Which action would an administrator take to ensure that a service object will be available only to the selected device group?
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
Starting with PAN-OS version 9.1, application dependency information is now reported in which two locations? (Choose two.)
An administrator should filter NGFW traffic logs by which attribute column to determine if the entry is for the start or end of the session?
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choices to block the sameURL then which choice would be the last to block access to the URL?
Which action results in the firewall blocking network traffic with out notifying the sender?
Which feature would be useful for preventing traffic from hosting providers that place few restrictions on content, whose services are frequently used by attackers to distribute illegal or unethical material?
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
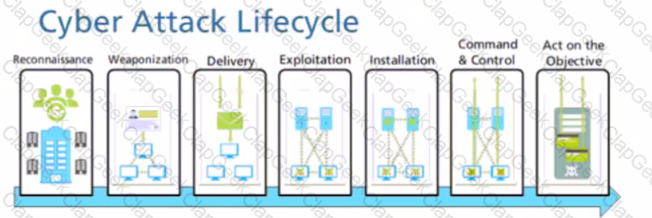
Given the cyber-attack lifecycle diagram identify the stage in which the attacker can run malicious code against a vulnerability in a targeted machine.
Which Security policy action will message a user's browser that their web session has been terminated?
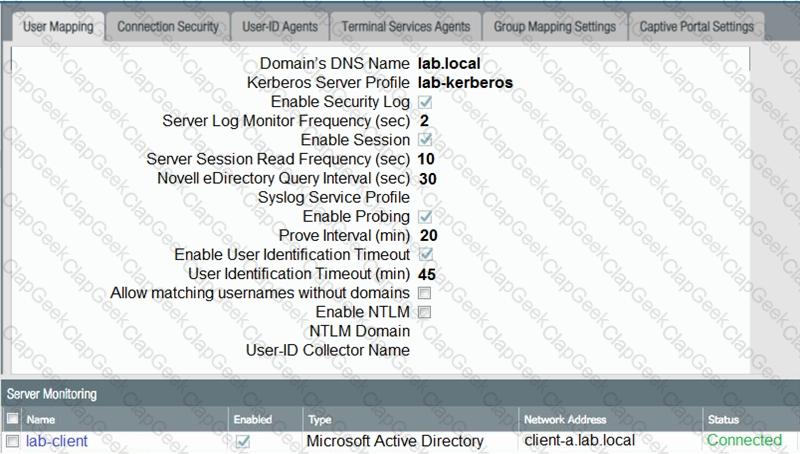
Based on the graphic which statement accurately describes the output shown in the server monitoring panel?
What are three differences between security policies and security profiles? (Choose three.)
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
Which type security policy rule would match traffic flowing between the inside zone and outside zone within the inside zone and within the outside zone?
Which Security profile can you apply to protect against malware such as worms and Trojans?
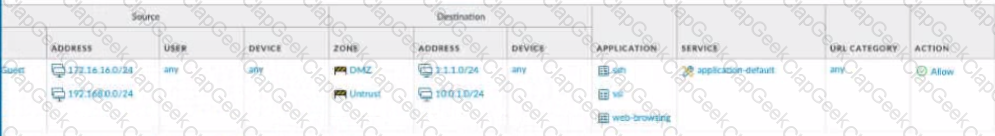
View the diagram.
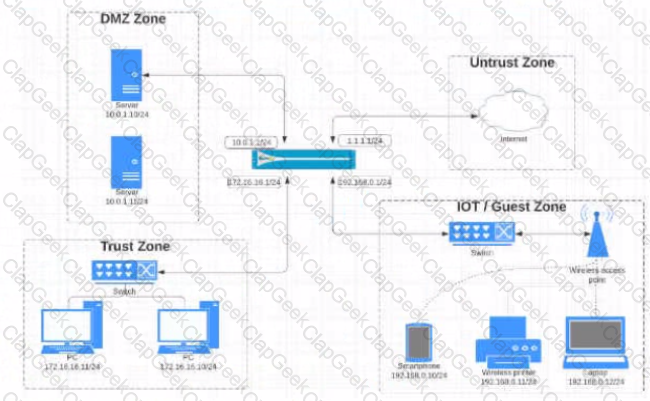
What is the most restrictive yet fully functional rule to allow general Internet and SSH traffic into both the DMZ and Untrust/lnternet zones from each of the lOT/Guest and Trust Zones?
