Refer to the exhibit.
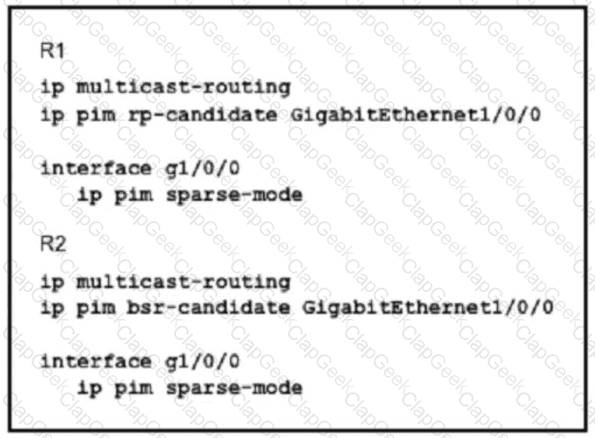
An engineer is configuring an administrative domain in the given multi-vendor environment with PIM-SM. Which feature must the engineer implement so that devices will dynamically learn the RP?
Which three OSPF parameters must match before two devices can establish an OSPF adjacency? (Choose three.)
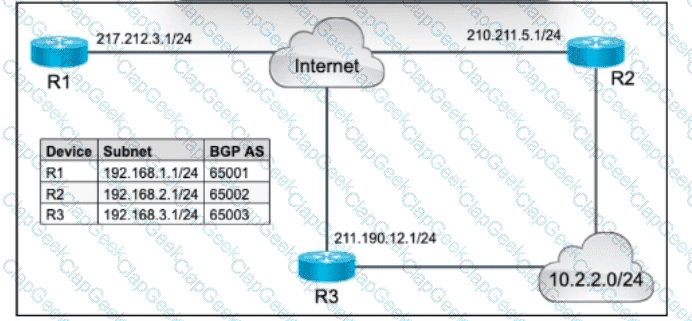
Refer to the exhibit. A growing company wants to ensure high availability and redundancy for its critical web servers, which are located in an offsite data center. The network architect decided to implement BGP so that the network can use redundant paths for outbound traffic toward the destination subnet 10.2.2.0/24. A network engineer already configured basic BGP settings on edge router R1, which is a Cisco ASR-1001X router. The engineer also confirmed loopback reachability to routers R2 and R3, and the AS path length toward the destination is the same via R2 and R3. Which action must the engineer take on R1 to complete the implementation?
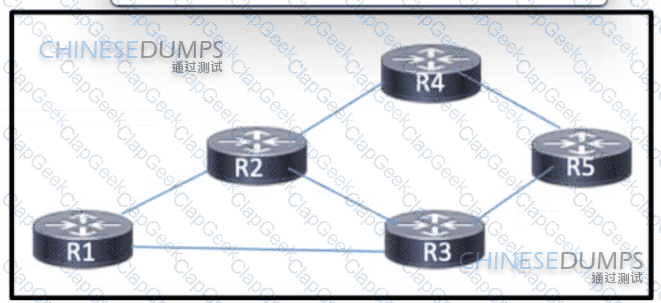
Refer to the exhibit. Routers R1 through R5 are being deployed within the core of a service provider running BGP The core supports distribution of VPNv4 routes using MPLS. R3 currently has multiple paths to reach R4. A network engineer must implement BGP attributes so that R3 can reach R4 via R1. Which action must the engineer take to meet the requirement?
An engineer is configuring IEEE 802.1 ad on the access port on a new Cisco router. The access port handles traffic from multiple customer VLANs, and it is expected to mark all customer traffic to the same VLAN without dropping any traffic. Which configuration must the engineer apply?
A)

B)

C)

D)

Refer to the exhibit.
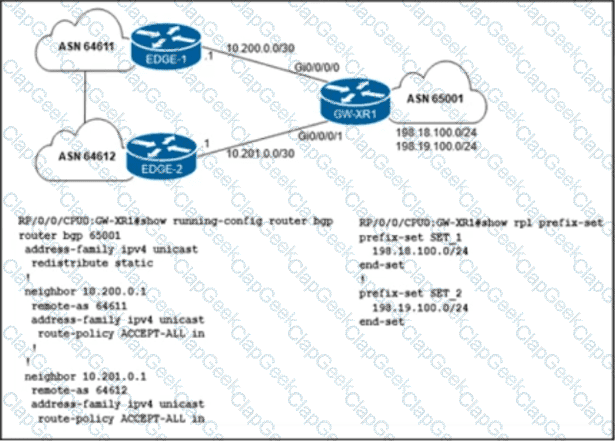
The network engineer who manages ASN 65001 must configure a BGP routing policy on GW-XR1 with these requirements:
• Advertise locally-originated routes and /24 prefixes assigned within the 198.18.0.0/15 range. All other prefixes must be dropped.
• Reachability to 198.18.100.0/24 must be preferred via the EDGE-1 connection.
• Reachability to 198.19.100.0/24 must be preferred via the EDGE-2 connection.
Which configuration must the network engineer implement on GW-XR1?
Refer to the exhibit.
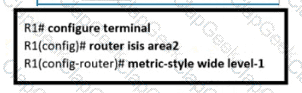
An engineer is configuring multitopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to the router to complete the task?

Refer to the exhibit.
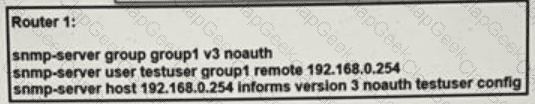
A network engineer is deploying SNMP configuration on client's routers. Encrypted authentication must be included on router 1 to provide security and protect message confidentially. Which action should the engineer perform on the routers to accomplish this task?
Refer to the exhibit.
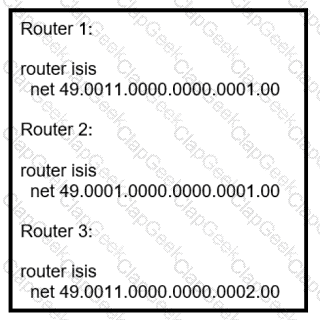
Router 4 is added to the network and must be in the same area as router 1. Which NET should the engineer assign?
Refer to the exhibit.

AN engineer is configuring segment routing on an ISP to simplify traffic engineering and management across network domains. What should the engineer do to complete the implementation of segment routing?
Refer to Exhibit.
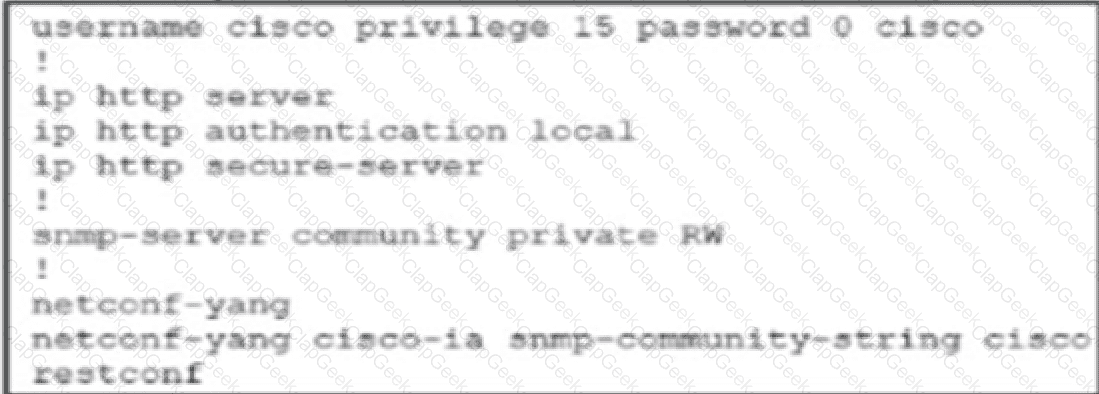
A network engineer is trying to retrieve SNMP MIBs with RESTCONF on the Cisco switch but fails. End-to-end routing is in place. Which configuration must the engineer implement on the switch to complete?
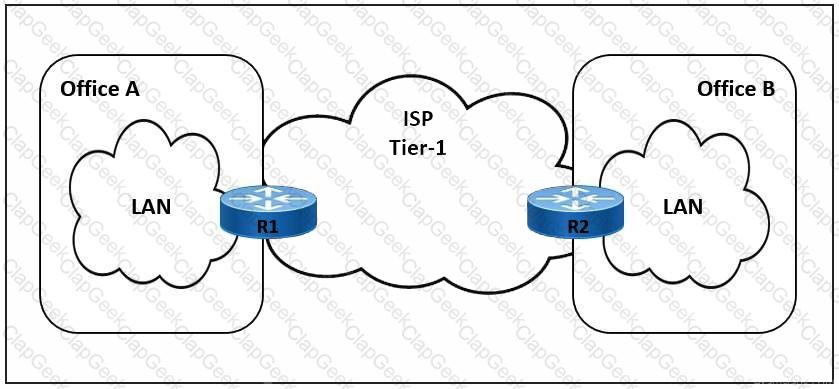
Refer to the exhibit. The link between Office A and Office B is running at 90% load, and occasionally the CPU on router R1 is overloaded. The company implemented QoS for business-critical applications at both offices as a temporary solution. A network engineer must update the R1 configuration to 600 ms to reduce CPU load and limit downtime after connection failure to avoid data loss. Which action meets this requirement?
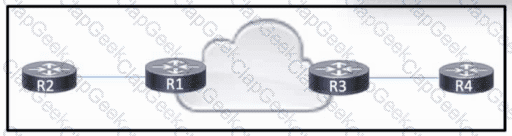
Refer to the exhibit. R1 and R3 have a pseudowire connection between them, which allows R2 and R4 to communicate via Layer 2. R2 uses VLAN 10. R4 also uses VLAN 10, but with a different subnet associated.
Which configuration should the engineer apply to R3 to rewrite the VLAN on traffic from R2 to VLAN 15?
Refer to the exhibit:
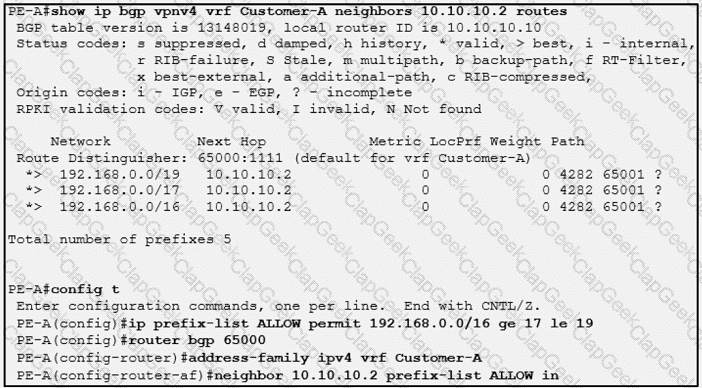
Which three outcomes occur if the prefix list is added to the neighbor? (Choose three)
According to RFC5305 on IS-IS extensions for traffic engineering, what is the 4-octet sub-TLV type 10 of extended IS-IS reachability TLV type 22?
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network. Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
After implement MPLS protocol for multiple VRFs on a single Cisco device, the engineer notices all VRFs on the router still do to not LDP session protection feature enabled. Which configuration must the engineer apply to enable the LDP session protection feature FOR LDP neighbors within each VRF?
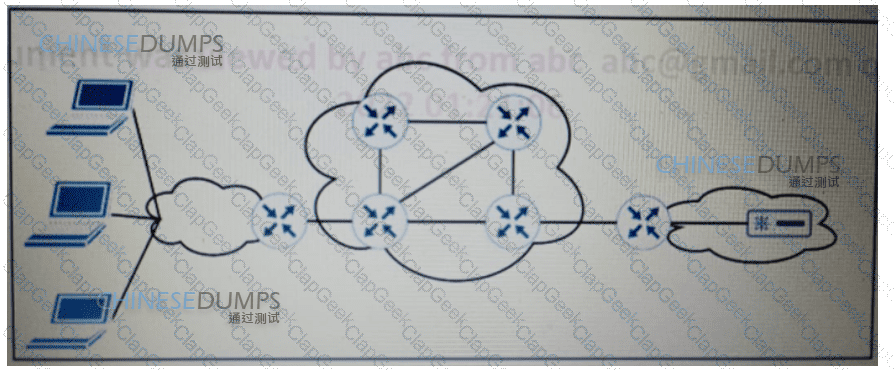
Refer to the exhibit. ISP A provides VPLS services and DDoS protection to Company XYZ to connect their branches across the North America and Europe regions. The uplink from the data center to the ISP is Mbps. The company XYZ security team asked the ISP to redirect ICMP requests which are currently going to the web server to a new local security appliance which configuration must an ISPP engineer apply to router R2 to redirect the ICMP traffic?
A)

