You have a Microsoft 365 E5 subscription.
You need to create static retention policies for the following locations:
● Teams chats
● Exchange email
● SharePoint sites
● Microsoft 365 Groups
● Teams channel messages
What is the minimum number of retention policies required?
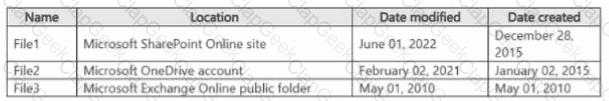
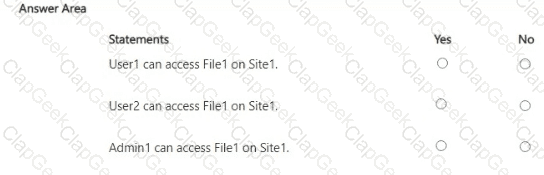
You have a Microsoft 365 E5 tenant that contains two users named User1, and User2 and a Microsoft SharePoint Online site named Site! as shown in the following exhibit.
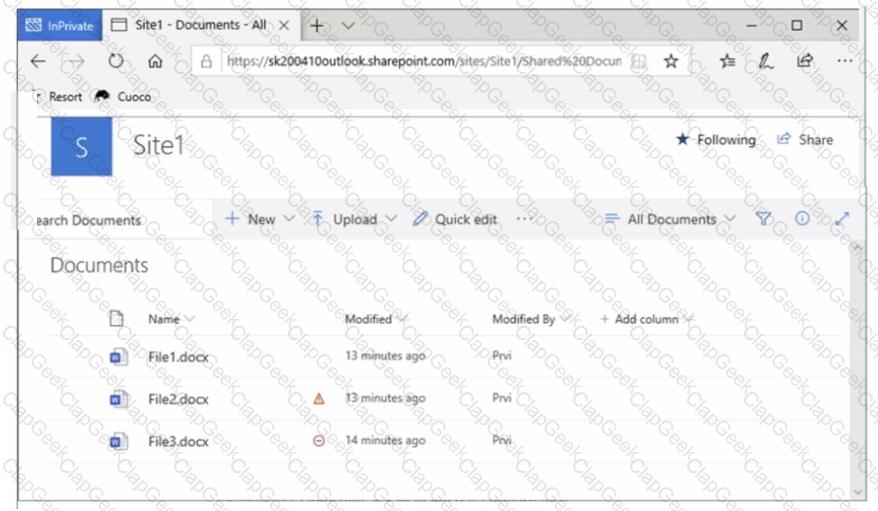
For Site1, the users are assigned the roles shown in the following table.
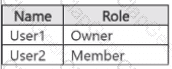
You publish a retention label named Retention1 to Site1.
To which files can the users apply Retention!? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to test Microsoft Purview Advanced Message Encryption capabilities for your company. The test must verify the following information:
• The acquired default template names
• The encryption and decryption verification status
Which PowerShell cmdlet should you run?
You have the files shown in the following table.
You configure a retention policy as shown >n the exhibit. (Click the Exhibit lab.)
The start of the retention period is based on when items are created. The current date is January 01. 207S.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

You have a Microsoft 365 E5 subscription.
You need to review a Microsoft 365 Copilot usage report.
From where should you review the report?
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and the users shown in the following table.
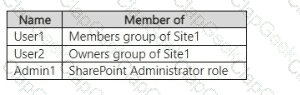
You have a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.
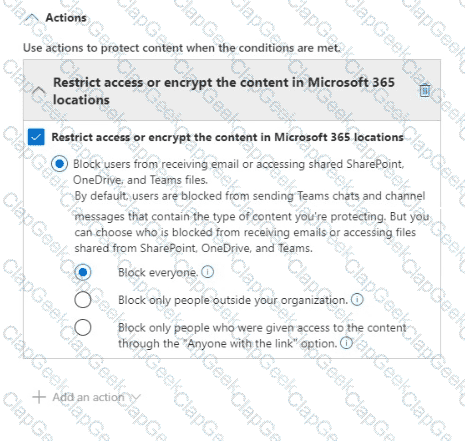
You apply DLP1 to Site1.
