An engineer must implement intrusion protection on the WLAN. The AP coverage is adequate and on-channel attacks are the primary concern. The building is historic, which makes adding APs difficult. Which AP mode and submode must be implemented?
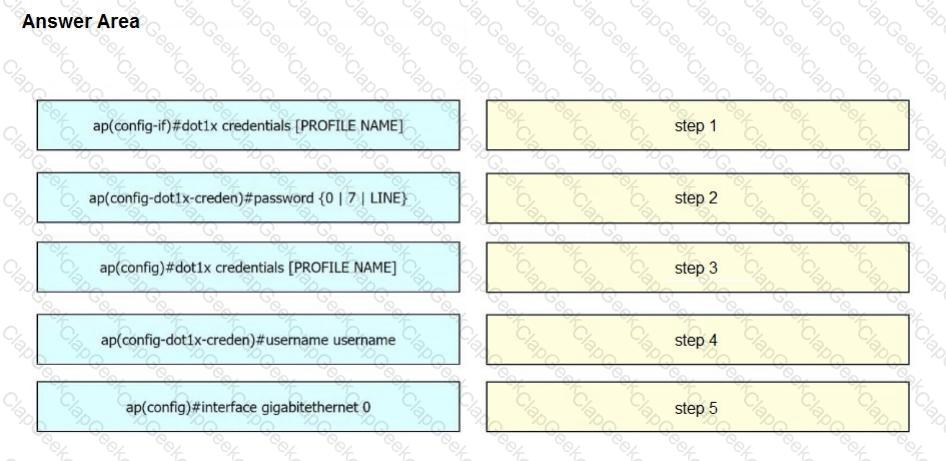
A network engineer must get an autonomous AP to authenticate to the upstream switch via IEEE 802.1 X. Drag and drop the commands from the left onto the right to complete the configuration.
Refer to the exhibit.
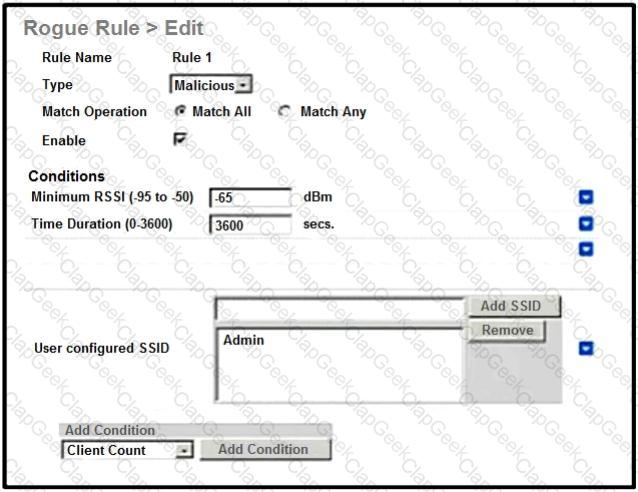
An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
An SSID is set up with central web authentication using Cisco ISE The new SSID uses guest tunneling from the foreign controller to the anchor controller. Which device must be configured ISE as the one performing the RADIUS authentication requests for the web authentication method?
An engineer has configured the wireless controller to authenticate clients on the employee SSID against Microsoft Active Directory using PEAP authentication.
Which protocol does the controller use to communicate with the authentication server?
What is the Cisco recommended configuration for a Cisco switch port connected to an AP in local mode for optimal voice over WLAN performance with an 8821 wireless phone?
Refer to the exhibit.