B)

C)

D)

Refer to the exhibit.
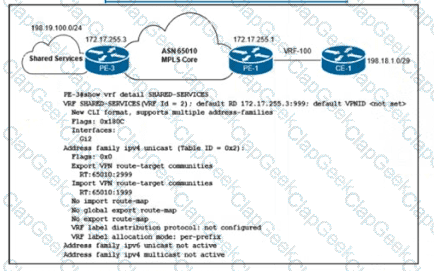
Refer to the exhibit. An ISP provides shared VoIP Extranet services to a customer in VRF-100 with these settings:
The VoIP services are hosted in the 198.19.100.0/24 space.
The customer has been assigned the 198.18.1.0/29 IP address block.
VRF-100 is assigned import and export route target 65010:100.
Which configuration must the engineer apply to PE-1 to provision VRF-100 and provide access to the shared services?
How do intent APIs make it easier for network engineers to deploy and manage networks?

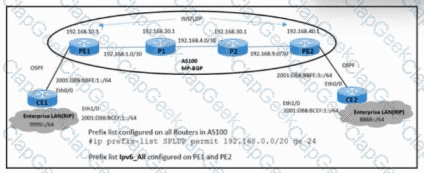
Refer to the exhibit. An engineer must update the configuration of the network with these requirements:
PE routers must define labels for IS-IS learned routes in AS100.
P routers must not receive LDP bindings for the external network in the IPv6 address family.
Which configuration must the engineer implement to meet these requirements?
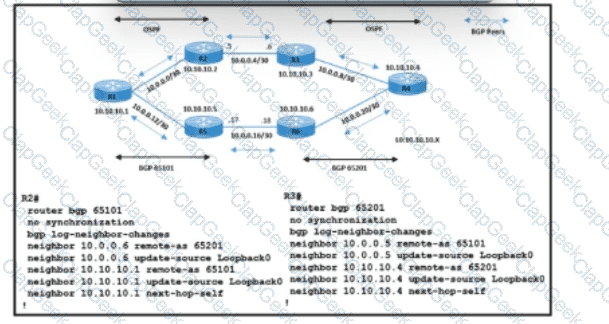
Refer to the exhibit. A network operations team is implementing eBGP on the service provider network. Data traffic between routers R1 and R4 must use the R2-R3 link, which connects AS 65101 and AS65201. iBGP sessions with adjacent routers are up on 10.10.10.1 and 10.10.10.4. The team is now updating the configuration for eBGP peers on routers R2 and R3. Which action must be taken to meet the requirements?
A service provider is in the process of implementing Unified MPLS on an enterprise network with many nodes. After the migration, several new customers will be added to the environment. RFC 3107 is used to build BGP LSPs across the domains. Which action must the networking team take to reduce the full-mesh requirement for IBGP?
An engineer is implementing IGMP with SSM on a multicampus network that supports video streaming. Which task must the engineer perform as part of the process?
Refer to the exhibit:
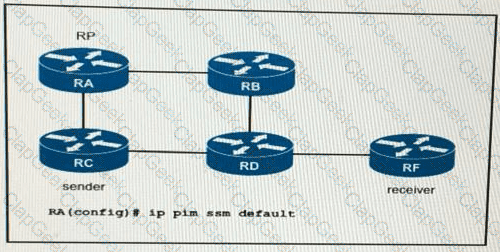
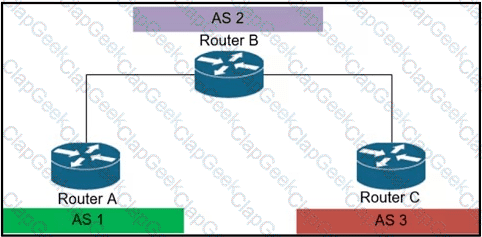
If router RA is configured as shown, which IPv4 multicast address space does it use?

Refer to the exhibit. The ISP is implementing a new hosting-as-a-service solution for its business customers. Service accessibility must be unique and separate for each customer. The network architect must ensure that multiple paths toward the hosting-as-a-service solution are always available. Basic protection against traffic black-holing on the MPLS network is required in case of link failure. Which two actions must the engineering team perform to meet the requirements? (Choose two.)
Refer to the exhibit.
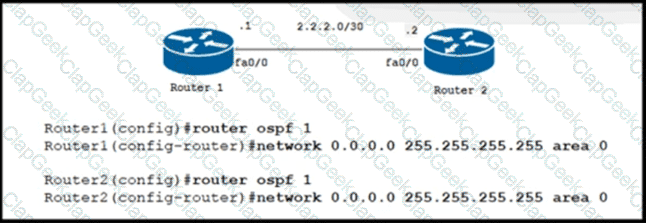
A network engineer must configure an LDP neighborship between two newly installed routers that are located in two different offices. Router 1 is the core router in the network and it has already established OSPF adjacency with router 2. On router 1 and router 2. interface fa0/0 is configured for BFD. Which additional configuration must the engineer apply to the two devices to meet the requirement?
How do CSC VPN services use BGP to support connectivity between customer sites?
Refer to the exhibit.
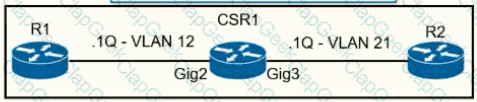
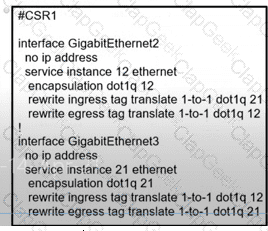
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively. Which configurator accomplishes this task?
A)

