What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
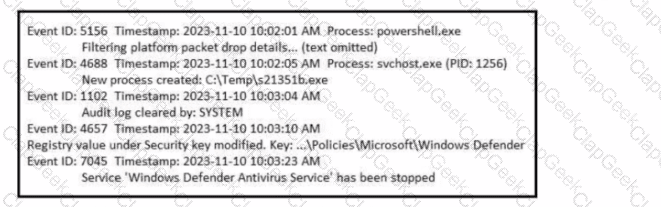
Refer to the exhibit. A SOC analyst is examining the Windows security logs of one of the endpoints. What is the possible reason for this event log?
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
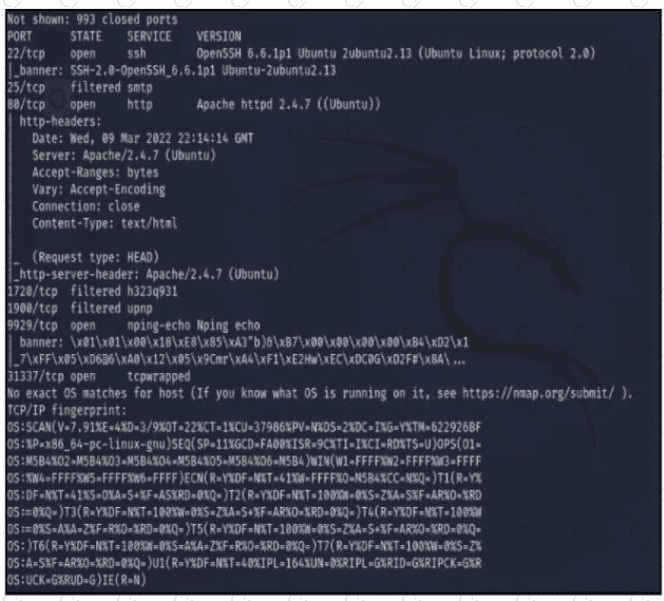
Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)
The SOC team detected an ongoing port scan. After investigation, the team concluded that the scan was targeting the company servers. According to the Cyber Kill Chain model, which step must be assigned to this type of event?
Which element is included in an incident response plan as stated m NIST SP800-617
What is a benefit of agent-based protection when compared to agentless protection?
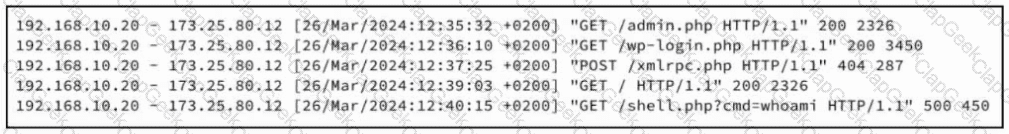
Refer to the exhibit. A security analyst examines Apache web server logs and notices the entries. Which security concern is occurring?
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
An employee received an email from a colleague’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender’s address. What does this incident describe?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
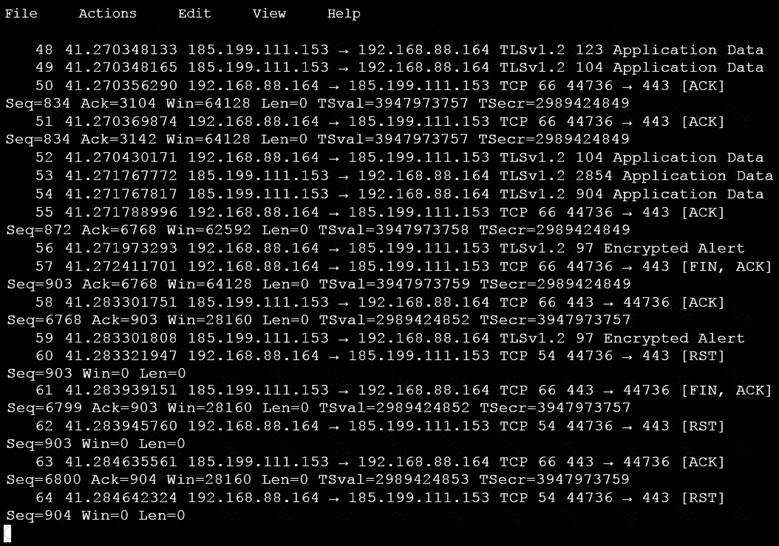
Which obfuscation technique is the attacker using?
