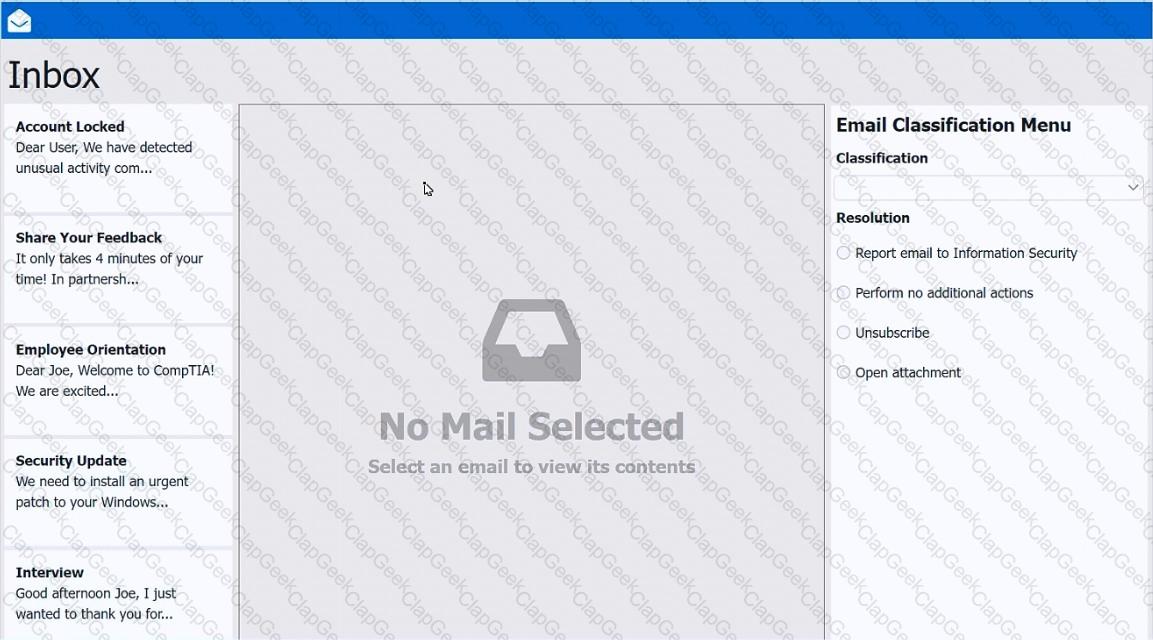
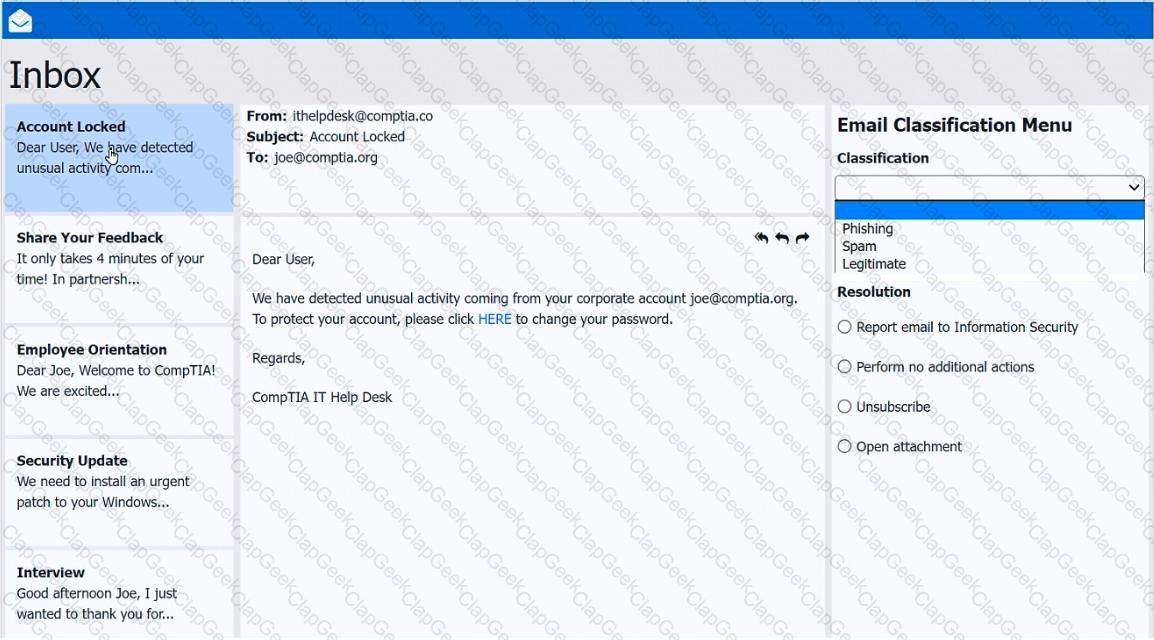
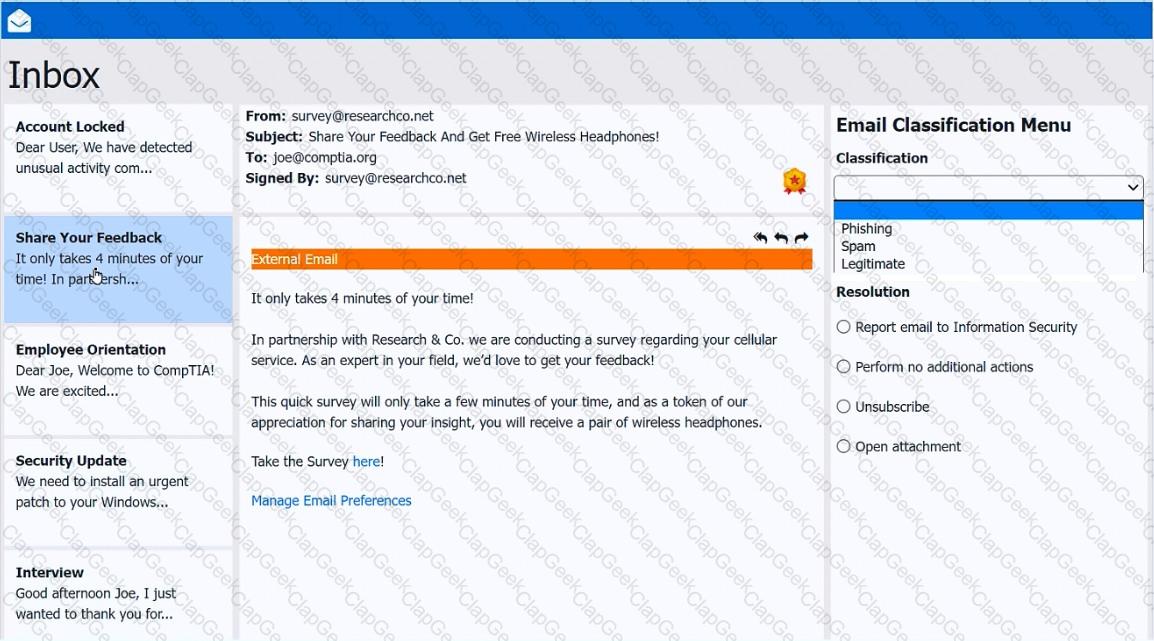
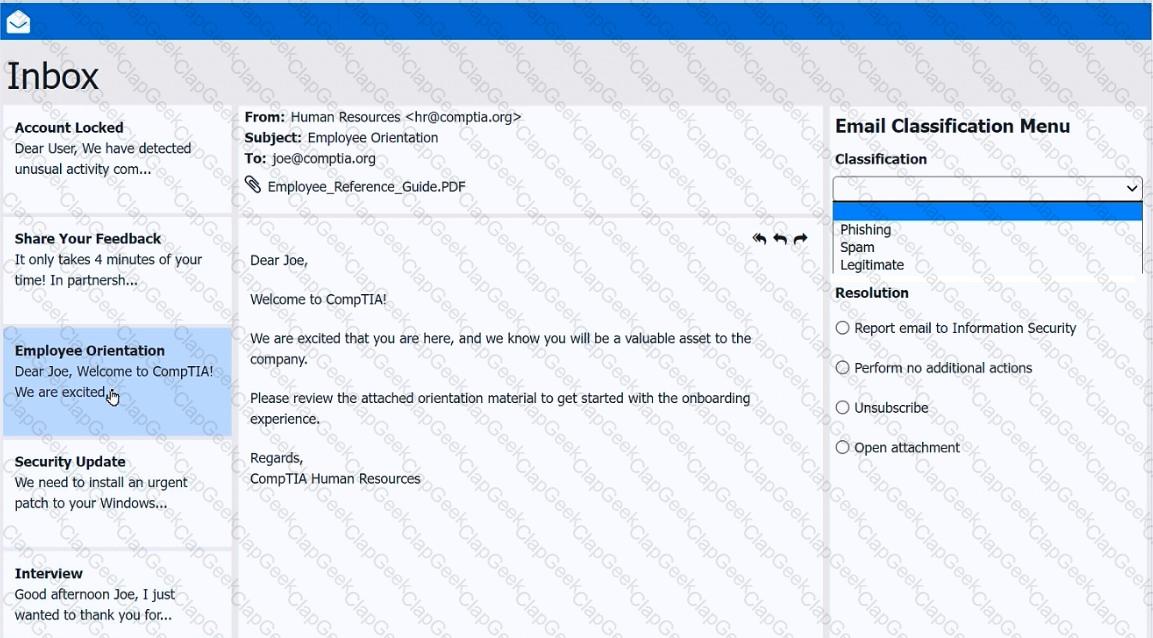