User1 uploads a file named File1 to Site1. File1 does NOT match any of the DLP1 rules. User2 updates File1 to contain data that matches the DLP1 rules.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You create a sensitivity label named Label1 and publish Label1 to all users and groups.
You have the following files in a SharePoint site:
• File1.doc
• File2.docx
• File3.xlsx
• File4.txt
You need to identify which files can have Label1 applied.
Which files should you identify?
You are creating a data loss prevention (DLP) policy that will apply to all available locations except Fabric and Power BI workspaces.
You configure an advanced DLP rule in the policy.
Which type of condition can you use in the rule?
You have a Microsoft 36S ES subscription.
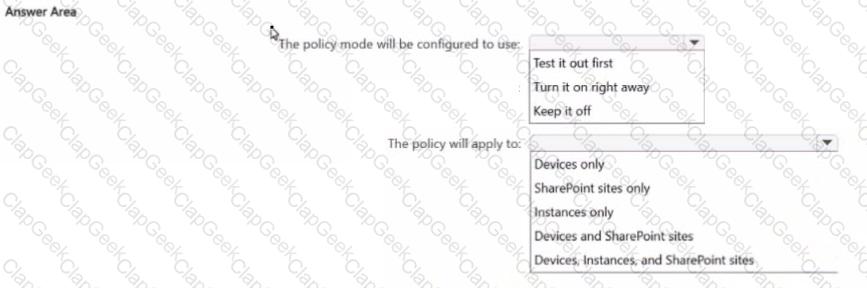
From the Microsoft Purview Data Security Posture Management for Al portal, you review the recommendations for Al data security
You plan to create a one-click policy to block elevated risk users from pasting or uploading sensitive data to Al websites
How will the policy be configured? To answer, select the appropriate options in the answer area
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage Account keys in plain text to third parties.
You need to ensure that when Azure Storage Account keys are emailed, the emails are encrypted.
Solution: You create a data loss prevention (DLP) policy that has only the Exchange email location selected.
Does this meet the goal?
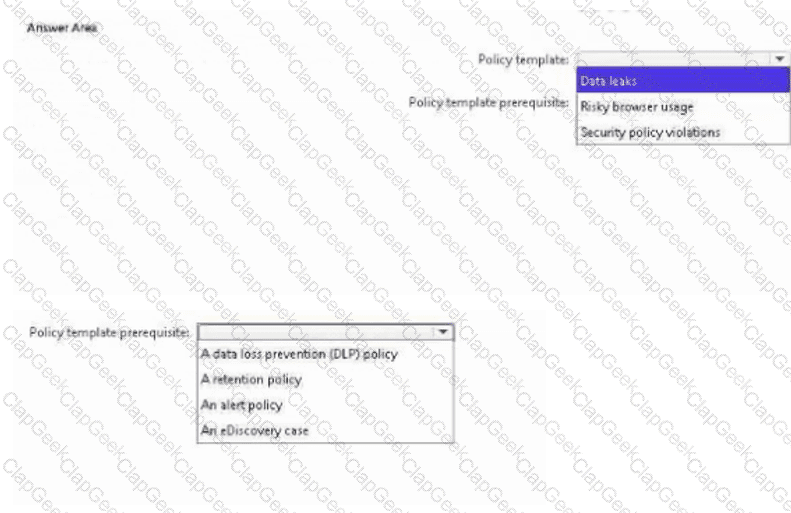
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You need to deploy a compliance solution that will detect the accidental oversharing of information outside of an organization.
The solution must minimize administrative effort.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
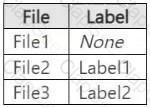
You have a Microsoft 365 E5 subscription that contains three DOCX files named File1, File2, and File3.
You create the sensitivity labels shown in the following table.

You apply the labels to the files as shown in the following table.
You ask Microsoft 365 Copilot to summarize the files, and you receive the results shown in the following table.
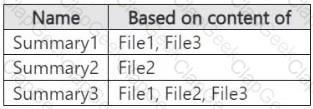
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft SharePoint Online site named Site1 that has the users shown in the following table.
