An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network, what action will resolve this issue?
In which two customer environments is the Cisco Secure Web Appliance Virtual connector traffic direction method selected? (Choose two.)
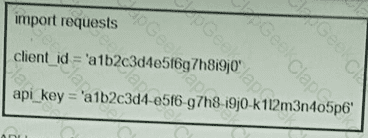
Refer to the exhibit. What function does the API key perform while working with https://api.amp.cisco.com/v1/computers?
A company deploys an application that contains confidential data and has a hybrid hub-and-spoke topology. The hub resides in a public cloud environment, and the spoke resides on-premises. An engineer must secure the application to ensure that confidential data in transit between the hub-and-spoke servers is accessible only to authorized users. The engineer performs these configurations:
Segregation of duties
Role-based access control
Privileged access management
What must be implemented to protect the data in transit?
What are two functionalities of northbound and southbound APIs within Cisco SDN architecture? (Choose two.)
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two)
An engineer must configure Cisco AMP for Endpoints so that it contains a list of files that should not be executed by users. These files must not be quarantined. Which action meets this configuration requirement?
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
Which type of dashboard does Cisco DNA Center provide for complete control of the network?
Which two actions does the Cisco identity Services Engine posture module provide that ensures endpoint security?(Choose two.)
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention
System?
Refer to the exhibit.

What does the API key do while working with https://api.amp.cisco.com/v1/computers?
Which action must be taken in the AMP for Endpoints console to detect specific MD5 signatures on endpoints and then quarantine the files?
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer data?
Due to a traffic storm on the network, two interfaces were error-disabled, and both interfaces sent SNMP traps.
Which two actions must be taken to ensure that interfaces are put back into service? (Choose two)
Refer to the exhibit.

Refer to the exhibit. A Cisco ISE administrator adds a new switch to an 802.1X deployment and has difficulty with some endpoints gaining access.
Most PCs and IP phones can connect and authenticate using their machine certificate credentials. However printer and video cameras cannot base d on the interface configuration provided, what must be to get these devices on to the network using Cisco ISE for authentication and authorization while maintaining security controls?
Refer to the exhibit.
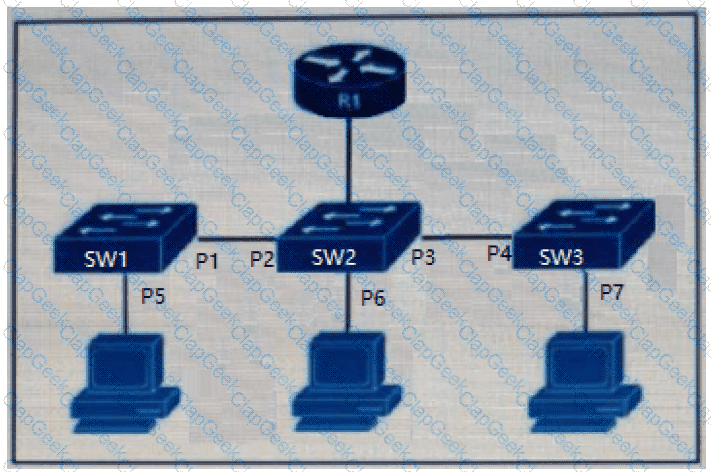
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
An organization recently installed a Cisco Secure Web Appliance and would like to take advantage of the AVC engine to allow the organization to create a policy to control application-specific activity. After enabling the AVC engine, what must be done to implement this?
While using Cisco Secure Firewall's Security Intelligence policies, which two criteria is blocking based upon? (Choose two.)
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
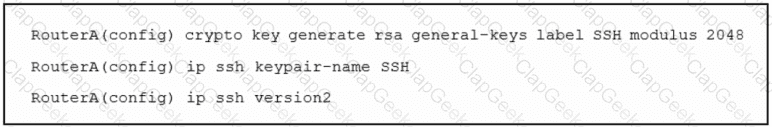
Refer to the exhibit. An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.)
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability
would help an attacker brute force their way into the systems?
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
Which characteristic is unique to a Cisco WSAv as compared to a physical appliance?
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
What is a benefit of using Cisco AVC (Application Visibility and Control) for application control?
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration?
An engineer is configuring cloud logging on Cisco ASA and needs events to compress. Which component must be configured to accomplish this goal?
