
Company
SIEM
UEBA
DLP
ISAC Member
TIP Integration
Time to Detect
Time to Respond
1
Yes
No
Yes
Yes
Yes
10 minutes
20 minutes
2
Yes
Yes
Yes
Yes
No
20 minutes
40 minutes
3
Yes
Yes
No
No
Yes
12 minutes
24 minutes
Which of thefollowing is the most important issue to address to defend against future attacks?
Which of the following are the best ways to mitigate the threats that are the highest priority? (Select two).
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
An ISAC supplied recent threat intelligence information about pictures used on social media that provide reconnaissance of systems in use in secure facilities. In response, the Chief Information Security Officer (CISO) wants several configuration changes implemented via the MDM to ensure the following:
• Camera functions and location services are blocked for corporate mobile devices.
• All social media is blocked on the corporate and guest wireless networks.
Which of the following is the CISO practicing to safeguard against the threat?
After a vendor identified a recent vulnerability, a severity score was assigned to the vulnerability. A notification was also publicly distributed. Which of the following would most likely include information regarding the vulnerability and the recommended remediation steps?
A systems administrator works with engineers to process and address vulnerabilities as a result of continuous scanning activities. The primary challenge faced by the administrator is differentiating between valid and invalid findings. Which of the following would the systems administrator most likely verify is properly configured?
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the least amount of downtime. Which of the following should the analyst perform?
A company reduced its staff 60 days ago, and applications are now starting to fail. The security analyst is investigating to determine if there is malicious intent for the application failures. The security analyst reviews the following logs:
22:03:50 sshd[21502]: Success login for user01 from 192.168.2.5
22:10:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:11:40 sshd[21502]: Success login for user07 from 192.168.2.58
22:12:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:13:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:13:00 sshd[21502]: Success login for user03 from 192.168.2.27
22:13:00 sshd[21502]: Failed login for user10 from 192.168.2.5
Which of the following is the most likely reason for the application failures?
A security engineer must resolve a vulnerability in a deprecated version of Python for a custom-developed flight simul-ation application that is monitored and controlled remotely. The source code is proprietary and built with Python functions running on the Ubuntu operating system. Version control is not enabled for the application in development or production. However, the application must remain online in the production environment using built-in features. Which of the following solutions best reduces theattack surface of these issues and meets the outlined requirements?
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
A healthcare system recently suffered from a ransomware incident. As a result, the board of directors decided to hire a security consultant to improve existing network security. The security consultant found that the healthcare network was completely flat, had no privileged access limits, and had open RDP access to servers with personal health information. As the consultant builds the remediation plan, which of the following solutions would best solve these challenges? (Select three).
A cybersecurity architect seeks to improve vulnerability management and orchestrate a large number of vulnerability checks. Key constraints include:
. There are 512 containerized microservices.
. Vulnerability data is sourced from multiple scanners.
. CIS baselines must be enforced.
. Scan activity must be scheduled.
Which of the following automation workflows best meets this objective?
A malware researcher has discovered a credential stealer is looking at a specific memory register to harvest passwords that will be used later for lateral movement in corporate networks. The malware is using TCP 4444 to communicate with other workstations. The lateral movement would be best mitigated by:
A company receives several complaints from customers regarding its website. An engineer implements a parser for the web server logs that generates the following output:
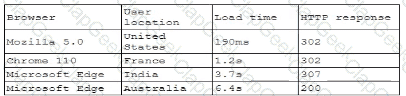
which of the following should the company implement to best resolve the issue?
A security engineer reviews an after action report from a previous security breach and notes a long lag time between detection and containment of a compromised account. The engineer suggests using SOAR to address this concern. Which of the following best explains the engineer's goal?
A company plans to deploy a new online application that provides video training for its customers. As part of the design, the application must be:
• Fast for all users
• Available for users worldwide
• Protected against attacks
Which of the following are the best components the company should use to meet these requirements? (Select two).
A company's help desk is experiencing a large number of calls from the finance department slating access issues to www bank com The security operations center reviewed the following security logs:
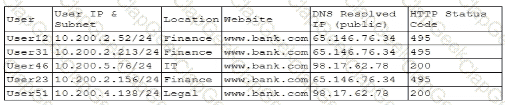
Which of the following is most likely the cause of the issue?
As part of a security audit in the software development life cycle, a product manager must demonstrate and provide evidence of a complete representation of the code and modules used within the production-deployed application prior to the build. Which of the following best provides the required evidence?
Asoftware company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?
Embedded malware has been discovered in a popular PDF reader application and is currently being exploited in the wild. Because the supply chain was compromised, this malware is present in versions 10.0 through 10.3 of the software's official versions. The malware is not present in version 10.4.