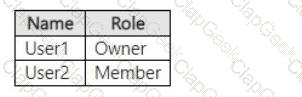
You create the retention labels shown in the following table.
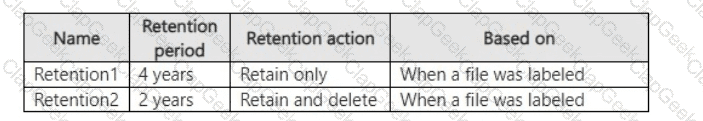
You publish the retention labels to Site1.
On March 1,2023, you assign the retention labels to the files shown in the following table.
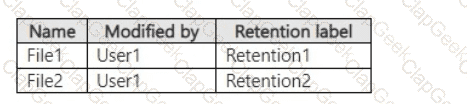
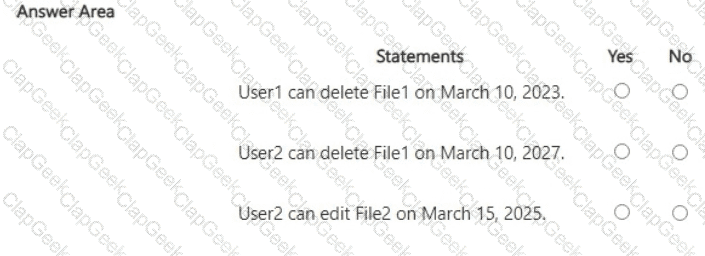
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
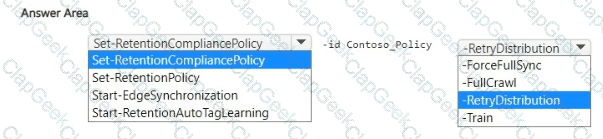
You create a retention label policy named Contoso_Policy that contains the following labels:
• 10 years then delete
• 5 years then delete
• Do not retain
Contoso.Policy is applied to content in Microsoft SharePoint Online sites.
After a couple of days, you discover the following messages on the Properties page of the label policy:
• Status: Off (Error)
• It's taking longer than expected to deploy the policy
You need to reinitiate the policy.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have Microsoft 365 E5 subscription that uses data loss prevention (DLP) to protect sensitive information.
You have a document named Form.docx.
You plan to use PowerShell to create a document fingerprint based on Form.docx.
You need to first connect to the subscription.
Which cmdlet should you run?
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You need ensure that an incident will be generated when a user visits a phishing website.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft J65 E5 subscription. You plan to implement retention policies for Microsoft Teams. Which item types can be retained?
You have a Microsoft 365 subscription that contains two Microsoft SharePoint Online sites named Site1 and Site2. You plan to use policies to meet the following requirements:
• Add a watermark of Confidential to a document if the document contains the words Project1 or Project2.
• Retain a document for seven years if the document contains credit card information.
• Add a watermark of Internal Use Only to all the documents stored on Site2.
• Add a watermark of Confidential to all the documents stored on Site1.
You need to recommend the minimum number of sensitive info types required.
How many sensitive info types should you recommend?
You have a Microsoft SharePoint Online site named Site1 that contains a document library. The library contains more than 1,000 documents. Some of the documents are job applicant resumes. All the documents are in the English language.
You plan to apply a sensitivity label automatically to any document identified as a resume. Only documents that contain work experience, education, and accomplishments must be labeled automatically.
You need to identify and categorize the resumes. The solution must minimize administrative effort.
What should you include in the solution?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true -AdminAuditLogCmdlets *Mailbox* command.
Does that meet the goal?
You have a Microsoft 365 E5 subscription that contains two users named User! and User2.
You need to implement insider risk management. The solution must meet the following requirements:
• Ensure that User1 can create insider risk management policies.
• Ensure that User2 can use content captured by using insider risk management policies
• Follow the principle of least privilege.
