A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
Rotor to the exhibit.
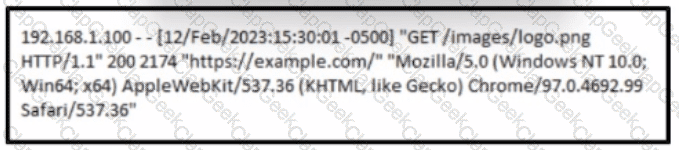
A cybersecurity analyst must analyst the logs from an Apache server for the client. The concern is that an offboarded employee home IP address was potentially used to access the company web server via a still active VPN connection Based on this log entry, what should an analyst conclude?
An attacker embedded a macro within a word processing file opened by a user in an organization’s legal department. The attacker used this technique to gain access to confidential financial data. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook. Which two elements are part of the eradication phase for this incident? (Choose two.)
Refer to the exhibit.
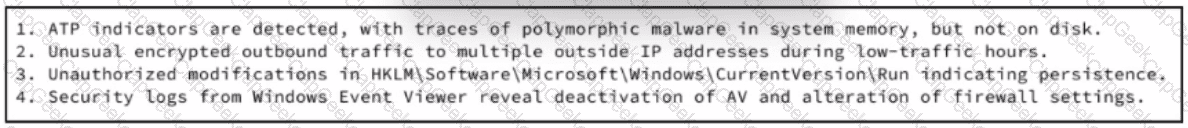
An experienced cybersecurity analyst is investigating a sophisticated suspected breach on a Windows server within an enterprise network and compiled the evidence gathered so far Which action should the analyst prioritize to understand the scope and impact of the breach?
During a routine security audit, an organization's security team detects an unusual spike in network traffic originating from one of their internal servers. Upon further investigation, the team discovered that the server was communicating with an external IP address known for hosting malicious content. The security team suspects that the server may have been compromised. As the incident response process begins, which two actions should be taken during the initial assessment phase of this incident? (Choose two.)
Which information is provided about the object file by the “-h” option in the objdump line command objdump –b oasys –m vax –h fu.o?
In a secure government communication network, an automated alert indicates the presence of anomalous DLL files injected into the system memory during a routine update of communication protocols. These DLL files are exhibiting beaconing behavior to a satellite IP known for signal interception risks. Concurrently, there is an uptick in encrypted traffic volumes that suggests possible data exfiltration. Which set of actions should the security engineer prioritize?
An incident responder reviews a log entry that shows a Microsoft Word process initiating an outbound network connection followed by PowerShell execution with obfuscated commands. Considering the machine's role in a sensitive data department, what is the most critical action for the responder to take next to analyze this output for potential indicators of compromise?
Refer to the exhibit.
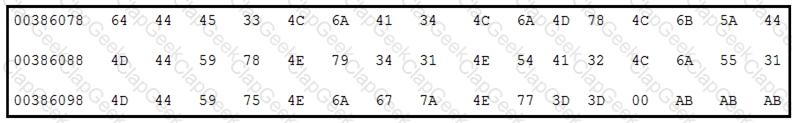
Which encoding technique is represented by this HEX string?
Data has been exfiltrated and advertised for sale on the dark web. A web server shows:
Database unresponsiveness
PageFile.sys changes
Disk usage spikes with CPU spikes
High page faults
Which action should the IR team perform on the server?
Refer to the exhibit.
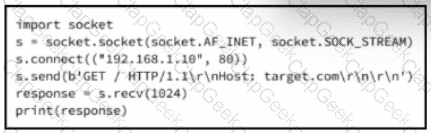
A cybersecurity analyst is presented with the snippet of code used by the threat actor and left behind during the latest incident and is asked to determine its type based on its structure and functionality. What is the type of code being examined?
An incident response analyst is preparing to scan memory using a YARA rule. How is this task completed?
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?


A company had a recent data leak incident. A security engineer investigating the incident discovered that a malicious link was accessed by multiple employees. Further investigation revealed targeted phishing attack attempts on macOS systems, which led to backdoor installations and data compromise. Which two security solutions should a security engineer recommend to mitigate similar attacks in the future? (Choose two.)
Refer to the exhibit.