B)
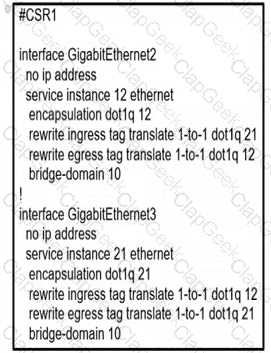
C)
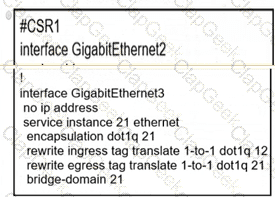
D)
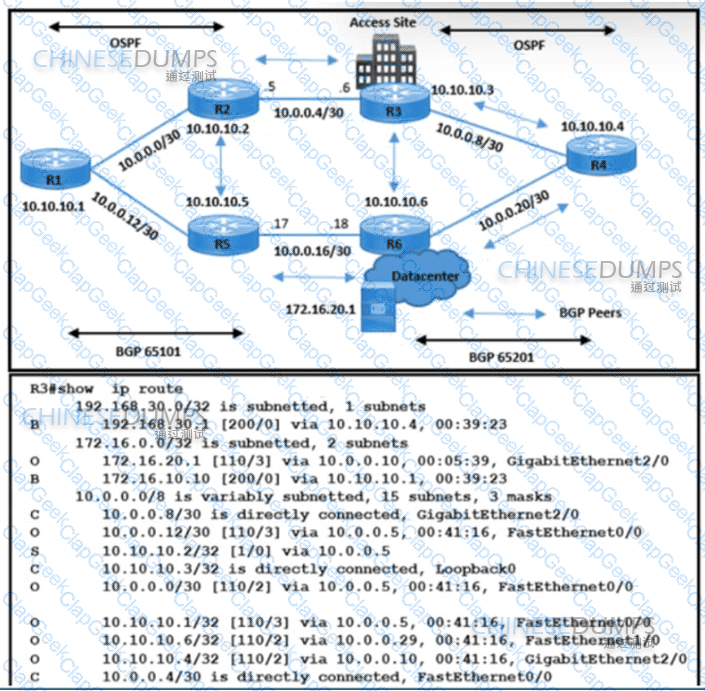
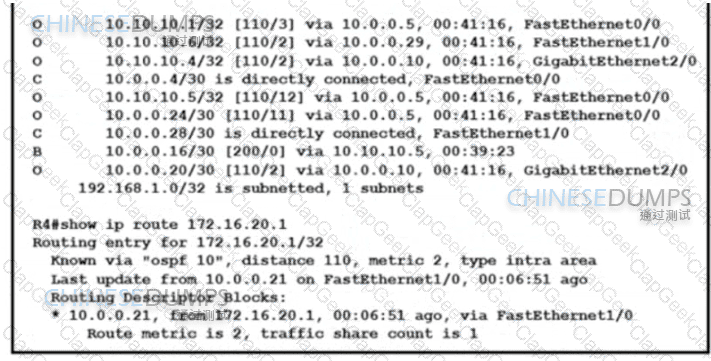
Refer to the exhibit. The network operations team reported that the access site that is connected to R3 is not connecting to the application server in the data center and that all packets that are sent from the application server to the access site are dropped. The team verified that OSPF and BGP peerings are up in BGP AS 65101 and BGP AS 65201. R4 is expected to receive traffic from the application server route via OSPF. Which action resolves this issue?
Refer to the exhibit:
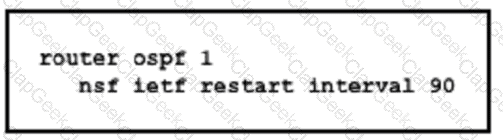
Which purpose of implementing NSF with this configuration is true?
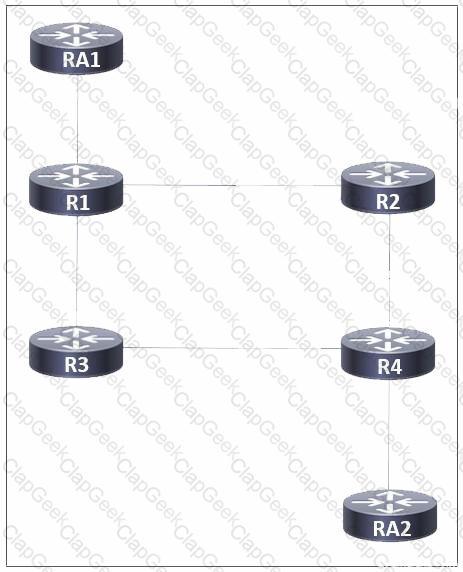
Refer to the exhibit. A network administrator implemented MPLS routing between routers R1, R2, R3, and R4. AToM is configured between R1 and R4 to allow Layer 2 traffic from hosts on RA1 and RA2. A targeted MPLS session is established between R1 and R4. Which additional action must the administrator take on all routers so that LDP synchronization occurs between connected LDP sessions?
Refer to the exhibit.
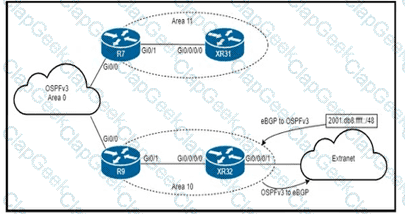
An engineer is updating this network to meet these conditions:
• Area 10 will receive inter-area routes and support mutual redistribution of external routes with the extranet.
• The ::/0 route is prohibited in Area 10.
• Area 11 will receive only the ::/0 route from the ABR.
• External route redistribution is not supported in Area 11.
• The ABR in Area 11 will advertise no interarea routes.
Which two configurations must be performed to meet the requirements? (Choose two.)
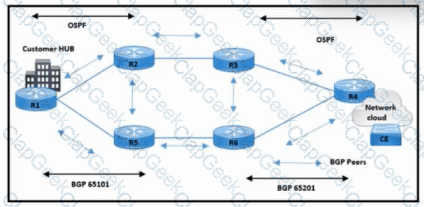
Refer to the exhibit. The NOC is configuring PE router R4 for BGP-originated traffic. R4 is connected to a CE device at a customer location. The customer requires:
BGP peers must establish a neighborship with NSR and NSF capability.
BGP must maintain state with the CE and provide continuous forwarding during ISSU and RP switchover events.
Which action meets the NSR requirement on PE routers?
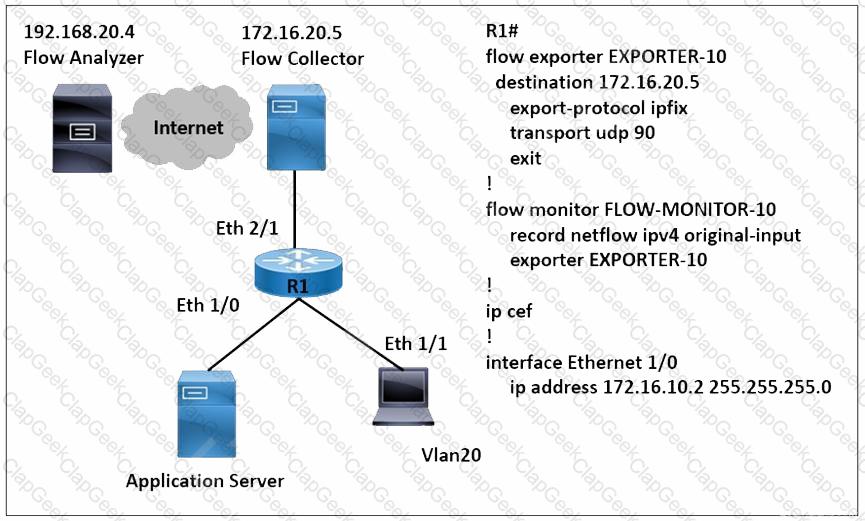
Refer to the exhibit. A network engineer wants to monitor traffic from the application server and send the output to the external monitoring device at 172.16.20.5. Application server traffic should pass through the R1 Eth2/1 interface for further analysis after it is monitored. Which configuration must be applied on the R1 router?
Which capability does the MPLS TE FRR facility backup protection method provide?
Company A is implementing VoIP services across the company. The network architect designed a QoS policy to allow only specific IP subnets and mark the signaling flow with DSCP 36. The solution should be as secure as possible. Phones receive their IP addresses from the 172.184.12.0/24 pool and are assigned by the RADIUS server to VLAN 1021. Skinny Client Control Protocol is used as a signaling protocol in the network. For security reasons, switchport port-security maximum 1 vlan voice has been preconfigured on the switch side. Which two tasks must an engineer perform on SW_1 to achieve this goal? (Choose two.)
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
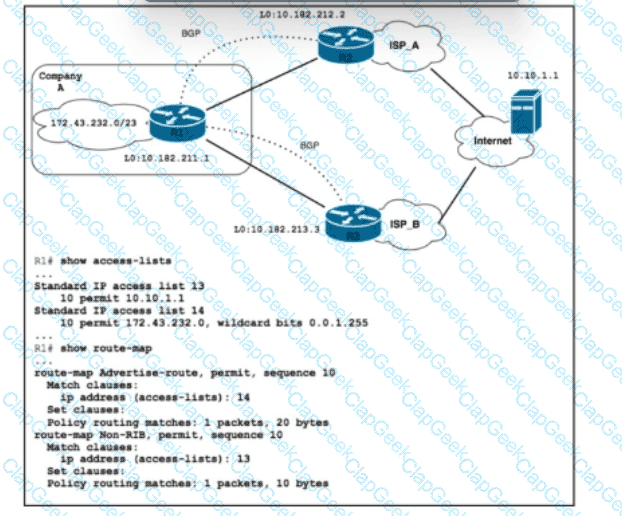
Refer to the exhibit. Company A is connected to multiple upstream ISPs, with ISP_A serving as the primary upstream ISP. The company A subnet 172.43.232.0 should be announced to the secondary ISP_B only when the FTP server with IP address 10.10.1.1 is not accessible via the primary ISP. Which configuration must be applied on R1?
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
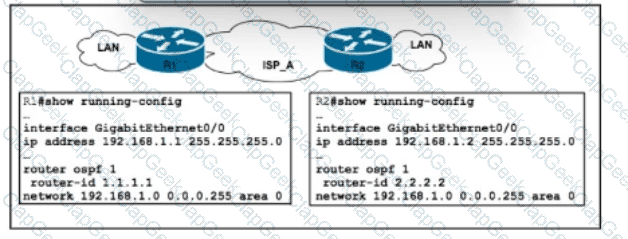
Refer to the exhibit. A growing company with an increasing international presence requires a secure and scalable solution for inter-office data transfer across their geographically dispersed locations. To ensure departmental privacy, the network must enforce granular access control. BGP is running in the network, and two VRF instances with unique route distinguishers and route targets have been configured to segregate critical financial data from regular network traffic. A network engineer with an employee ID: 5086:72:617 must find a solution that allows for future network expansion while maintaining robust security and data privacy between departments. The solution must comply with the RFC 4364 standard. Which action must the engineer take to meet the requirements?
Drag and drop the LDP features from the left onto the correct usages on the right.

An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?