A)
B)
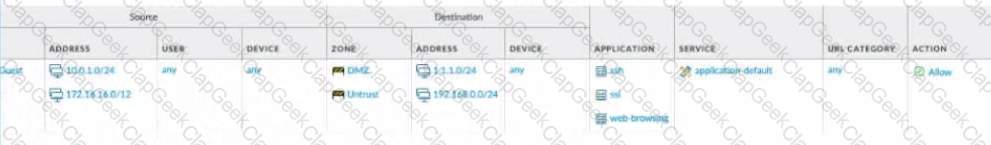
C)
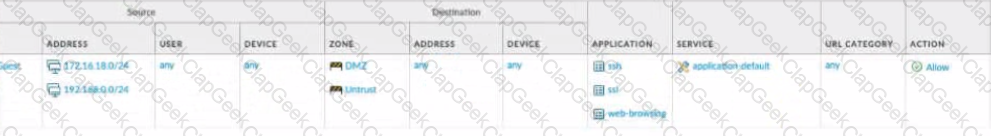
D)
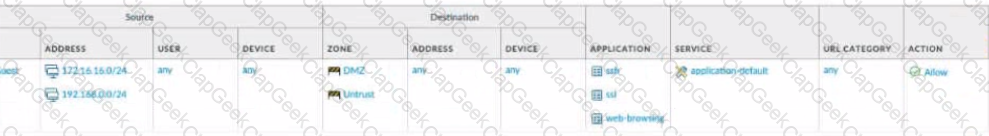
What can be achieved by disabling the Share Unused Address and Service Objects with Devices setting on Panorama?
An administrator would like to create a URL Filtering log entry when users browse to any gambling website. What combination of Security policy and Security profile actions is correct?
Starting with PAN_OS version 9.1 which new type of object is supported for use within the user field of a security policy rule?
Your company occupies one floor in a single building you have two active directory domain controllers on a single networks the firewall s management plane is only slightly utilized.
Which user-ID agent sufficient in your network?
What does an administrator use to validate whether a session is matching an expected NAT policy?
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base.
On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days.
Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
An administrator manages a network with 300 addresses that require translation. The administrator configured NAT with an address pool of 240 addresses and found that connections from addresses that needed new translations were being dropped.
Which type of NAT was configured?
Which Security profile should be applied in order to protect against illegal code execution?
Which three interface deployment methods can be used to block traffic flowing through the Palo Alto Networks firewall? (Choose three.)
An administrator would like to see the traffic that matches the interzone-default rule in the traffic logs.
What is the correct process to enable this logging1?
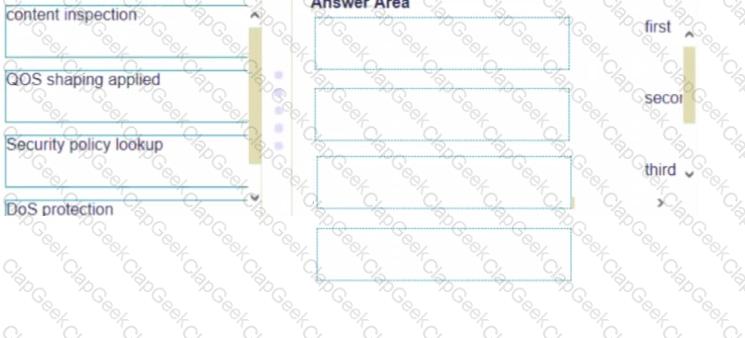
Place the following steps in the packet processing order of operations from first to last.