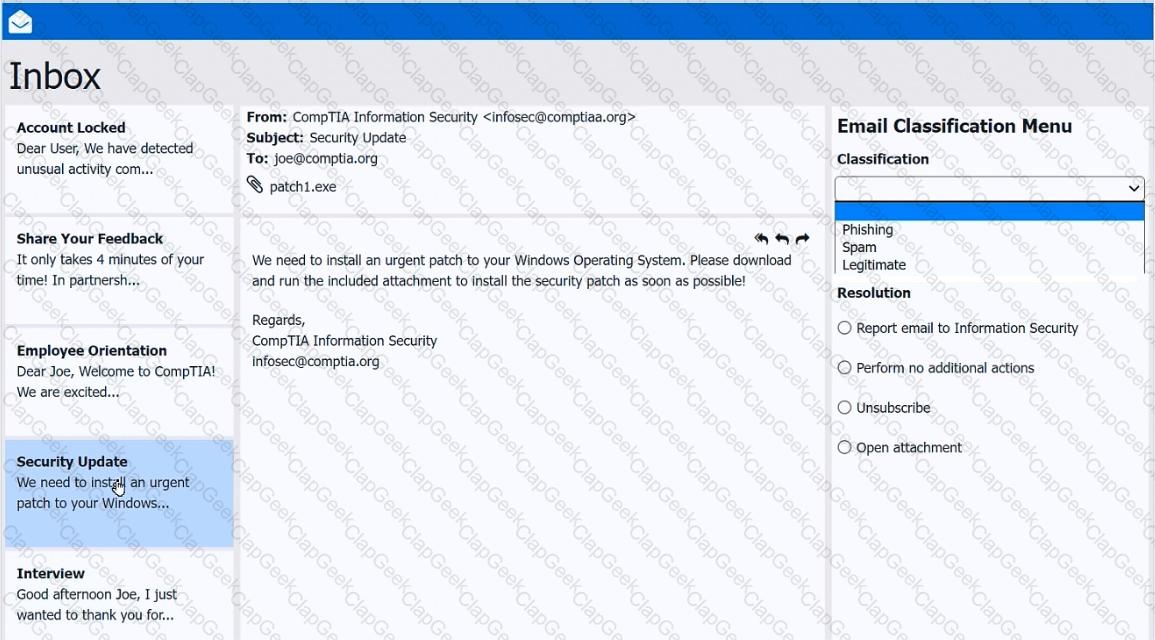
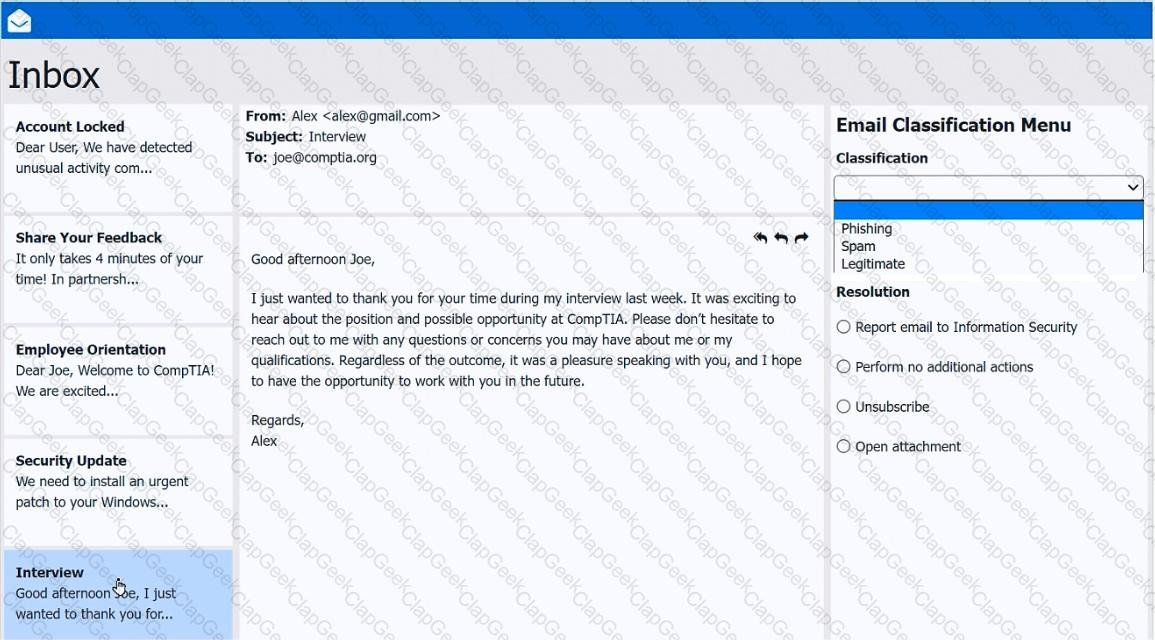
As a corporate technician, you are asked to evaluate several suspect email messages on a client's computer. Corporate policy requires the following:
>All phishing attempts must be reported.
>Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the following within the email:
>Classify the emails
>Identify suspicious items, if applicable, in each email
>Select the appropriate resolution
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
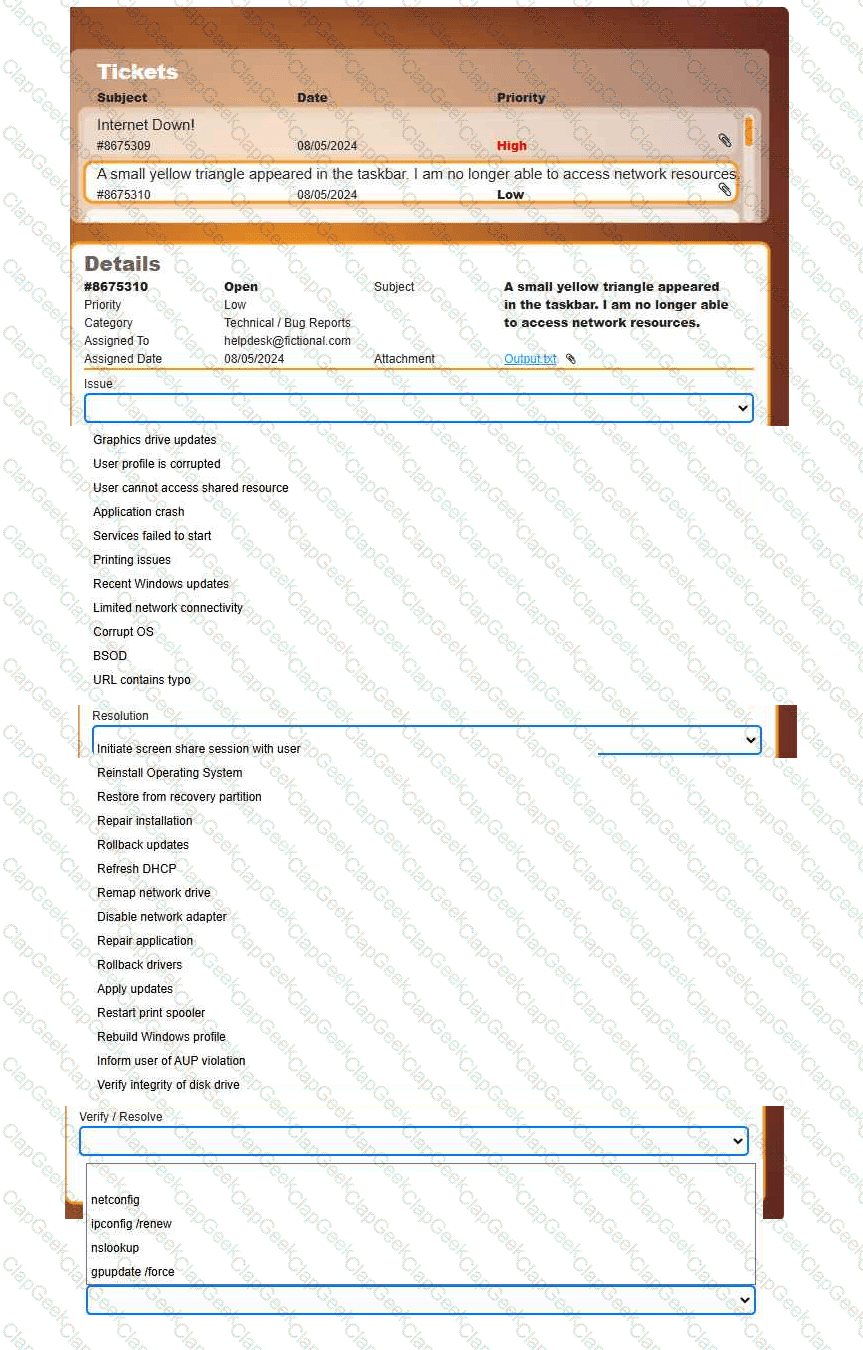
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
After completing malware removal steps, what is the next step the technician should take?
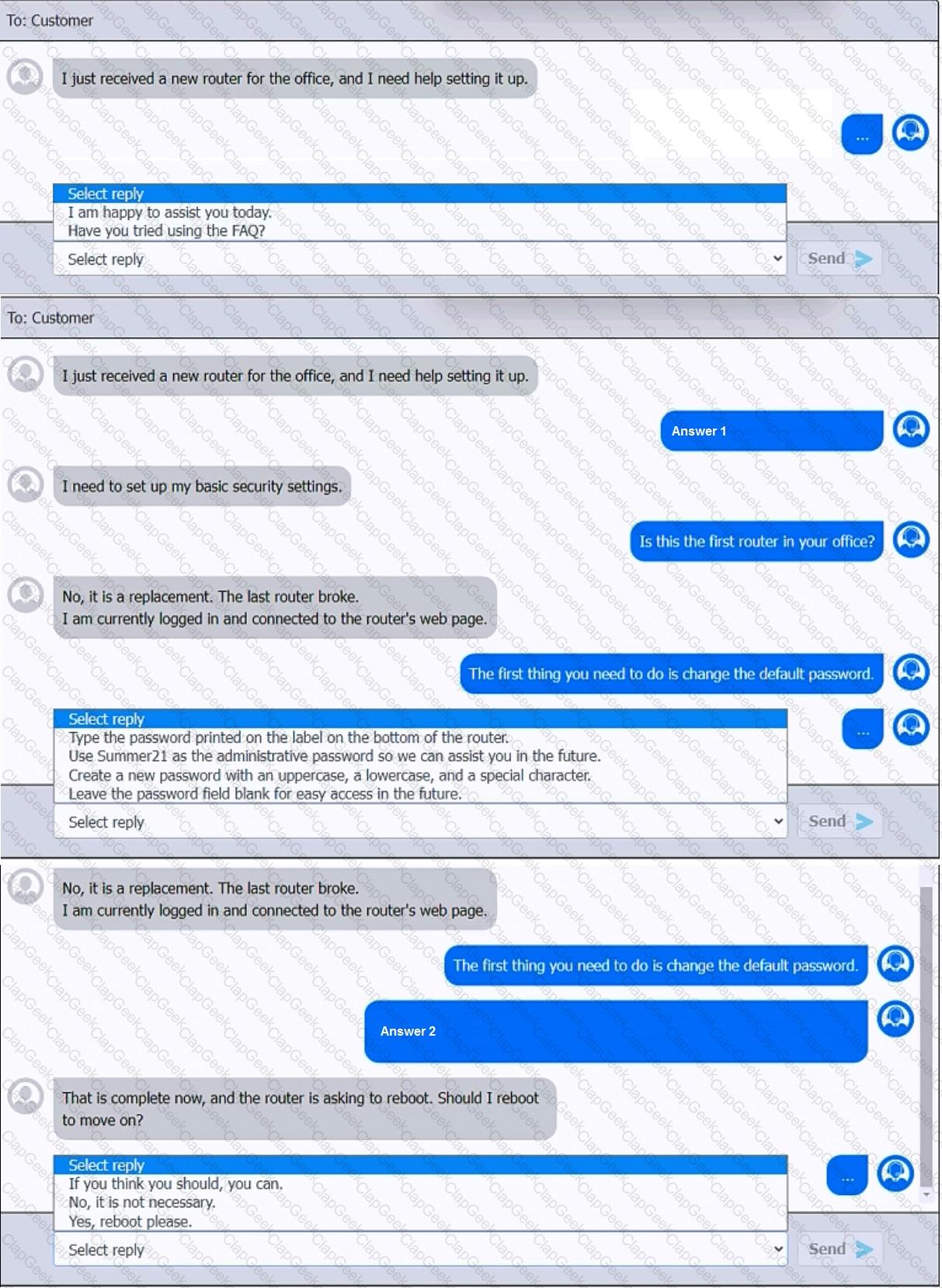
You have been contacted through the help desk chat application. A user is setting up a replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A technician is setting up a Windows server to allow remote desktop connections for multiple users. Which of the following should the technician configure on the workstation?
A user reports that their corporate mobile phone is lost. Which of the following protects the data locally on the phone from unauthorized access?
Which of the following file types allows macOS users to uninstall software completely by placing the file in the trash?
A popular game frequently freezes and crashes on a mobile phone. The user updates the OS, but the issue persists. The device is one year old and has plenty of free storage space. Which of the following is the most appropriate first step to troubleshoot this issue?
What is the next step a technician should take after completing malware cleanup?
MFA for a custom web application on a user's smartphone is no longer working. The last time the user remembered it working was before taking a vacation to another country. Which of the following should the technician do first?
A user is unable to use the latest version of an app on a legacy tablet. What is the most likely reason?
A user renames a .txt file to an .xml file. Windows Explorer shows the filename as Document.xml, but the file properties still show the type as Text Document (.txt). Which of the following controls enables the user to correctly change the file type?
A technician needs to prevent accidental access to Wi-Fi networks available in a shared office space. The BYOD and company-owned devices already have Wi-Fi settings configured via MDM solutions. Which of the following settings should the technician change?
An engineer notices that many websites prompt users to input login and payment details. The engineer wants to require the browser to encrypt communications. Which of the following best helps to protect sensitive data?
A company wants to use a single operating system for its workstations and servers and avoid licensing fees. Which of the following operating systems would the company most likely select?
An employee is trying to connect their company laptop to an airport’s Wi-Fi during a business trip. Once the network is connected, a pop-up window appears with the airport logo, which the employee quickly closes. The internet connection is not working properly. Which of the following should a help desk technician suggest?