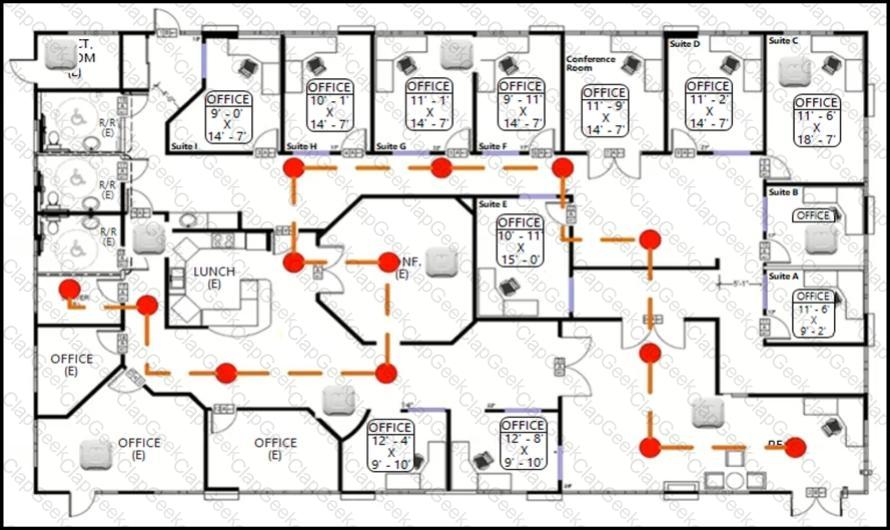
An engineer needs to configure location services in an office. The requirement is to use FastLocate and achieve higher locations refresh rates. Which location-based technique should be implemented?
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
An organization is supporting remote workers in different locations. In order to provide wireless network connectivity and services, OfficeExtend has been implemented. The wireless connectivity is working, but users report losing connectivity to their local network printers. Which solution must be used to address this issue?
A network is set up to support wired and wireless clients. Both types must authenticate using 802.1X before connecting to the network. Different types of client authentication must be separated on a Cisco ISE deployment. Which two configuration items achieve this task? (Choose two.)
An engineer is troubleshooting a Cisco CMX high-availability deployment and notices that the primary and backup Cisco CMX servers are both considered primary. Which command must the engineer run on the backup server?
An engineer is setting up a WLAN to work with a Cisco ISE as the AAA server. The company policy requires that all users be denied access to any resources until they pass the validation. Which component must be configured to achieve this stipulation?
A wireless engineer has performed a Wireshark ccapture on an 802.1x authentication process to troubleshoot a connectivity issue.
Which two types of packet does the EAP contain? (Choose two.)
An IT administrator deployed an OEAP to the home of a remote user, but the OEAP cannot reach the WLC. Which two configuration settings must be completed before an OEAP is deployed successfully? (Choose two.)
An engineer is configuring wireless guests using Cisco CWA. When a device connects, it must be redirected to the WebAuth, but this was failing. What must be configured for the device to be redirected correctly?
Refer to the exhibit.
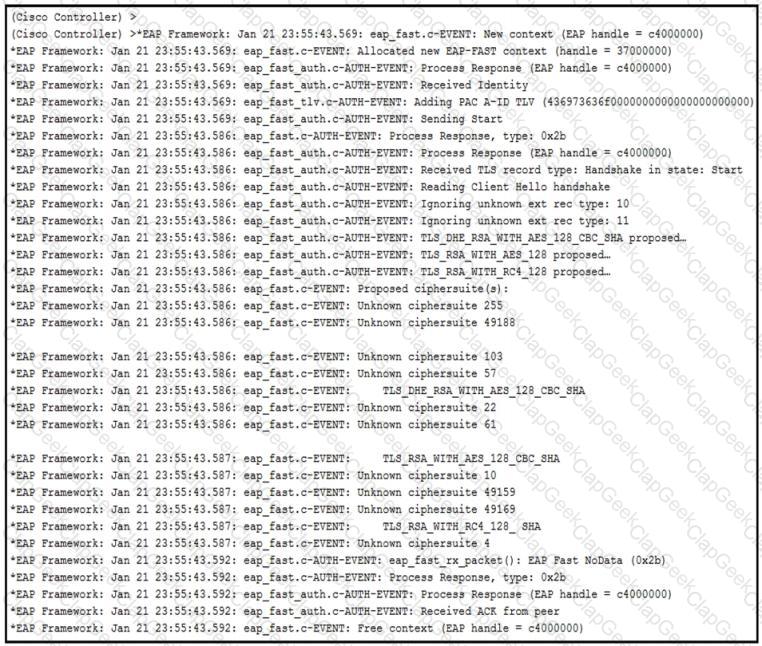
An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug on the controller provided, why is the client unable to connect?
