A network engineer must configure a new SNMP configuration and syslog servers. The requirement is for all faults and events related to endpoint groups, bridge domains, and VRFs to be sent to it. Which action must be taken to meet the requirements?
Which method does the Cisco ACI fabric use to load-balance multidestination traffic?
An engineer is extending an EPG out of the ACI fabric using static path binding. Which statement about the endpoints is true?
Cisco ACI fabric contains 10 standalone leaf switches. An engineer must configure only the first two leaf switches in a VPC. Which VPC protection type must be configured to accomplish goal?
Cisco ACI fabric must detect all silent endpoints for the Layer 3 bridge domain. Which actions accomplish this goal?
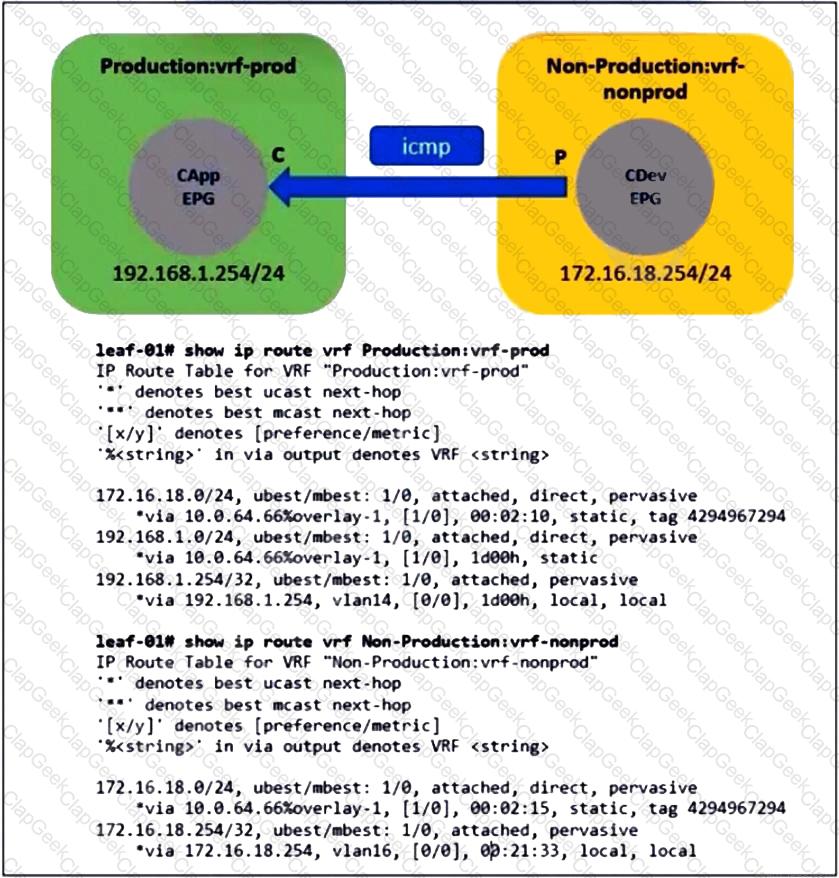
Refer to the exhibit. An administrator configures inter-VRF route leaking between Production:vrf-prod and Non-Production:vrf-nonprod. However, the route in the Non-Production:vrf-nonprod VRF to the production tenant is missing. Which action resolves the VRF route leaking issue?
Which type of policy configures the suppression of faults that are generated from a port being down?
Refer to the exhibit.