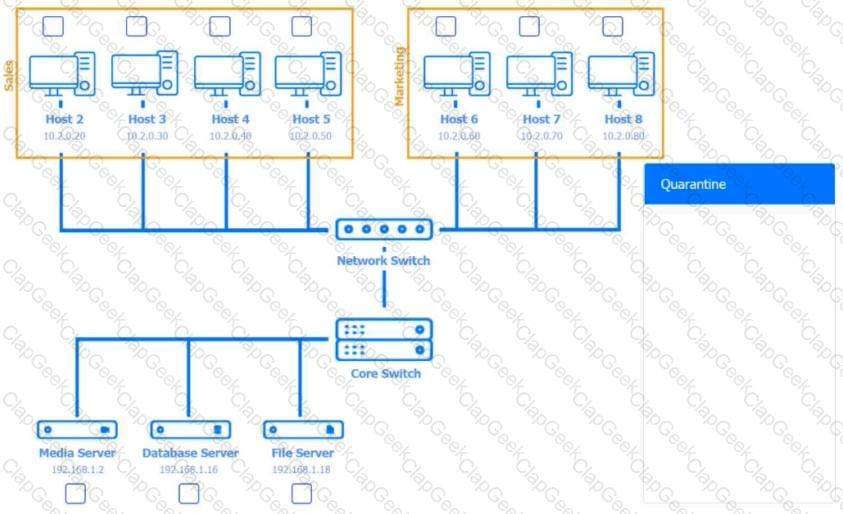
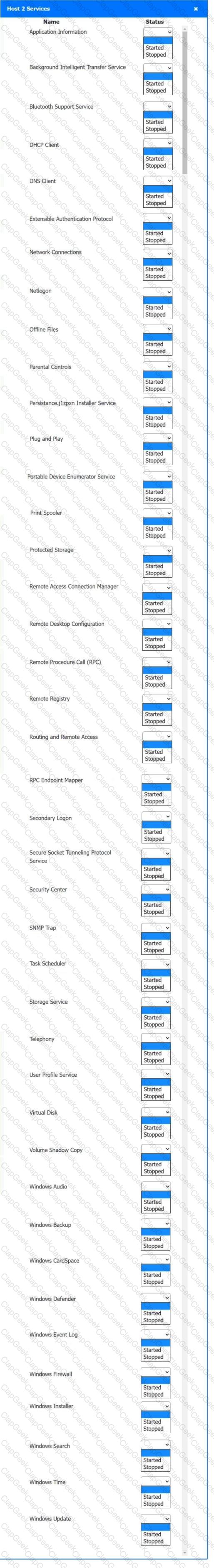
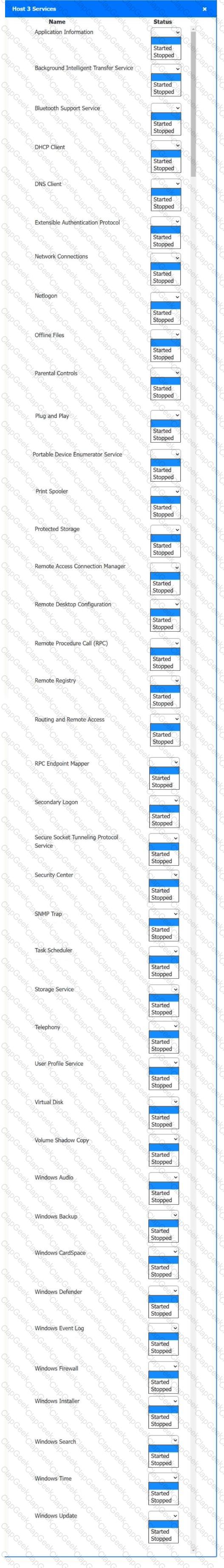
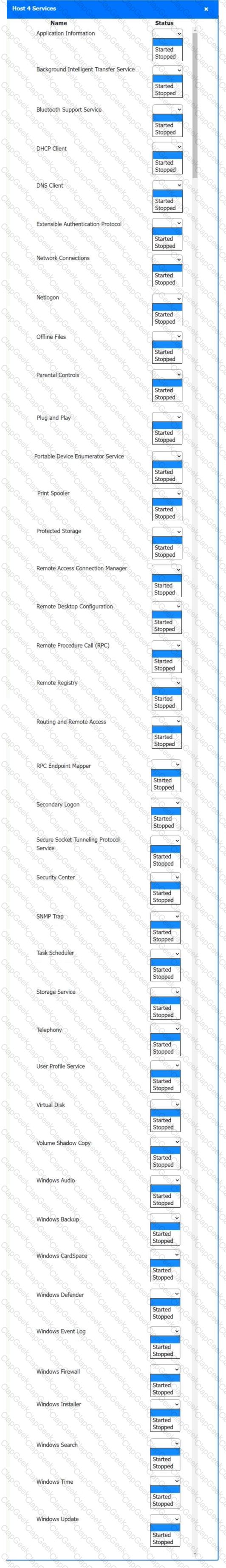
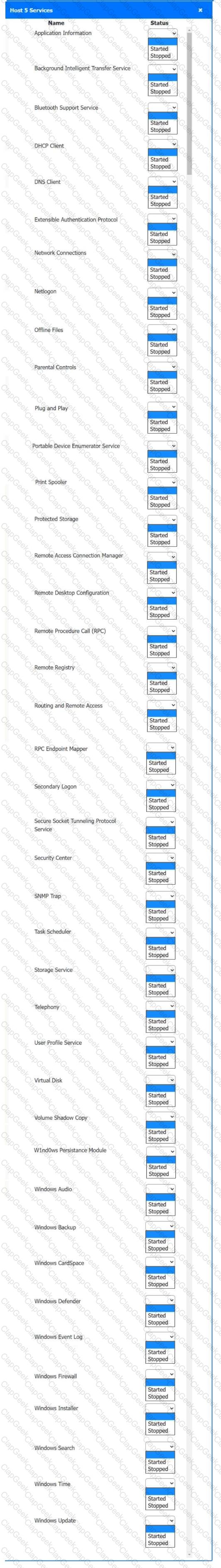
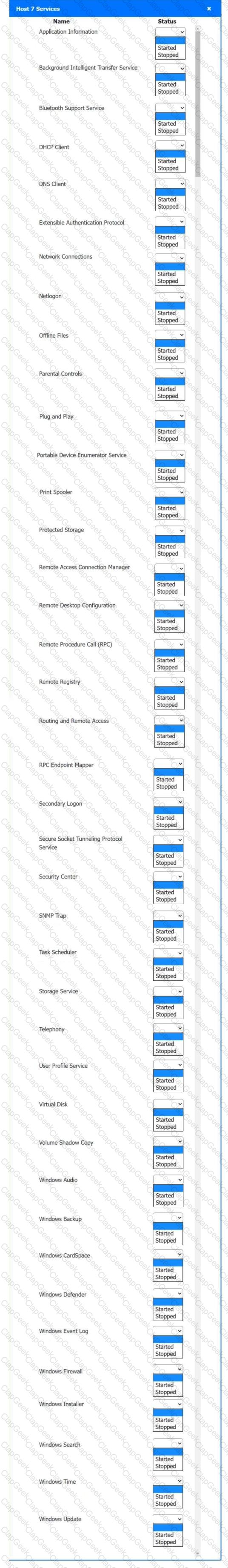
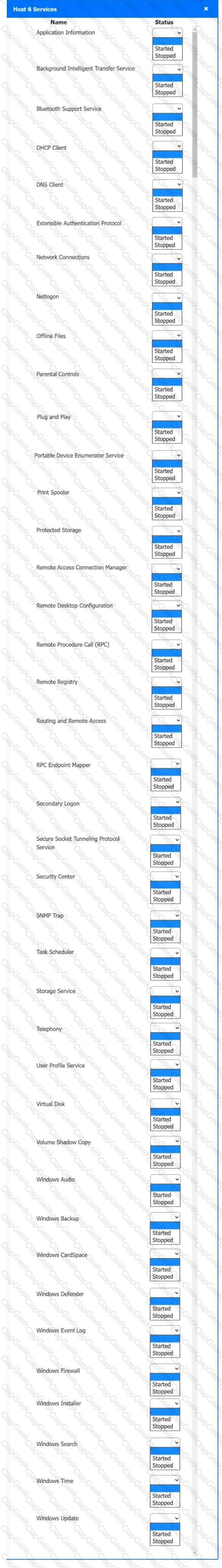
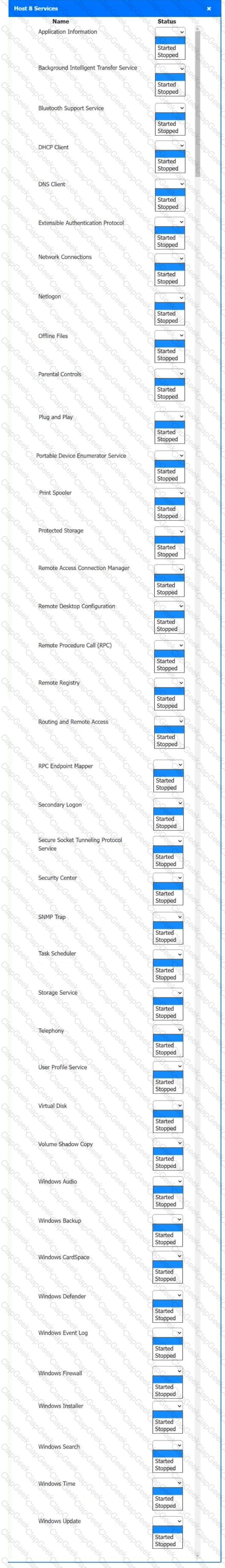
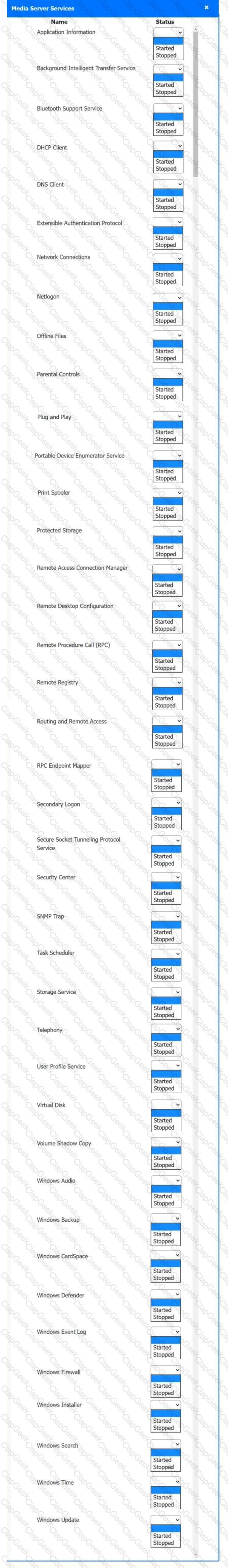
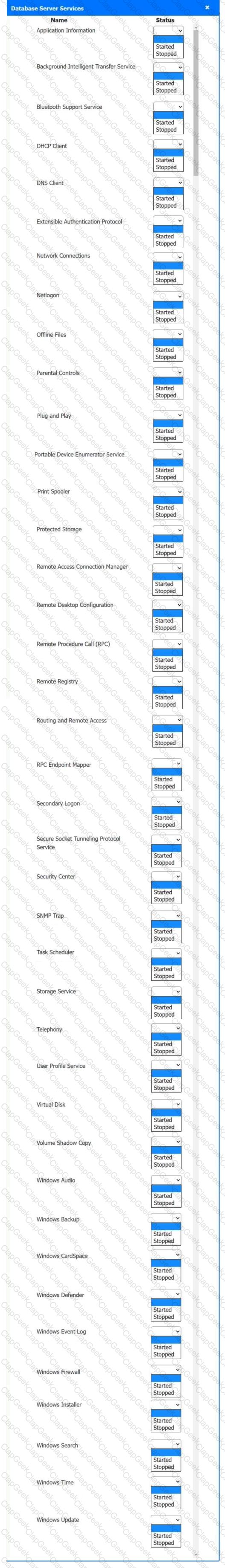
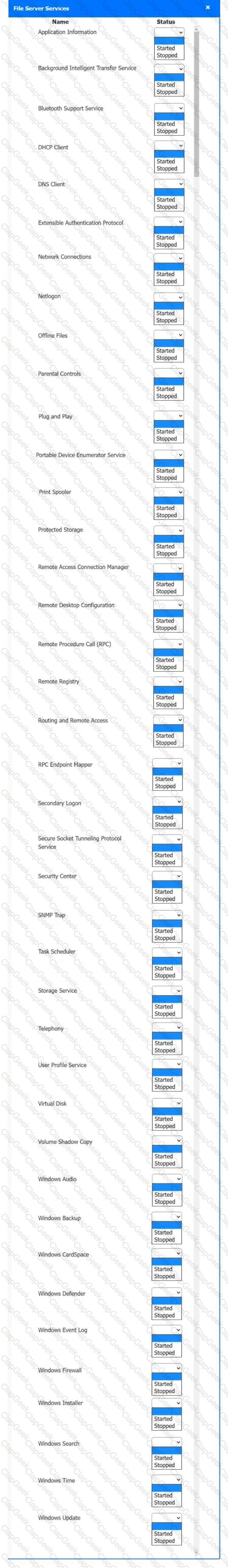
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users’ audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
The screen of a previously working computer repeatedly displays an OS Not Found error message when the computer is started. Only a USB drive, a keyboard, and a mouse are plugged into the computer. Which of the following should a technician do first?
Which of the following is an example of an application publisher including undisclosed additional software in an installation package?
A secretary receives an email from the company's chief executive officer with a request to pay a vendor immediately. After the payment is made, the CEO informs the secretary that they never sent that email. Which of the following social engineering tactics best describes this type of attack?
A company executive is currently attending a major music festival with a large number of attendees and is having trouble accessing a work email account. The email application is not downloading emails and also appears to become stuck during connection attempts. Which of the following is most likely causing the disruption?
