Refer to the exhibit, which shows the current network topology.
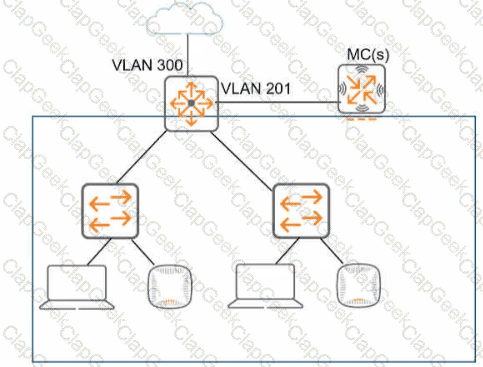
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the forwarding mode and Implements WPA3-Enterprise security
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
A company has Aruba Mobility Controllers (MCs). Aruba campus APs. and ArubaOS-CX switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type The ClearPass admins tell you that they want to run Network scans as part of the solution
What should you do to configure the infrastructure to support the scans?
A company has Aruba Mobility Controllers (MCs), Aruba campus APs, and ArubaOS-Switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type. This company is using only CPPM and no other ClearPass solutions.
The ClearPass admins tell you that they want to use HTTP User-Agent strings to help classify endpoints.
What should you do as a part of configuring the ArubaOS-Switches to support this requirement?
A company has an ArubaOS solution. The company wants to prevent users assigned to the "user_group1" role from using gaming and peer-to-peer applications.
What is the recommended approach for these requirements?
What is one method for HPE Aruba Networking ClearPass Policy Manager (CPPM) to use DHCP to classify an endpoint?
From which solution can ClearPass Policy Manager (CPPM) receive detailed information about client device type OS and status?
A company with 382 employees wants to deploy an open WLAN for guests. The company wants the experience to be as follows:

The company also wants to provide encryption for the network for devices mat are capable, you implement Tor the WLAN?
Which security options should
The monitoring admin has asked you to set up an AOS-CX switch to meet these criteria:
Send logs to a SIEM Syslog server at 10.4.13.15 at the standard TCP port (514)
Send a log for all events at the "warning" level or above; do not send logs with a lower level than "warning"The switch did not have any "logging" configuration on it. You then entered this command:AOS-CX(config)# logging 10.4.13.15 tcp vrf defaultWhat should you do to finish configuring to the requirements?
You have been instructed to look in the ArubaOS Security Dashboard's client list Your goal is to find clients mat belong to the company and have connected to devices that might belong to hackers
Which client fits this description?
Refer to the exhibit.
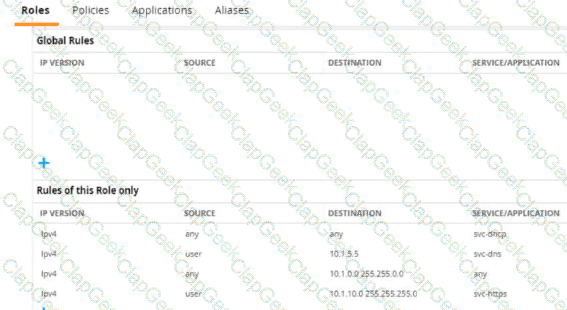
A diem is connected to an ArubaOS Mobility Controller. The exhibit snows all Tour firewall rules that apply to this diem
What correctly describes how the controller treats HTTPS packets to these two IP addresses, both of which are on the other side of the firewall
10.1 10.10
203.0.13.5
An AOS-CX switch currently has no device fingerprinting settings configured on it. You want the switch to start collecting DHCP and LLDP information. You enter these commands:
Switch(config)# client device-fingerprint profile myprofile
Switch(myprofile)# dhcp
Switch(myprofile)# lldp
What else must you do to allow the switch to collect information from clients?
What is one difference between EAP-Tunneled Layer security (EAP-TLS) and Protected EAP (PEAP)?
What is a benefit of Protected Management Frames (PMF). sometimes called Management Frame Protection (MFP)?