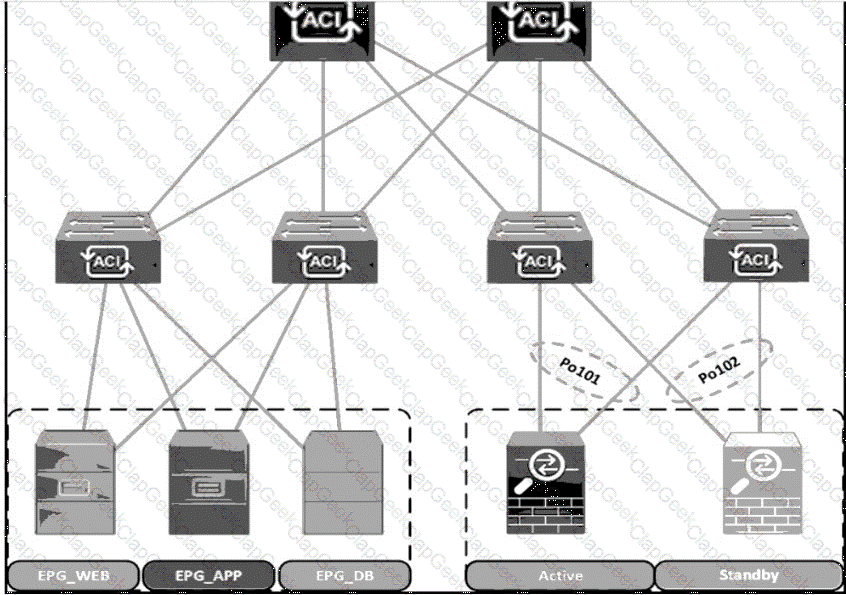
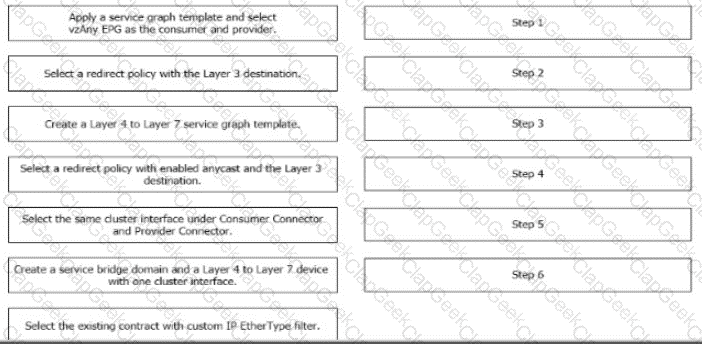
A Cisco ACI fabric is newly deployed, and the security team requires more visibility of all inter-EPG traffic flows. All traffic in a VRF must be forwarded to an existing firewall pair. During fallover, the standby firewall must continue to use the same IP and MAC as the primary firewall. Drag and drop the steps from the left Into the Implementation order on the right to configure the service graph that meets the requirements. (Not all steps are used.)
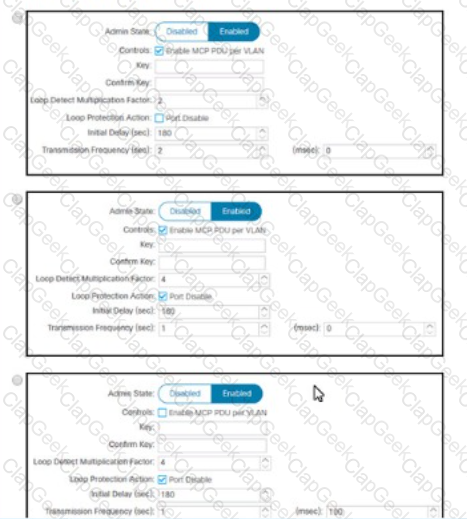
An engineer wants to monitor all configuration changes, threshold crossing, and link-state transitions in a Cisco ACI fabric. Which action must be taken to receive the required messages?
A Cisco ACI is integrated with a VMware vSphere environment. The port groups must be created automatically in vSphere and propagated to hypervisors when created in the ACI environment. Which action accomplishes this goal?
A network engineer must configure a Cisco ACI system to detect network loops for untagged and tagged traffic The loop must be detected and slopped by disabling an interface within 4 seconds Which configuration must be used?
Which two hardware models are supported as fixed spine in Cisco ACI fabrics? (Choose two.)
An engineer must ensure that Cisco ACI flushes the appropriate endpoints when a topology change notification message is received in an MST domain. Which three steps are required to accomplish this goal? (Choose three.)
New ESXi hosts are procured in a data center compute expansion project. An engineer must update the
configuration on the Cisco APIC controllers to support the addition of the new servers to the existing VMM
domain. Which action should be taken to support this change?
Refer to the exhibit.