Refer to the exhibit.
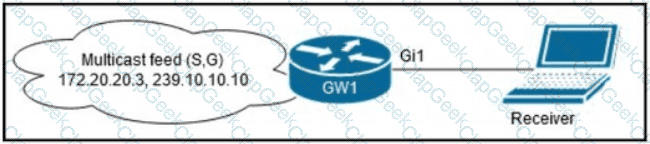
A network administrator is implementing IGMP to enable multicast feed transmission to the receiver. Which configuration must the administrator deploy on GW1 to permit IGMP Joins only to the assigned (S, G) feed?
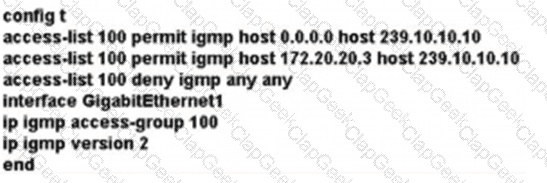
A)
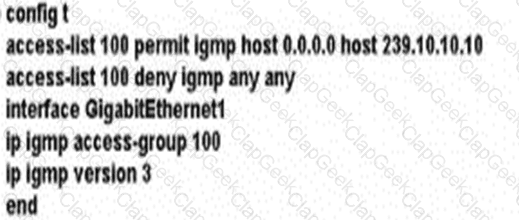
B)
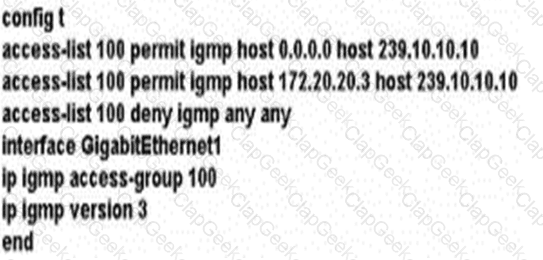
C)
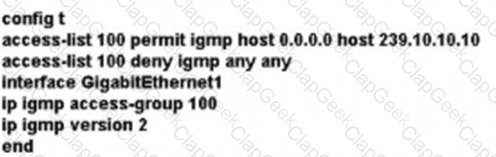
D)
Refer to the exhibit.
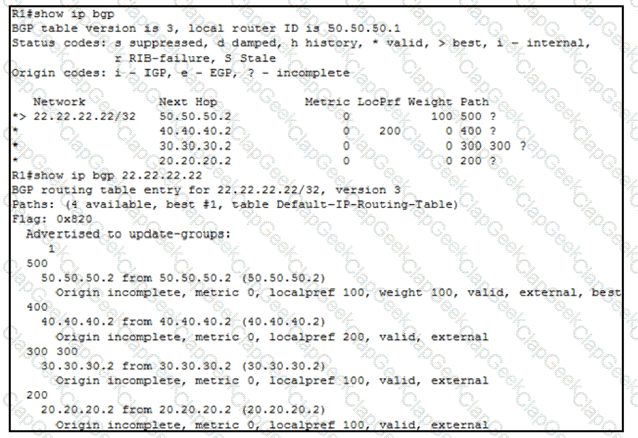
An engineer wants to determine which paths are best, second best, third best, and fourth best. Drag and drop the peer addresses on the left to the corresponding BGP best-path selection order on the right.
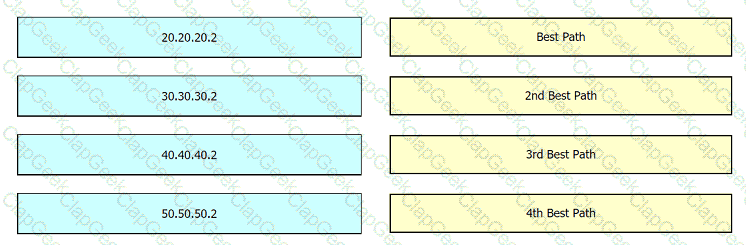
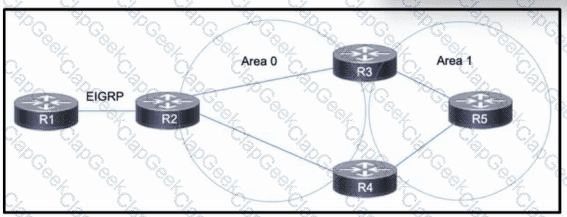
Refer to the exhibit. Company A is running OSPF within its network, comprised of routers R2, R3, R4, and R5 and consisting of two areas. Company A just acquired Company B, which uses EIGRP on its own R1. R1 has several routes in its routing table. The network engineering team at Company A needs access to the Company B network to manage network devices there, but each company will otherwise operate independently. R2 will serve as the ASBR between the two networks. Which action must the team take to reduce the number of EIGRP routes received on R2 and include only the necessary routes in the routing table?
A network engineer is implementing NetFlow to observe traffic patterns on the network. The engineer is planning to review the patterns to help plan future strategies for monitoring and preventing congestion as the network grows. If the captures must include BGP next-hop flows, which configuration must the engineer apply to the router?
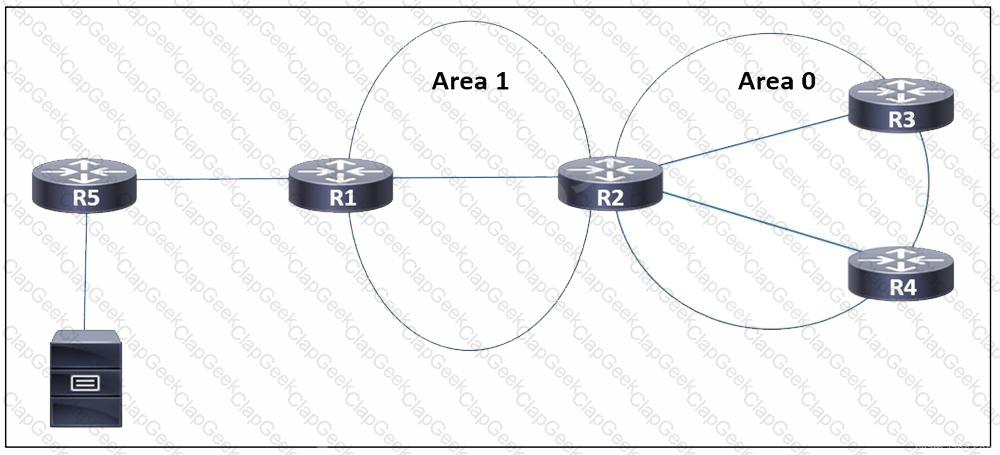
Refer to the exhibit. EIGRP is running between routers R5 and R1, and OSPF is used in the rest of the network. Users in a network attached to router R3 need to access a server connected to R5. Which task must the engineer perform so that only the users attached to R3 are able to access the server, but no other network is shared to OSPF?
An engineer needs to implement QOS mechanism on customer's network as some applications going over the internet are slower than others are. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two)
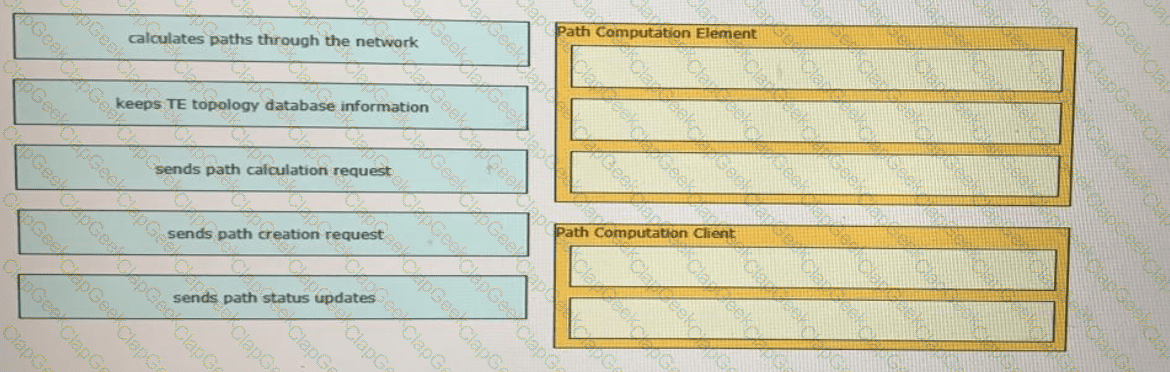
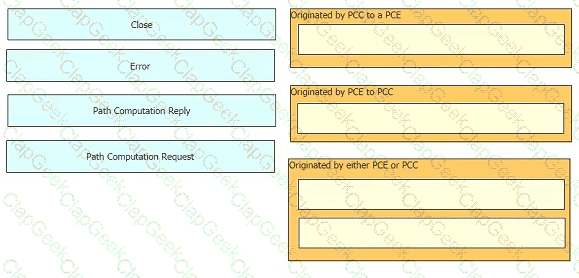
Drag and drop the functions from the left onto the correct Path Computation Element Protocol roles on the right
Refer to me exhibit.
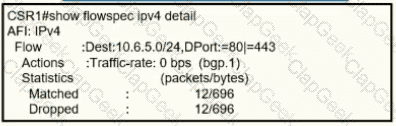
A network operator recently configured BGP FlowSpec for me internal IT network What will be inferred from the configuration deployed on me network?
Drag and drop the characteristics from the left onto the automation tool on the right.
Refer to the exhibit.
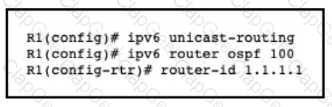
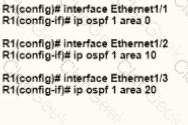
An engineer is configuring router R1 for OSPFv3 as shown. Which additional configuration must be performed so that the three active interfaces on the router will advertise routes and participate in OSPF IPv6 processes?
A)

B)

C)
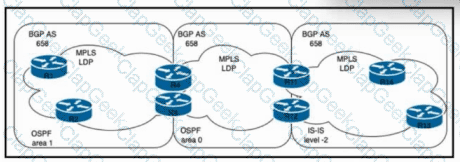
Refer to the exhibit. ISP_A is a Tier-1 ISP that provides private Layer 2 and Layer 3 VPN services across the globe using an MPLS-enabled backbone network. Routers R1, R2, R13, and R14 are PE devices. ASRs R3 and R4 and ASBRs R11 and R12 are acting as route reflectors with preconfigured next-hop-self for all BGP neighbors. After the network experienced IGP RIB overflow with multiple routes, a network engineer is working on a more scalable network design to minimize the impact on local RIBs. The solution should be based on RFC 3107 and maintain existing QoS capabilities.
Which task must the engineer perform to achieve the goal?
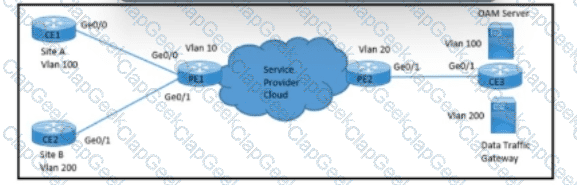
Refer to the exhibit. A network engineer with an employee ID: 5086:72:817 is configuring a connection to manage CE1 from the OAM server on VLAN 100. PE1 must push S-VLAN tag 10 toward PE2 while forwarding traffic from CE1 to the OAM server. PE1 must push S-VLAN tag 20 toward PE2 while forwarding traffic from CE2 to the data traffic gateway. Which configuration must the engineer implement on PE2?
A network engineer is configuring a newly installed PE router at the regional gateway location. The new PE router must use MPLS core routing protocols with the existing P router, and LDP sessions between the two routers must be protected to provide faster MPLS convergence. Which configuration must the engineer perform on the network so that LDP sessions are established?
Refer to the exhibit:

What is significant about the number 2 in the configuration?
Refer to the exhibit.
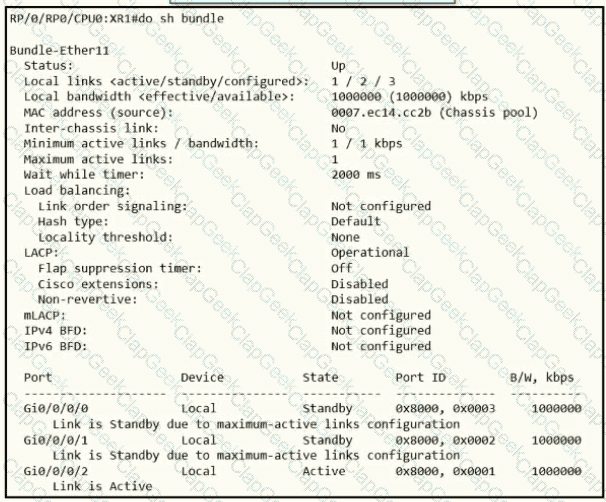
A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
What is the purpose of OSPF-TE extensions to MPLS traffic engineering functionality?
An engineer implemented LDP protocol on the ISP network. The engineer must ensure that there are no packet loss issues when IGP and LDP protocols are not synchronized. Which configuring must the engineer implement so that the IGP routing protocol will wait until LDP convergence is completed?
A regional company is planning to bolster the security of their LAN infrastructure by implementing advanced encryption techniques between their core switch and their distribution switch. The solution must leverage hardware-accelerated encryption capabilities to transparently encrypt all traffic between the two switches at the data-link layer to safeguard against unauthorized access. However, it is important for the solution to have minimal impact on network performance and latency.
Which action must the engineer take to meet the requirements?
Refer to the exhibit:
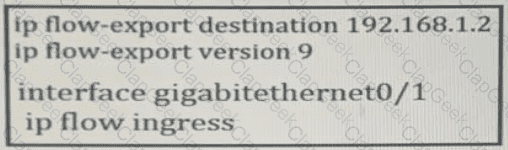
Which information is provided for traceback analysis when this configuration is applied?
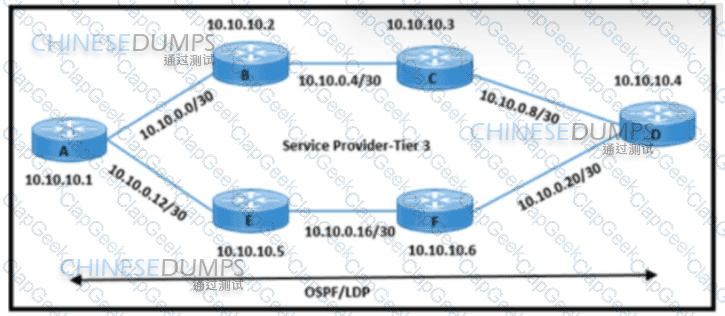
Refer to the exhibit. An engineering team must update the network configuration so that data traffic from router A to router D continues in case of a network outage between routers B and C. During a recent outage on the B-C link, the IGP traffic path was switched to the alternate path via routers E and F. but label forwarding did not occur on the new path. Which action ensures that traffic on the end-to-end path continues?
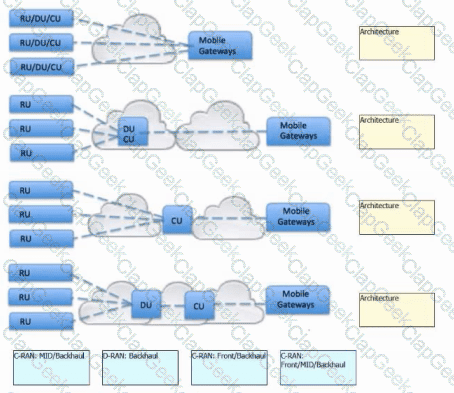
Drag and drop the 5G RAN architecture types from the bottom next to the corresponding topologies on the right.
Which regular expression query modifier function indicates the start of a string?
Refer to the exhibit.
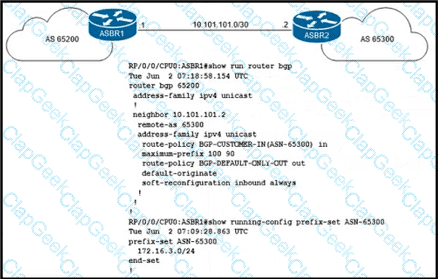
A network engineer is implementing a standard customer route-policy on ASBR1 with these requirements:
• It must accept only customer-assigned prefixes
• It must preserve customer advertised BGP communities
• It must set the local-preference to 110 for all prefixes
• It must attach the ORIGINATION-PE and LOCAL-CITY communities to all accepted prefixes.
Which route policy must the engineer implement on ASBR1 to satisfy the requirements?