A network engineer is implementing BYOD on a wireless network. Based on the customer requirements, a dual SSID approach must be taken. Which two advanced WLAN configurations must be performed? (Choose two.)
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
A WLAN is being configured for guest access using the portal on the Cisco CMX. Which Layer 3 security setting must be selected?
An enterprise has recently deployed a voice and video solution available to all employees using AireOS controllers. The employees must use this service over their laptops, but users report poor service when connected to the wireless network. The programs that consume bandwidth must be identified and restricted. Which configuration on the WLAN aids in recognizing the traffic?
Refer to the exhibit.
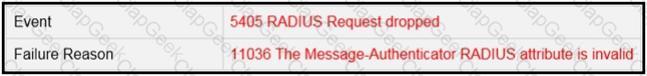
A wireless engineer has integrated the wireless network with a RADIUS server. Although the configuration on the RADIUS is correct, users are reporting that they are unable to connect. During troubleshooting, the engineer notices that the authentication requests are being dropped. Which action will resolve the issue?
Refer to the exhibit.
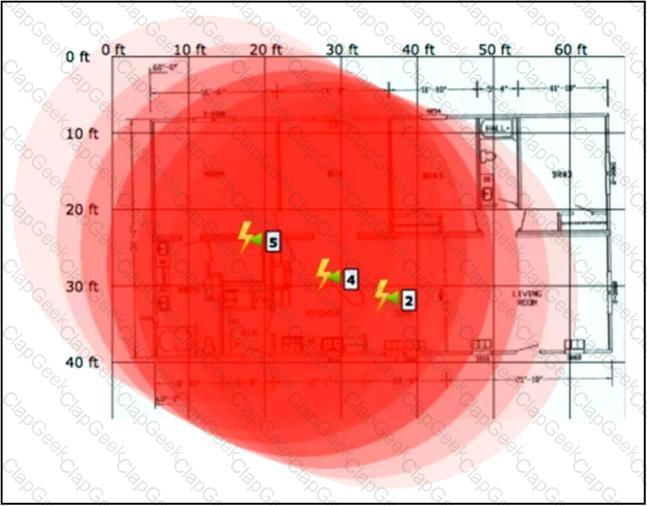
An engineer needs to manage non-802.11 interference. What is observed in the output on PI?
A wireless engineer is configuring LWA using ISE. The customer is a startup company and requested the wireless users to authenticate against a directory, but LDAP is unavailable. Which solution should be proposed in order to have the same security and user experience?
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
A company is deploying wireless PCs on forklifts within its new 10,000-square-foot(3048-square-rneter) facility.
The clients are configured for PEAP-MS-CHAPv2 with WPA TKIP. Users report that applications frequently drop when the clients roam between access points on the floor. A professional site survey was completed.
Which configuration change is recommended to improve the speed of client roaming?
An engineer has configured Cisco Centralized Key Management for an enterprise that has remote branches. The remote offices are connected back to the data center using a VPN connection with low-bandwidth connections. The goal is to improve roaming. Which type of group must be configured?
A network engineer must segregate all IPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using Cisco
ISE?
An engineer is assembling a PCI report for compliance purposes and must include missed best practices that are related to WLAN controllers. The engineer has access to all WLCs, Cisco MSE, and Cisco Prime Infrastructure. Which method most efficiently displays a summary of inconsistencies?