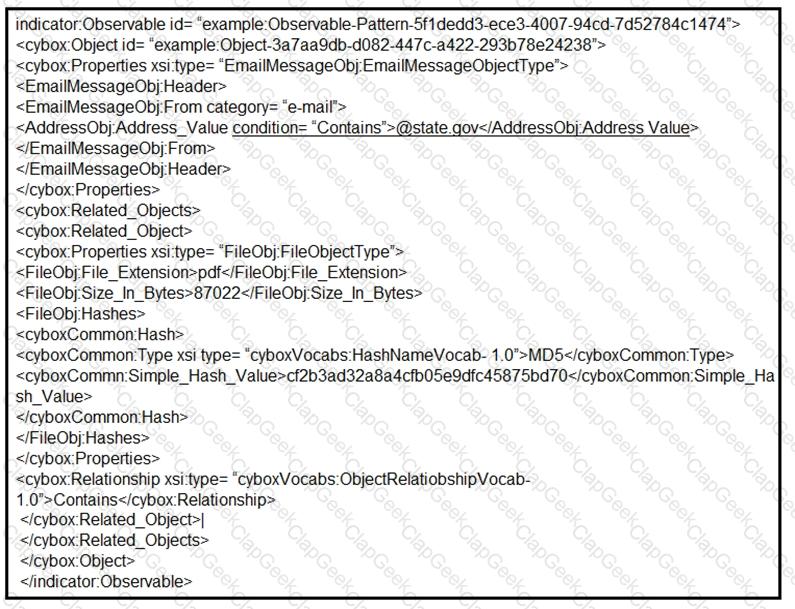
Which two actions should be taken as a result of this information? (Choose two.)
Refer to the exhibit.
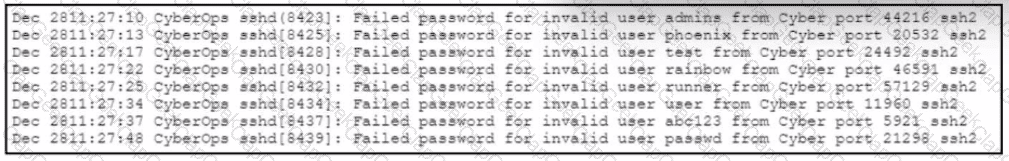
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor activities. Which attack vector is used and what mitigation can the analyst suggest?
A malware outbreak revealed that a firewall was misconfigured, allowing external access to the SharePoint server. What should the security team do next?
A cybersecurity analyst detects fileless malware activity on secure endpoints. What should be done next?
During an overnight shift, a cybersecurity team at a global trading firm detects irregular activity The network intrusion system flags an encrypted traffic spike from high-value transaction servers to an anonymous Tor exit node Simultaneously, internal surveillance tools report unusual database queries and access patterns resembling exfiltration techniques Which focused action should the team take first to analyze and address these potential security threats?
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner;
several network systems were affected as a result of the latency in detection;
security engineers were able to mitigate the threat and bring systems back to a stable state; and
the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
Refer to the exhibit.
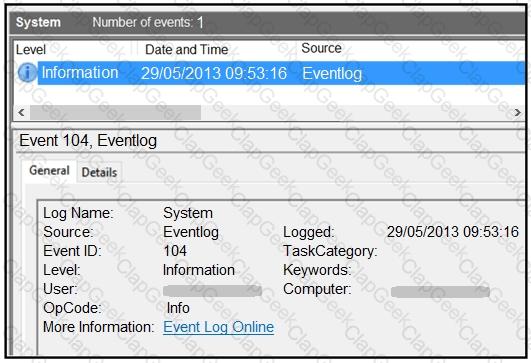
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
Refer to the exhibit.

A security analyst is reviewing alerts from the SIEM system that was just implemented and notices a possible indication of an attack because the SSHD system just went live and there should be nobody using it. Which action should the analyst take to respond to the alert?
A threat intelligence report identifies an outbreak of a new ransomware strain spreading via phishing emails that contain malicious URLs. A compromised cloud service provider, XYZCloud, is managing the SMTP servers that are sending the phishing emails. A security analyst reviews the potential phishing emails and identifies that the email is coming from XYZCloud. The user has not clicked the embedded malicious URL. What is the next step that the security analyst should take to identify risk to the organization?


