You are asked to download and install the IPS signature database to a device operating in chassis cluster mode. Which statement is correct in this scenario?
Exhibit
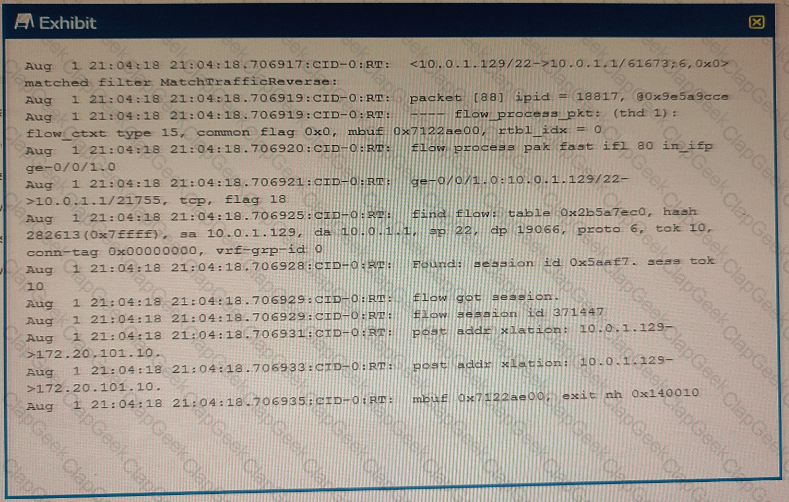
You are using trace options to verity NAT session information on your SRX Series device
Referring to the exhibit, which two statements are correct? (Choose two.)
What are two important function of the Juniper Networks ATP appliance solution? (Choose two.).
You must implement an IPsec VPN on an SRX Series device using PKI certificates for authentication. As part of the implementation, you are required to ensure that the certificate submission, renewal, and retrieval processes are handled
automatically from the certificate authority.
In this scenario, which statement is correct.
Exhibit
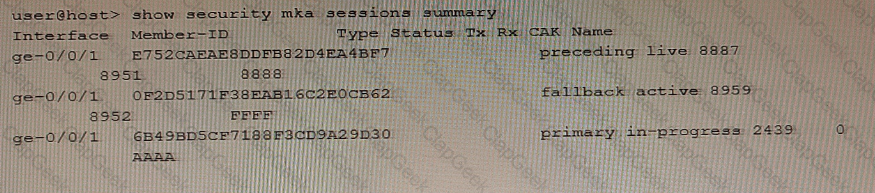
Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
You are asked to configure a security policy on the SRX Series device. After committing the policy, you receive the “Policy is out of sync between RE and PFE
Which command would be used to solve the problem?
Click the Exhibit button.
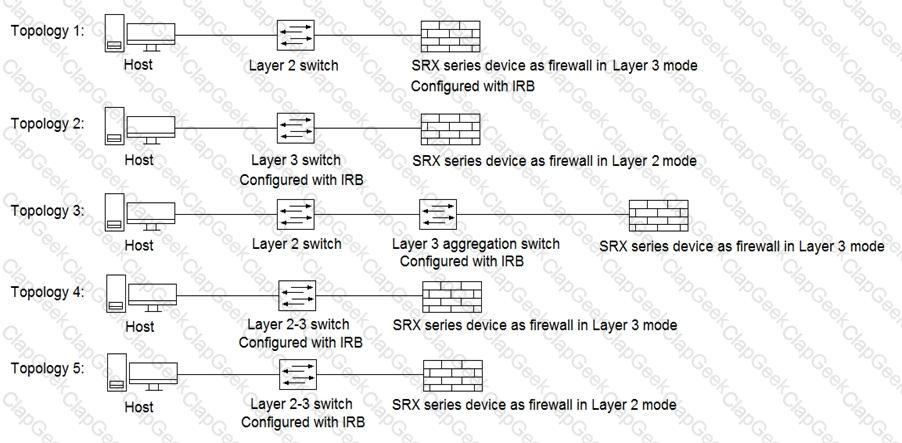
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
you must create a secure fabric in your company’s network
In this Scenario, Which three statements are correct? (Choose Three)
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)
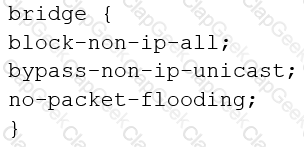
B)
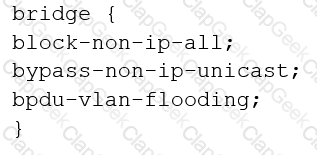
C)
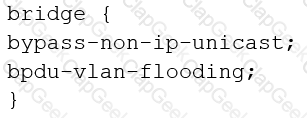
D)
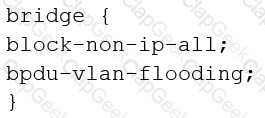
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)
You are asked to share threat intelligence from your environment with third party tools so that those
tools can be identify and block lateral threat propagation from compromised hosts.