A new PE router is configured to run OSPF as an IGP with LDP on all interfaces. The engineer is trying to prevent black holes after convergence when the PERSON device loses an LDP session with other PE routers. Which action must the engineer take to implement LDP session protection on a new PE router?
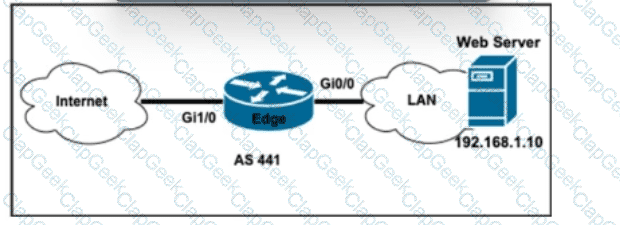
Refer to the exhibit. The network manager asked a network engineer to increase data-plane security on an Edge router connected to the internet with these requirements:
*Allow incoming HTTP traffic from any source to the Web server with IP address 192.168.1.10.
*Allow incoming SSH traffic from the management host with IP address 10.0.0.10.
*Block incoming Telnet traffic from all sources.
Which action must the engineer take to meet the requirements?
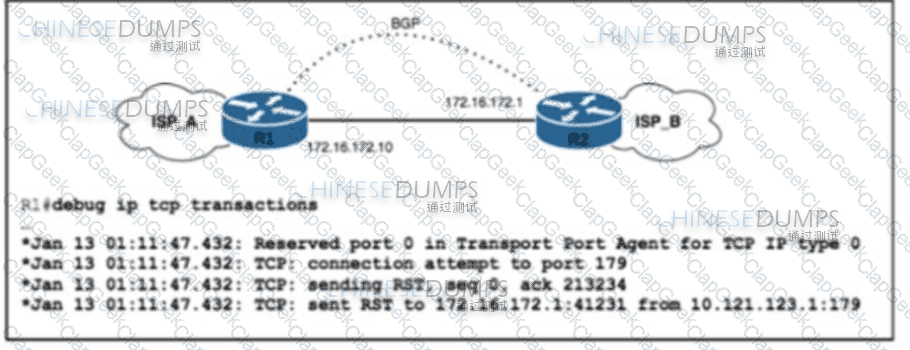
Refer to the exhibit. ISP_A and ISP_B use AS numbers 38321 and 16213 respectively. After a network engineer reloaded router R1, the BGP session with R2 failed to establish. The engineer confirmed BGP next-hop availability with a connectivity test between the router loopback addresses 10.121.123.2 and 10.121.123.1, as well as between interfaces Gi1/1 and Gi1/2. EBGP multihop has been configured on both routers. Which action must the engineer take to resolve the issue?
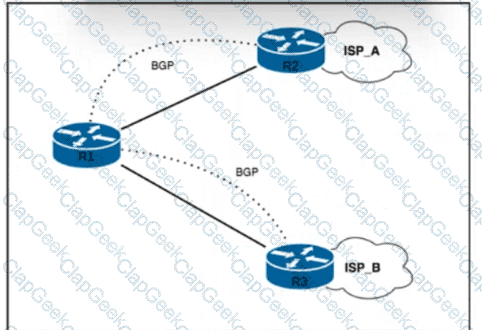
Refer to the exhibit. R1 has two upstream Tier 1 service providers. BGP is in use as the exterior routing protocol, and ISP_A and ISP_B are sending the full BGP table. A network engineer must assign local-preference 70 to all routes with multiple exit discriminator 30. Which configuration must the network engineer apply?

A network architect plans to implement MPLS OAM to provide additional troubleshooting functionality for the NOC team. After analyzing the configuration on the MPLS P/PE nodes, the architect decides to revise the CoPP policies. Which two actions ensure that the new solution is secure? (Choose two.)
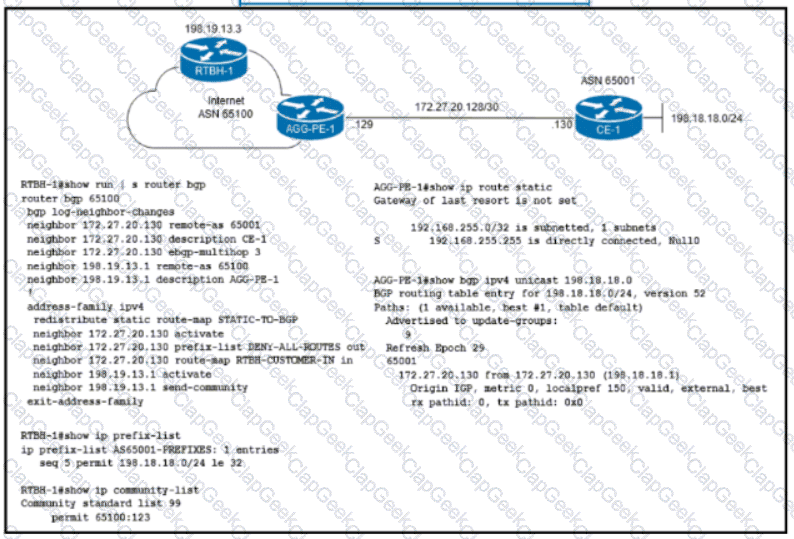
Refer to the exhibit. ISP ASN 65100 provides Internet services to router CE-1 and receives customer prefix 198.18.18.0/24 via eBGP. An administrator for the ISP is now provisioning RTBH services to provide on-demand data-plane security for the customer’s IP space. Which route-map configuration must the administrator apply to router RTBH-1 to complete the implementation of RTBH services to CE-1?
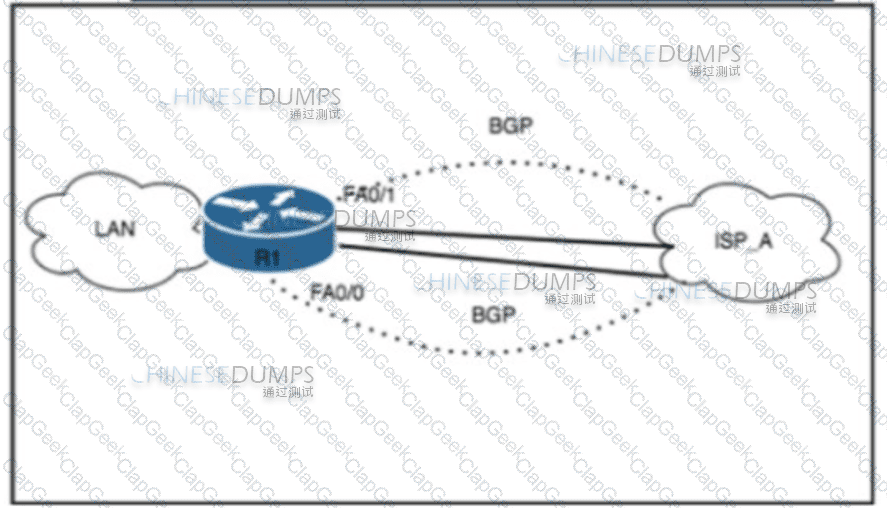
Refer to the exhibit. A network engineer must deny access from spoofed addresses to the LAN. The edge router currently has two active BGP sessions established with Tier 1 ISP_A. Due to asymmetric routing, no ACL is configured on either interface. Which two configurations must the engineer perform on the edge router to complete the task? (Choose two.)
Refer to the exhibit.

An engineer needs to implement this QoS policy on customer's network due to ongoing slow network issues. What will be the effect on the network when the engineer implements this configuration?
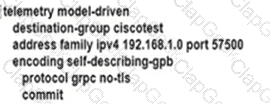
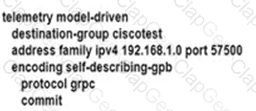
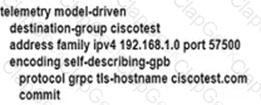
An engineer is developing a configuration script to enable dial-out telemetry streams using gRPC on several new devices. TLS must be disabled on the devices. Which configuration must the engineer apply on the network?
A)
B)
C)
D)
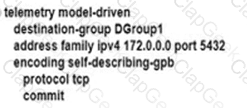

Refer to the exhibit. This enterprise configured MPLS within its network to connect offices that span different geographic areas, with LDP running between connected neighbors. At each office, including headquarters, the networks are running OSPF with a similar configuration.
Which additional action must the engineering team take to support a more reliable connection between MPLS and OSPF?
Refer to the exhibit.
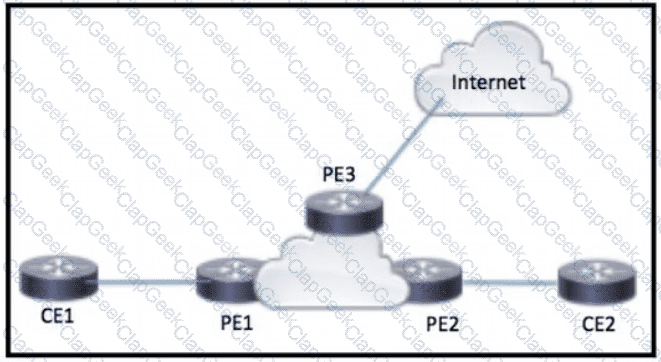
CE1 and CE2 require connectivity to the internet through the ISP connected to PE3 What should an engineer configure to complete this task?