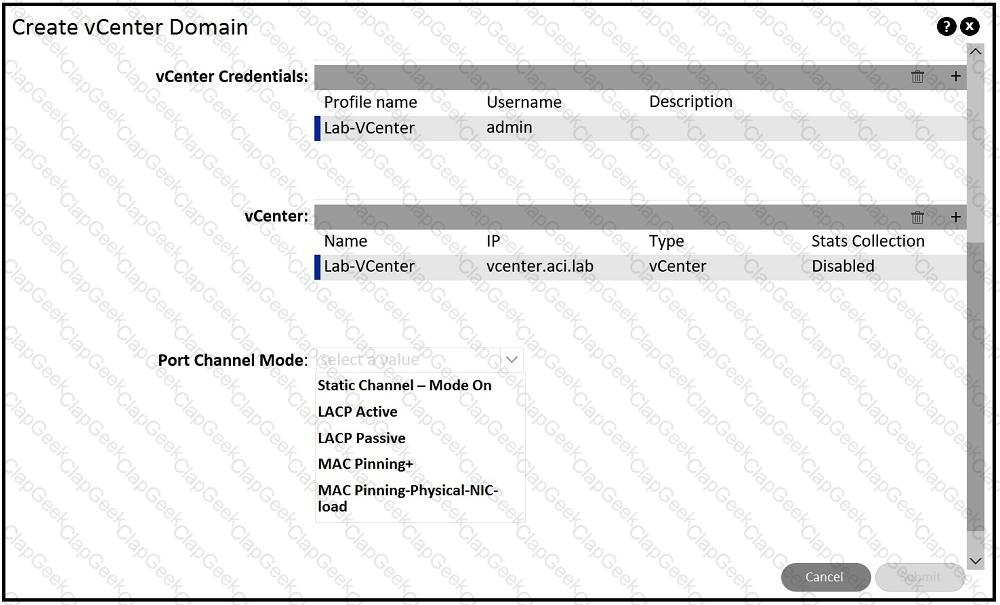
An engineer is implementing Cisco ACI – VMware vCenter integration for a blade server that lacks support of bonding. Which port channel mode results in “route based on originating virtual port” on the VMware VDS?
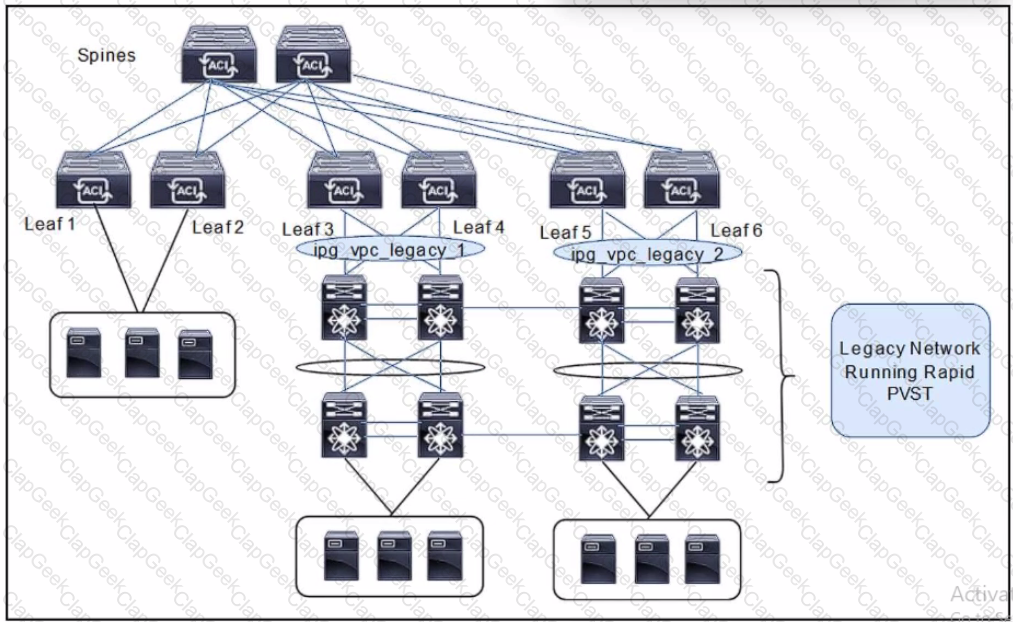
Refer to the exhibit. A client is configuring a new Cisco ACI fabric. All VLANs will be extended during the migration phase using the VPC connections on leaf switches 3. 4 and leaf switches toward the legacy network. The migration phase has these requirements;
* If The legacy switches must be able to transfer BPDUs through the ACI fabric.
* If the legacy switches fail to break a loop. Cisco ACI must break the loop.
Which group settings must be configured on VPC interface policy groups ipg_vpc-legacy_1 and ipg_vpc-legacy_2 to meet these requirements?
Refer to the exhibit. VM1 and VM2 are in Cisco ACI POD1 and communication takes place. Which event is triggered when VM2 is live migrated from POD1 to POD2?