Which two steps accomplish this goal? (Choose Two)
You have designed the firewall filter shown in the exhibit to limit SSH control traffic to yours SRX Series device without affecting other traffic.
Which two statement are true in this scenario? (Choose two.)
Exhibit
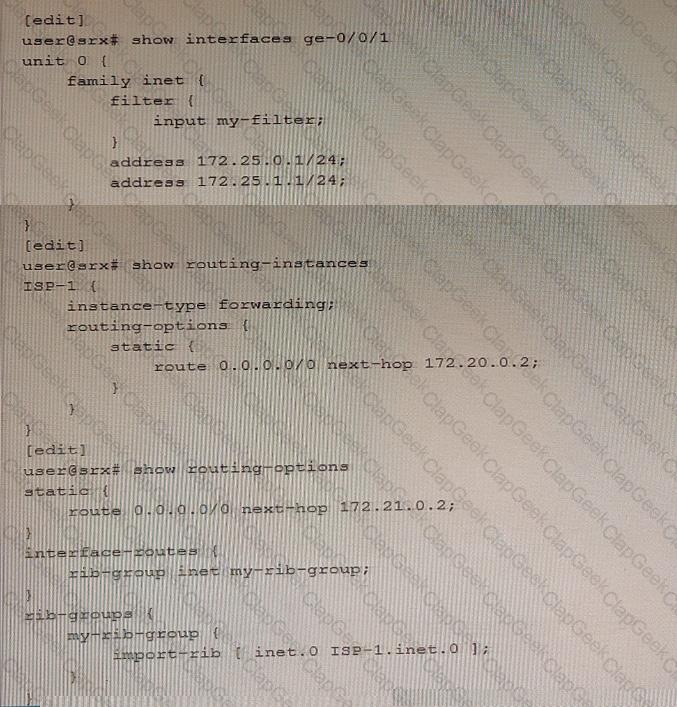
You are implementing filter-based forwarding to send traffic from the 172.25.0.0/24 network through ISP-1 while sending all other traffic through your connection to ISP-2. Your ge-0/0/1 interface connects to two networks, including the 172.25.0.0/24 network. You have implemented the configuration shown in the exhibit. The traffic from the 172.25.0.0/24 network is being forwarded as expected to 172.20.0.2, however traffic from the other network (172.25.1.0/24) is not being forwarded to the upstream 172.21.0.2 neighbor.
In this scenario, which action will solve this problem?
Exhibit.
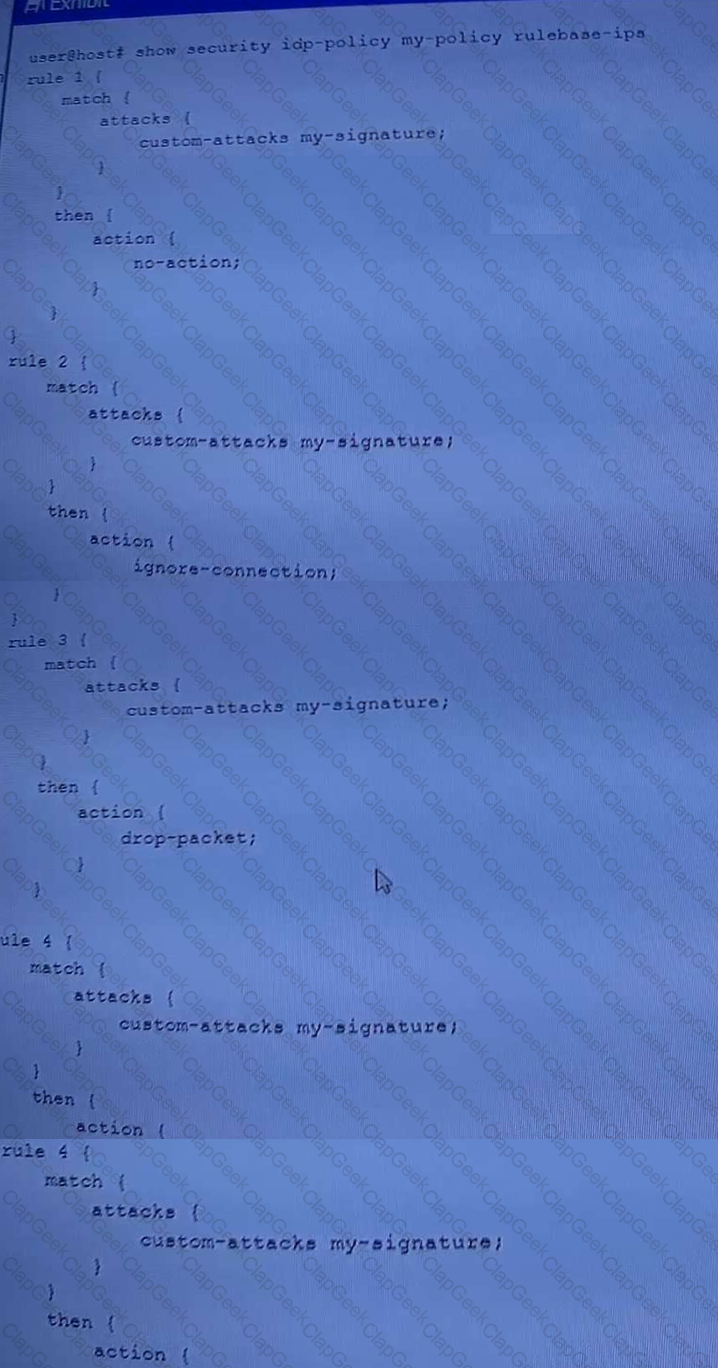
A hub member of an ADVPN is not functioning correctly.