An engineer is deploying a Cisco Secure Email Gateway and must ensure it reaches the Cisco update servers to retrieve new rules. The engineer must now manually configure the Outbreak Filter rules on an AsyncOS for Cisco Secure Email Gateway. Only outdated rules must be replaced. Up-to-date rules must be retained. Which action must the engineer take next to complete the configuration?
Which method of attack is used by a hacker to send malicious code through a web application to an unsuspecting user to request that the victim's web browser executes the code?
Which method must be used to connect Cisco Secure Workload to external orchestrators at a client site when the client does not allow incoming connections?
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
An engineer is adding a Cisco router to an existing environment. NTP authentication is configured on all devices in the environment with the command ntp authentication-key 1 md5 Clsc427128380. There are two routers on the network that are configured as NTP servers for redundancy, 192.168.1.110 and 192.168.1.111. 192.168.1.110 is configured as the authoritative time source. What command must be configured on the new router to use 192.168.1.110 as its primary time source without the new router attempting to offer time to existing devices?
For which two conditions can an endpoint be checked using ISE posture assessment? (Choose two)
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access The Cisco ESA must also join a cluster machine using preshared keys What must be configured to meet these requirements?
After deploying a Cisco ESA on your network, you notice that some messages fail to reach their destinations.
Which task can you perform to determine where each message was lost?
Which security solution is used for posture assessment of the endpoints in a BYOD solution?
Which CLI command is used to register a Cisco FirePower sensor to Firepower Management Center?
What is a functional difference between Cisco Secure Endpoint and Cisco Umbrella Roaming Client?
A Cisco Secure Cloud Analytics administrator is setting up a private network monitor sensor to monitor an on-premises environment. Which two pieces of information from the sensor are used to link to the Secure Cloud Analytics portal? (Choose two.)
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis?
Which two capabilities of Integration APIs are utilized with Cisco DNA center? (Choose two)
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also
provides an option to specify HTTP/TFTP commands to perform file retrieval from the server?
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA?
A company recently discovered an attack propagating throughout their Windows network via a file named abc428565580xyz exe The malicious file was uploaded to a Simple Custom Detection list in the AMP for Endpoints Portal and the currently applied policy for the Windows clients was updated to reference the detection list Verification testing scans on known infected systems shows that AMP for Endpoints is not detecting the presence of this file as an indicator of compromise What must be performed to ensure detection of the malicious file?
An engineer is adding a Cisco DUO solution to the current TACACS+ deployment using Cisco ISE. The engineer wants to authenticate users using their account when they log into network devices. Which action accomplishes this task?
What does Cisco ISE use to collect endpoint attributes that are used in profiling?
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices The default management port conflicts with other communications on the network and must be changed What must be done to ensure that all devices can communicate together?
Which two protocols must be configured to authenticate end users to the Web Security Appliance? (Choose two.)
A university policy must allow open access to resources on the Internet for research, but internal workstations are exposed to malware. Which Cisco AMP feature allows the engineering team to determine whether a file is installed on a selected few workstations?
When a transparent authentication fails on the Web Security Appliance, which type of access does the end user get?
What are two facts about WSA HTTP proxy configuration with a PAC file? (Choose two.)
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
Which file type is supported when performing a bulk upload of destinations into a destination list on Cisco Umbrella?
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system’s applications. Which
vulnerability allows the attacker to see the passwords being transmitted in clear text?
An administrator is configuring N I P on Cisco ASA via ASDM and needs to ensure that rogue NTP servers cannot insert themselves as the authoritative time source Which two steps must be taken to accomplish this task? (Choose two)
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
Based on the NIST 800-145 guide, which cloud architecture may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises?
Which functions of an SDN architecture require southbound APIs to enable communication?
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization
needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of
172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
Which CoA response code is sent if an authorization state is changed successfully on a Cisco IOS device?
An organization has noticed an increase in malicious content downloads and wants to use Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web traffic. Which action will accomplish this task?
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature?
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption?
An administrator needs to configure the Cisco ASA via ASDM such that the network management system
can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration?
(Choose two.)
Which two actions does the Cisco ISE posture module provide that ensures endpoint security? (Choose two.)
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat?
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a
proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured
to select when to connect direct or when to use the proxy?
