You want to deploy a virtualized SRX in your environment.
In this scenario, why would you use a vSRX instead of a cSRX? (Choose two.)
Which two statements about SRX Series device chassis clusters are correct? (Choose two.)
You want to be alerted if the wrong password is used more than three times on a single device within five minutes.
Which Juniper Networks solution will accomplish this task?
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Which two statements about SRX Series device chassis clusters are true? (Choose two.)
Click the Exhibit button.
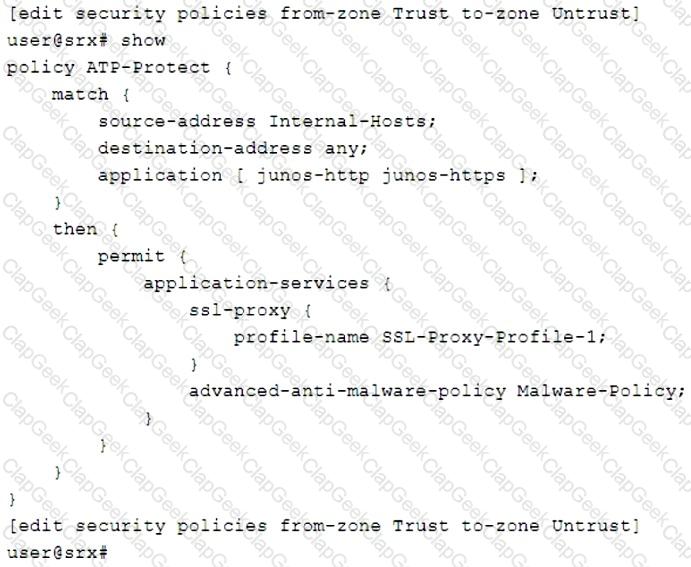
You are asked to create a security policy that will automatically add infected hosts to the infected hosts feed and block further communication through the SRX Series device.
What needs to be added to this configuration to complete this task?
Exhibit
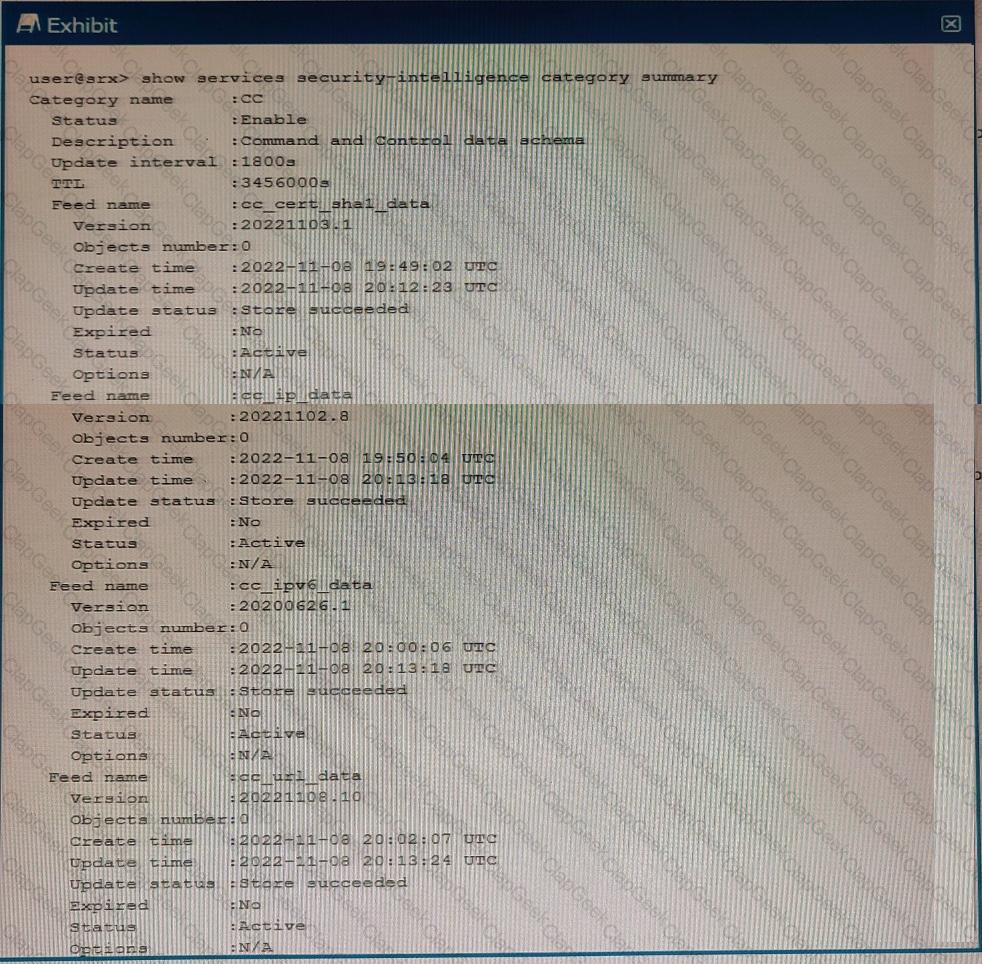
You just finished setting up your command-and-control (C&C) category with Juniper ATP Cloud. You notice that all of the feeds have zero objects in them.