Drag and drop the type of evidence from the left onto the description of that evidence on the right.

Which technology assures that the information transferred from point A to point B is unaltered and authentic?
An employee of a company receives an email with an attachment. They notice that this email is from a suspicious source, and they decide not to open the attached file. After further investigation, a security analyst concludes that this file is malware. To which category of the Cyber Kill Chain model does this event belong?
Refer to the exhibit
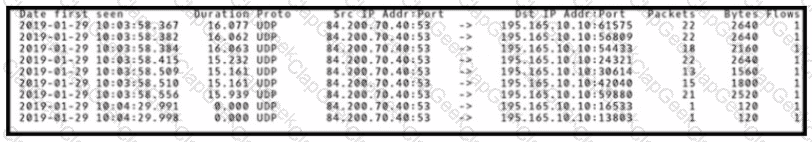
An engineer is analyzing DNS response packets that are larger than expected The engineer looks closer and notices a lack of appropriate DNS queries What is occurring?
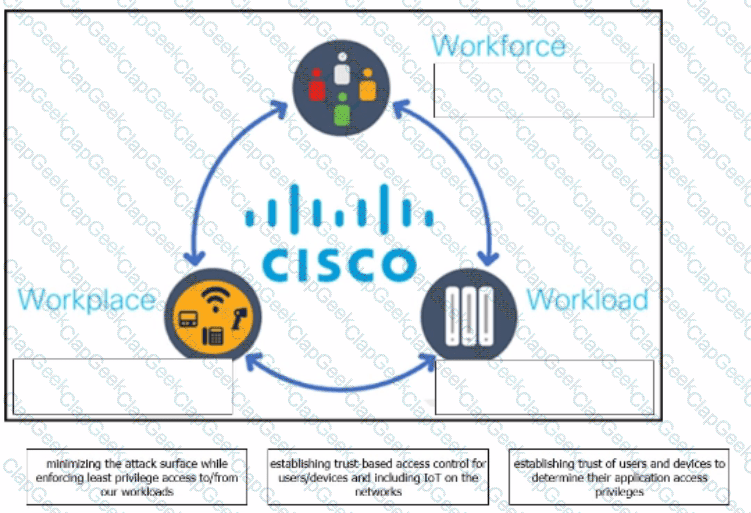
The Cisco Zero Trust Architecture simplifies the zero trust journey into three critical areas. Drag and drop the definitions onto the graphic to describe zero trust from the Cisco perspective.
Refer to the exhibit.
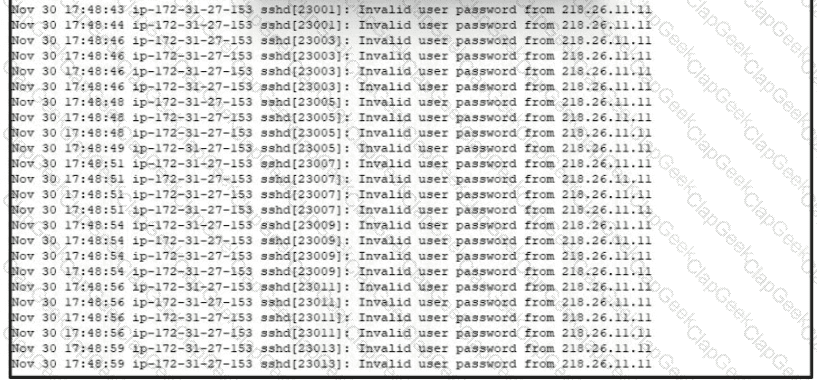
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
Refer to the exhibit.
