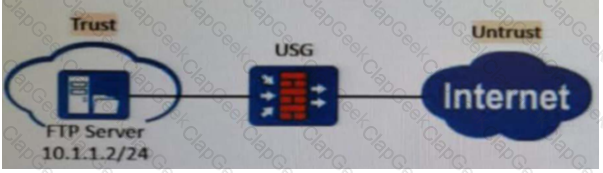
As shown in the figure, nat server global202.106.1.1 inside10.10.1.1 is configured on the firewall. Which of the following is the correct configuration for interzone rules? ( )[Multiple choice]*
Regarding the characteristics of the routing table, which of the following items is described correctly
What is correct in the following description of Security Alliance in IPSec?
There are two ways to set up an IPSec SA
Under normal circumstances, the Emai1 protocols we often talk about include ____, POP3, and SMTP.[fill in the blank]*
The following description of the intrusion fire protection system IPS, which is correct?
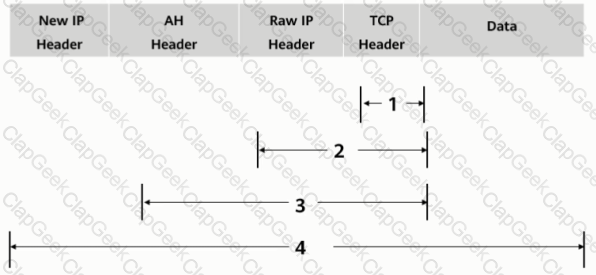
As shown in the figure, what is the authentication range of the AH protocol in tunnel mode?