Since the details around this malware are still emerging, the Chief Information Security Officer has asked the senior security analyst to collaborate with the IT asset inventory manager to find instances of the installed software in order to begin response activities. The asset inventory manager has asked an analyst to provide a regular expression that will identify the affected versions. The software installation entries are formatted as follows:
Reader 10.0
Reader 10.1
Reader 10.2
Reader 10.3
Reader 10.4
Which of the following regular expression entries will accuratelyidentify all the affected versions?
An audit finding reveals that a legacy platform has not retained loos for more than 30 days The platform has been segmented due to its interoperability with newer technology. As a temporarysolution, the IT department changed the log retention to 120 days. Which of the following should the security engineer do to ensure the logs are being properly retained?
A company implemented a NIDS and a NIPS on the most critical environments. Since this implementation, the company has been experiencing network connectivity issues. Which of the following should the security architect recommend for a new NIDS/NIPS implementation?
A subcontractor develops safety critical avionics software for a major aircraft manufacturer. After an incident, a third-party investigator recommends the company begin to employ formal methods in the development life cycle. Which of the following findings from the investigation most directly supports the investigator's recommendation?
A company needs to quickly assess whether software deployed across the company's global corporate network contains specific software libraries. Which of the following best enables the company's SOC to respond quickly when such an assessment is required?
A compliance officer isfacilitating abusiness impact analysis (BIA)and wantsbusiness unit leadersto collect meaningful data. Several business unit leaders want more information about the types of data the officer needs.
Which of the following data types would be the most beneficial for the compliance officer?(Select two)
A global manufacturing company has an internal application mat is critical to making products This application cannot be updated and must Beavailable in the production area A security architect is implementing security for the application. Which of the following best describes the action the architect should take-?
An organization wants to create a threat model to identity vulnerabilities in its infrastructure. Which of the following, should be prioritized first?
Which of the following includes best practices for validating perimeter firewall configurations?
A security operations analyst is reviewing network traffic baselines for nightly database backups. Given the following information:
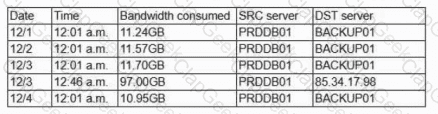
Which of the following should the security analyst do next?
A security analyst received a report that an internal web page is down after a company-wide update to the web browser Given the following error message:

Which of the following is the b«« way to fix this issue?
A security analyst is using data provided from a recent penetration test to calculate CVSS scores to prioritize remediation. Which of the following metric groups would the analyst need to determine to get the overall scores? (Select three).
A company wants to protect against the most common attacks and rapidly integrate with different programming languages. Which of the following technologies is most likely to meet this need?
A security engineer receives the following findings from a recent security audit:
• Data should be protected based on user permissions and roles.
• User action tracking should be implemented across the network.
• Digital identities should be validated across the data access workflow.
Which of the following is the first action the engineer should take to address the findings?
A systems administrator wants to use existing resources to automate reporting from disparate security appliances that do not currently communicate. Which of the following is the best way to meet this objective?
A news organization wants to implement workflows that allow users to request that untruthful data be retraced and scrubbed from online publications to comply with the right to be forgotten Which of the following regulations is the organization most likely trying to address'
A security architect is designing Zero Trust enforcement policies for all end users. The majority of users work remotely and travel frequently for work. Which of the following controls should the security architect do first?
During a recent audit, a company's systems were assessed- Given the following information:
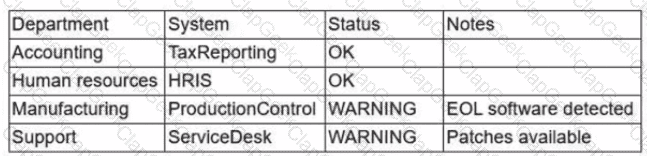
Which of the following is the best way to reduce the attack surface?
A user from the sales department opened a suspicious file attachment. The sales department then contacted the SOC to investigate a number of unresponsive systems, and the team successfully identified the file and the origin of the attack. Which of the following is the next step of the incident response plan?
A security engineer is developing a solution to meet the following requirements?
• All endpoints should be able to establish telemetry with a SIEM.
• All endpoints should be able to be integrated into the XDR platform.
• SOC services should be able to monitor the XDR platform
Which of the following should the security engineer implement to meet the requirements?
Which of the following most likely explains the reason a security engineer replaced ECC with a lattice-based cryptographic technique?
A threat hunter is identifying potentially malicious activity associated with an APT. When the threat hunter runs queries against the SIEM platform with a date range of 60 to 90 days ago, the involved account seems to be typically most active in the evenings. When the threat hunter reruns the same query with a date range of 5 to 30 days ago, the account appears to be most active in the early morning. Which of the following techniques is the threat hunter using to better understand the data?