Referring the exhibit, which action should you take to solve the problem?
You want to enforce I DP policies on HTTP traffic.
In this scenario, which two actions must be performed on your SRX Series device? (Choose two )
Which two types of source NAT translations are supported in this scenario? (Choose two.)
Which two features would be used for DNS doctoring on an SRX Series firewall? (Choose two.)
Which method does an SRX Series device in transparent mode use to learn about unknown devices in a network?
You are asked to provide single sign-on (SSO) to Juniper ATP Cloud. Which two steps accomplish this goal? (Choose two.)
Exhibit
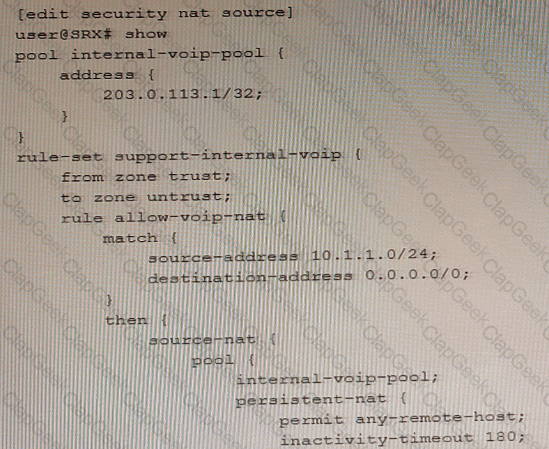
Referring to the exhibit, an internal host is sending traffic to an Internet host using the 203.0.113.1 reflexive address with source port 54311.
Which statement is correct in this situation?
Exhibit:

You are troubleshooting a firewall filter shown in the exhibit that is intended to log all traffic and block
only inbound telnet traffic on interface ge-0/0/3.
How should you modify the configuration to fulfill the requirements?
Refer to the exhibit,
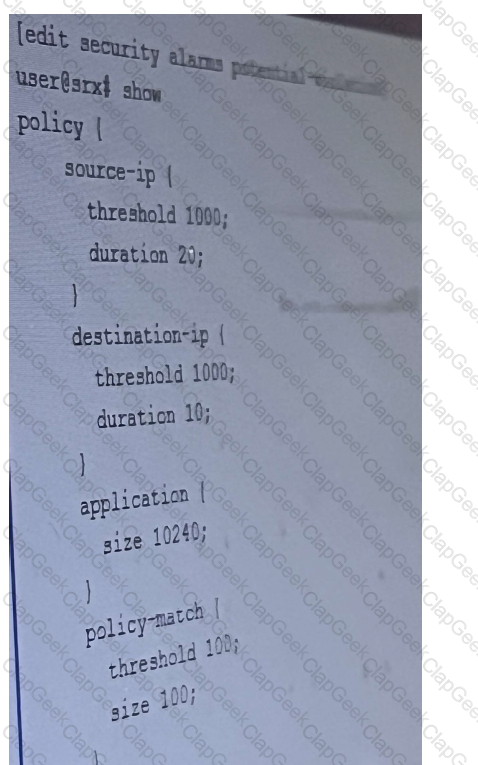
which two potential violations will generate alarm ? (Choose Two)
You are connecting two remote sites to your corporate headquarters site; you must ensure that all traffic is secured and
only uses a single Phase 2 SA for both sites.
In this scenario, which VPN should be used?
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
your company wants to take your juniper ATP appliance into private mode. You must give them a list
of impacted features for this request.
Which two features are impacted in this scenario? (Choose two)