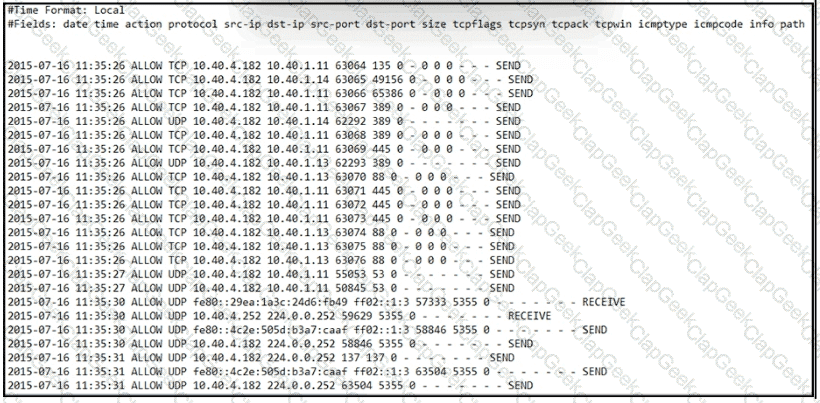
An engineer received an event log file to review. Which technology generated the log?
What technology should be used for the verified and secure exchange of public keys between entities Tom3350050239 and Dan0932353050?
At a company party a guest asks questions about the company’s user account format and password complexity. How is this type of conversation classified?
Which type of verification consists of using tools to compute the message digest of the original and copied data, then comparing the similarity of the digests?
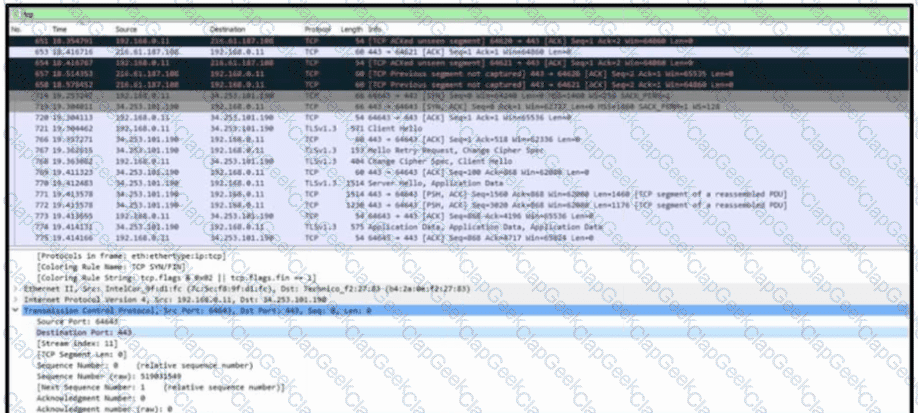
Refer to the exhibit. A communication issue exists between hosts 192.168.0.11 and 34.253.101.190. What is a description of the initial TCP connection?
What is a difference between inline traffic interrogation and traffic mirroring?
A SOC analyst detected connections to known C&C and port scanning activity to main HR database servers from one of the HR endpoints via Cisco StealthWatch. What are the two next steps of the SOC team according to the NISTSP800-61 incident handling process? (Choose two)
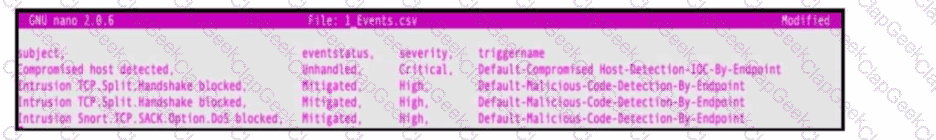
Refer to the exhibit. An engineer must map these events to the source technology that generated the event logs. To which technology do the generated logs belong?
A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
Which vulnerability type is used to read, write, or erase information from a database?
Refer to the exhibit.
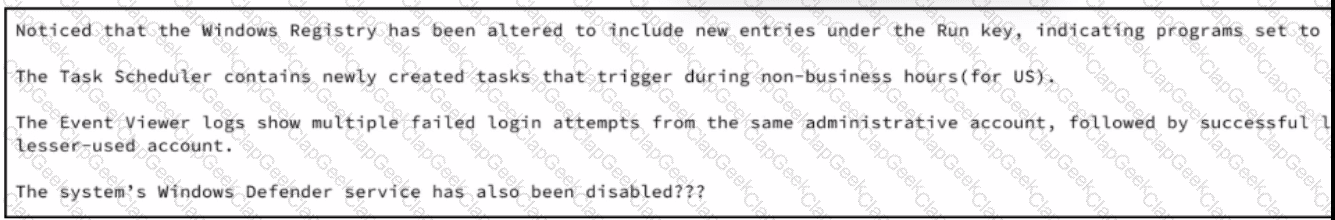
A security analyst wraps up the shift and passed open ticket notes to the night shift SOC team analyst. The ticket name in question is "Investigating suspicious activity on a Windows Server’’. Which operating system components must the analyst prioritize to uncover the attacker's persistence mechanisms?