Refer to the exhibit. An operations team recently located an archive of scripts for deploying routine network changes with an error-free approach. A junior network engineer, who is working to modify the scripts to support RESTCONF, has been asked to document the purpose of each updated script. Which two actions does the given script take? (Choose two.)
Refer to the exhibit:
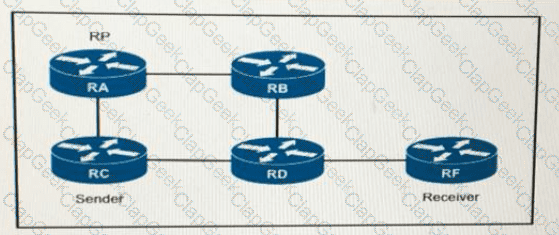
If router A is the RP, which PIM mode can you configure so that devices will send multicast traffic toward the RP?
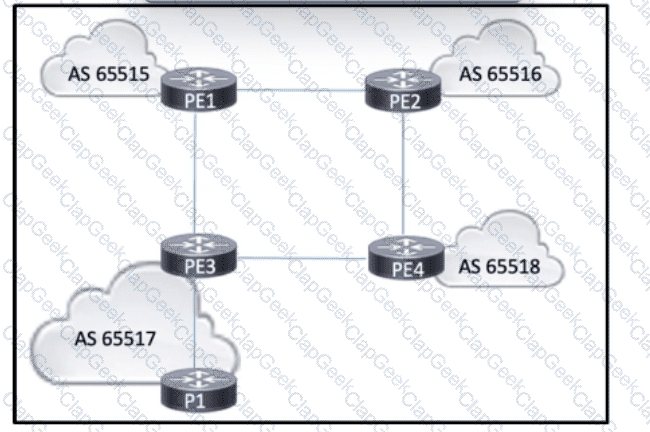
Refer to the exhibit. AS 65517 is running OSPF within the core. BGP is running between all four autonomous systems, interconnecting several ISPs that provide intranet and extranet services. All of the PE routers are connected, and eBGP peering relationships have been established. A network engineer also configured an iBGP peering between PE3 and P1, and the peering is up. However, P1 cannot reach routes outside of AS 65517. Which action must the engineer take so that P1 reaches external routes?)

Refer to the exhibit. A multinational corporation with a Cisco-based network wants to leverage Cisco security features to enhance the security of their LAN and protect against eavesdropping and man-in-the-middle attacks. The solution must comply with the IEEE 802.1AE standard. A network engineer must implement the new security configurations on a pair of interconnected Cisco switches. The engineer already completed the configuration to enable AAA new-model and set up a basic AAA configuration for user authentication. Management VLAN 10 is in place for network administration. Which action must the engineer take to meet the requirements?
An engineer is implementing a router redistribution within BGP. The route map must be configured to permit all unmatched routes. Which action must the engineer perform to complete this task?

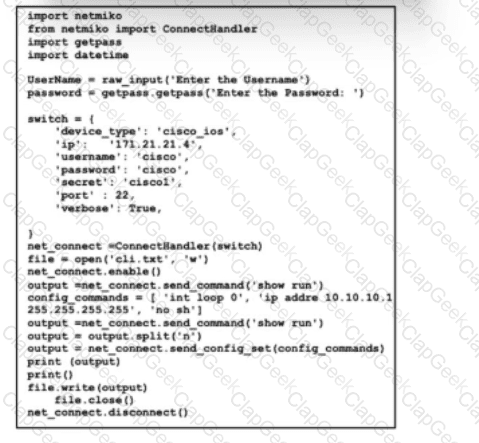
Refer to the exhibit. A junior engineer must update a group of scripts to use on a newly deployed subnet. However, one of the scripts is not documented or commented. What are the two effects of this script? (Choose two.)
Refer to the exhibit:
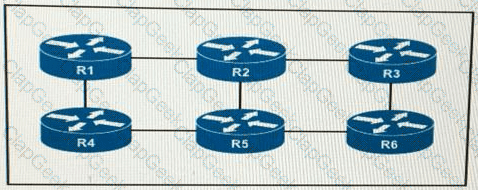
You are configuring an administrative domain implement so that devices can dynamically learn the RP?
How does Inter-AS Option-A function when two PE routers in different autonomous systems are directly connected?
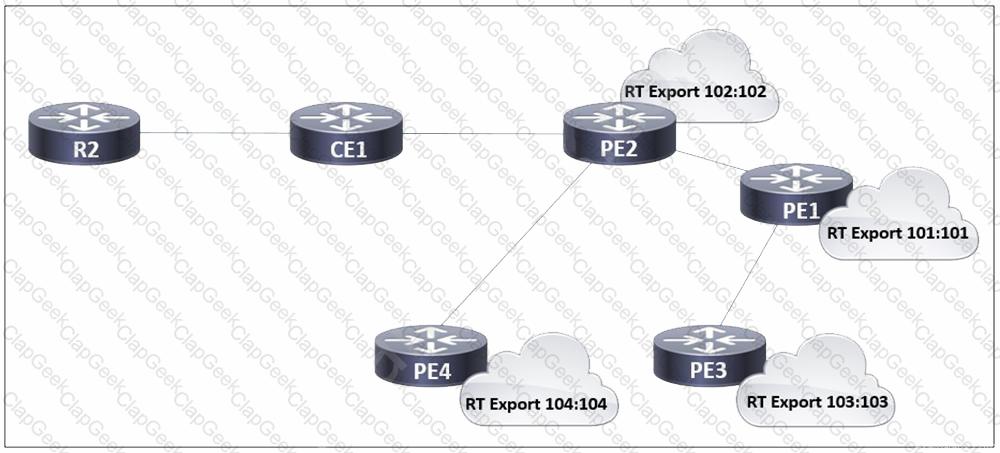
Refer to the exhibit. In the service provider network, routers PE1, PE2, and PE4 have access to the internet and provide access to customer networks. Router PE3 is used for access to other customer systems. In accordance with a new SLA, an engineer is updating settings on this network so that router CE1 accesses the internet via PE1 instead of PE2. Which two tasks must the engineer perform to complete the process? (Choose two.)
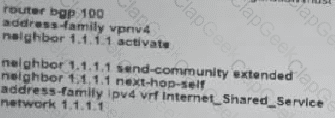
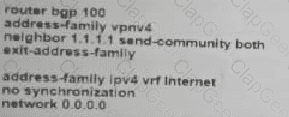
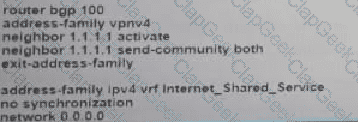
Refer to the exhibit. Which additional configuration must an engineer to the adge router to inject a default router into the MP-BGP address family for the internet_Shared_Services dedicated VRF?
A)
B)
C)
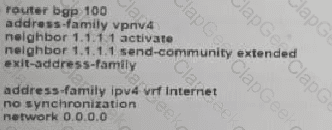
D)
You are configuring MPLS traffic-engineering tunnels in the core.
Which two ways exist for the tunnel path across the core? (Choose two )
Refer to the exhibit.
A network engineer is configuring customer edge routers to finalize a L2VPN over MPLS deployment Assume that the AToM L2VPN service that connects the two CEs is configured correctly on the service provider network Which action causes the solution to fail?
A network engineer is deploying VPLS configuration between multiple PE routers so that customer's remote offices have end-to-end LAN connectivity. Which additional configuration should the engineer perform on the PE routers to enable the virtual switch instance?
A)

B)

C)

D)
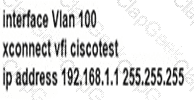
Refer to the exhibit:

Which command is used to complete this configuration for QoS class-based marking?
Under which circumstance does BGP ignore the best-path algorithm after receiving multiple routes to a destination?
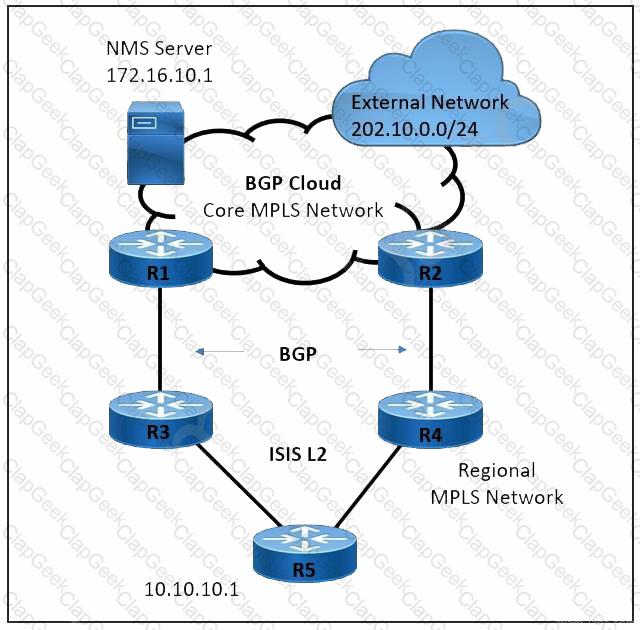
Refer to the exhibit. A large service provider is migrating device management from Layer 2 VLAN-based to Layer 3 IP-based solution. An engineer must configure the ISIS solution with these requirements:
Network management server IP 172.16.10.1 must be advertised from the core MPLS network to the regional domain.
The external network 202.10.0.0/24 must not establish ISIS peering with the R5 router.
The regional network must prevent sending unnecessary hello packets and flooding the routing tables of the R5 router.
Which two ISIS parameters must be implemented to meet these requirements? (Choose two.)
Drag and drop the message types from the left onto the target field of the message originator on the right.
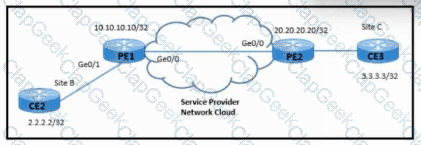
Refer to the exhibit. A network engineer is configuring Ethernet Layer 2 service to connect CE2 and CE3 for video and data application sharing with these requirements:
A point-to-point cross-connect service must be established between 10.10.10.10 and 20.20.20.20.
PE1 and PE2 must learn neighbors dynamically in PW 10.
Which configuration must be implemented on PE1 to meet the requirements?
How does Cisco MPLS TE use OSPF extensions to allow for optimized transit between a headend router and a destination router?
A network operator needs to implement PIM-SSM multicast configuration on customer's network so that users in different domains are able to access and stream live traffic. Which two actions must the engineer perform on the network
to make the streaming work? (Choose two.)
The NOC engineer in a service provider network must configure an SNMP community on switch SW with these security attributes:
* Event messages must be authenticated with the MD5 algorithm and encrypted.
* The remote user name for the SNMP server at 172.16.10.1 is AuthNocUser.
Which configuration must the engineer apply to the switch?