A large organization deployed a generative AI platform for its global user population to use. Based on feedback received during beta testing, engineers have identified issues with user interface latency and page-loading performance for international users. The infrastructure is currently maintained within two separate data centers, which are connected using high-availability networking and load balancers. Which of the following is the best way to address the performance issues?
An engineer wants to automate several tasks by running commands daily on a UNIX server. The engineer has only built-in, default tools available. Which of the following should the engineer use to best assist with this effort? (Select Two).
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
A company migrating to aremote work model requires that company-owned devices connect to a VPN before logging in to the device itself. The VPN gateway requires that a specific key extension is deployed to the machine certificates in the internal PKI. Which of the following best explains this requirement?
A developer receives feedback about code quality and efficiency. The developer needs to identify and resolve the following coding issues before submitting the code changes for peer review:
Indexing beyond arrays
Dereferencing null pointers
Potentially dangerous data type combinations
Unreachable code
Non-portable constructs
Which of the following would be most appropriate for the developer to use in this situation?
A user tried to access a web page at http://10.1.1.1. Previously the web page did not require authentication, and now the browser is prompting for credentials. Which of the following actions would best prevent the issue from reoccurring and reduce the likelihood of credential exposure?
During an incident response activity, the response team collected some artifacts from a compromised server, but the following information is missing:
• Source of the malicious files
• Initial attack vector
• Lateral movement activities
The next step in the playbook is to reconstruct a timeline. Which of the following best supports this effort?
Which of the following AI concerns is most adequately addressed by input sanitation?
A company is migrating from a Windows Server to Linux-based servers. A security engineer must deploy a configuration management solution that maintains security software across all the Linux servers. Which of the following configuration file snippets is the most appropriate to use?
A security analyst is reviewing the following vulnerability assessment report:
192.168.1.5, Host = Server1, CVSS 7.5, Web Server, Remotely Executable = Yes, Exploit = Yes
205.1.3.5, Host = Server2, CVSS 6.5, Bind Server, Remotely Executable = Yes, Exploit = POC
207.1.5.7, Host = Server3, CVSS 5.5, Email Server, Remotely Executable = Yes, Exploit = Yes
192.168.1.6, Host = Server4, CVSS 9.8, Domain Controller, Remotely Executable = Yes, Exploit = Yes
Which of the following should be patched first to minimize attacks against internet-facing hosts?
A manufacturing plant is updating its IT services. During discussions, the senior management team created the following list of considerations:
• Staff turnover is high and seasonal.
• Extreme conditions often damage endpoints.
• Losses from downtime must be minimized.
• Regulatory data retention requirements exist.
Which of the following best addresses the considerations?
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
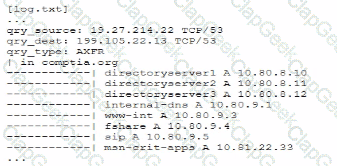
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A company developed a new solution that needs to track any changes to the data, and the changes need to be quickly identified. If any changes are attempted without prior approval, multiple events must be triggered, such as:
Raising alerts
Blocking the unapproved changes
Quickly removing access to the data
Which of the following solutions best meets these requirements?
A company is adopting microservice architecture in order to quickly remediate vulnerabilities and deploy to production. All of the microservices run on the same Linux platform. Significant time was spent updating the base OS before deploying code. Which of the following should the company do to make the process efficient?
An administrator reviews the following log and determines the root cause of a site-to-site tunnel failure:
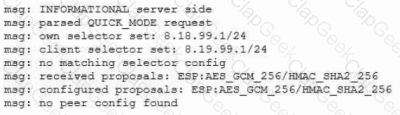
Which of the following actions should the administrator take to most effectively correct the failure?
A security engineer wants to propose an MDM solution to mitigate certain risks. The MDM solution should meet the following requirements:
• Mobile devices should be disabled if they leave the trusted zone.
• If the mobile device is lost, data is not accessible.
Which of the following options should the security engineer enable on the MDM solution? (Select two).
An analyst reviews a SIEM and generates the following report:
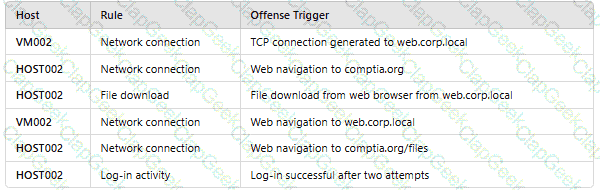
OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
Audit findings indicate several user endpoints are not utilizing full disk encryption During me remediation process, a compliance analyst reviews the testing details for the endpoints and notes the endpoint device configuration does not support full disk encryption Which of the following is the most likely reason me device must be replaced'
A security architect wants to develop abaseline of security configurations These configurations automatically will be utilized machine is created Which of the following technologies should the security architect deploy to accomplish this goal?
