You work as an IT Technician for uCertify Inc. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
Which of the following security protocols can be used to support MS-CHAPv2 for wireless client authentication?
Each correct answer represents a complete solution. Choose two.
Which of the following attacks allows an attacker to recover the key in an RC4 encrypted stream from a large number of messages in that stream?
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com network. Now, when you have finished your penetration testing, you find that the weare- secure.com server is highly vulnerable to SNMP enumeration. You advise the we-are-secure Inc. to turn off SNMP; however, this is not possible as the company is using various SNMP services on its remote nodes. What other step can you suggest to remove SNMP vulnerability?
Each correct answer represents a complete solution. Choose two.
GSM uses either A5/1 or A5/2 stream cipher for ensuring over-the-air voice privacy. Which of the following cryptographic attacks can be used to break both ciphers?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He has to ping 500 computers to find out whether these computers are connected to the server or not. Which of the following will he use to ping these computers?
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Website. The we-are-secure.com Web server is using Linux operating system. When you port scanned the we-are-secure.com Web server, you got that TCP port 23, 25, and 53 are open. When you tried to telnet to port 23, you got a blank screen in response. When you tried to type the dir, copy, date, del, etc. commands you got only blank spaces or underscores symbols on the screen. What may be the reason of such unwanted situation?
Fill in the blank with the appropriate word.
____is a port scanner that can also be used for the OS detection.
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
You enter the following URL on your Web browser:
http://www.we-are-secure.com/scripts/..%co%af../..%co%
af../windows/system32/cmd.exe?/c+dir+c:\
What task do you want to perform?
You want to perform passive footprinting against we-are-secure Inc. Web server. Which of the following tools will you use?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He enters a single quote in the input field of the login page of the Weare- secure Web site and receives the following error message:
Microsoft OLE DB Provider for ODBC Drivers error '0x80040E14'
This error message shows that the We-are-secure Website is vulnerable to __________.
While scanning a remote system that is running a web server with a UDP scan and monitoring the scan with a sniffer, you notice that the target is responding with ICMP Port Unreachable only once a second What operating system is the target likely running?
You have compromised a Windows XP system and Injected the Meterpreter payload into the lsass process. While looking over the system you notice that there is a popular password management program on the system. When you attempt to access the file that contains the password you find it is locked. Further investigation reveals that it is locked by the passmgr process. How can you use the Meterpreter to get access to this file?
By default Active Directory Controllers store password representations in which file?
Which of the following file transfer programs will automatically convert end-of line characters between different platforms when placed in ASCII Mode?
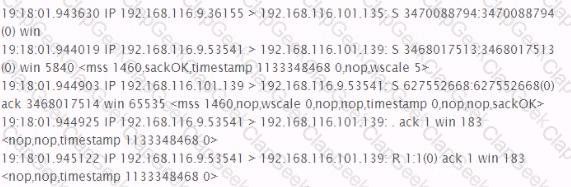
Analyze the excerpt from a packet capture between the hosts 192.168.116.9 and 192.168.116.101. What factual conclusion can the tester draw from this output?
A client has asked for a vulnerability scan on an internal network that does not have internet access. The rules of engagement prohibits any outside connection for the Nessus scanning machine. The customer has asked you to scan for a new critical vulnerability, which was released after the testing started, winch of the following methods of updating the Nessus plugins does not violate the rules of engagement?
Which of the following is the number of bits of encryption that 64-bit Wired Equivalent Privacy (WEP) effectively provides?
You suspect that system administrators In one part of the target organization are turning off their systems during the times when penetration tests are scheduled, what feature could you add to the ' Rules of engagement' that could help your team test that part of the target organization?
Where are Netcat's own network activity messages, such as when a connection occurs, sent?
When attempting to crack a password using Rainbow Tables, what is the output of the reduction function?
A customer has asked for a scan or vulnerable SSH servers. What is the penetration tester attempting to accomplish using the following Nmap command?

What section of the penetration test or ethical hacking engagement final report is used to detail and prioritize the results of your testing?
You are pen testing a Linux target from your windows-based attack platform. You just moved a script file from the windows system to the Linux target, but it will not execute properly. What is the most likely problem?
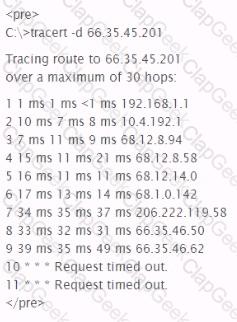
What is the most likely cause of the responses on lines 10 and 11 of the output below?
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
Which of the following techniques is used to monitor telephonic and Internet conversations by a third party?
Which of the following is the correct sequence of packets to perform the 3-way handshake method?
Fill in the blank with the appropriate act name.
The ____act gives consumers the right to ask emailers to stop spamming them.
__________ firewall architecture uses two NICs with a screening router inserted between the host and the untrusted network.
Fill in the blank with the appropriate tool name.
__________is a wireless network cracking tool that exploits the vulnerabilities in the RC4 Algorithm, which comprises the WEP security parameters.
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
You send SYN packets with the exact TTL of the target system starting at port 1 and going up to port 1024 using hping2 utility. This attack is known as __________.
Which of the following tools monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools?
You are concerned about rogue wireless access points being connected to your network. What is the best way to detect and prevent these?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. Rick, your assistant, is configuring some laptops for wireless access. For security, WEP needs to be configured for wireless communication. By mistake, Rick configures different WEP keys in a laptop than that is configured on the Wireless Access Point (WAP). Which of the following statements is true in such situation?
Which of the following tools is spyware that makes Windows clients send their passwords as clear text?
Which of the following statements are true about firewalking?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Penetration Tester in a security service providing firm named you-are-secure Inc.
Recently, John's company has got a project to test the security of a promotional Website www.missatlanta.com and assigned the pen-testing work to John. When John is performing penetration testing, he inserts the following script in the search box at the company home page:
<script>alert('Hi, John')</script>
After pressing the search button, a pop-up box appears on his screen with the text - "Hi, John."
Which of the following attacks can be performed on the Web site tested by john while considering the above scenario?
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
You want to search the Apache Web server having version 2.0 using google hacking. Which of the following search queries will you use?
The employees of EWS Inc. require remote access to the company's Web servers. In order to provide solid wireless security, the company uses EAP-TLS as the authentication protocol. Which of the following statements are true about EAP-TLS?
Each correct answer represents a complete solution. Choose all that apply.