Which type of tunnel is required between two WLCs to enable intercontroller roaming?
Which RF value represents the decline of the RF signal amplitude over a given distance"?
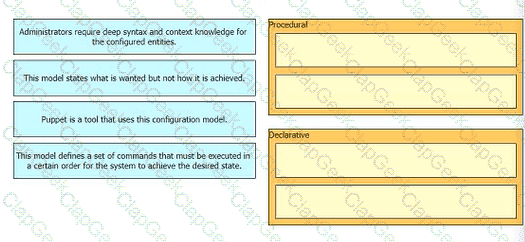
Drag anti drop the characteristics from the ten onto the configuration models on the right.
An engineer is configuring a new SSID to present users with a splash page for authentication. Which WLAN Layer 3 setting must be configured to provide this functionally?
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
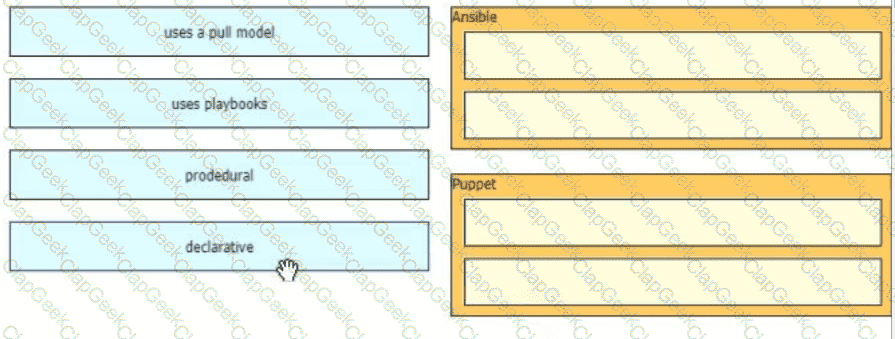
Drag and drop the characteristics from the left onto the orchestration tools that they describe on the right.
Whichtwo benefits result from a network design mat uses small and repeatable sections? (Choose two.)
What is a client considered when it is in web authentication state and roams between two controllers with mobility tunnels?
Which nodes require VXLAN encapsulation support In a Cisco SD-Access deployment?
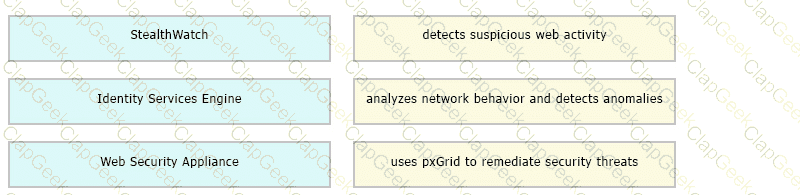
Drag and drop the solutions that comprise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
Which characteristic applies to the endpoint security aspect of the Cisco Threat Defense architecture?
Which AP mode allows an engineer to scan configured channels for rogue access points?

Refer to the exibit. How should the programmer access the list of VLANs that are recevied via the API call?
Which authorization framework gives third-party applications limited access to HTTP services?
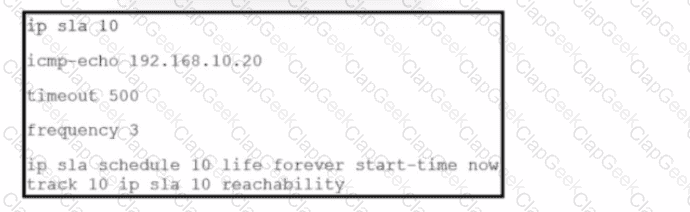
Refer to the exhibit. The IP SLA is configured in a router. An engineer must configure an EEM applet to shut down the interface and bring it back up when there is a problem with the IP SLA. Which configuration should the engineer use?
Which devices does Cisco DNA Center configure when deploying an IP-based access control policy?
In a high-density AP environment, which feature can be used to reduce the RF cell size and not demodulate radio packets above a given threshold?