During a forensic review of a cybersecurity incident, a security engineer collected a portion of the payload used by an attacker on a comprised web server Given the following portion of the code:
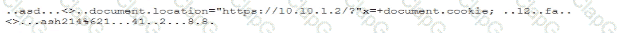
Which of the following best describes this incident?
An attacker infiltrated the code base of a hardware manufacturer and inserted malware before the code was compiled. The malicious code is now running at the hardware level across a number of industries and sectors. Which of the following categories best describes this type of vendor risk?
An incident response team is analyzing malware and observes the following:
• Does not execute in a sandbox
• No network loCs
• No publicly known hash match
• No process injection method detected
Which of thefollowing should the team do next to proceed with further analysis?
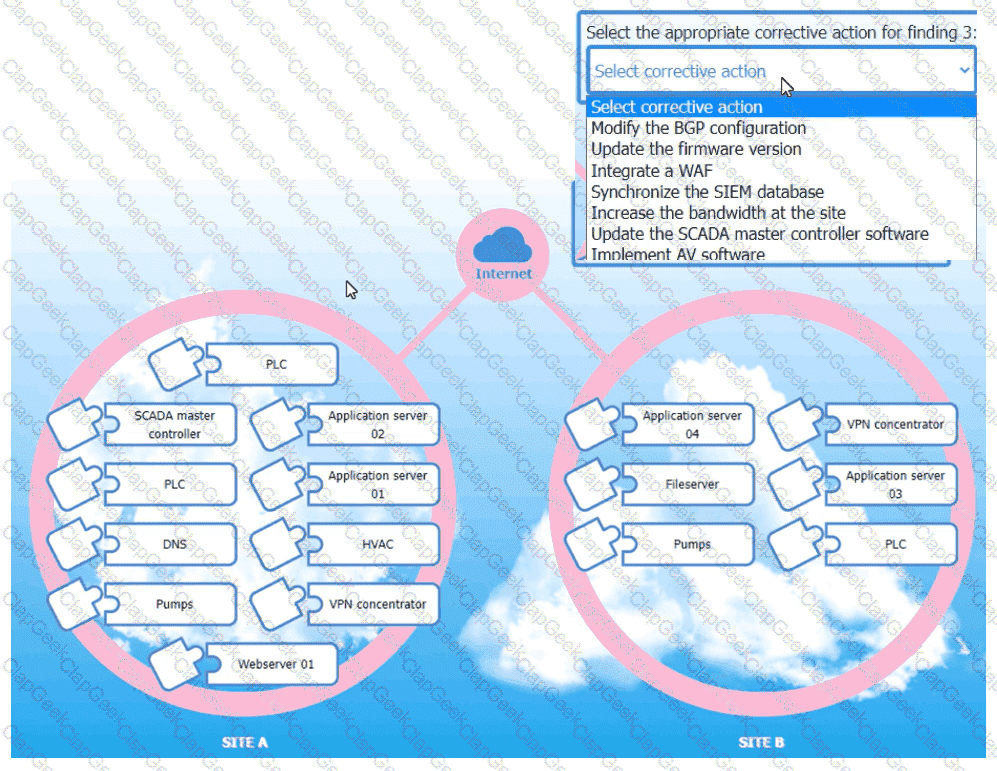
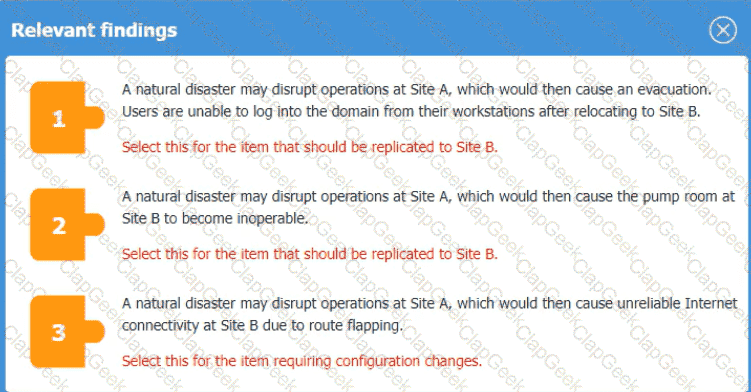
An organization is planning for disaster recovery and continuity ofoperations, and has noted the following relevant findings:
1. A natural disaster may disrupt operations at Site A, which would then cause an evacuation. Users are
unable to log into the domain from-their workstations after relocating to Site B.
2. A natural disaster may disrupt operations at Site A, which would then cause the pump room at Site B
to become inoperable.
3. A natural disaster may disrupt operations at Site A, which would then cause unreliable internet
connectivity at Site B due to route flapping.
INSTRUCTIONS
Match each relevant finding to the affected host by clicking on the host name and selecting the appropriate number.