What is the advantage of agent-based protection compared to agentless protection?
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
What are two differences and benefits of packet filtering, stateful firewalling, and deep packet inspections? (Choose two.)
What is a key difference between a tampered and an untampered disk image during a forensic investigation?
A compliance analyst receives a complaint from a customer regarding personal data being unlawfully retained despite a deletion request. The company is based in Europe and must comply with GDPR. The only data collected is the email address 0524l9i75@gmail.com. How should the compliance analyst act?
In digital communications, which method is recommended for securely exchanging public keys between users T0n2262144790 and D4n4126220794?
Which type of attack involves sending input commands to a web server to access data?
Refer to the exhibit.
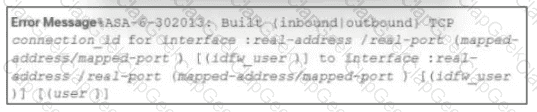
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
An analyst is investigating an incident in a SOC environment. Which method is used to identify a session from a group of logs?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
A vulnerability analyst is performing the monthly scan data review Output data is very big and getting bigger each month The analyst decides to create a more efficient process to complete the task on time All false positives and true positives are excluded from the results The remaining findings will be assigned to a technical team for further remediation What is the result of such activity?
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
Which technology on a host is used to isolate a running application from other applications?
An engineer received a ticket to investigate a potentially malicious file detected by a malware scanner that was trying to execute multiple commands. During the initial review, the engineer discovered that the file was created two days prior. Further analyses show that the file was downloaded from a known malicious domain after a successful phishing attempt on an asset owner. At which phase of the Cyber Kill Chain was this attack mitigated?
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
Which event artifact is used to identify HTTP GET requests for a specific file?
Which type of evidence supports a theory or an assumption that results from initial evidence?
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
An organization's security team detected network spikes coming from the internal network. An investigation concluded that the spike in traffic was from intensive network scanning. How must the analyst collect the traffic to isolate the suspicious host?
Which information must an organization use to understand the threats currently targeting the organization?
What is the practice of giving an employee access to only the resources needed to accomplish their job?
Which technique obtains information about how the system works without knowing it's design details?
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and dan1968754032?
Refer to the exhibit.
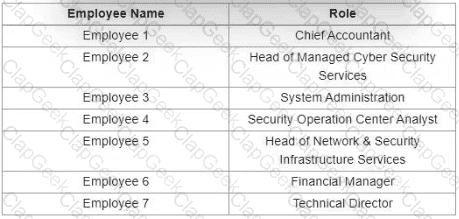
Which stakeholders must be involved when a company workstation is compromised?

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
Refer to the exhibit.
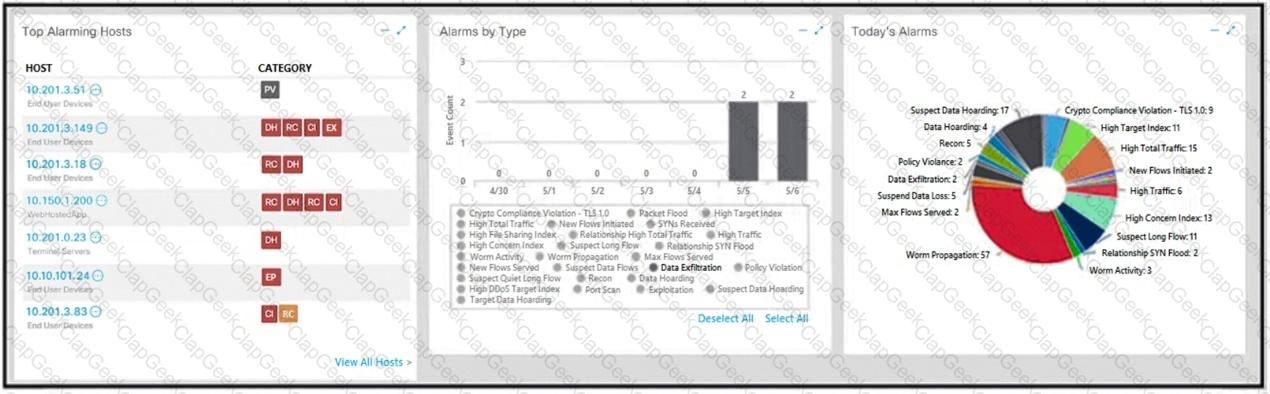
What is the potential threat identified in this Stealthwatch dashboard?