Which statement is correct in this scenario?
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
Exhibit
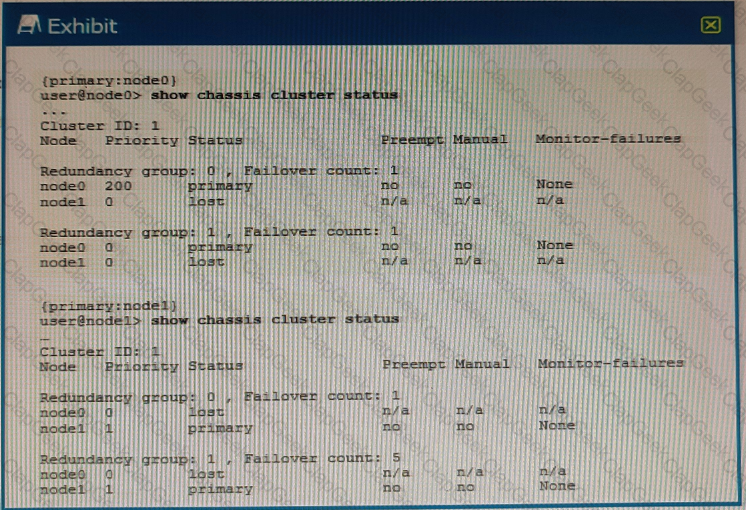
Referring to the exhibit, what do you determine about the status of the cluster.
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
Which solution enables you to create security policies that include user and group information?
Which two statements are correct about security policy changes when using the policy rematch feature? (Choose two.)
You are asked to determine how much traffic a popular gaming application is generating on your network.
Which action will you perform to accomplish this task?
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
You need to deploy an SRX Series device in your virtual environment.
In this scenario, what are two benefits of using a CSRX? (Choose two.)
You are asked to find systems running applications that increase the risks on your network. You must ensure these systems are processed through IPS and Juniper ATP Cloud for malware and virus protection.
Which Juniper Networks solution will accomplish this task?
Exhibit
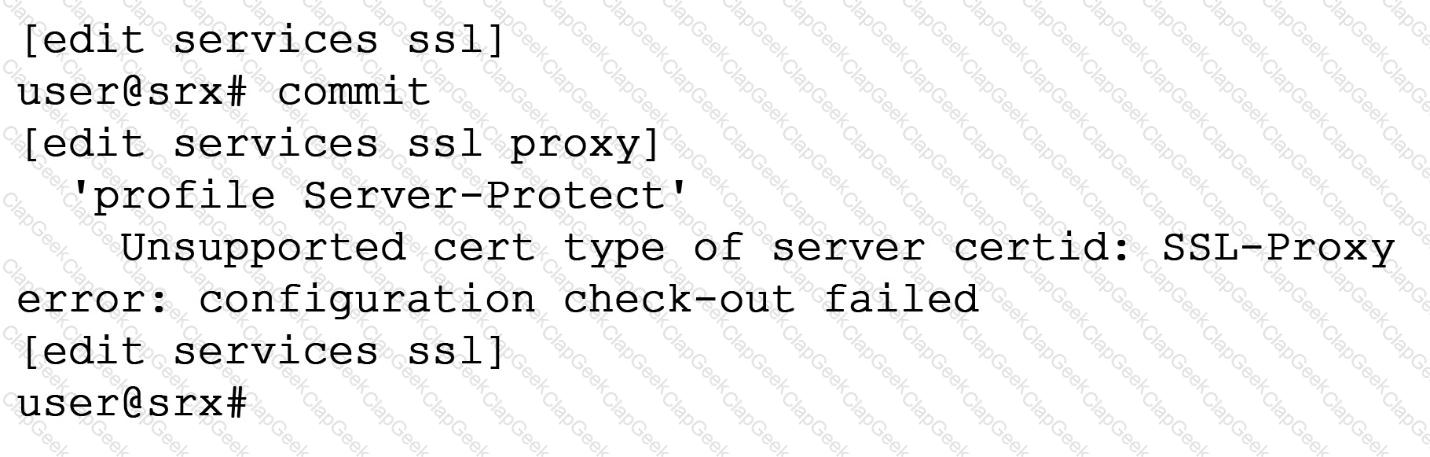
When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
You administer a JSA host and want to include a rule that sets a threshold for excessive firewall denies and sends an SNMP trap after receiving related syslog messages from an SRX Series firewall.
Which JSA rule type satisfies this requirement?
Click the Exhibit button.
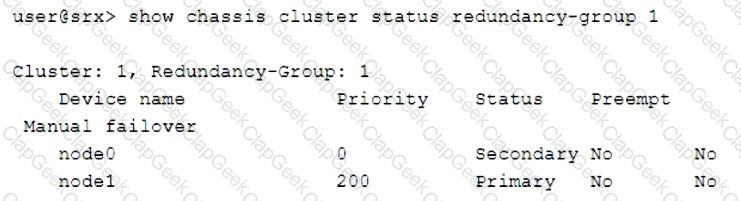
Which two statements describe the output shown in the exhibit? (Choose two.)
You have deployed an SRX300 Series device and determined that files have stopped being scanned.
In this scenario, what is a reason for this problem?