Which three statement describe the operation of Security Policy rules or Security Profiles? (Choose three)
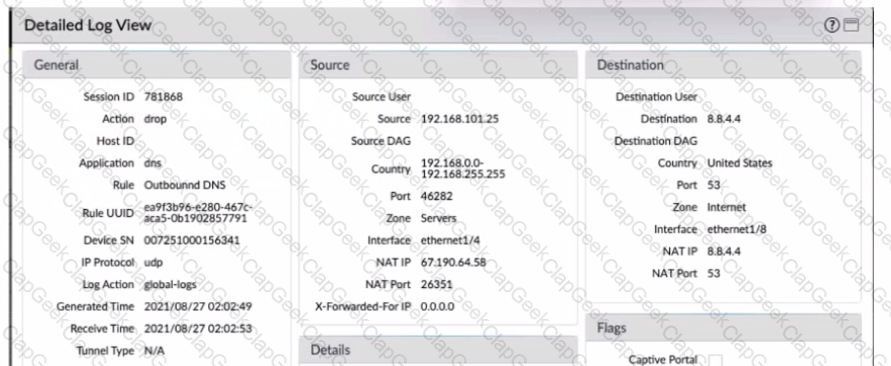
Given the detailed log information above, what was the result of the firewall traffic inspection?
A server-admin in the USERS-zone requires SSH-access to all possible servers in all current and future Public Cloud environments. All other required connections have already been enabled between the USERS- and the OUTSIDE-zone. What configuration-changes should the Firewall-admin make?
Which license must an Administrator acquire prior to downloading Antivirus Updates for use with the firewall?
The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet The firewall is configured with two zones;
1. trust for internal networks
2. untrust to the internet
Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two )
Which file is used to save the running configuration with a Palo Alto Networks firewall?
Which action results in the firewall blocking network traffic without notifying the sender?
Complete the statement. A security profile can block or allow traffic____________
Which Palo Alto networks security operating platform service protects cloud-based application such as Dropbox and salesforce by monitoring permissions and shared and scanning files for Sensitive information?
Which two DNS policy actions in the anti-spyware security profile can prevent hacking attacks through DNS queries to malicious domains? (Choose two.)
Which Security policy match condition would an administrator use to block traffic from IP addresses on the Palo Alto Networks EDL of Known Malicious IP Addresses list?
URL categories can be used as match criteria on which two policy types? (Choose two.)
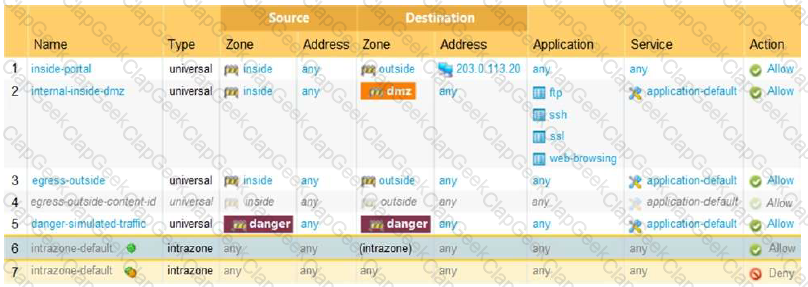
Based on the show security policy rule would match all FTP traffic from the inside zone to the outside zone?
Which three filter columns are available when setting up an Application Filter? (Choose three.)
Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic
Which statement accurately describes how the firewall will apply an action to matching traffic?
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
Which two types of profiles are needed to create an authentication sequence? (Choose two.)
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
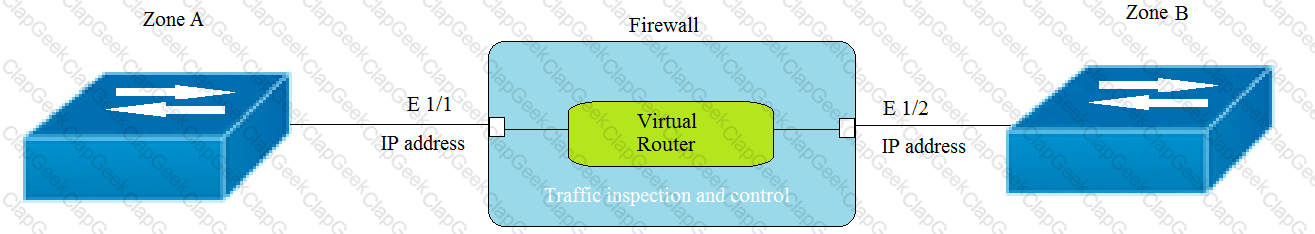
Given the topology, which zone type should zone A and zone B to be configured with?