Refer to the exhibit. Customers report occasional forwarding issues from hosts connected to R6 to hosts connected to R1. A network engineer has just updated the MPLS configuration on the network, and a targeted LDP session has been established between R1 and R5. Which additional task must the engineer perform so that the team can identify the path from R6 to R1 in case the forwarding issues continue?
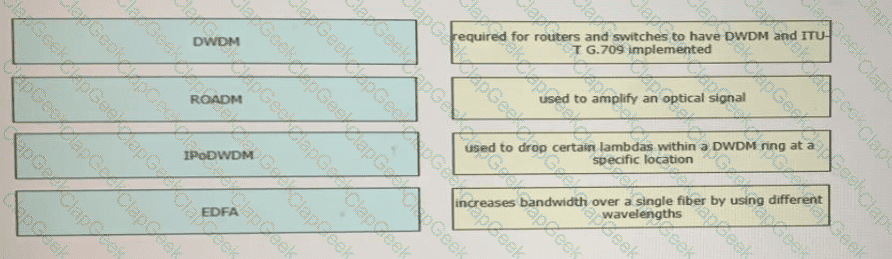
Drag and drop the technologies from the left onto the correct definitions on the right.
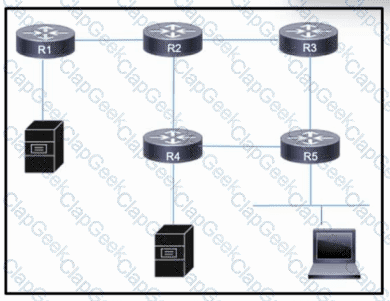
Refer to the exhibit. Users on a LAN connected to router R5 frequently open high-traffic connections with servers connected to R1 and R4. Users on R2 also require access to the servers, but performance is not a major concern and their traffic can be treated as secondary. As traffic on all links grows, the network architect wants to mitigate the potential for congestion on the link between R2 and R4.
Which action must the engineering team take to improve performance on the R2-R4 link for users on R5 while still allowing other traffic to flow?
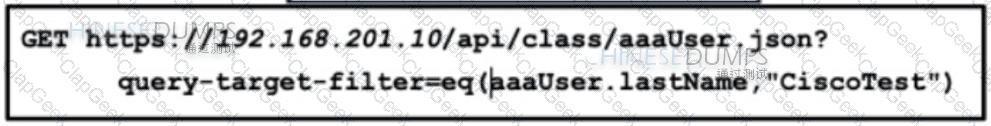
Refer to the exhibit. An engineer configured several network devices to run REST APIs. After testing, the organization plans to use REST APIs throughout the network to manage the network more efficiently. What is the effect if this script?
What occurs when a high bandwidth multicast stream is sent over an MVPN using Cisco hardware?
Which control plane protocol is used between Cisco SD-WAN routers and vSmart controllers?
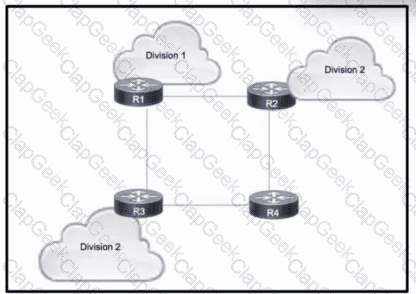
Refer to the exhibit. A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?
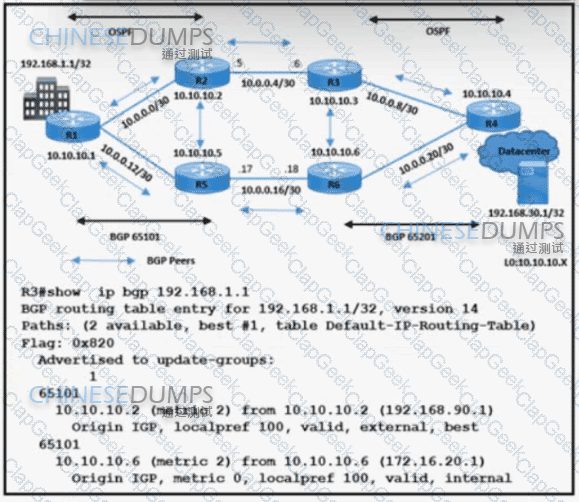
Refer to the exhibit. A network engineer is implementing BGP in AS 65101 and AS 65201. R3 sends data traffic to 192.168.1.1 /32 via the path R3-R2-R1. The traffic must travel via alternate path R6-R5 for prefix 192.168.1.1/32. Which action must be taken to meet the requirement?
Refer to the exhibit.
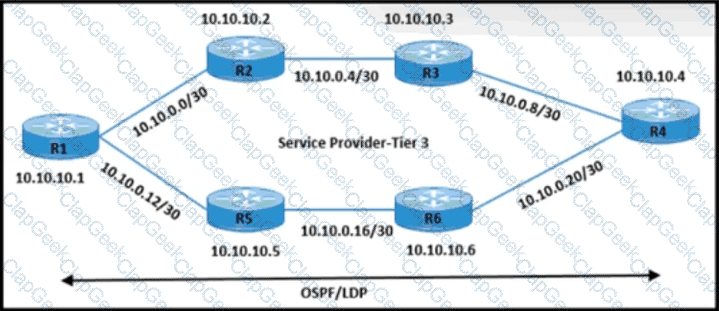
The network engineer is performing end-to-end MPLS path testing with these conditions:
• Users must perform MPLS OAM for all available same-cost paths from R1 to R4.
• Traceroute operations must return all of the next-hop IP details.
Which configuration meets these requirements?
BGP has been implemented on a IOS XR router. Which configuration sends BGP IPv4 labels to build inter-domain LSPs?
Refer to the exhibit.
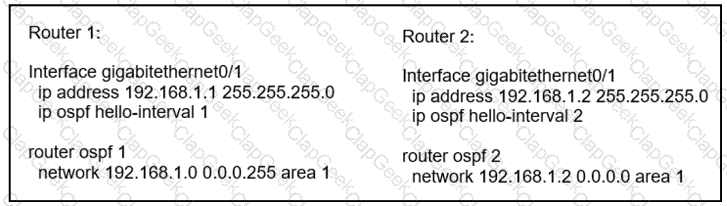
What reestablishes the OSPF neighbor relationship between Router 1 and Router 2?
An engineering team must implement Unified MPLS to scale an MPLS network. Devices in the core layer use different IGPs, so the team decided to split the network into different areas. The team plans to keep the MPLS services as they are and introduce greater scalability. Which additional action must the engineers take to implement the Unified MPLS?
Refer to the exhibit.
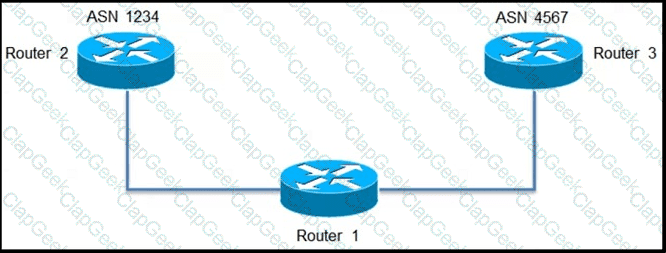
An engineer is configuring path selection on router R1 for two ASNs as shown. Which additional task must the engineer perform on Router 1 so that all outbound traffic utilizes the link between R1 and R3 to reach ASN 4567?
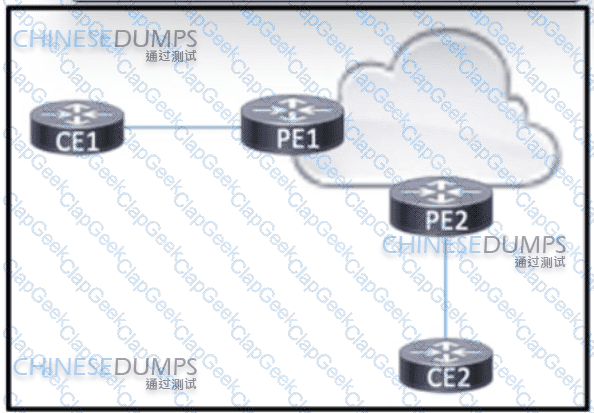
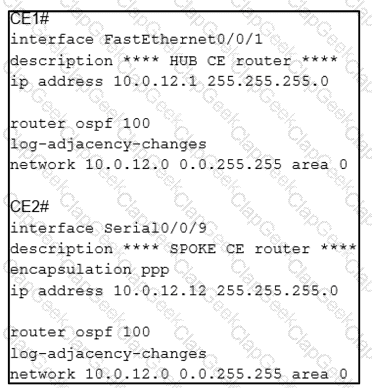
Refer to the exhibit BGP is running in the core of the service provider to exchange routes for its customers, and OSPF serves as the PE-CE routing protocol. The service provider s existing customer at CE1 is opening a new office in a different geographical location connected via CE2. A network engineer must update the BGP implementation so that PE1 and PE2 will share routes and provide communication between CE1 and CE2 Which action must the engineer take?
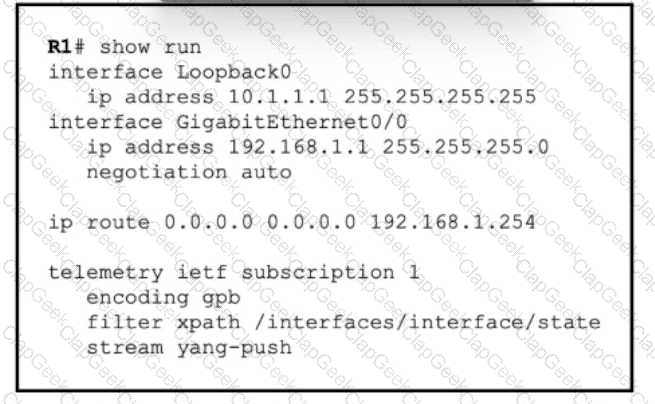
Refer to the exhibit. A regional company is implementing a network-health monitoring solution on their Cisco ISR routers to monitor network performance metrics and gather real-time data. The router R1 Ethernet interface, GigabitEthernet0/0, is assigned IP address 192.168.1.1/24, and basic IP addressing and connectivity to the data-collection server have already been configured. A network engineer must update R1 to ensure secure and reliable data transmission to the monitoring server, which is located at IP address 192.168.50.50 on port 50051. To achieve secure communication, the configuration must comply with RFC 5246, and to ensure reliable data transmission, it must follow RFC 793. Which command must the engineer execute to configure data collection?
Refer to the exhibit. A service provider is running MPLS in the core to support Layer 3 VPN. OSPF is configured to support dynamic routing, and BGP is enabled throughout the network. A network engineer is adding a new P router to the infrastructure and is connecting it to P1 and P3.
Which task must the engineer perform on the new router to allow it to participate in the Layer 3 VPN?
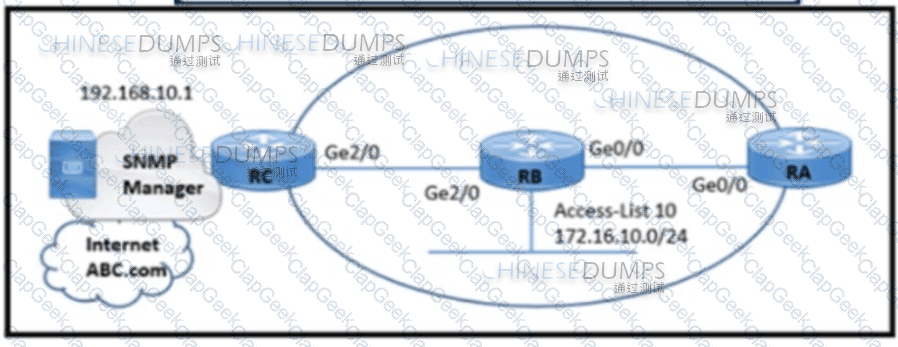
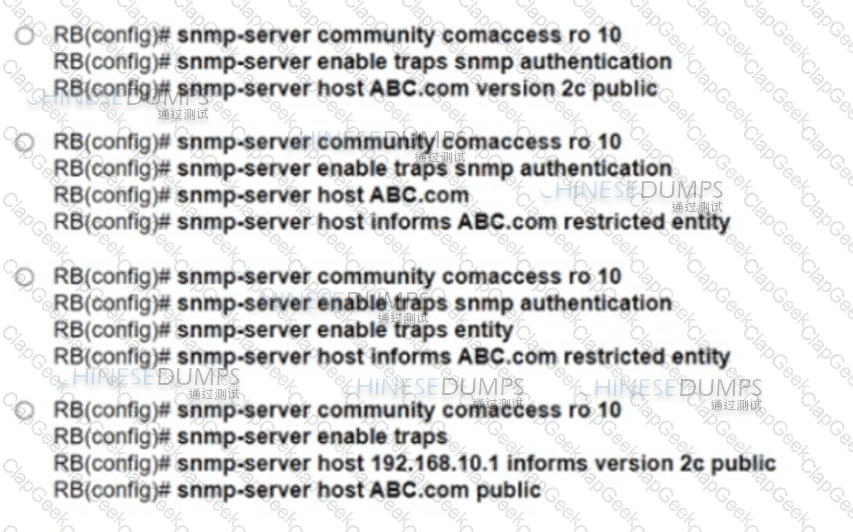
Refer to the exhibit. A network engineer is configuring an SNMP community on router RB with these requirements:
Allow read-only access for all objects to members of Access-List 10 that use the comaccess community string.
Other SNMP managers must not have access to objects.
SNMP authentication failure traps must be sent to SNMPv2c and then to the host using SNMPv2c with the public community string.
Which configuration meets these requirements?
You are creating new Cisco MPLS TE tunnels. Which type of RSVP message does the headend router send to reserve bandwidth on the path to the tunnel’s router?
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
How can shared services in an MPLS Layer 3 VPN provide Internet access to the customers of a central service provider?
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services For which reason do you make this decision?
Refer to the exhibit.
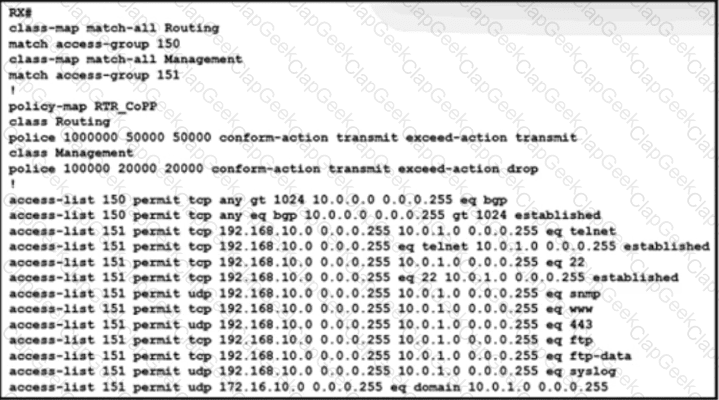
The engineering team wants to limit control traffic on router RX with the following IP address assignments:
• Accepted traffic for router: 10.0.0.0/24
• NOC users IP allocation: 192.168.10.0/24
Which additional configuration must be applied to RX to apply the policy for MSDP?
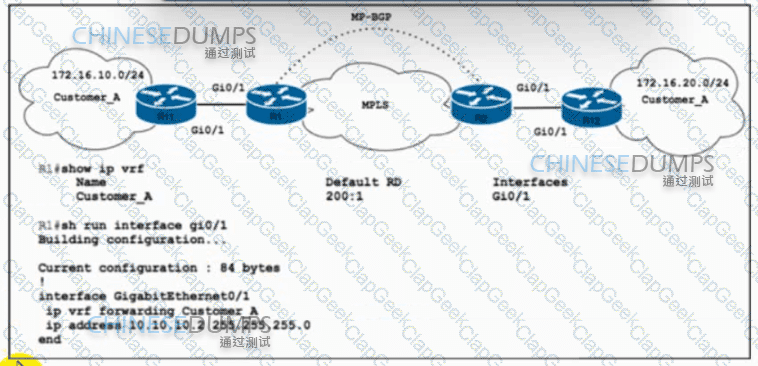
Refer to the exhibit. Customer_A asked ISP_A to connect two offices via an MPLS L3 VPN. Customer_A is currently using only the default route toward ISP_A. The engineer at ISP_A already configured the ip route vrf Customer_A 172.16.10.0 255.255.255.0 10.10.10.1 command on R1. Which action completes the configuration?
Refer to the exhibit.
An engineer working for private Service Provider with employee id: 3948:11:613 is configuring the BGPsec framework. Which two conditions must the engineer take into account? (Choose two.)
Refer to the exhibit.
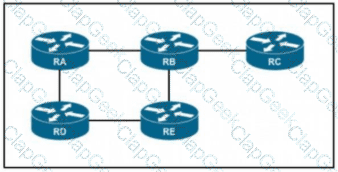
If RC is a stub router, which entry must be injected so that it will send traffic outside the OSPF domain?
Which CLI mode must be used to configure the BGP keychain in Cisco IOS XR software?
Refer to the exhibit.
An engineer configured multicast routing on client's network. What is the effect of this multicast implementation?
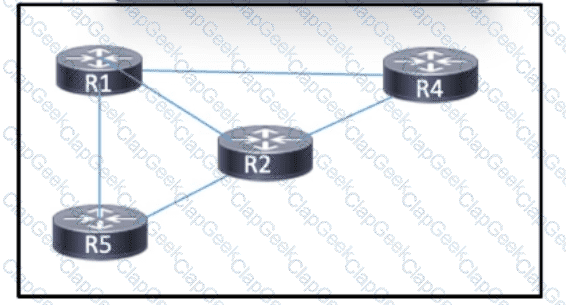
Refer to the exhibit. MPLS is running in the network with OSPF as the IGP. Full routes are shared between the routers, and each connected link has an MPLS neighbor relationship. A network engineer must update the network configuration so that it will maintain LDP neighbor relationships if a directly connected link goes down. Which action must the engineer take as part of the process?
Refer to the exhibit.