An engineer implements a configuration backup on the Cisco APIC. The backup job must meet these requirements:
• The backup must transfer the encrypted data to the remote server.
• The transfer must be resumed if the connection is interrupted.
Which configuration set meets these requirements?
Which Cisco APIC configuration prevents a remote network that is not configured on the bridge domain from
being learned by the fabric?
A bridge domain for a new endpoint group in the Cisco ACI fabric must meet these requirements:
The bridge domain must function as the default gateway for the subnet so that routing remains within the Cisco ACI fabric.
ARP requests must be managed via Layer 3 unicast packets or be dropped to reduce excessive broadcast traffic.
The impact of misconfigured virtual machines must be kept to a minimum by preventing IP addresses outside of the configured subnet from being routed.
Which set of actions must be taken?
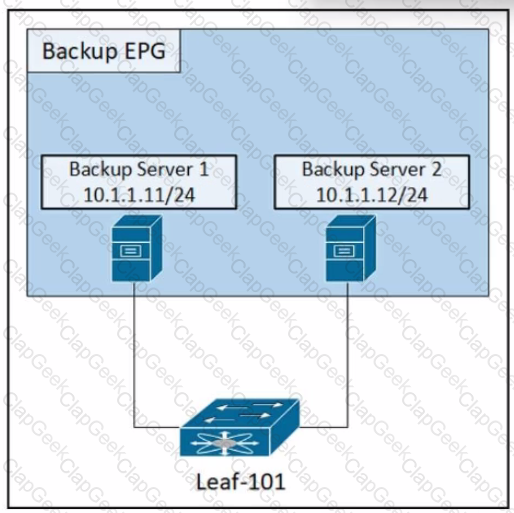
Refer to the exhibit. An engineer must disable the communication between the two backup servers in the backup EPG. Which action accomplishes this goal?
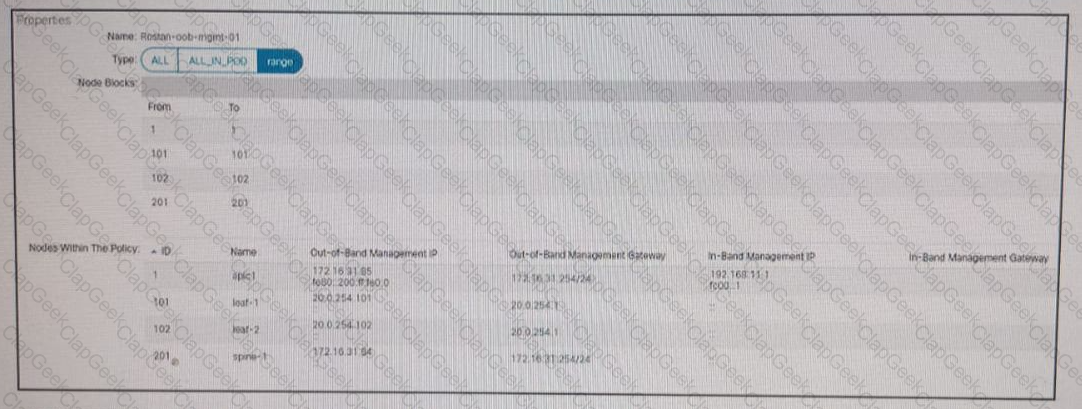
Refer to the exhibit A Cisco ACI fabric is using out-of-band management connectivity The APIC must access a routable host with an IP address of 192 168 11 2 Which action accomplishes this goal?
An ACI engineer is implementing a Layer 3 out inside the Cisco ACI fabric that must meet these requirements:
The data center core switch must be connected to one of the leaf switches with a single 1G link.
The routes must be exchanged using a link-state routing protocol that supports hierarchical network design.
The data center core switch interface must be using 802.1Q tagging, and each vlan will be configured with a dedicated IP address.
Which set of steps accomplishes these goals?
Cisco ACI fabric is integrated with a VMware environment. The engineer must back up the current configuration of the fabric and restore the vCenter password when the configuration is ... Which action accomplishes this goal?
What happens to the traffic flow when the Cisco ACI fabric has a stale endpoint entry for the destination
endpoint?
What are two PBR characteristics of the Cisco ACI Active-Active Across Pods deployment mode in Cisco ACI Multi-Pod design? (Choose two.)
What is the name of the automatically configured VLAN 3600 presented during Cisco ACI fabric discovery?

