Refer to the exhibit.
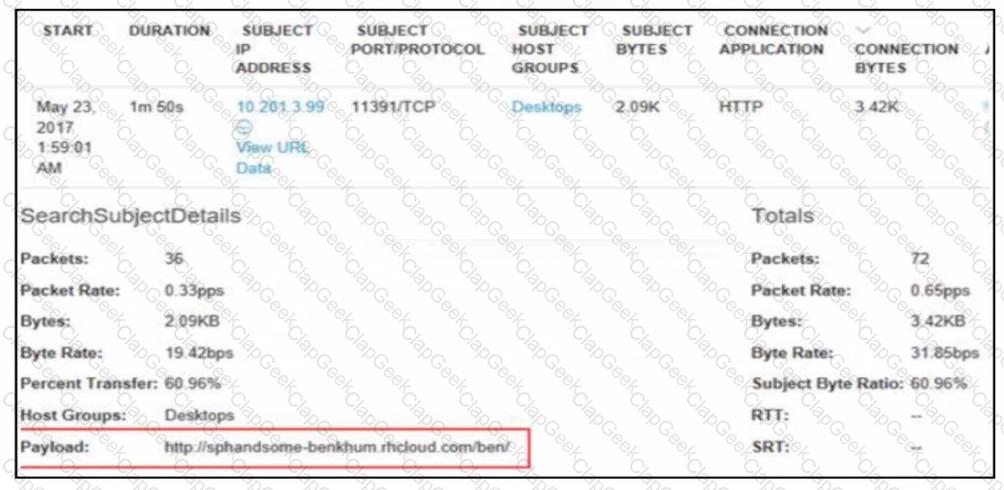
A security analyst receives an alert from Cisco Secure Network Analytics (formerly StealthWatch) with the C2 category. Which information aids the investigation?
A SOC team using Cisco security technologies wants to improve its ability to detect threats that bypass traditional security controls by abusing valid user credentials. Which hunting focus MOST effectively addresses this challenge?
A SOC leadership team wants to demonstrate the business value of investing in Cisco-based threat hunting capabilities. Which outcome BEST demonstrates that value?
While analyzing telemetry from Cisco Secure Endpoint and Secure Network Analytics, analysts observe that an adversary consistently avoids deploying malware and instead abuses built-in administrative tools. Why does this observation matter for attribution?
A security team is performing threat modeling for a hybrid environment consisting of on-prem Active Directory and Azure AD. The team wants to identify how an attacker could move from a compromised cloud identity to full on-prem domain dominance. Which modeling focus is MOST appropriate?
A SOC team wants to detect lateral movement performed using legitimate administrative tools rather than malware. Which telemetry source provides the MOST reliable visibility for this hunting objective?
Refer to the exhibit.
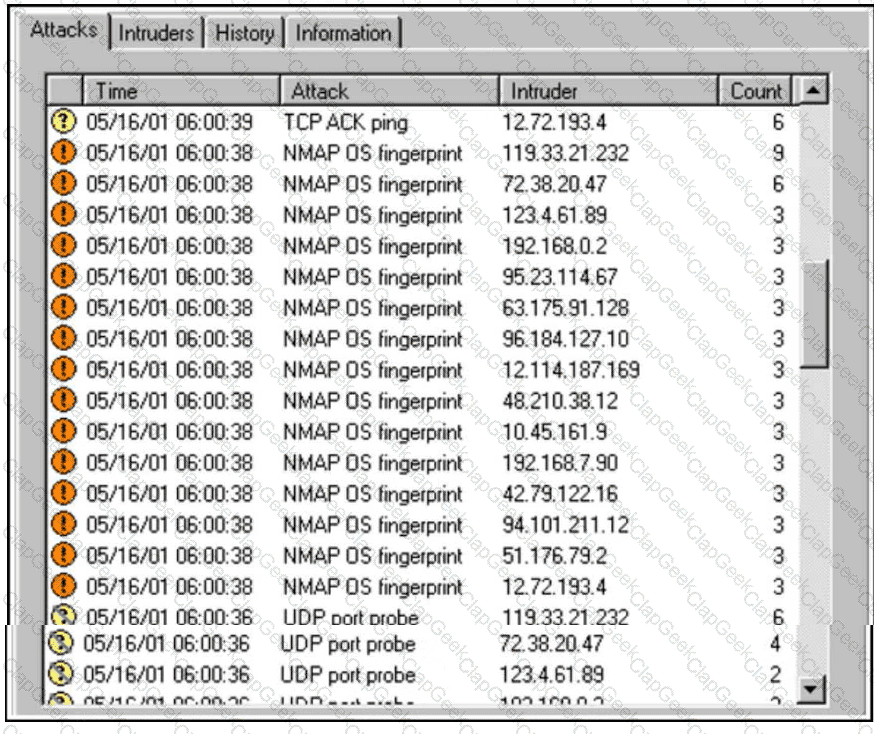
An increase in company traffic is observed by the SOC team. After they investigate the spike, it is concluded that the increase is due to ongoing scanning activity. Further analysis reveals that an adversary used Nmap for OS fingerprinting. Which type of indicators used by the adversary sits highest on the Pyramid of Pain?
Refer to the exhibit.