For findings 1 and 2, select the items that should be replicated to Site B. For finding 3, select the item requiring configuration changes, then select the appropriate corrective action from the drop-down menu.
A security architect is establishing requirements to design resilience in un enterprise system trial will be extended to other physical locations. The system must
• Be survivable to one environmental catastrophe
• Re recoverable within 24 hours of critical loss of availability
• Be resilient to active exploitation of one site-to-site VPN solution
All organization is concerned about insider threats from employees who have individual access to encrypted material. Which of the following techniques best addresses this issue?
After a penetration test on the internal network, the following report was generated:
Attack Target Result
Compromised host ADMIN01S.CORP.LOCAL Successful
Hash collected KRBTGT.CORP.LOCAL Successful
Hash collected SQLSV.CORP.LOCAL Successful
Pass the hash SQLSV.CORP.LOCAL Failed
Domain control CORP.LOCAL Successful
Which of the following should be recommended to remediate the attack?
An organization is increasing its focus on training that addresses new social engineering and phishing attacks. Which of the following is the organization most concerned about?
After an incident occurred, a team reported during the lessons-learned review that the team.
* Lost important Information for further analysis.
* Did not utilize the chain of communication
* Did not follow the right steps for a proper response
Which of the following solutions is the best way to address these findinds?
A company wants to modify its process to comply with privacy requirements after an incident involving PII data in a development environment. In order to perform functionality tests, the QA team still needs to use valid data in the specified format. Which of the following best addresses the risk without impacting the development life cycle?
A cloud engineer needs to identify appropriate solutions to:
• Provide secure access to internal and external cloud resources.
• Eliminate split-tunnel traffic flows.
•Enable identity and access management capabilities.
Which of the following solutions arc the most appropriate? (Select two).