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this
requirement using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
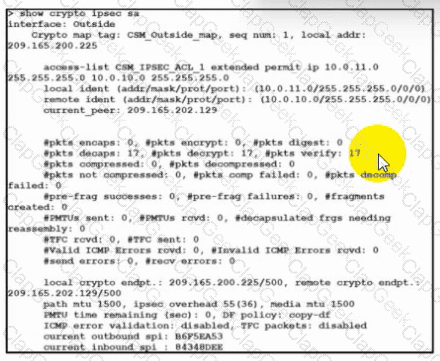
Refer to the exhibit. Traffic is not passing through IPsec site-to-site VPN on the Secure Firewall Threat Defense appliance. What is causing this issue?
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint?
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures The configuration is created in the simple detection policy section, but it does not work What is the reason for this failure?
An organization wants to use Cisco FTD or Cisco ASA devices. Specific URLs must be blocked from being
accessed via the firewall which requires that the administrator input the bad URL categories that the
organization wants blocked into the access policy. Which solution should be used to meet this requirement?
Which attack type attempts to shut down a machine or network so that users are not able to access it?
Which command is used to log all events to a destination colector 209.165.201.107?
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization?
Which baseline form of telemetry is recommended for network infrastructure devices?
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains IPs, and flies, and helps to pinpoint attackers' infrastructures and predict future threat?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites
but other sites are not accessible due to an error. Why is the error occurring?
Drag and drop the exploits from the left onto the type of security vulnerability on the right.
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
Which type of data does the Cisco Stealthwatch system collect and analyze from routers, switches, and firewalls?
A network engineer must migrate a Cisco WSA virtual appliance from one physical host to another physical host by using VMware vMotion. What is a requirement for both physical hosts?
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
Drag and drop the deployment models from the left onto the explanations on the right.
An engineer must implement a file transfer solution between a company's data center and branches. The company has numerous servers hosted in a hybrid cloud implementation. The file transfer protocol must support authentication, protect the data against unauthorized access, and ensure that users cannot list directories or remove files remotely. Which protocol must be used?
When MAB is configured for use within the 802.1X environment, an administrator must create a policy that allows the devices onto the network. Which information is used for the username and password?
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
Which VPN technology supports a multivendor environment and secure traffic between sites?
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two)
Refer to the exhibit.
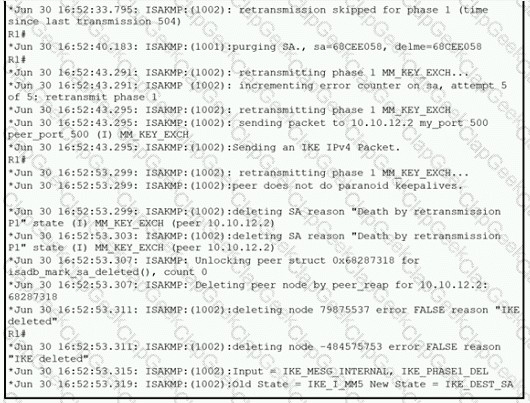
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
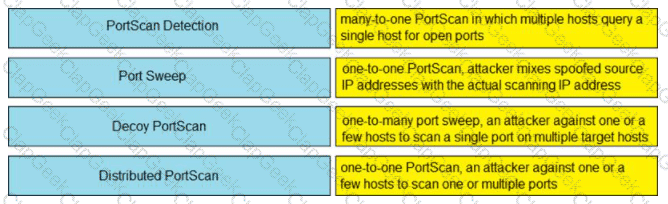
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
Which solution stops unauthorized access to the system if a user's password is compromised?
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA Center?
A security test performed on one of the applications shows that user input is not validated. Which security vulnerability is the application more susceptible to because of this lack of validation?
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router?
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems?
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized
solution. The organization does not have a local VM but does have existing Cisco ASAs that must migrate over
to Cisco FTDs. Which solution meets the needs of the organization?
An engineer is implementing DHCP security mechanisms and needs the ability to add additional attributes to profiles that are created within Cisco ISE Which action accomplishes this task?
Which type of protection encrypts RSA keys when they are exported and imported?
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?
Which type of dashboard does Cisco Catalyst Center provide for complete control of the network?
During a recent security audit a Cisco IOS router with a working IPSEC configuration using IKEv1 was flagged for using a wildcard mask with the crypto isakmp key command The VPN peer is a SOHO router with a dynamically assigned IP address Dynamic DNS has been configured on the SOHO router to map the dynamic IP address to the host name of vpn sohoroutercompany.com In addition to the command crypto isakmp key Cisc425007536 hostname vpn.sohoroutercompany.com what other two commands are now required on the Cisco IOS router for the VPN to continue to function after the wildcard command is removed? (Choose two)
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
Refer to the exhibit.