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802.11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
An engineer is configuring an autonomous AP to allow 802.1X authentication for users. The policy on the RADIUS server only allows for EAP-TLS authentication. Which authentication method must the engineer select under the Client Authentication Settings for the SSID on the AP?
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
An engineer must enable LSS for the AppleTV mDNS service only when ORIGIN is set to Wired. Which action meets this requirement?
A user is trying to connect to a wireless network that is configured for WPA2-Enterprise security using a corporate laptop. The CA certificate for the authentication server has been installed on the Trusted Root Certification Authorities store on the laptop. The user has been prompted to enter the credentials multiple times, but the authentication has not succeeded. What is causing the issue?
An engineer is configuring multicast for two WLCs. The controllers are in different physical locations and each handles around 500 wireless clients. How should the CAPWAP multicast group address be assigned during configuration?
An engineer is setting up a new unique NAD on a Cisco ISE.
Which two parameters must be configured? (Choose two.)
A corporation has recently implemented a BYOD policy at their HQ. Which two risks should the security director be concerned about? (Choose two.)
A network engineer has been hired to perform a new MSE implementation on an existing network. The MSE must be installed in a different network than the Cisco WLC. Which configuration allows the devices to communicate over NMSP?
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
For security purposes, an engineer enables CPU ACL and chooses an ACL on the Security > Access Control Lists > CPU Access Control Lists menu. Which kind of traffic does this change apply to as soon as the change is made?
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
An engineer must implement Cisco Identity-Based Networking Services at a remote site using ISE to dynamically assign groups of users to specific IP subnets. If the subnet assigned to a client is available at the remote site, then traffic must be offloaded locally, and subnets are unavailable at the remote site must be tunneled back to the WLC. Which feature meets these requirements?
A FlexConnect remote office deployment is using five 2702i APs indoors and two 1532i APs outdoors. When a code upgrade is performed and FlexConnect Smart AP Image Upgrade is leveraged, but no FlexConnect Master AP has been configured, how many image transfers between the WLC and APs will occur?
An engineer set up a VoWLAN with QoS on the WLC and a class map on the switch, but the markings are not being preserved correctly in the end-to- end traffic flow. Which two configurations on the wired network ensure end-to-end QoS? (Choose two.)
A network engineer is implementing BYOD on a wireless network. Based on the customer requirements, a dual SSID approach must be taken. Which two advanced WLAN configurations must be performed? (Choose two.)
A customer wants to allow employees to easily onboard their personal devices to the wireless network. The visitors also must be able to connect to the same network without the need to engage with anyone from the reception desk. Which process must be configured on Cisco ISE to support this requirement?
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
Refer to the exhibit. A network administrator must automate notifications for Security Advisories Data reports on the Cisco Catalyst Center v2.3.7 using the Report notification feature. Preferring a programmable approach over UI/CLI, the administrator decides to create a webhook via the Cisco DNA Center API to send real-time HTTP notifications to an external application. The webhook URL https://example.com/webhook uses HTTPS with a self-signed certificate, which requires a specific configuration in the payload to ensure the webhook functions correctly. Which code snippet must be placed onto the box in the code to complete the Python script that configures the webhook to use the self-signed certificate to extract the Security Advisories Data report?

An engineer is working for an organization that recently deployed Cisco SD-Access-based network with all SSIDs working in Fabric-enabled wireless. A recent project requires third-party APs to be connected to the access switches for some interoperability testing. However, Cisco Catalyst Center (formerly DNA Center) detects these APs as rogue on the wire. Which action must the engineer take to avoid reporting third-party APs as high-threat rogue and containing them?
You are configuring the social login for a guest network. Which three options are configurable social connectors in Cisco CMX Visitor Connect? (Chose three)
An engineer must run a Client Traffic Stream Metrics report in Cisco Prime Infrastructure. Which task must be run before the report?
CMX Facebook Wi-Fi allows access to the network before authentication. Which two elements are available? (Choose two.)