A cloud engineer wants to configure mail security protocols to support email authenticity and enable the flow of email security information to a third-party platform for further analysis. Which of the following must be configured to achieve these requirements? (Select two).
A security architect for a global organization with a distributed workforce recently received funding lo deploy a CASB solution Which of the following most likely explains the choice to use a proxy-based CASB?
Protected company data was recently exfiltrated. The SOC did not find any indication of a network or outside physical intrusion, and the DLP systems reported no unusual activity. The incident response team determined a text file was encrypted and reviews the following log excerpt:
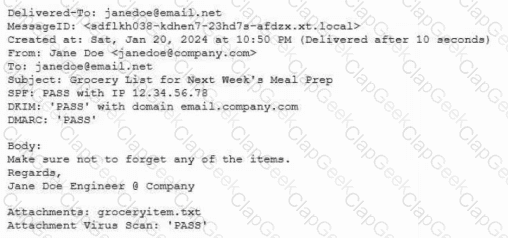
Which of the following is the most appropriate action for the team to take?
A security engineer wants to reduce the attack surface of a public-facing containerized application Which of the following will best reduce the application's privilege escalation attack surface?
After discovering that an employee is using a personal laptop to access highly confidential data, a systems administrator must secure the company's data. Which of the following capabilities best addresses this situation?
After remote desktop capabilities were deployed in the environment, various vulnerabilities were noticed.
• Exfiltration of intellectual property
• Unencrypted files
• Weak user passwords
Which of the following is the best way to mitigate these vulnerabilities? (Select two).
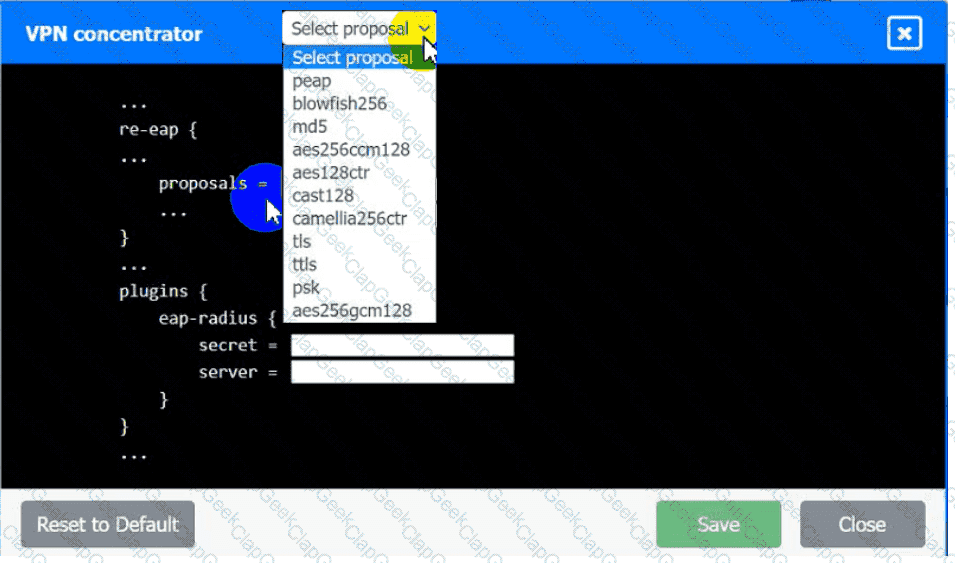
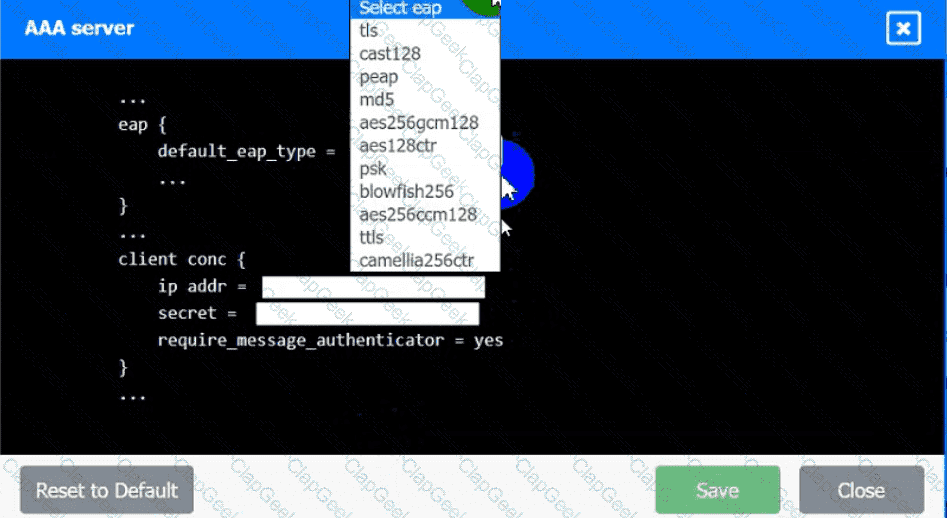
An IPSec solution is being deployed. The configuration files for both the VPN
concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With
issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure
authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase
character, one numeric character, and one special character, and it must
meet a minimumlength requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration.
Fill in the appropriate fields and make selections from the drop-down menus.
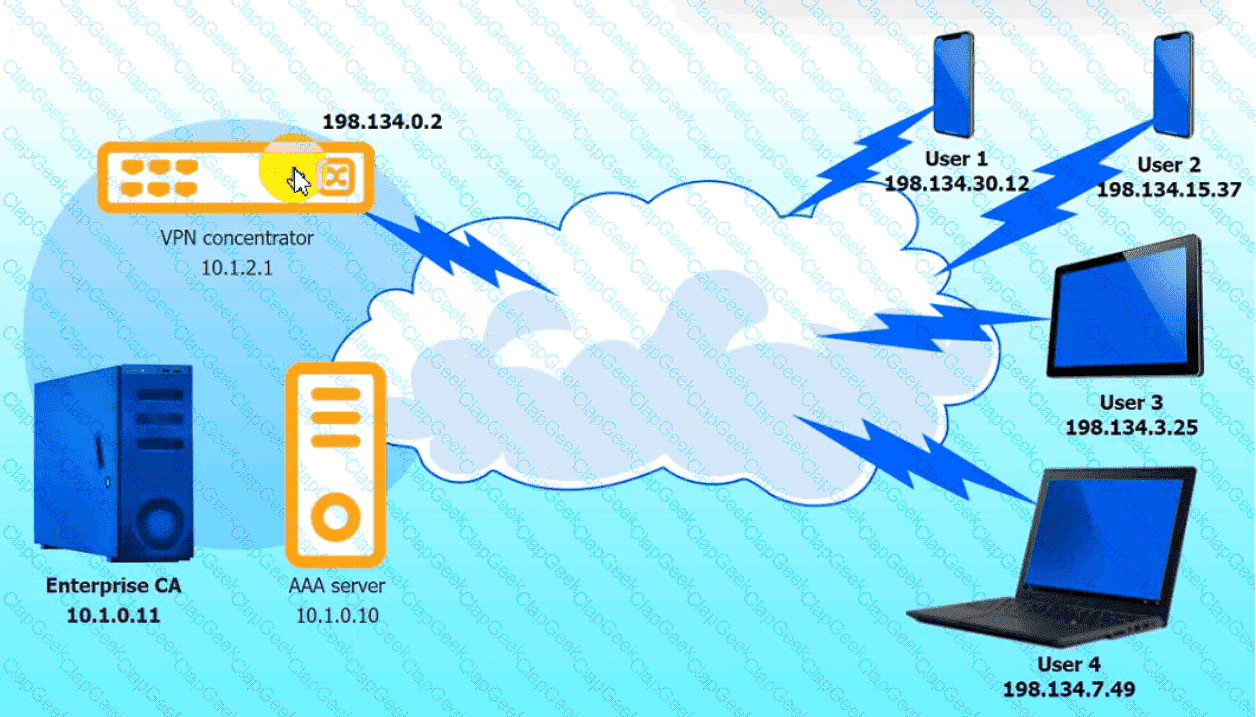
VPN Concentrator:
AAA Server:
A security operations engineer needs to prevent inadvertent data disclosure when encrypted SSDs are reused within an enterprise. Which of the following is the most secure way to achieve this goal?