Two wireless clients, client 1 and client 2, are connected to an ArubaOS Mobility Controller. Subnet 10.1.10.10/24 is a network of servers on the other side of the ArubaOS firewall. The exhibit shows all three firewall rules that apply to these clients.
Which traffic is permitted?
You are troubleshooting an authentication issue for Aruba switches that enforce 802 IX10 a cluster of Aruba ClearPass Policy Manager (CPPMs) You know that CPPM Is receiving and processing the authentication requests because the Aruba switches are showing Access-Rejects in their statistics However, you cannot find the record tor the Access-Rejects in CPPM Access Tracker
What is something you can do to look for the records?
You need to implement a WPA3-Enterprise network that can also support WPA2-Enterprise clients. What is a valid configuration for the WPA3-Enterprise WLAN?
The first exhibit shows roles on the MC, listed in alphabetic order. The second and third exhibits show the configuration for a WLAN to which a client connects. Which description of the role assigned to a user under various circumstances is correct?
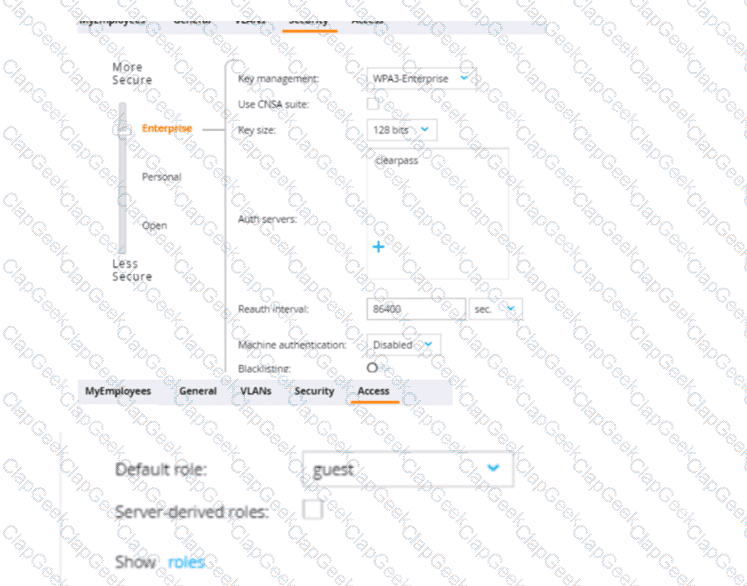
What is one way that Control Plane Security (CPSec) enhances security for the network?
A company is deploying AOS-CX switches to support 114 employees, which will tunnel client traffic to an HPE Aruba Networking Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the AOS-CX switches.
What are the licensing requirements for the MC?
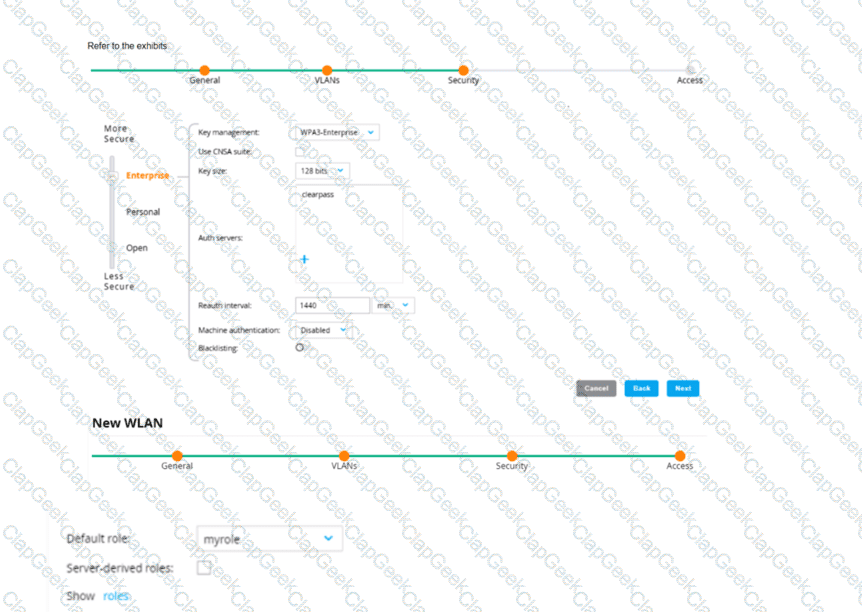
An admin has created a WLAN that uses the settings shown in the exhibits (and has not otherwise adjusted the settings in the AAA profile) A client connects to the WLAN Under which circumstances will a client receive the default role assignment?