Various alerts on a user's Windows 11 laptop are continually interrupting the user during videoconference calls. Which of the following should a support technician recommend to best solve the issue?
A technician thinks that an application a user downloaded from the internet may not be the legitimate one, even though the name is the same. The technician needs to confirm whether the application is legitimate. Which of the following should the technician do?
A Microsoft OS laptop user requests an alternative log-in authentication method because they have forgotten their password multiple times. Which of the following should a technician enable to satisfy this request?
After a technician upgrades the RAM on a user's workstation, the system shows a “No boot device found” message. Which of the following is most likely the cause?
Which of the following is used to apply corporate restrictions on an Apple device?
Which of the following Linux commands is used to read another command's documentation?
A user is unable to upload files to the corporate servers from their mobile phone when outside the office, but uploading files works without issue in the office. The user saw an error notification but dismissed it. Which of the following should a technician do to determine the root cause?
An administrator is investigating a technical outage. The management team wants information that includes the summary of the outage and actions taken. Which of the following documentation should the administrator provide to the management team?
A help desk technician is setting up speech recognition on a Windows system. Which of the following settings should the technician use?
A user reports getting a BSOD (Blue Screen of Death) error on their computer at least twice a day. Which of the following should the technician use to determine the cause?
Which of the following must be followed during incident response to ensure the collected evidence is properly handled and accounted for?
A technician is attempting to join a workstation to a domain but is receiving an error message stating the domain cannot be found. However, the technician is able to ping the server and access the internet. Given the following information:
IP Address – 192.168.1.210
Subnet Mask – 255.255.255.0
Gateway – 192.168.1.1
DNS1 – 8.8.8.8
DNS2 – 1.1.1.1
Server – 192.168.1.10
Which of the following should the technician do to fix the issue?
A user wants to dispose of a failed hard drive in a way that ensures the data is unrecoverable. Which of the following is the best at-home method?
A technician needs to provide remote support for a legacy Linux-based operating system from their Windows laptop. The solution needs to allow the technician to see what the user is doing and provide the ability to interact with the user's session. Which of the following remote access technologies would support the use case?