A security manager at a local hospital wants to secure patient medical records. The manager needs to:
• Choose an access control model that clearly defines who has access to sensitive information.
• Prevent those who enter new patient information from specifying who has access to this data.
Which of the following access control models is the best way to ensure the lowest risk of granting unintentional access?
A security analyst is troubleshooting the reason a specific user is having difficulty accessing company resources The analyst reviews the following information:
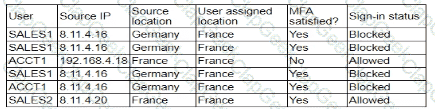
Which of the following is most likely the cause of the issue?
An organization wants to manage specialized endpoints and needs a solution that provides the ability to
* Centrally manage configurations
* Push policies.
• Remotely wipe devices
• Maintain asset inventory
Which of the following should the organization do to best meet these requirements?
Which of the following key management practices ensures that an encryption key is maintained within the organization?
A software development team requires valid data for internal tests. Company regulations, however do not allow the use of this data in cleartext. Which of the following solutions best meet these requirements?
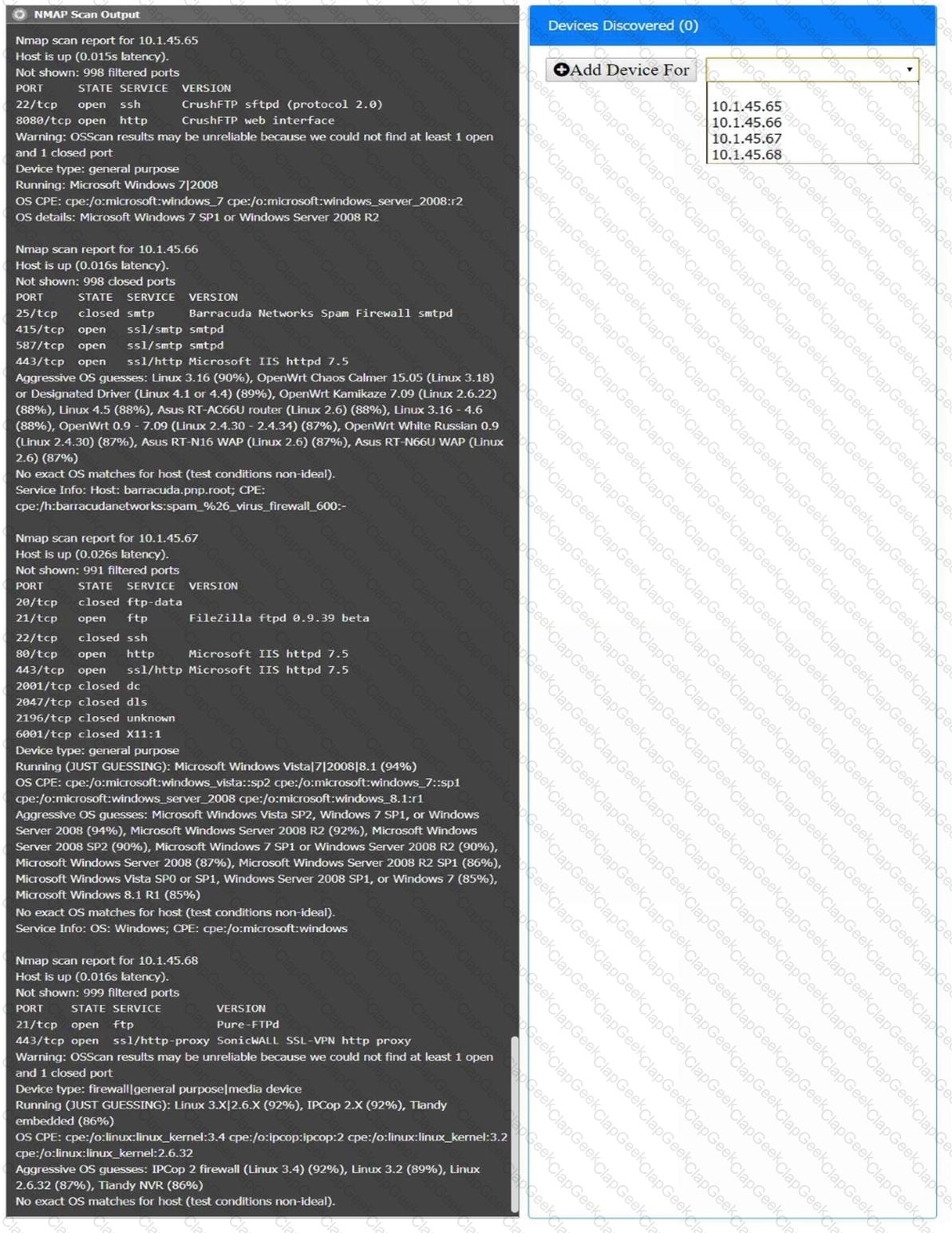
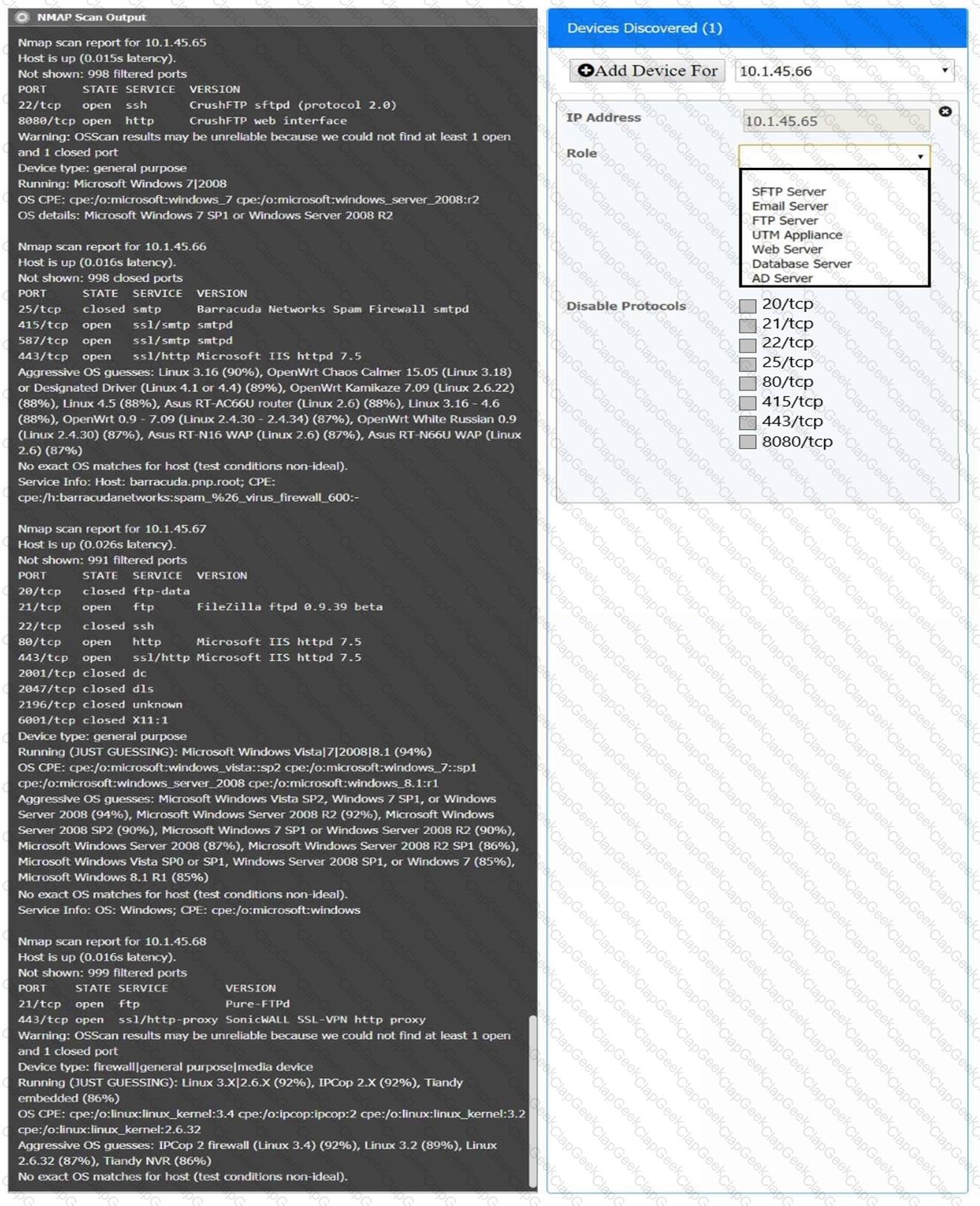
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An organization is developing on Al-enabled digital worker to help employees complete common tasks such as template development, editing, research, and scheduling. As part of the Al workload the organization wants to Implement guardrails within the platform. Which of the following should the company do to secure the Al environment?


