A company has decided to expand NKP to features that require higher product tiers, like fleet-management and additional infrastructure providers. The company has already obtained the necessary licensing. Which action is required when adding and activating a license from NKP Starter to a higher-tier product?
A Platform Engineer needs to create an NKP custom image for vSphere.
Which option should the engineer use?
A company recently deployed NKP. A Platform Engineer was asked to attach the existing Amazon EKS. A workspace and project were created accordingly, and resource requirements were met. What does the engineer need to do first to prepare the EKS clusters?
NKP cluster nodes require a disk for some of its deployed components, outside of an application’s persistent volume requirements. What are these components and where are they deployed?
A Kubernetes administrator needs to deploy a new Kubernetes cluster into a new workspace. This cluster requires a predictive analytics solution that detects current and future anomalies. Which option does the administrator need to deploy after the cluster is ready?
A Platform Engineer is deploying NKP into a highly secure vSphere environment. The NKP cluster will be air-gapped, and must also be FIPS compliant. The OS platform to be used for NKP cluster nodes is RHEL.
What must the engineer do to properly prep an OS image and have it be deployed as a FIPS compliant NKP cluster node?
In an effort to control cloud cost consumption, auto-scale is configured to meet demands as needed.
What is the behavior for when nodes are scaled down?
A company has a new DevOps team that needs to be provided cloud native computing resources. This team will need to have access to multiple NKP clusters for development, testing and validation of an in-house application. However, they also need to be restricted to a specific namespace and a consistent level of access across the clusters within this namespace so that they do not adversely impact the environment of other user groups or the clusters themselves.
As a part of this consideration, the new team also needs to be limited to the amount of storage, CPU and memory they can consume on the clusters. A Platform Engineer has been tasked with providing the appropriate level of access to the team on these multiple NKP clusters.
How should the engineer best accomplish this task?
A company has been modernizing on cloud-native platforms for the past few years and has been running some small consumer support utilities on their production NKP cluster. After a thorough testing and QA cycle with simulated workloads on a development cluster, the company is ready to bring their online retail application into the fold. While they have sufficient system resources to scale the NKP cluster properly from a performance standpoint, they also want to ensure they properly scale their monitoring stack’s resource settings to retain a sufficient amount of data to see how overall system resource utilization trends for the NKP cluster over several months’ time with the added workloads. Which NKP Platform Application component should the company be most concerned with adjusting, and how should their Platform Engineer adjust it?
A Platform Engineer is deploying an NKP workload cluster using the nkp create cluster vsphere command. The cluster will be utilized by the company’s code-green team and the engineer has already created a code-green NKP workspace on the NKP management cluster.
After issuing the deploy command, the engineer monitored the build using the nkp describe cluster command and confirmed it completed successfully. However, a few hours later, after logging into the NKP UI, the engineer checked the code-green NKP workspace and saw that the NKP workload cluster was not there.
What is the likely reason the NKP workload cluster is not in the code-green NKP workspace?
Refer to the exhibits.
A Cloud Administrator had provisioned a Kubernetes cluster named demo that is no longer actively being used. A Quick review from the Systems Engineer confirms that the following VMs are part of the demo Kubernetes cluster
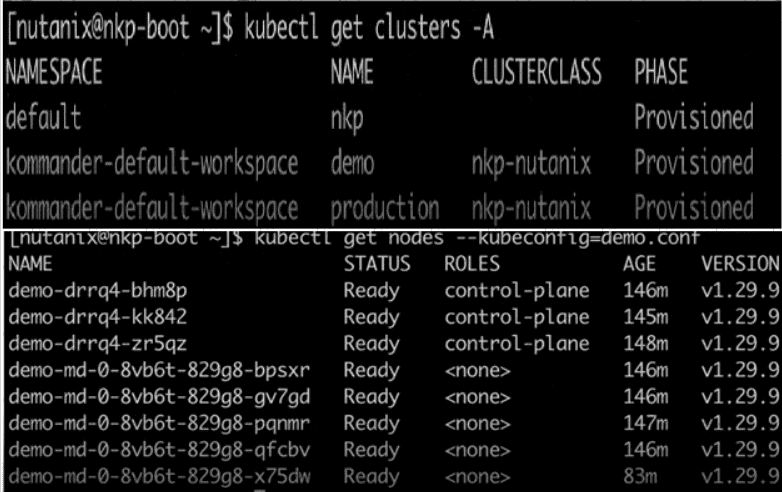
How should the demo cluster be properly deleted?
A Platform Engineer is deploying a new Kubernetes application in Amazon Web Services (AWS) Elastic Container Service for Kubernetes (EKS) and Azure Kubernetes Service (AKS). The engineer’s team has decided to use a custom image instead of the default images provided by AWS or Azure for their clusters. What functionality will the engineer lose in both AWS EKS and Azure AKS by choosing to use a custom image?