To which role group should you add each user? To answer, drag the appropriate role groups to the correct users. Each role group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

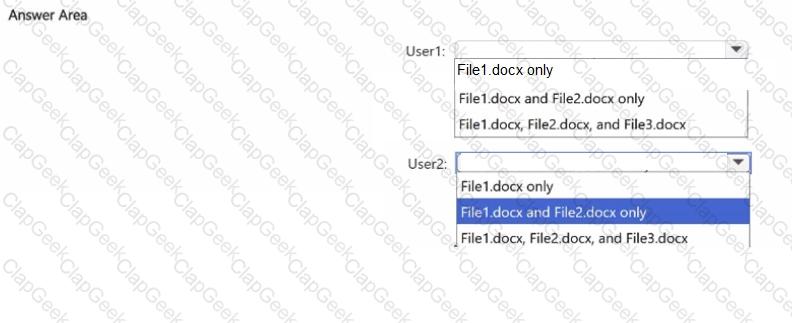
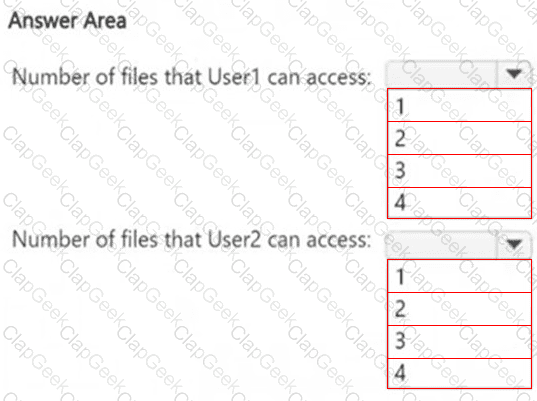
HOTSPOT
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?
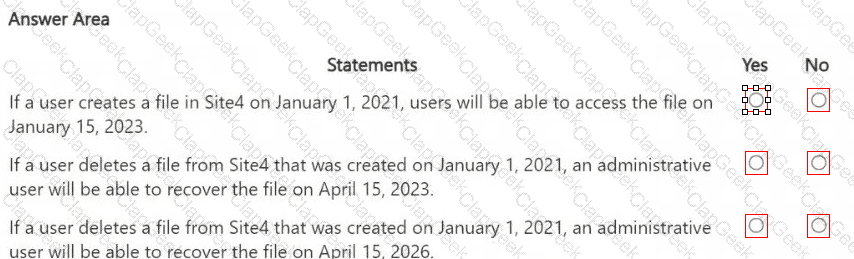
HOTSPOT
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
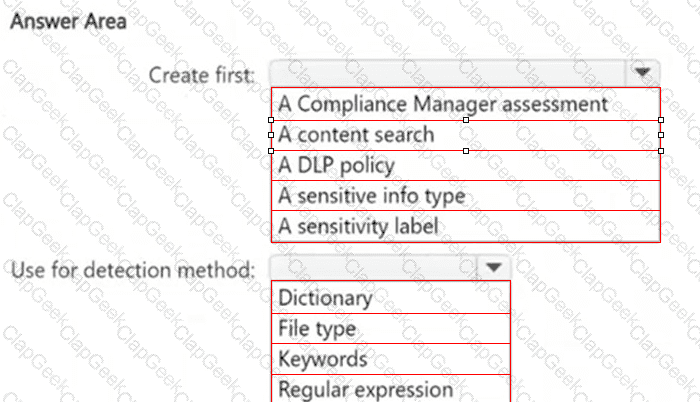
HOTSPOT
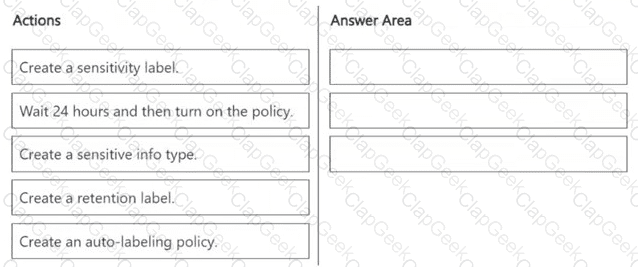
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the retention requirement for the users' Microsoft 365 data.
What is the minimum number of retention policies required to achieve the goal?
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.