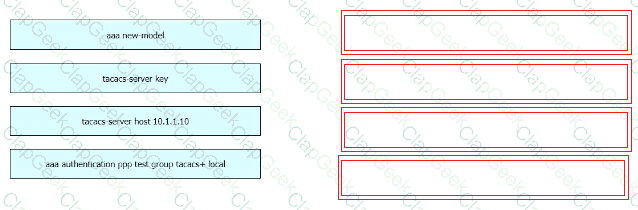
An engineer must configure a Cisco switch to perform PPP authentication via a TACACS server located at IP address 10.1.1.10. Authentication must fall back to the local database using the username LocalUser and password C1Sc0451069341l if the TACACS server is unreachable.
Drag and drop the commands from the left onto the corresponding configuration steps on the right.
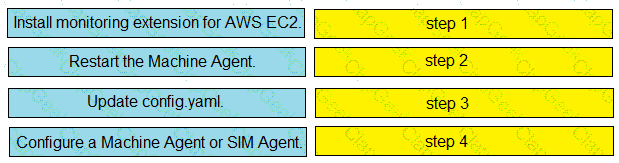
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.
For which type of attack is multifactor authentication an effective deterrent?
A large organization wants to deploy a security appliance in the public cloud to form a site-to-site VPN
and link the public cloud environment to the private cloud in the headquarters data center. Which Cisco
security appliance meets these requirements?
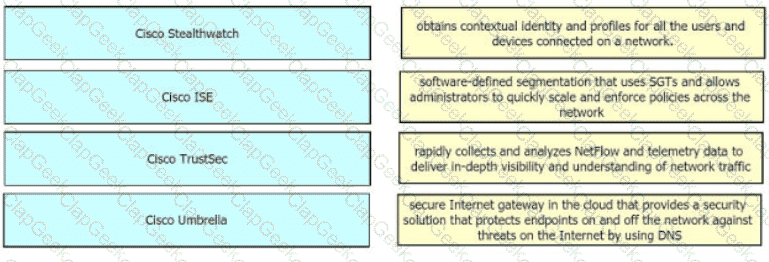
Drag and drop the solutions from the left onto the solution's benefits on the right.
Which action configures the IEEE 802.1X Flexible Authentication feature to support Layer 3 authentication mechanisms?
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users. Which action accomplishes this goal?
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers
and can be stopped by Cisco Umbrella?
Which feature is used in a push model to allow for session identification, host reauthentication, and session termination?
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
What is the process In DevSecOps where all changes In the central code repository are merged and synchronized?
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively used by devices, using many of the default policy elements.
What else must be done to accomplish this task?
When a Cisco Secure Web Appliance checks a web request, what occurs if it is unable to match a user-defined policy?
Refer to the exhibit.
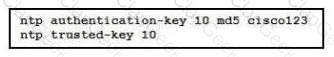
A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced What is the cause of this issue?
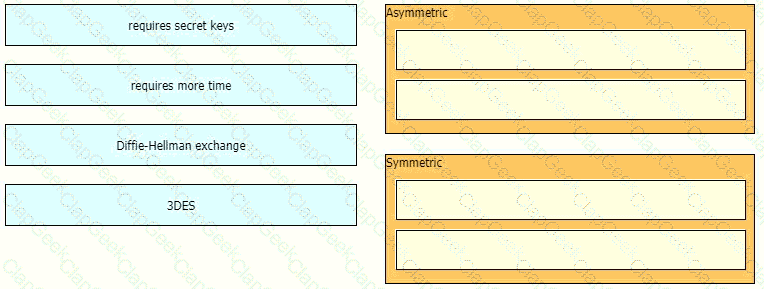
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
Which API method and required attribute are used to add a device into Cisco DNA Center with the native API?
A customer has various external HTTP resources available including Intranet. Extranet, and Internet, with a proxy configuration running in explicit mode Which method allows the client desktop browsers to be configured to select when to connect direct or when to use the proxy?