You are managing an Aruba Mobility Controller (MC). What is a reason for adding a "Log Settings" definition in the ArubaOS Diagnostics > System > Log Settings page?
What is an Authorized client, as defined by AOS Wireless Intrusion Prevention System (WIP)?
Refer to the exhibit.
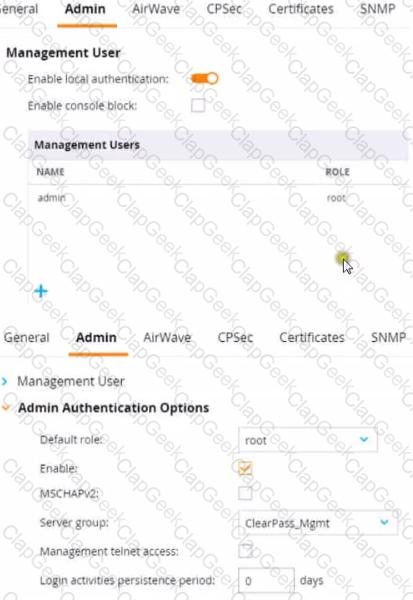
This Aruba Mobility Controller (MC) should authenticate managers who access the Web Ul to ClearPass Policy Manager (CPPM) ClearPass admins have asked you to use RADIUS and explained that the MC should accept managers' roles in Aruba-Admin-Role VSAs
Which setting should you change to follow Aruba best security practices?
A customer has an AOS-10 network infrastructure. The customer is looking for a solution that can classify many different types of devices, including IoT devices. Which solution should you explain can provide these capabilities?
Refer to the exhibit, which shows the settings on the company’s MCs.
— Mobility Controller
Dashboard General Admin AirWave CPSec Certificates
Configuration
WLANsv Control Plane Security
Roles & PoliciesEnable CP Sec
Access PointsEnable auto cert provisioning:
You have deployed about 100 new Aruba 335-APs. What is required for the APs to become managed?
What is one way that WPA3-Enterprise enhances security when compared to WPA2-Enterprise?
Refer to the exhibit.

A company has an HPE Aruba Networking Instant AP cluster. A Windows 10 client is attempting to connect to a WLAN that enforces WPA3-Enterprise with authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM is configured to require EAP-TLS. The client authentication fails. In the record for this client's authentication attempt on CPPM, you see this alert.
What is one thing that you check to resolve this issue?
Your HPE Aruba Networking Mobility Master-based solution has detected a rogue AP. Among other information, the AOS Detected Radios page lists this information for the AP:
SSID = PublicWiFi
BSSID = a8:bd:27:12:34:56
Match method = Plus one
Match method = Eth-Wired-Mac-Table
The security team asks you to explain why this AP is classified as a rogue. What should you explain?
What distinguishes a Distributed Denial of Service (DDoS) attack from a traditional Denial or service attack (DoS)?
A user attempts to connect to an SSID configured on an AOS-8 mobility architecture with Mobility Controllers (MCs) and APs. The SSID enforces WPA3-Enterprise security and uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as the authentication server. The WLAN has initial role, logon, and 802.1X default role, guest.
A user attempts to connect to the SSID, and CPPM sends an Access-Accept with an Aruba-User-Role VSA of "contractor," which exists on the MC.
What does the MC do?
What is one difference between EAP-Tunneled Layer Security (EAP-TLS) and Protected EAP (PEAP)?
What is one way that WPA3-PerSonal enhances security when compared to WPA2-Personal?
