A Cortex XSIAM analyst in a SOC is reviewing an incident involving a workstation showing signs of a potential breach. The incident includes an alert from Cortex XDR Analytics Alert source "Remote service command execution from an uncommon source." As part of the incident handling process, the analyst must apply response actions to contain the threat effectively.
Which initial Cortex XDR agent response action should be taken to reduce attacker mobility on the network?
Two security analysts are collaborating on complex but similar incidents. The first analyst merges the two incidents into one for easier management. The other analyst immediately discovers that the custom incident field values relevant to the investigation are missing.
How can the team retrieve the missing details?
How would Incident Context be referenced in an alert War Room task or alert playbook task?
An analyst conducting a threat hunt needs to collect multiple files from various endpoints. The analyst begins the file retrieval process by using the Action Center, but upon review of the retrieved files, notices that the list is incomplete and missing files, including kernel files.
What could be the reason for the issue?
A security analyst is reviewing alerts and incidents associated with internal vulnerability scanning performed by the security operations team.
Which built-in incident domain will be assigned to these alerts and incidents in Cortex XSIAM?
An on-demand malware scan of a Windows workstation using the Cortex XDR agent is successful and detects three malicious files. An analyst attempts further investigation of the files by right-clicking on the scan result, selecting "Additional data," then "View related alerts," but no alerts are reported.
What is the reason for this outcome?
A Cortex XSIAM analyst is investigating a security incident involving a workstation after having deployed a Cortex XDR agent for 45 days. The incident details include the Cortex XDR Analytics Alert "Uncommon remote scheduled task creation." Which response will mitigate the threat?
Which Cytool command will re-enable protection on an endpoint that has Cortex XDR agent protection paused?
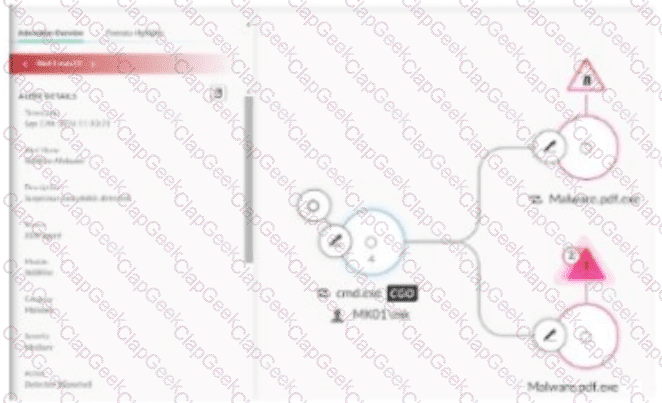
Based on the image below, which two determinations can be made from the causality chain? (Choose two.)
For a critical incident, Cortex XSIAM suggests several playbooks which should have been executed automatically.
Why were the playbooks not executed?