An engineer wants to filter the System Faults page and view only the active faults that are present in the Cisco
ACI fabric. Which two lifecycle stages must be selected for filtering? (Choose two.)
An engineer discovered an outage on the mgmt0 port of Leaf113 and Leaf114. Both leaf switches were recently registered in the fabric and have health scores of 100. The engineer overs there is no IP address assigned to the mgmt0 interface of the switches. Which action resolves the outage?
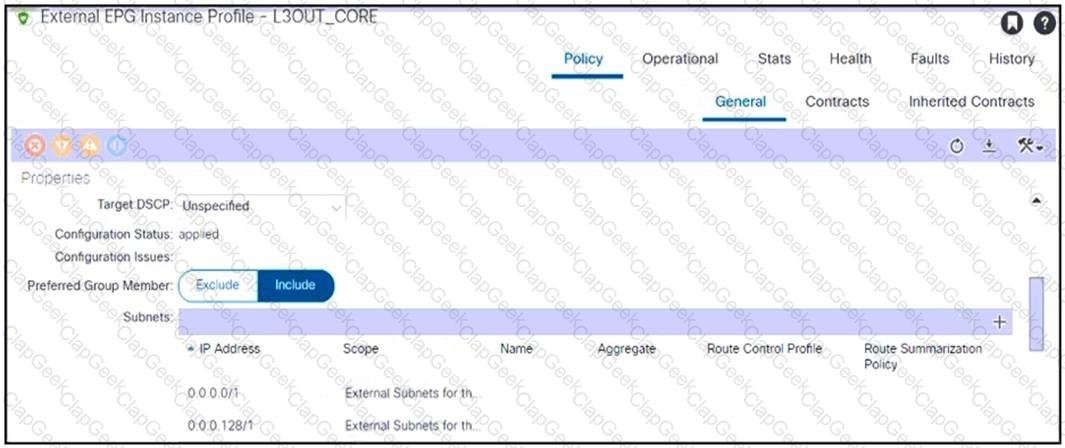
Refer to the exhibit. An engineer configured subnets on the external EPG called L3OUT_CORE. The external endpoints in the 10.1.0.0/24 subnet can reach internal endpoints, but the external endpoints in the 172.16.1.0/24 subnet are unreachable. Which set of actions enables the connectivity?
An Cisco ACI leaf switch learns the source IP address of a packet that enters the front panel port of the switch. Which bridge domain setting is used?
How many ARP requests are sent from leaf switches to perform host tracking for local endpoints?
Which two dynamic routing protocols are supported when using Cisco ACI to connect to an external Layer 3 network? (Choose two.)
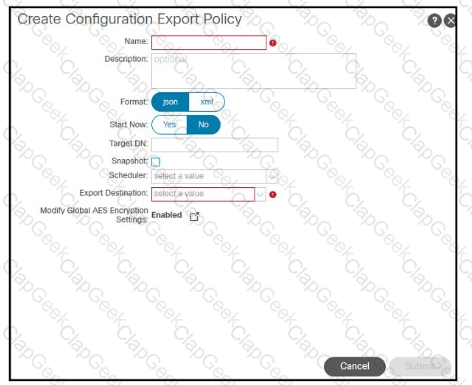
Refer to the exhibit A customer must back up the current Cisco ACl configuration securely to the remote location using encryption and authentication. The backup job must run once per day The customer s security policy mandates that any sensitive information including passwords, must not be exported from the device Which set of steps meets these requirements?

An engineer must create a backup of the Cisco ACI fabric for disaster recovery purposes. The backup must be transferred over a secure and encrypted transport. The backup file must contain all user and password related information. The engineer also wants to process and confirm the backup file validity by using a Python script. This requires the data structure to have a format similar to a Python dictionary. Which configuration set must be used to meet these requirements?
Which setting prevents the learning of Endpoint IP addresses whose subnet does not match the bridge domain subnet?
Which description regarding the initial APIC cluster discovery process is true?
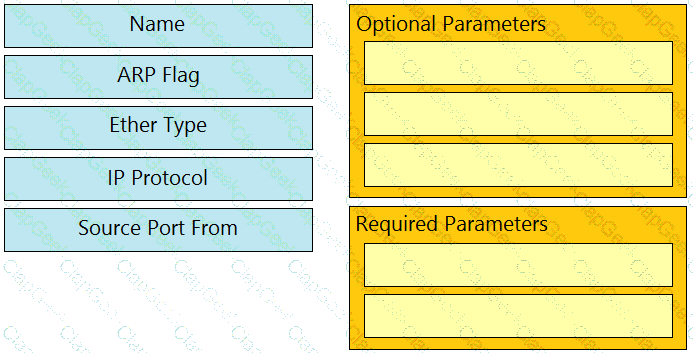
Drag and drop the Cisco ACI filter entry options from the left onto the correct categories on the right indicating what are required or optional parameters.