Which System log severity level would be displayed as a result of a user password change?
An administrator creates a new Security policy rule to allow DNS traffic from the LAN to the DMZ zones. The administrator does not change the rule type from its default value.
What type of Security policy rule is created?
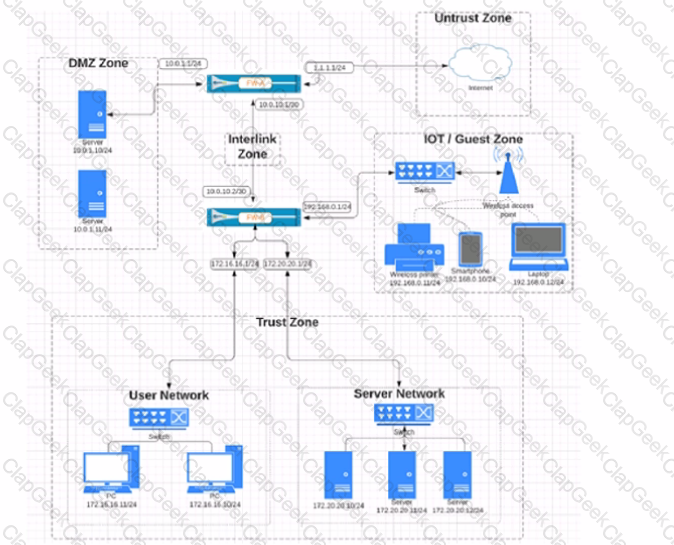
Based on the network diagram provided, which two statements apply to traffic between the User and Server networks? (Choose two.)
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
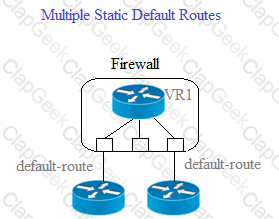
Given the scenario, which two statements are correct regarding multiple static default routes? (Choose two.)
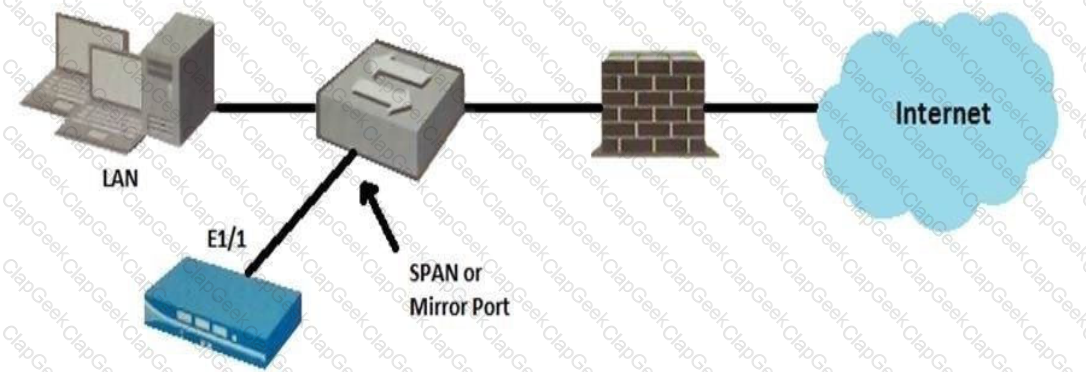
Given the topology, which zone type should you configure for firewall interface E1/1?
An administrator has an IP address range in the external dynamic list and wants to create an exception for one specific IP address in this address range.
Which steps should the administrator take?
Files are sent to the WildFire cloud service via the WildFire Analysis Profile. How are these files used?
Which administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact and command-and-control (C2) server.
Which security profile components will detect and prevent this threat after the firewall`s signature database has been updated?
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis Unit 42 research and data gathered from telemetry?
Which administrative management services can be configured to access a management interface?
Which URL Filtering profile action would you set to allow users the option to access a site only if they provide a URL admin password?
An administrator is troubleshooting traffic that should match the interzone-default rule. However, the administrator doesn't see this traffic in the traffic logs on the firewall. The interzone-default was never changed from its default configuration.
Why doesn't the administrator see the traffic?