A security analyst received a ticket about suspicious traffic from one of the workstations. During the investigation, the analyst discovered that the workstation was communicating with an external IP. The analyst could not investigate further and escalated the case to a T2 security analyst. What are the two data visibility challenges that the security analyst should identify? (Choose two.)
A company recently encountered a breach. Critical services went through a disturbance and the integrity of the data was altered. An engineer is investigating the issue and searching through the logs in the SIEM. Which phase of the incident response is an engineer working on?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
What is the difference between deep packet inspection and stateful inspection?
An organization that develops high-end technology is going through an internal audit The organization uses two databases The main database stores patent information and a secondary database stores employee names and contact information A compliance team is asked to analyze the infrastructure and identify protected data Which two types of protected data should be identified? (Choose two)
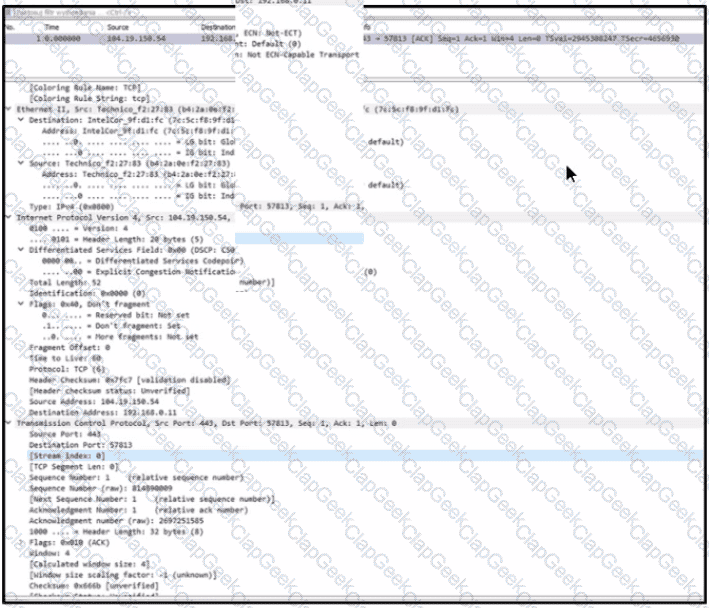
Refer to the exhibit. An engineer must use a 5-tuple approach to isolate a compromised host in a grouped set of logs.
Which data must the engineer use?
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
Refer to the exhibit.
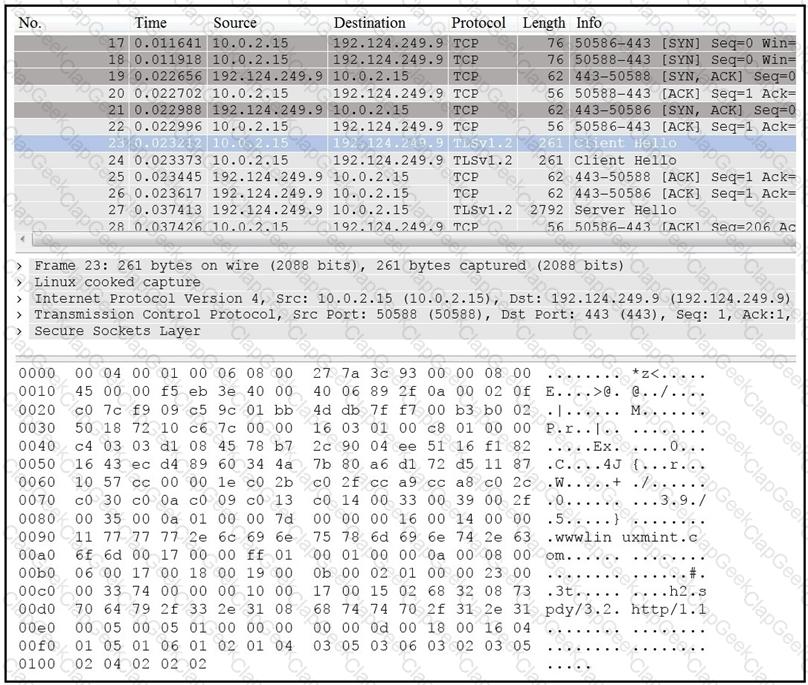
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Drag and drop the definitions from the left onto the phases on the right to classify intrusion events according to the Cyber Kill Chain model.