Which two behavioral patterns characterize a ping of death attack? (Choose two)
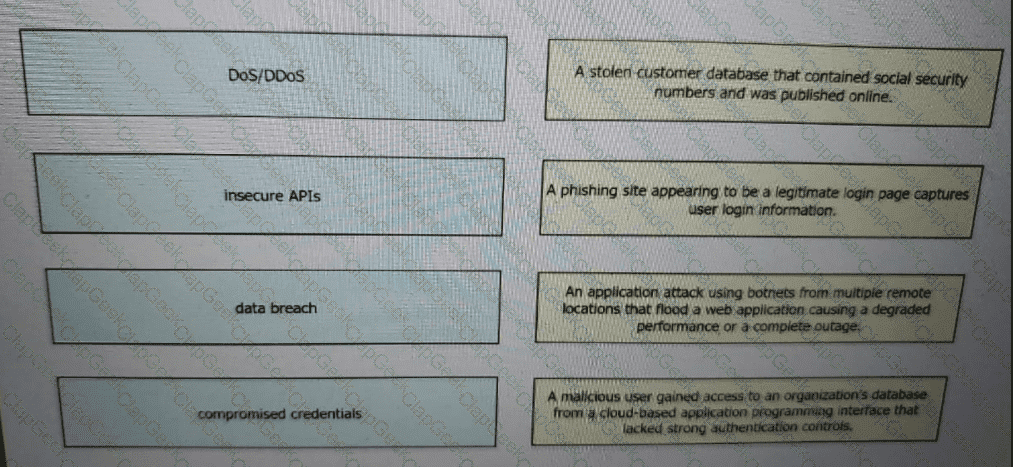
Drag and drop the threats from the left onto examples of that threat on the right
Which benefit is provided by ensuring that an endpoint is compliant with a posture policy configured in Cisco ISE?
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?
Which action configures the IEEE 802.1X Flexible Authentication feature lo support Layer 3 authentication mechanisms?
An engineer is trying to securely connect to a router and wants to prevent insecure algorithms from being used.
However, the connection is failing. Which action should be taken to accomplish this goal?
What are two list types within AMP for Endpoints Outbreak Control? (Choose two)
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
An email administrator is setting up a new Cisco ESA. The administrator wants to enable the blocking of greymail for the end user. Which feature must the administrator enable first?
A security engineer must add destinations into a destination list in Cisco Umbrella. What describes the application of these changes?
Which two configurations must be made on Cisco ISE and on Cisco TrustSec devices to force a session to be adjusted after a policy change is made? (Choose two)
Which policy does a Cisco Secure Web Appliance use to block or monitor URL requests based on the reputation score?
An organization is implementing AAA for their users. They need to ensure that authorization is verified for every command that is being entered by the network administrator. Which protocol must be configured in order to provide this capability?
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
Which Cisco solution provides a comprehensive view of Internet domains. IP addresses, and autonomous systems to help pinpoint attackers and malicious infrastructures?
Which service allows a user export application usage and performance statistics with Cisco Application Visibility
and control?
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System? (Choose two)
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.)
When network telemetry is implemented, what is important to be enabled across all network infrastructure devices to correlate different sources?
An organization must add new firewalls to its infrastructure and wants to use Cisco ASA or Cisco FTD.
The chosen firewalls must provide methods of blocking traffic that include offering the user the option to bypass the block for certain sites after displaying a warning page and to reset the connection. Which solution should the organization choose?
An organization wants to improve its cybersecurity processes and to add intelligence to its data The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA What must be done to accomplish these objectives?
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection?
Which portion of the network do EPP solutions solely focus on and EDR solutions do not?
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social
engineering attacks? (Choose two)
Which type of algorithm provides the highest level of protection against brute-force attacks?
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.)
What are two reasons for implementing a multifactor authentication solution such as Duo Security provide to an
organization? (Choose two)
Which industry standard is used to integrate Cisco ISE and pxGrid to each other and with other
interoperable security platforms?
What is the purpose of the Trusted Automated exchange cyber threat intelligence industry standard?
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a
recipient address. Which list contains the allowed recipient addresses?
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view
of activity?
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two)
An engineer used a posture check on a Microsoft Windows endpoint and discovered that the MS17-010 patch
was not installed, which left the endpoint vulnerable to WannaCry ransomware. Which two solutions mitigate
the risk of this ransom ware infection? (Choose two)
Which Cisco DNA Center RESTful PNP API adds and claims a device into a workflow?