Which option lists the attributes that are selectable when setting up an Application filters?
Which two components are utilized within the Single-Pass Parallel Processing architecture on a Palo Alto Networks Firewall? (Choose two.)
The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesn’t want to unblock the gambling URL category.
Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.)
An administrator wants to create a No-NAT rule to exempt a flow from the default NAT rule. What is the best way to do this?
An administrator is troubleshooting an issue with traffic that matches the intrazone-default rule, which is set to default configuration.
What should the administrator do?
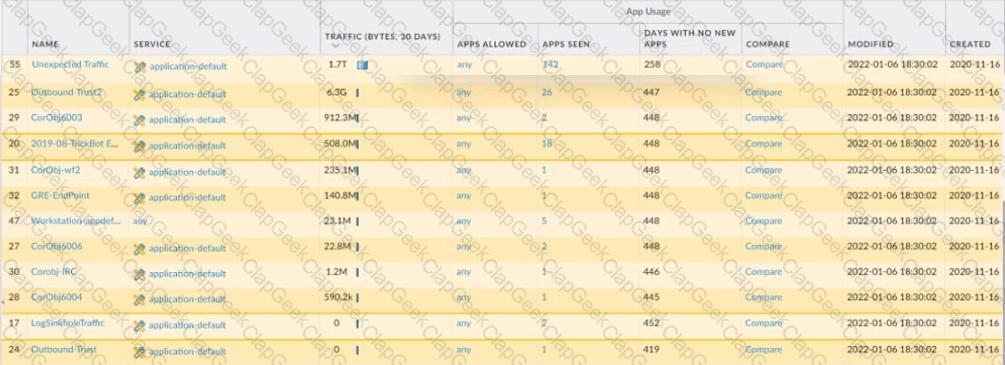
An administrator is updating Security policy to align with best practices.
Which Policy Optimizer feature is shown in the screenshot below?
An administrator would like to override the default deny action for a given application and instead would like to block the traffic and send the ICMP code "communication with the destination is administratively prohibited"
Which security policy action causes this?
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
Which DNS Query action is recommended for traffic that is allowed by Security policy and matches Palo Alto Networks Content DNS Signatures?
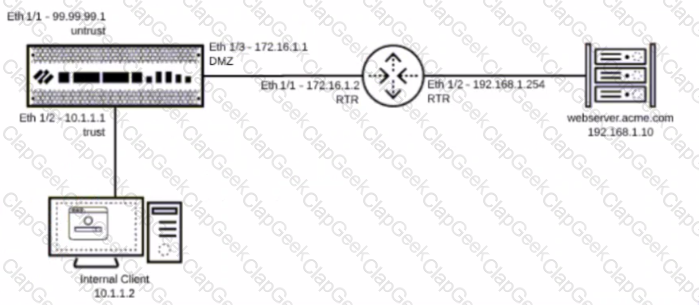
You have been tasked to configure access to a new web server located in the DMZ
Based on the diagram what configuration changes are required in the NGFW virtual router to route traffic from the 10 1 1 0/24 network to 192 168 1 0/24?
Which action related to App-ID updates will enable a security administrator to view the existing security policy rule that matches new application signatures?
An administrator is trying to enforce policy on some (but not all) of the entries in an external dynamic list. What is the maximum number of entries that they can be exclude?
Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall’s
data plane?
What action will inform end users when their access to Internet content is being restricted?
What must first be created on the firewall for SAML authentication to be configured?
Which Security policy action will message a user's browser thai their web session has been terminated?
An administrator needs to create a Security policy rule that matches DNS traffic within the LAN zone, and also needs to match DNS traffic within the DMZ zone The administrator does not want to allow traffic between the DMZ and LAN zones.
Which Security policy rule type should they use?
Which rule type is appropriate for matching traffic both within and between the source and destination zones?
What are three Palo Alto Networks best practices when implementing the DNS Security Service? (Choose three.)
Which two settings allow you to restrict access to the management interface? (Choose two )
A network has 10 domain controllers, multiple WAN links, and a network infrastructure with bandwidth needed to support mission-critical applications. Given the scenario, which type of User-ID agent is considered a best practice by Palo Alto Networks?