A company went through several rounds of restructuring and the previous security team has been let go A new engineer joins and rediscovers all the tools thatthe previous team left behind.One of the tools Is a Bash script related to monitoring AWS accounts for threats What is the purpose of the script?
During multiple investigations using Cisco telemetry, analysts observe attackers consistently perform internal discovery before privilege escalation and avoid high-risk actions. Why is this observation useful for attribution?
During an investigation, analysts observe that attackers consistently avoid PowerShell logging, disable AMSI, and prefer WMI for execution. Why is this information critical for attribution?
A SOC manager wants to evaluate whether the organization’s Cisco-based threat hunting program is improving over time. Which metric BEST reflects increased threat hunting effectiveness?
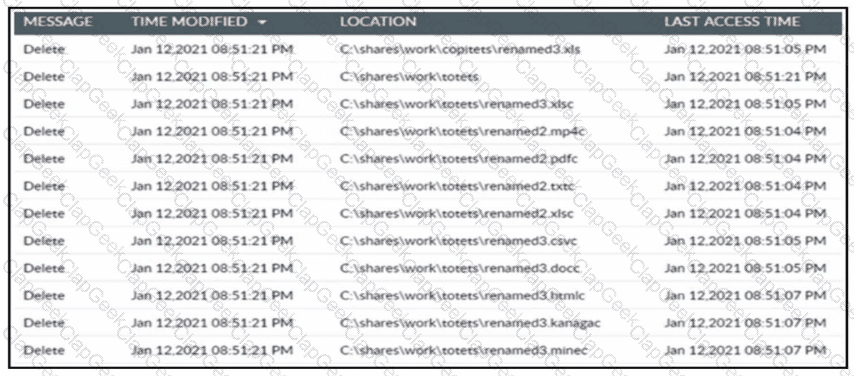
Refer to the exhibit. A cybersecurity team receives an alert from its Intrusion Prevention System about multiple file changes to a file server. Before the changes were made, the team detected a successful remote sign-in from a user account to the server. Which type of threat occurred?
During a structured hunt, analysts using Cisco SIEM tools complete hypothesis testing and confirm malicious activity. What is the NEXT step in the Cisco threat hunting lifecycle?
A structured threat hunt using Cisco Secure Network Analytics confirms abnormal internal SMB traffic consistent with lateral movement. Which action should occur NEXT to improve organizational security posture?
After a multi-week threat hunting exercise, a security team confirms that an attacker gained access using valid credentials, moved laterally, and exfiltrated data without deploying malware. Senior leadership asks how the hunting program reduced organizational risk. Which outcome BEST demonstrates the value of threat hunting?