Regarding the MTU value of MP-BGP EVPN control plane packets in Cisco ACI, which statement about communication between spine nodes in different sites is true?
An engineer has set the VMM resolution immediacy to pre-provision in a Cisco ACI environment. No Cisco Discovery Protocol neighborship has been formed between the hypervisors and the ACI fabric leaf nodes. How does this affect the download policies to the leaf switches?
Which endpoint learning operation is completed on the egress leaf switch when traffic is received from an L3Out?
What must be enabled in the bridge domain to have the endpoint table learn the IP addresses of endpoints?
Cisco ACI fabric has three different endpoints S1, S2. and S3. These endpoints must communicate with each other without contracts. These objects have been created in APIC:
•Two EPGs named DNS_EPG and Database_EPG
•Two application profiles. PROD_App and Data_App
•Two bridge domains DNS_BD and Database_BD
•PROD_APP and Database_BD mapped to Tenant PROD
•Data_App and DNS_BD mapped to Tenant Data
Which set of actions completes the fabric configuration?
A Cisco ACI fabric is integrated with a Cisco ASA firewall using a service graph under the tenant called Operations. The fabric must permit the firewall used on tenant Operations to be referenced by the tenant called Management. Which export action must be used to accomplish this goal?
In the context of ACI Multi-Site, when is the information of an endpoint (MAC/IP) that belongs to site 1 advertised to site 2 using the EVPN control plane?
An engineer is configuring ACI VMM domain integration with Cisco UCS-B Series. Which type of port channel policy must be configured in the vSwitch policy?
An engineer must limit management access to me Cisco ACI fabric that originates from a single subnet where the NOC operates. Access should be limited to SSH and HTTPS only. Where should the policy be configured on the Cisco APIC to meet the requirements?
What are two requirements for the IPN network when implementing a Multi-Pod ACI fabric? (Choose two.)
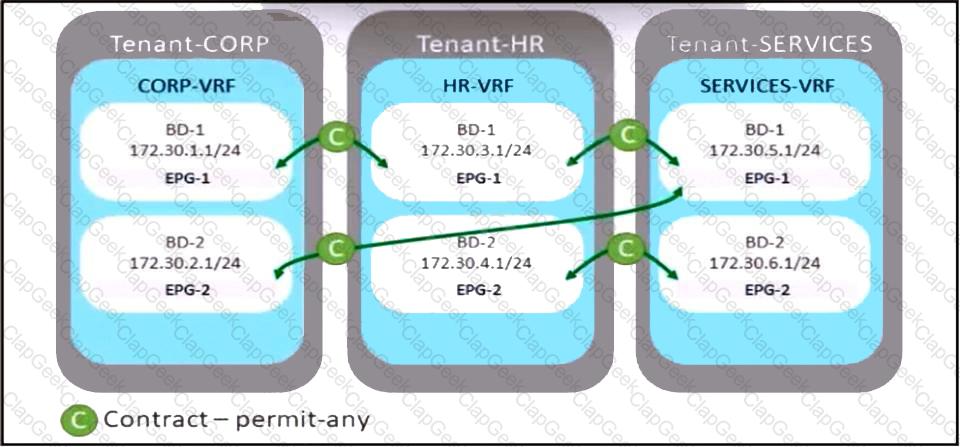
Refer to the exhibit. A company merges three of its departments: CORP, HR, and SERVICES, Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking. Which configuration meets these criteria?
The company’s Cisco ACI fabric hosts multiple customer tenants. To meet a service level agreement, the company is constantly monitoring the Cisco ACI environment. Syslog is one of the methods used for monitoring. Only events related to leaf and spine environmental information without specific customer data should be logged. To which ACI object must the configuration be applied to meet these requirements?
A RADIUS user resolves its role via the Cisco AV Pair. What object does the Cisco AV Pair resolve to?