You have deployed a new Aruba Mobility Controller (MC) and campus APs (CAPs). One of the WLANs enforces 802.IX authentication lo Aruba ClearPass Policy Manager {CPPM) When you test connecting the client to the WLAN. the test falls You check Aruba ClearPass Access Tracker and cannot find a record of the authentication attempt You ping from the MC to CPPM. and the ping is successful.
What is a good next step for troubleshooting?
You have an AOS-8 architecture, consisting of a Mobility Conductor (MC) and Mobility Controllers (MCs). You want to monitor wireless clients’ application usage in the Traffic Analysis dashboard. What is a requirement?
Refer to the exhibit.
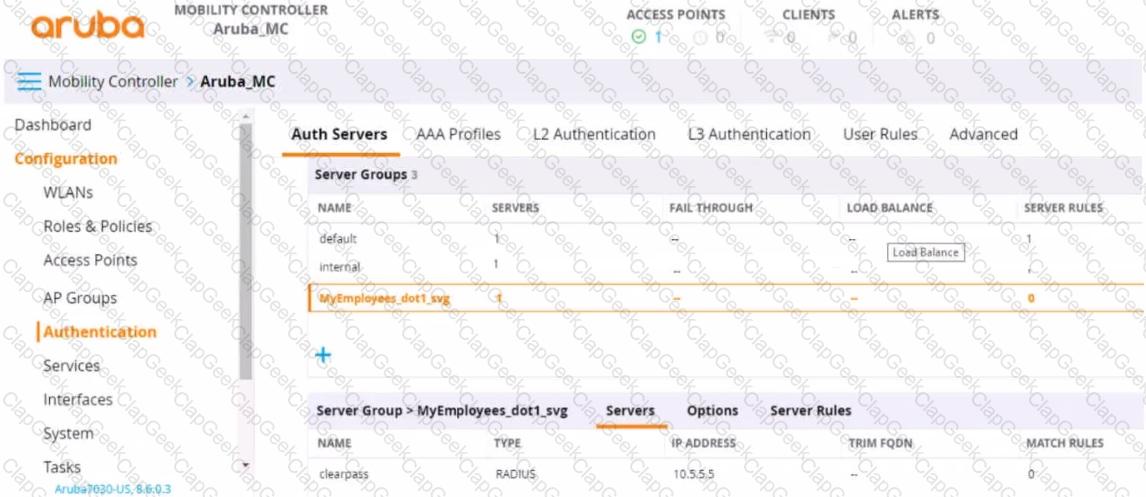
You have set up a RADIUS server on an ArubaOS Mobility Controller (MC) when you created a WLAN named "MyEmployees .You now want to enable the MC to accept change of authorization (CoA) messages from this server for wireless sessions on this WLAN.
What Is a part of the setup on the MC?
You have been asked to send RADIUS debug messages from an ArubaOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command: logging 10.5.6.12
You enter this command: debug radius all
What is the correct debug destination?
You have deployed a new HPE Aruba Networking Mobility Controller (MC) and campus APs (CAPs). One of the WLANs enforces 802.1X authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). When you test connecting the client to the WLAN, the test fails. You check ClearPass Access Tracker and cannot find a record of the authentication attempt. You ping from the MC to CPPM, and the ping is successful.
What is a good next step for troubleshooting?
Refer to the exhibit:
port-access role role1 vlan access 11
port-access role role2 vlan access 12
port-access role role3 vlan access 13
port-access role role4 vlan access 14
aaa authentication port-access dot1x authenticator
enable
interface 1/1/1
no shutdown
no routing
vlan access 1
aaa authentication port-access critical-role role1
aaa authentication port-access preauth-role role2
aaa authentication port-access auth-role role3
interface 1/1/2
no shutdown
no routing
vlan access 1
aaa authentication port-access critical-role role1
aaa authentication port-access preauth-role role2
aaa authentication port-access auth-role role3
The exhibit shows the configuration on an AOS-CX switch.
Client1 connects to port 1/1/1 and authenticates to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM sends an Access-Accept with this VSA: Aruba-User-Role: role4.
Client2 connects to port 1/1/2 and does not attempt to authenticate.To which roles are the users assigned?