An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
Which configuration modifies Local Packet Transport Services hardware policies?
A)
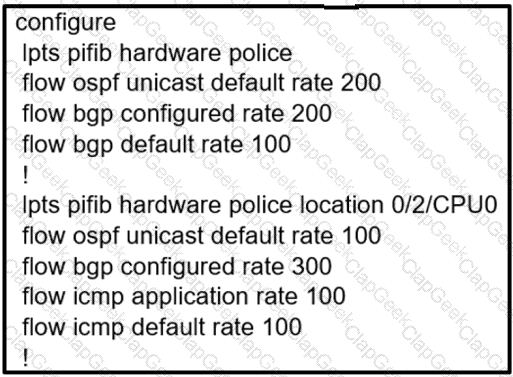
B)

C)
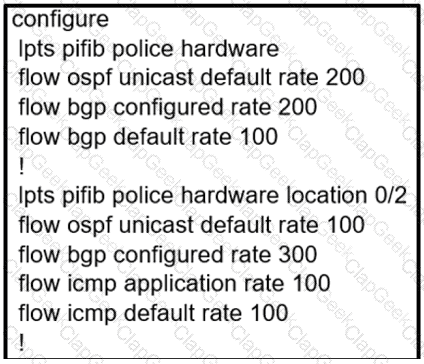
D)

Which two PHY modes are available to implement an IOS XR Gigabit Ethernet interface interface? (Choose two.)
Refer to the exhibit.
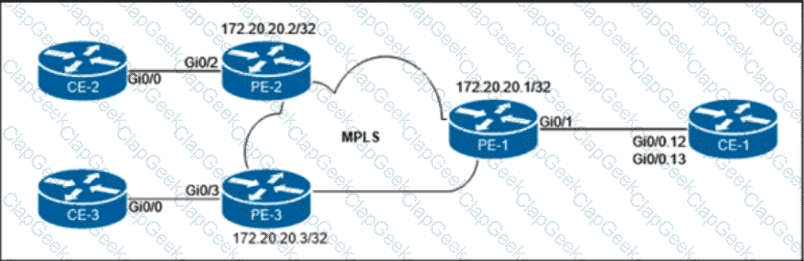
The customer that owns the CE-1, CE-2, and CE-3 routers purchased point-to-point E-Line services from the Carrier Ethernet provider. The service provider is delivering multiplexed UNI at the customer HQ location on PE-1 and untagged UNIs at the PE-2 and PE-3 locations. Additionally, the customer provided these VLAN to EVC mapping requirements:
• EVC 1 between CE-1 and CE-2 must be provisioned with C-VLAN 12 at the HQ location.
• EVC 2 between CE-1 and CE-3 must be provisioned with C-VLAN 13 at the HQ location.
Which configuration must the network engineer implement on the PE routers to provide end-to-end Carrier Ethernet service to the customer?
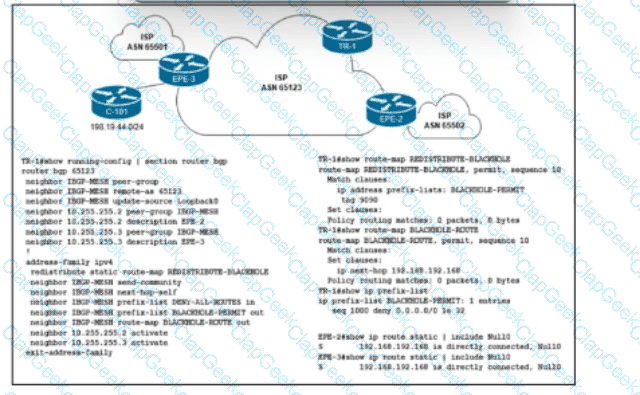
Refer to the exhibit. Customer C-101 in ASN 65123 requested that the ISP blackholes a host route 198.19.44.195, to which the customer is receiving a significant amount of malicious traffic. Which configuration must the network engineer implement on the trigger router TR-1 to fulfill the request without affecting other IP destinations in the customer's block?
Which is the benefit of implementing model-driven telemetry in a service provider environment?
An engineer working for a private telecommunication company with an employe id:3948:613 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
A)

B)

C)

D)