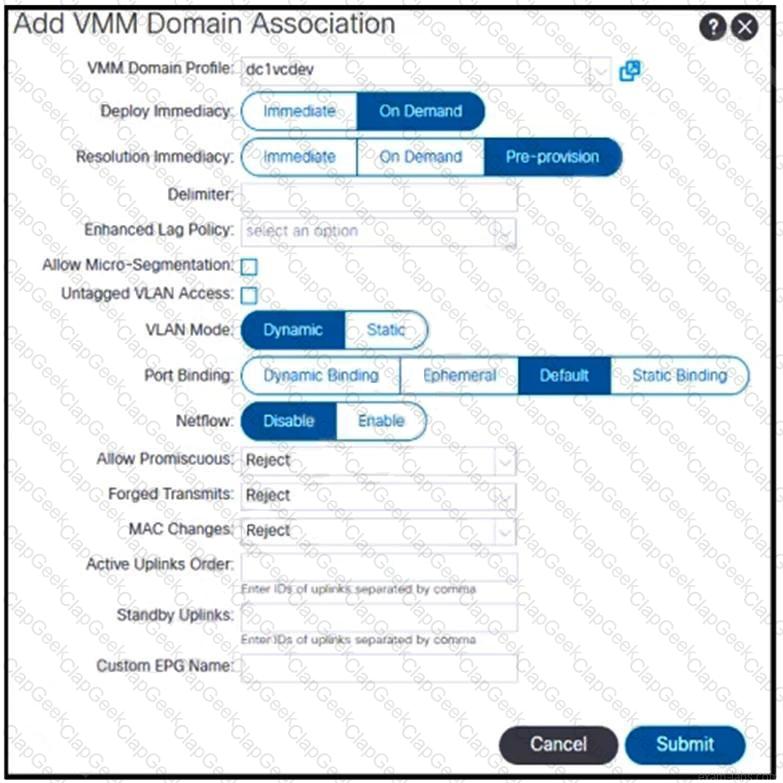
Refer to the exhibit. The EPG-100 must be extended to the vCenter as a port group with a tagged VLAN ID of 100. Which set of actions accomplishes this goal?
A network administrator configures AAA inside the Cisco ACI fabric. The authentication goes through the local users if the TACACS+ server is not reachable. If the Cisco APIC is out of the cluster, the access must be granted through the fallback domain. Which configuration set meets these requirements?
What is the result of selecting the On Demand attribute in the Deploy Immediacy feature during VMM domain association to an EPG?
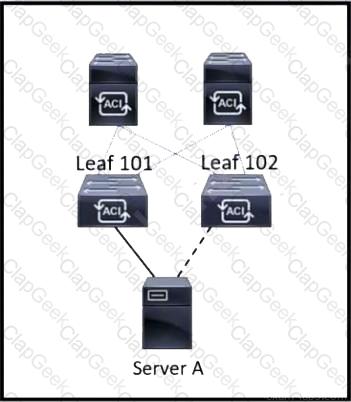
Refer to the exhibit. Server A is connected to the Cisco ACI fabric using two teamed interfaces. One interface in a team is configured as active and the other remains in standby mode. When a failover occurs and the standby interface becomes active, it uses its built-in MAC address to send traffic. Which bridge domain configuration must be applied to resolve the issue?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
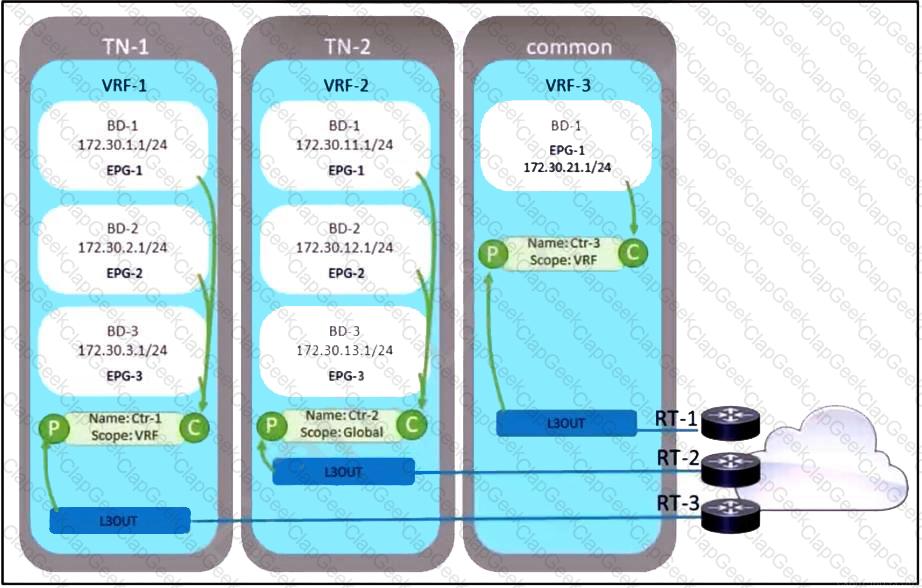
Refer to the exhibit. A company decided to decrease its routing footprint and remove RT-2 and RT-3 devices from its data center. Because of that, the exit point must be created from all the tenants by using the common tenant. Which two configuration tasks must be completed to meet these requirements? (Choose two.)