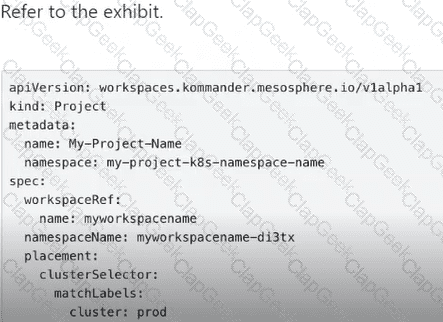
After creating the project, what should the administrator configure in order for the new software releases to automatically deploy to both environments?
A Platform Engineer has a requirement for backup and recovery and would like to leverage an Out-Of-The-Box solution distributed with NKP. What is the backup and recovery solution distributed for NKP?
A Platform Engineer has been tasked with backing up and restoring a production environment to ensure persistent data is available during a disaster at a primary site. What is recommended for backup and restore production use cases?
A dev team needed to optimize their logging system to be more robust, because the CPU and memory limits were insufficient, which caused delays in log collection and processing during times of high demand.
After a deep performance analysis, they decided to increase the CPU limits from 1 to 4 and the memory from 1000Mi to 4Gi.
Which ConfigMap should the development team run with custom resource requests and limit values for fluentd?
A company has enabled auto-scaling within an NKP cluster. What is the behavior for auto-scaling?
After a finished project, three Kubernetes clusters within a workspace were deleted, so the workspace is empty. Now a Platform Engineer needs to delete the workspace. How should the engineer delete the workspace in NKP?
A technology company has decided to migrate its infrastructure to NKP to improve the scalability and management of its applications. After a successful initial implementation, the operations team faces a new challenge of validating the HelmReleases to ensure that all applications are running correctly and avoid problems in production. Which command should the company execute to know the right status of their HelmReleases?
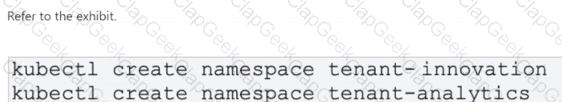
A DevOps team faces a growing challenge of managing logs from multiple applications in an NKP cluster. With several teams working on different projects, it is essential to implement a Multi-Tenant Logging system that allows each team to access their own logs securely and efficiently. Initially, two namespaces have been configured for each project, as shown in the exhibit. Then a ConfigMap has also been configured for each tenant, which contains the logging configuration. Which YAML output corresponds to a retention period of 30 days for tenant-innovation and seven days for tenant-analytics?
A company was using a test application called temp-shop developed in the temp-ecommerce NKP Starter cluster. Now, the cluster has just been taking up valuable resources that could be used for other projects, so the development team has decided to remove it.
Before proceeding, they verified that they had the cluster configuration file temp-ecommerce.conf.
What command should the development team execute to delete the cluster with its nodes and application?
A company uses an Artifactory private registry for development. The NKP deployment must use this private registry since the Security Administrator has the firewall configured to reject connections to public container registries. The first task is to push the NKP bundle to this private registry.
What options should be used to push the NKP bundle to this private registry?
A Platform Engineer is attaching existing Kubernetes clusters to NKP, but a particular Kubernetes Amazon EKS cluster is getting errors with application deployments. These errors are related to persistent volumes. What could be the issue, and what can the engineer do?
Recently, the reliability of some developer platforms has been impacted by out-of-memory errors, causing pods to crash and then remain in a pending state. A Cloud Engineer has been tasked with collecting and reviewing centralized metrics across the various platform environments to identify differences between them and better understand what is causing these performance issues. What should the engineer do to address this request?
A Platform Engineer is deploying an NKP cluster within an air-gapped AWS environment. However, after an infrastructure planning session with the network team, it’s been determined that the default CIDR block range that is used by pods on NKP clusters is already in use in their environment.
How can the engineer ensure there are no collisions between NKP pod traffic and the existing network using that subnet range?
A Platform Engineer is deploying a new NKP cluster that has internet connectivity. Now, a Cloud Administrator and Security Administrator are discussing the security of communications between the NKP Kubernetes cluster and the container registry. The engineer proposes to have an on-prem private registry.
What is the most significant reason that the engineer should create a private registry instead of configuring a secure connection between the NKP cluster and Github (SaaS)?
When deploying an NKP cluster onto air-gapped, pre-provisioned servers, Konvoy Image Builder is utilized to prepare the servers to become NKP cluster nodes.
What does the konvoy-image upload command do as a part of this preparation process?
A development team is working on a new application that requires access to certain cluster resources. The team needs to ensure that they have limited permissions to avoid unauthorized changes in other environments. Among the tasks they will perform are the following:
Deploy new versions of the application to their specific namespace.
Scale deployments according to demand.
View logs and metrics of their applications to monitor performance.When using the NKP GUI, what type of access should the team configure?