An engineer is working on the implementation of digital certificates for new cntical web applications One of the requirements is that the https connection must be validated and protected against malicious network impersonators The server will be exposed externally from the DMZ network Which certificate must be used?
Which security technology allows only a set of pre-approved applications to run on a system?
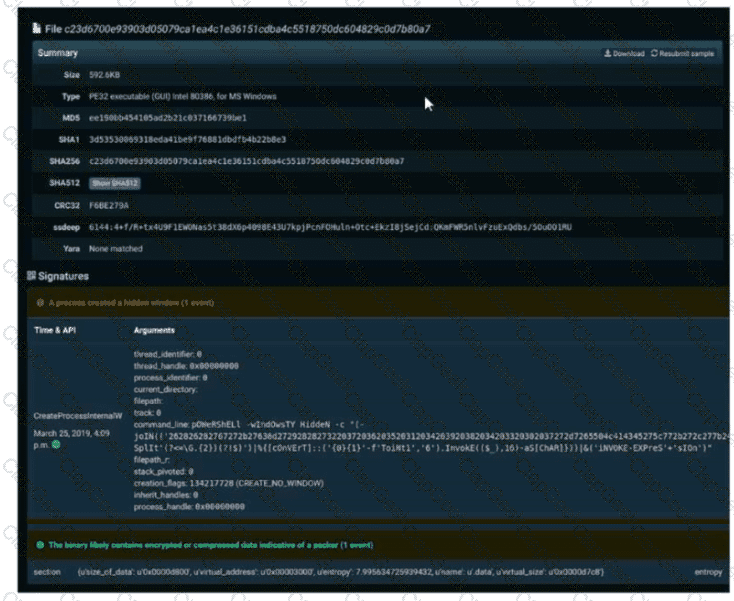
Refer to the exhibit. A SOC engineer is analyzing Cuckoo Sandbox report for a file that has been identified as suspicious by the endpoint security system. What is the state of the file?
Refer to the exhibit.
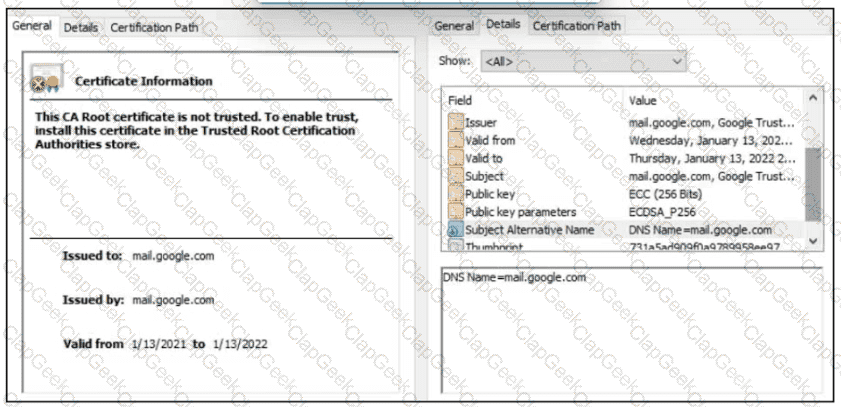
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
A company encountered a breach on its web servers using IIS 7 5 Dunng the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
An engineer must analyze a security event from last month. The engineer has access to a .pcap file collected via traffic mirroring and NetFlow data. The engineer must perform checks quickly on a busy network segment without prior knowledge of the incident details. Which source of data should be used for analysis?
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
A security analyst reviews the firewall and observes the large number of frequent events. The analyst starts the packet capture with the Wireshark and identifies that TCP port reuse was detected incorrectly as a TCP split-handshake attack by the firewall. How must an impact from this event be categorized?