A network engineer must allow secure access to the Cisco ACl out-of-band (OOB) management only from external subnets 10 0 0024 and 192.168 20 G'25. Which configuration set accomplishes this goal?
As part of a migration, legacy non-ACI switches must be connected to the Cisco ACI fabric. All non-ACI switches run per-VLAN RSTP. After the non-ACI switches are connected to Cisco ACI, the STP convergence caused a microloop and significant CPU spike on all switches. Which configuration on the interfaces of the external switches that face the Cisco ACI fabric resolves the problem?
When Layer 3 routed traffic is destined to a Cisco ACI fabric, which mechanism does ACI use to detect silent hosts?
An engineer is implementing a Cisco ACI data center network that includes Cisco Nexus 2000 Series 10G fabric extenders. Which physical topology is supported?
A)
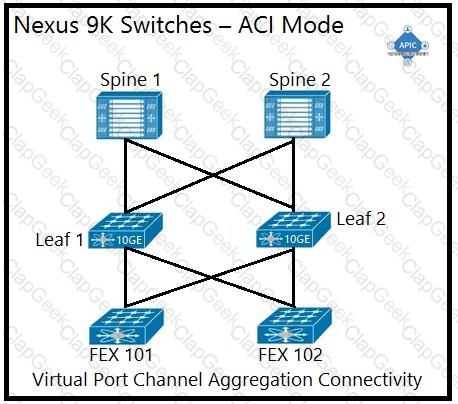
B)
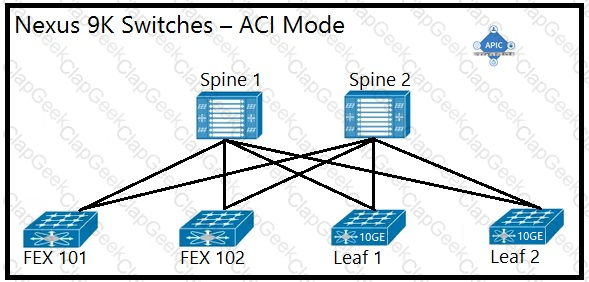
C)
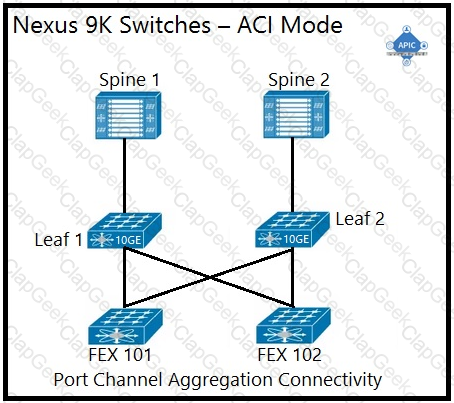
D)
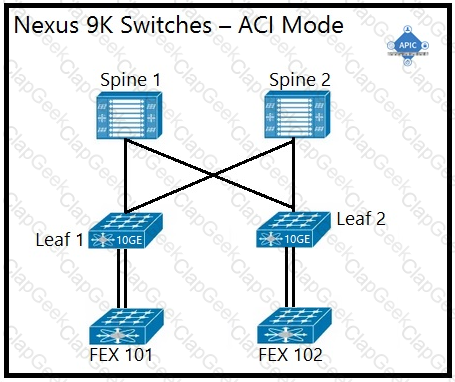
Refer to the exhibit.
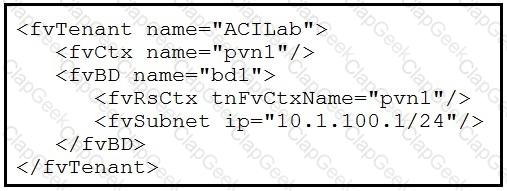
Which two objects are created as a result of the configuration? (Choose two.)