An engineer must provide a graphical report with summary grouped data of the total number of wireless clients on the network. Which Cisco Prime Infrastructure report provides the required data?
A healthcare organization notices many rogue APs and is concerned about a honeypot attack. Which configuration must a wireless network engineer perform in Cisco Prime Infrastructure to prevent these attacks most efficiently upon detection?
An engineer needs to provision certificates on a Cisco Catalyst 9800 Series Wireless Controller. The customer uses a third-party CA server. Which protocol must be used between the controller and CA server to request and install certificates?
You plan to implement Cisco Identity Based Networking Services on a Cisco Catalyst 3850 Series Switch. Which switch command is required when configuring downloadable ACLs?
Which two restrictions are in place with regards to configuring mDNS? (Choose two.)
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802.11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
A customer is deploying local web authentication. Which software application must be implemented on Cisco ISE to utilize as a directory service?
A hospital wants to offer indoor directions to patient rooms utilizing its existing wireless infrastructure. The wireless network has been using location services specifications. Which two components must be installed to support this requirement? (Choose two.)
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
A shopping center uses AireOS controllers with Cisco Wave 2 APs. A separate WLAN named Guest-012345678-WLAN is used for guest wireless clients. Management needs location analytics to determine popular areas. CMX must track only associated clients. What must be selected on the CMX server settings?
An engineer must use Cisco AVC on a Cisco WLC to prioritize Cisco IP cameras that use the wireless network. Which element do you configure in a rule?
An engineer needs to configure an autonomous AP for 802.1x authentication. To achieve the highest security an authentication server is used for user authentication. During testing, the AP fails to pass the user authentication request to the authentication server. Which two details need to be configured on the AP to allow communication between the server and the AP? (Choose two.)
An engineer is configuring multicast for wireless for an all-company video meeting on a network using EIGRP and BGP within a single domain from a single source. Which type of multicast routing should be implemented?
Which role does an engineer configure for administrative access to the wireless infrastructure, using Cisco ISE, to allow configuration of the WLC syslog configuration?
An engineer is considering an MDM integration with Cisco ISE to assist with security for lost devices.
Which two functions of MDM increase security for lost devices that access data from the network? (Choose two.)
The security learn is concerned about the access to all network devices, including the Cisco WLC. To permit only the admin subnet to have access to management, a CPU ACL is created and applied. However, guest users cannot get to the web portal. What must be configured to permit only admins to have access?
An engineer must implement rogue containment for an SSID. What is the maximum number of APs that should be used for containment?
A customer managing a large network has implemented location services. Due to heavy load, it is needed to load balance the data coming through NMSP from the WLCs. Load must be spread between multiple CMX servers to help optimize the data flow for APs. Which configuration in CMX meets this requirement?
An engineer has been hired to implement a way for users to stream video content without having issues on the wireless network. To accomplish this goal, the engineer must set up a reliable way for a Media Stream to work between Cisco FlexConnect APs. Which feature must be enabled to guarantee delivery?
A network engineer must get an autonomous AP to authenticate to the upstream switch via IEEE 802.1 X. Drag and drop the commands from the left onto the right to complete the configuration.

A network engineer is configuring a Cisco AireOS WLC environment for central web authentication using Cisco ISE.
The controllers are configured using auto-anchor for the guest network.
Which three components must be implemented for the foreign WLC?(Choose three.)
A WLC must be configured to allow multiple mDNS profiles based on a user authentication profile configured in Cisco ISE. Which WLAN setting must be configured?
An engineer is deploying a virtual MSE. The network has 3000 APs and needs 7000 IPS licenses.
To which size server does the engineer scale it?
An engineer configured a Cisco AireOS controller with two TACACS+ servers. The engineer notices that when the primary TACACS+ server fails, the WLC starts using the secondary server as expected, but the WLC does not use the primary server again until the secondary server fails or the controller is rebooted. Which cause of this issue is true?


